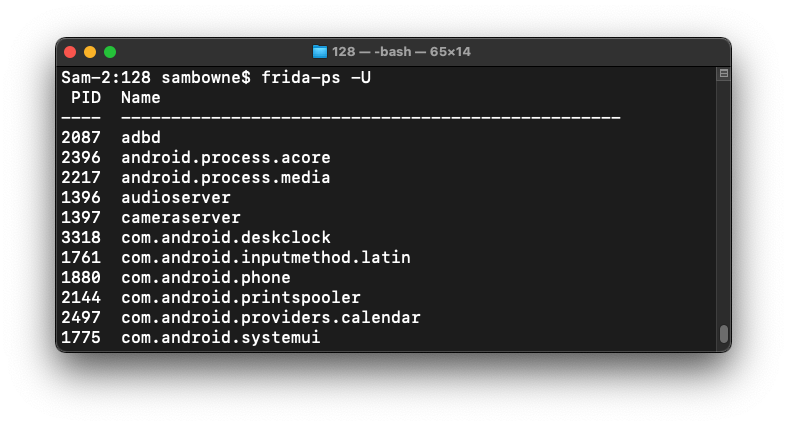
On your host system, open a new Terminal.
If your frida-tools were installed in a virtual environment, execute this command:
source venv/bin/activate
frida-ps -U

Follow the instructions for your emulator's processor below.
Intel x86_64 Processors
Download this file:keeper_x86_64.zipThen, on your host system, execute these commands:The response tells you the session ID, highlighted in the image below.Execute these commands, inserting your correct session ID instead of 1150567310 in each command below.
The reply to the last command should be "success".
ARM64 Processors
Download this file:keeperARM64.zipThen, on your host system, execute these commands:The response tells you the session ID, highlighted in the image below.Execute these commands, inserting your correct session ID instead of 277062312 in each command below.
The reply to the last command should be "success".
If an Alert box warns you that it's not safe to run it on a rooted phone. They're not wrong. Click "CONTINUE ANYWAY".
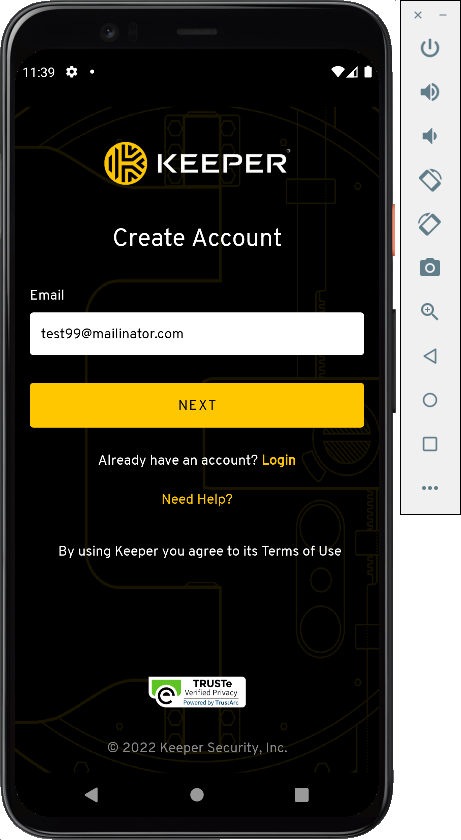
In the "Welcome to Your Keeper Vault" screen, click "CREATE ACCOUNT".
Enter an email address ending in mailinator.com, as shown below, and click NEXT.
At the top left, enter your mail account name and click GO.
