

On the next screen, click Register.
The next screen asks "Do you already have a Safway Club Card?" Click No.
Each student needs to use an unique phone number and email address, but I don't recommend using your personal data for tests like this.
You should use some handy word to label confidential data so we can search for it later--I used "WALRUS". So do this: pick a random four-digit number. Then fill out the next screen with test values, inserting your number where "NNNN" appears below.
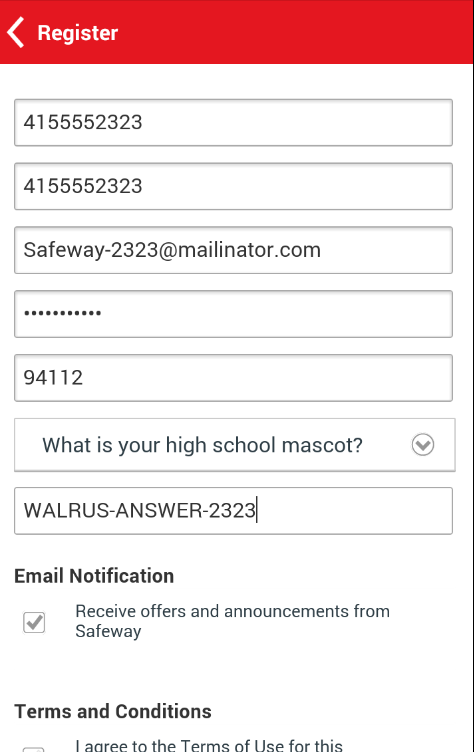
Agree to the Terms and Conditions and click Register.
A box asks if you want the browser to remember this password. Click "Not now".
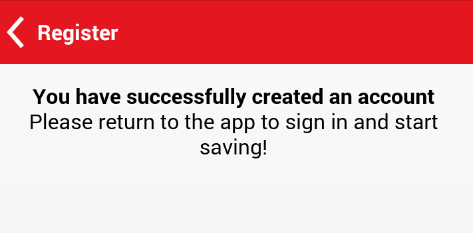
A message says "You have successfully created an account", as shown below.
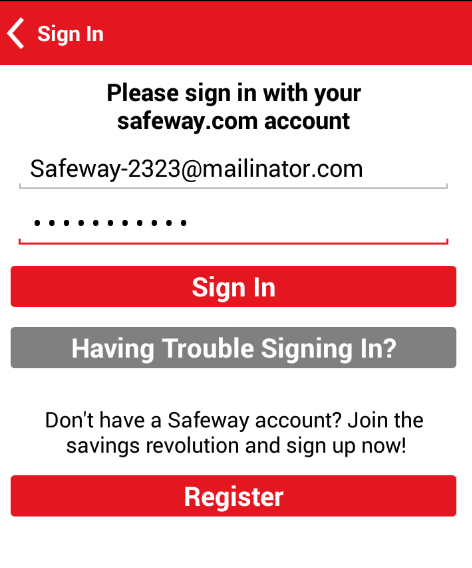
At the top lect, click the Back-arrow.
Sign in, as shown below.
Now that you are signed in, the app has probably stored some sort of local token to remember who you are. The question before us is what that token is, and where it is stored.
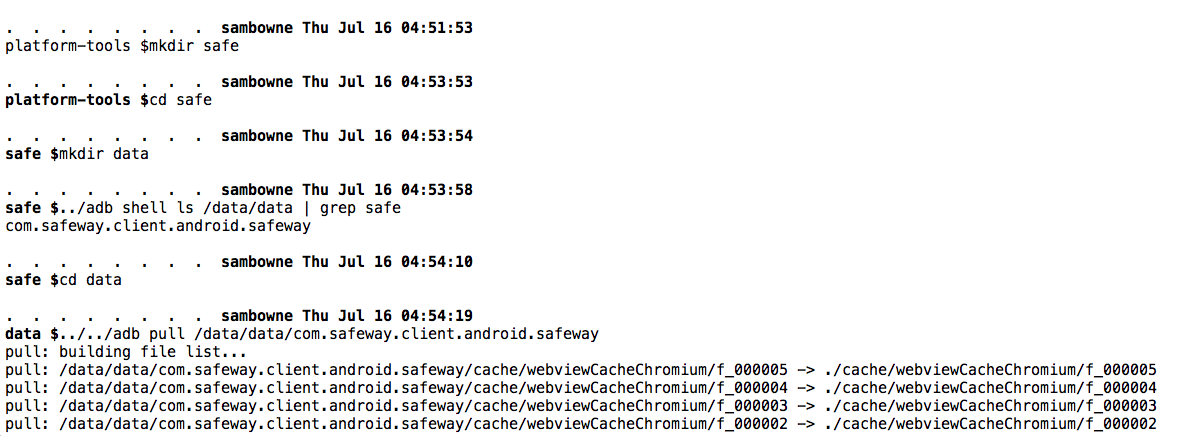
These commands move to the SDK tools directory, create a directory and a subdirectory to put the files in, find the correct path to the Safeway app's local data, and pull it to your computer.
