
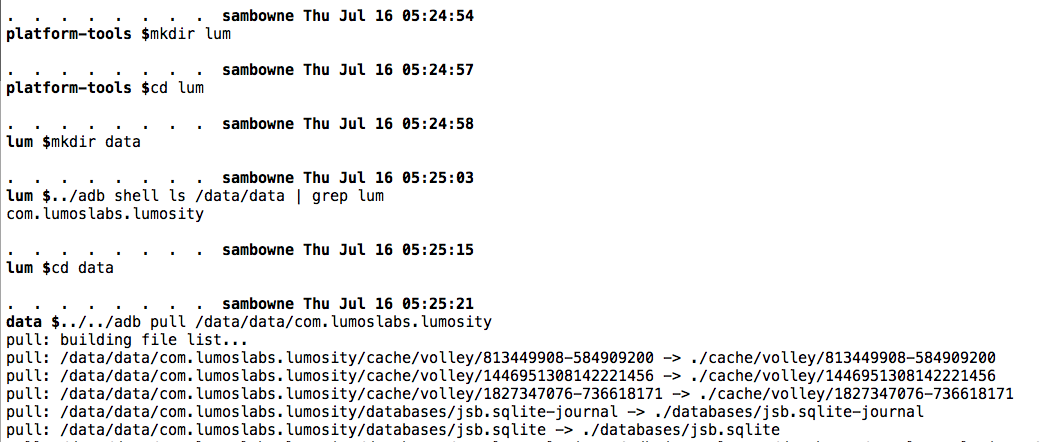
These commands move to the SDK tools directory, create a directory and a subdirectory to put the files in, find the correct path to the Safeway app's local data, and pull it to your computer.
cd
cd Android/Sdk/cd platform-tools
mkdir lum
cd lum
mkdir data
../adb shell ls /data/data | grep lum
cd data
../../adb pull /data/data/com.lumoslabs.lumosity
Troubleshooting: Finding ADB
If you are using Ubuntu, the commands above should work. If you are using another OS, the SDK path will be different.Here are common examples of SDK paths:
- Ubuntu: /home/user/Android/Sdk
- Mac: ~/Library/Android/sdk
- Windows: C:\Users\student\AppData\Local\Android\sdk
Another way to find your SDK path is to open Android Studio and click Tools, Android, "SDK Manager".
NOTE: If you are using Windows, remove the "./" before "adb".
You should see a series of files pulled, as shown below.
Explanation:
grep -air WALRUS .
grep -air 2323 .
grep -air password .
grep -air secret .
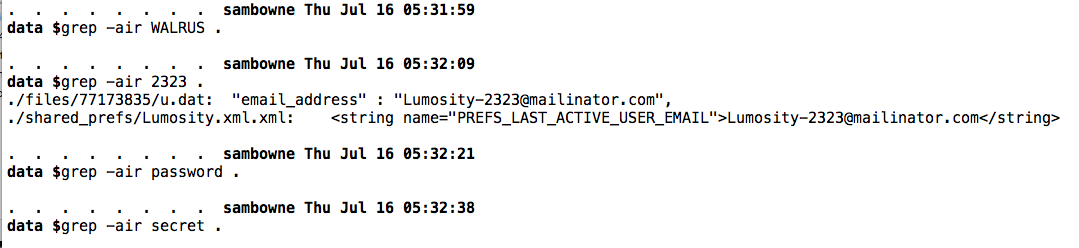
As you can see, the app stored your email address in plaintext, but not your password.
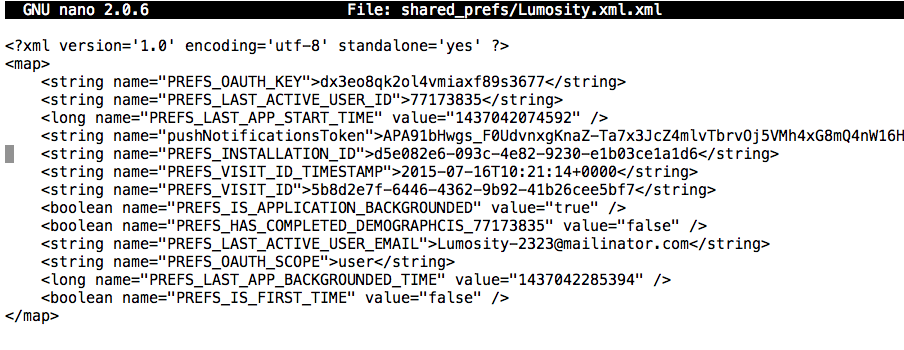
The personal data is apparently stored in two XML files: files/77173835/u.dat and /shared_prefs/Lumosity.xml.xml
It's worth looking at those files in their entirety in a text editor.
Execute this command:
nano files/77173835/u.dat
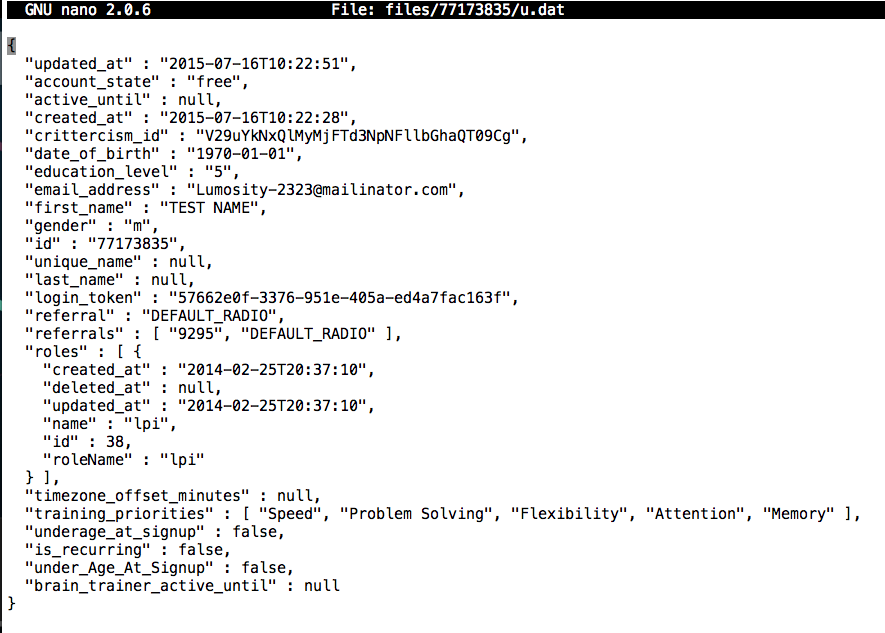
Press Ctrl+X to exit nano.
Execute this command:
nano /shared_prefs/Lumosity.xml.xml