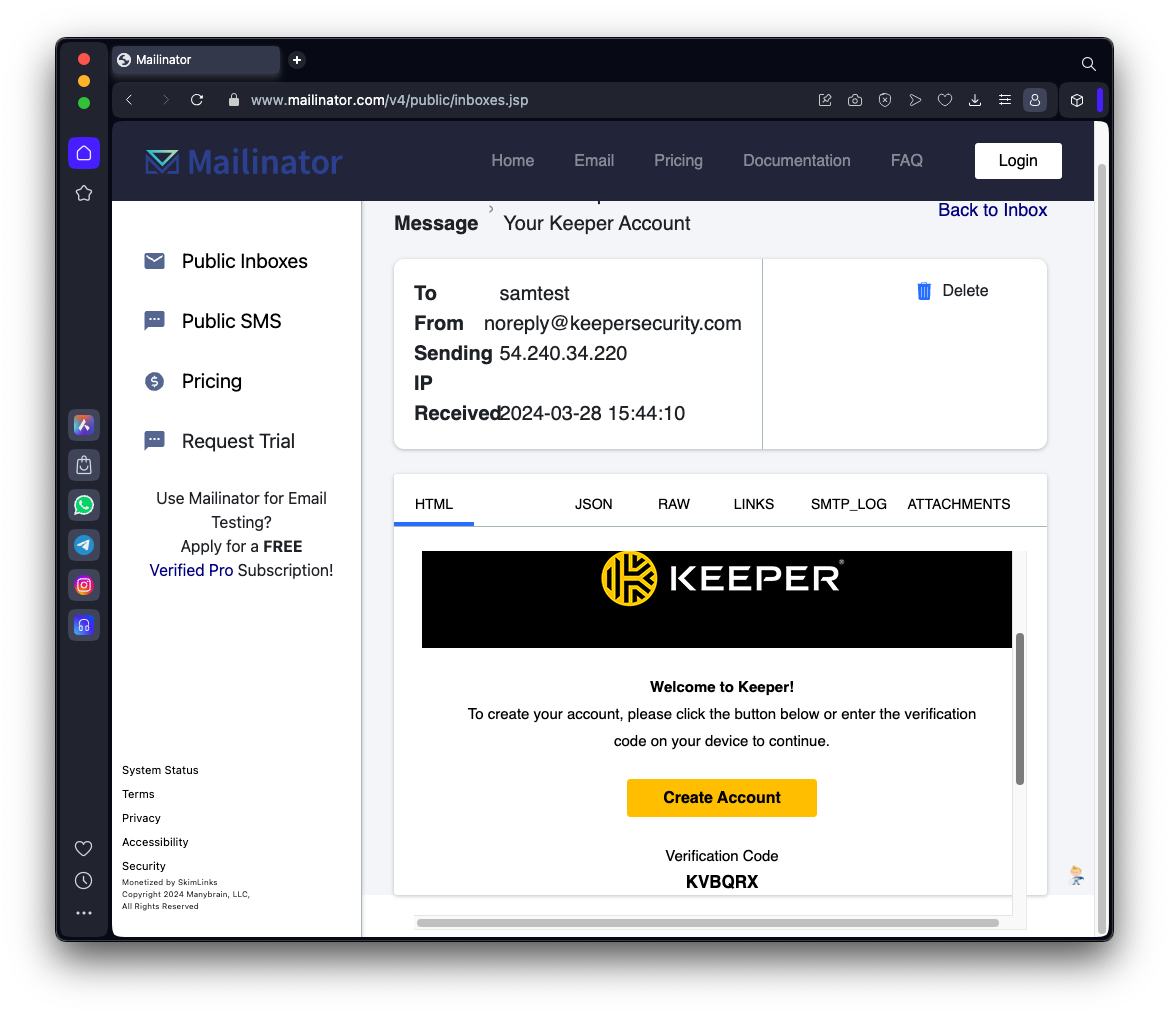
In the email from Keeper, find your Verification Code, as shown below.
On your Android device, a box appears saying "Creating your first record", as shown below.
click "LET'S DO IT".

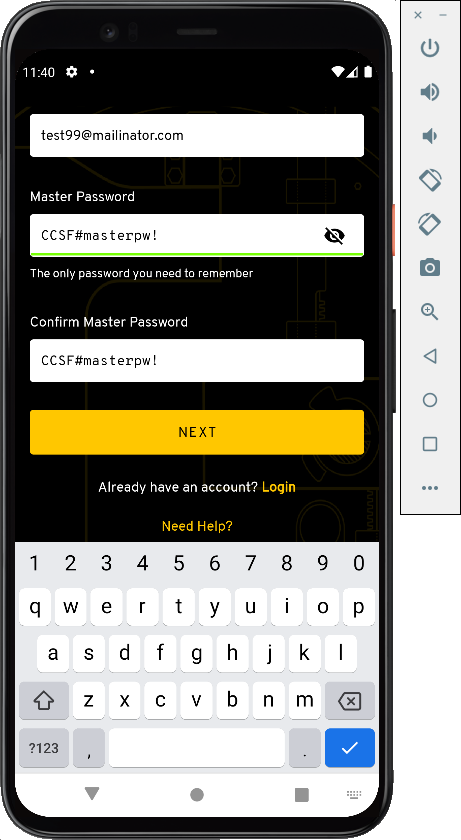
Enter a Facebook username and password, both containing the string CCSF#, as shown below.
