Garland & Associates Android Insecure Transmissions
Summary
The Garland & Associates Android app has serious security
problems: it sends some confidential data with no encrption at all,
and when it does use SSL, it fails to validate certificates.
These practices are probably illegal in the USA, violating
HIPAA laws, and also falling below the security standards
required by the FTC.
Two American companies were sanctioned
by the FTC in 2014 for making this
same error:
FTC Final Orders with Fandango and Credit Karma Provide Guidance on Mobile App Security
What You Need
After completing the previous projects,
you should have these things working:
- Genymotion set up with Google Play
- Burp running as a proxy
- The Genymotion networking configured to send traffic through Burp
Checking Proxy Settings
If you are routing traffic through
the Burp proxy, that will make
the Google Play store difficult or
impossible to use.
In your Genymotion emulated device,
open Settings. Click
Wi-Fi. Click and hold WiredSSID
until a box pops up.
Click "Modify network".
Check "Show advanced options".
Make sure the Proxy settings shows None.
Installing the App
In Google Play, find this app and
install it:
Adjusting Proxy Settings
Adjust the Android proxy settings again to
send traffic through Burp.
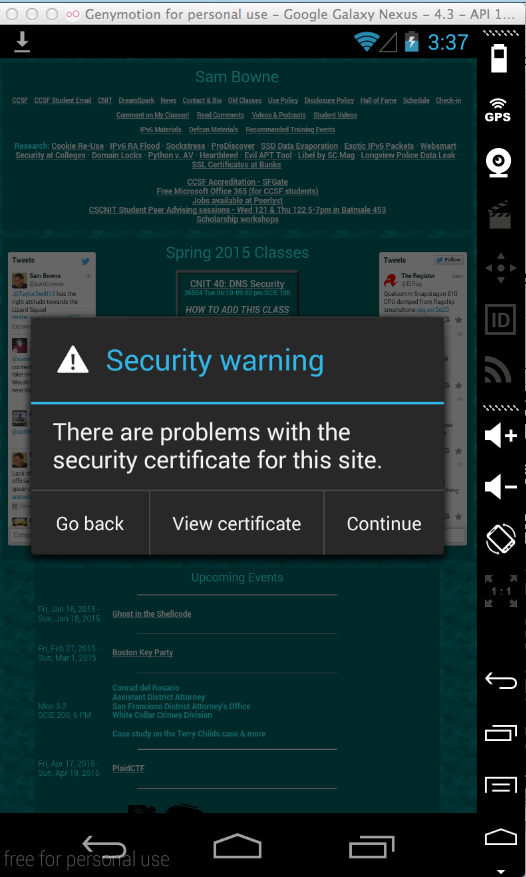
Testing Proxy Settings
On your Android device, open a Web browser and
go to https://samsclass.info
A "Security warning" box pops
up, as shown below. This shows that
the browser is operating properly
and detecting a MITM attack.
Transmitting Personal Data Over Broken SSL
In the app, at the top left, click the
icon with three horizontal dashes.
A menu appears. Click the last item:
"Log In".