cd
cd Android/Sdk/cd platform-tools
mkdir safe
cd safe
mkdir data
../adb shell ls /data/data | grep safe
cd data
../../adb pull /data/data/com.safeway.client.android.safeway
Troubleshooting: Finding ADB
If you are using Ubuntu, the commands above should work. If you are using another OS, the SDK path will be different.Here are common examples of SDK paths:
- Ubuntu: /home/user/Android/Sdk
- Mac: ~/Library/Android/sdk
- Windows: C:\Users\student\AppData\Local\Android\sdk
Another way to find your SDK path is to open Android Studio and click Tools, Android, "SDK Manager".
NOTE: If you are using Windows, remove the "./" before "adb".
You should see a series of files pulled, as shown below.
Explanation:
grep -air password .
grep -air WALRUS .
grep -air 2323 .
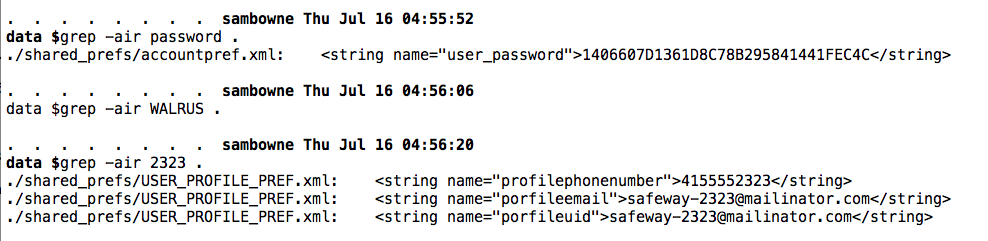
As you can see, the app stored your phone number and email address in plaintext, but your password was converted to a long random-looking number. That's a good practice, assuming that it used some good hashing or encryption method.
The personal data is apparently stored in two XML files: shared_prefs/accountpref.xml and shared_prefs/USER_PROFILE_PREF.xml
It's worth looking at those files in their entirety in a text editor.
Execute this command:
nano shared_prefs/accountpref.xml
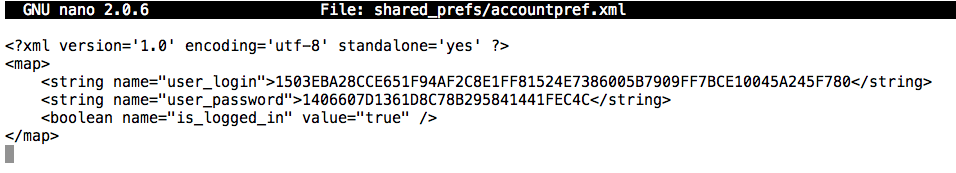
Press Ctrl+X to exit nano.
Execute this command:
nano shared_prefs/USER_PROFILE_PREF.xml
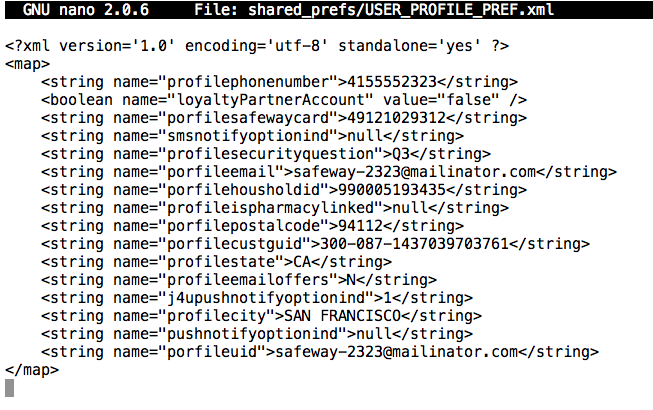
If you are at Working Connections, there's is a list of known insecure apps in the classroom to try.