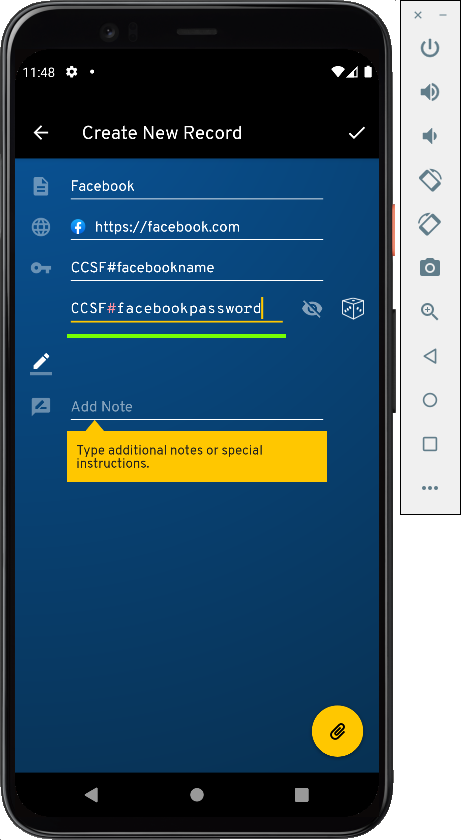
A box pops up saying "You created your first record". as shown below.

If your frida-tools were installed in a virtual environment, execute this command:
source venv/bin/activate
frida-ps -U

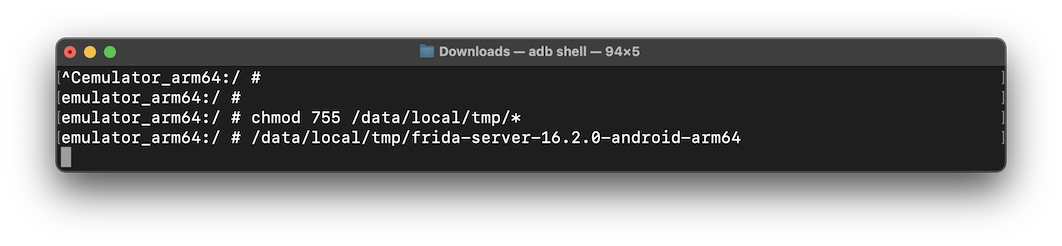
On your host system, execute these commands:
git clone https://github.com/Nightbringer21/fridump.git
python3 fridump/fridump.py -h
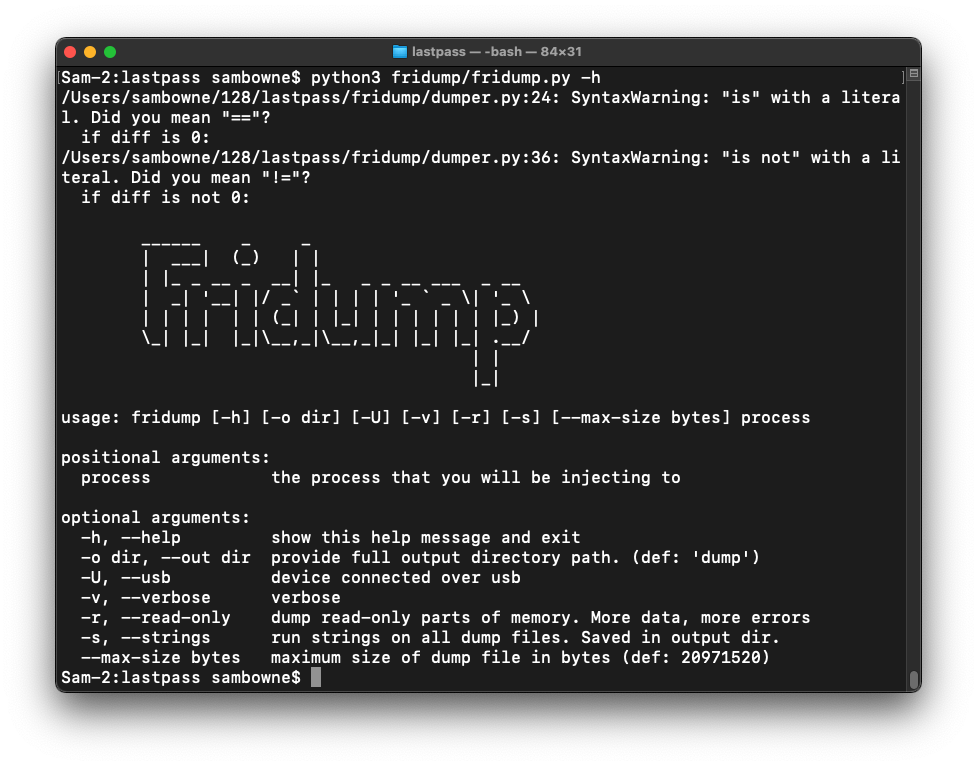
frida-ps -U | grep eep
Flag M 521.1: Dumping Memory from Keeper (15 pts)
On your host system, execute these commands.Be patient, the first one may take a minute or so to start.
Many copies of your private data are found, ending with your master password, as shown below.The flag is covered by a green rectangle in the image below.
Posted 11-8-22
Uses archived Keeper version, works for both x86_64 and ARM64 4-16-24
Video added 4-18-24