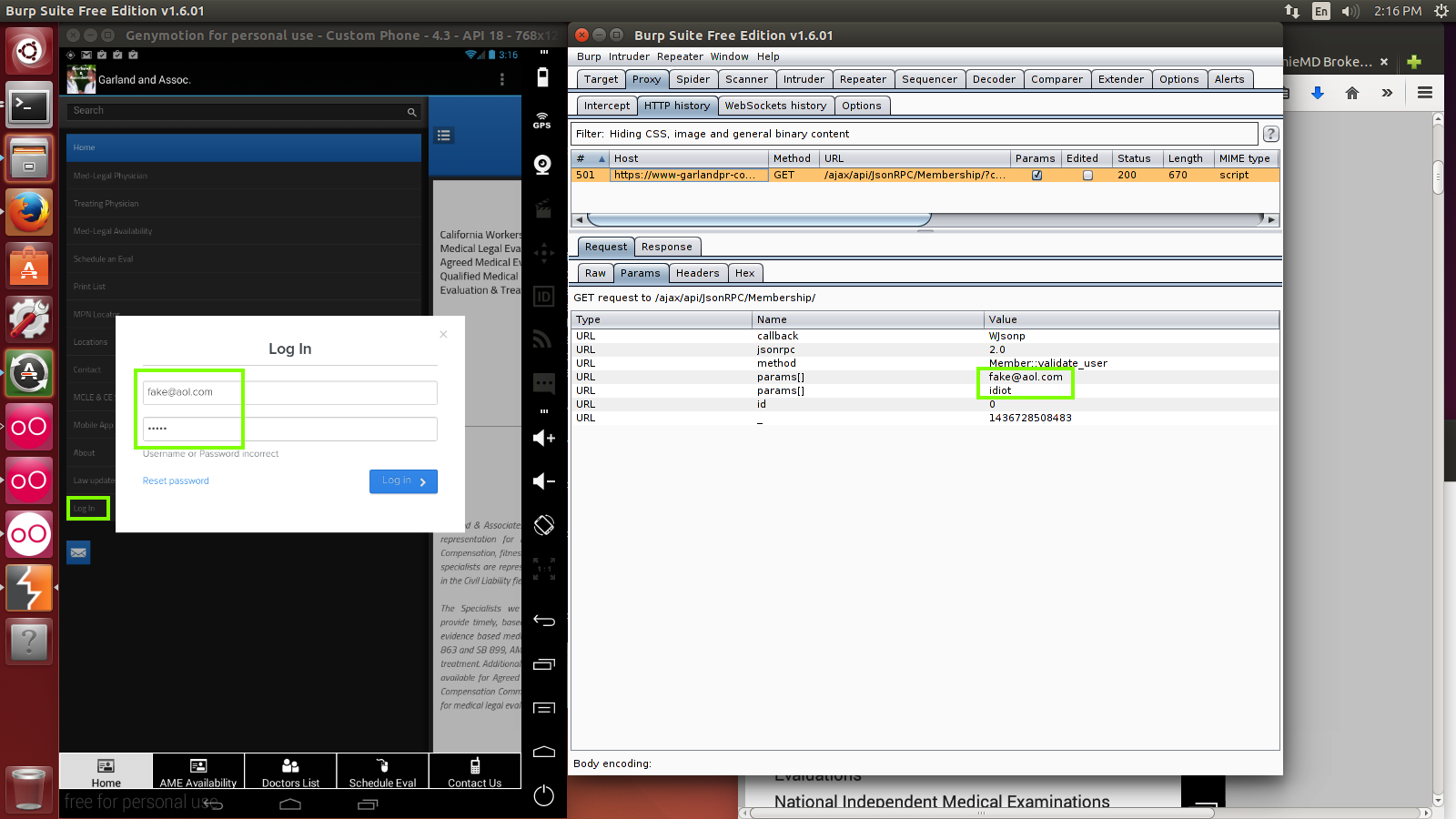
Enter a fake email address and password.
You will see it appear in Burp, as shown below.
This time it's an HTTPS connection, but the
app is skipping certificate validation, so
it allows Burp to perform a MITM attack.
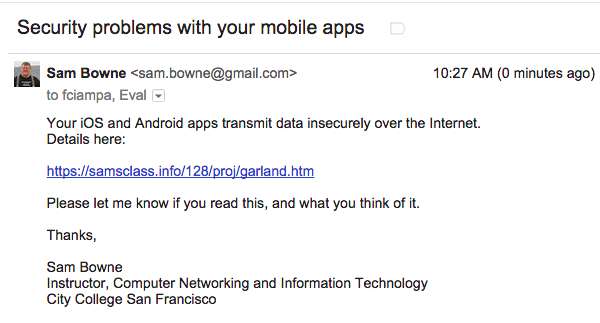
Notification
I sent this message on 6-10-15:
I got no reply.
Posted 7-12-15 by Sam Bowne
Modified to remove plaintext test 7-14-15 1 pm







