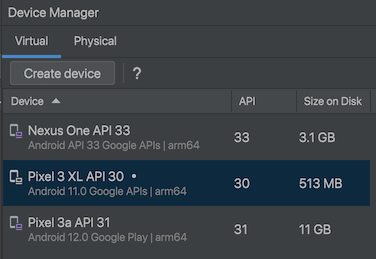
Note: the app we're using doesn't work on API 33.
I used the emulator highlighted in the image below. My emulator uses an ARM64 processor. Make a note of the processor your emulator is using.

python3 -m pip install frida-tools
Execute this command:
"error: externally-managed-environment"
If you see this error message, you need to create a Python virtual environment with these commands:
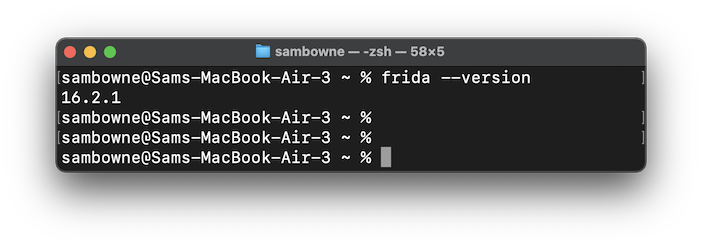
frida --version
Note your version of Frida. When I did it in 2024, it was version 16.2.1, as shown below.
https://github.com/frida/frida/releases
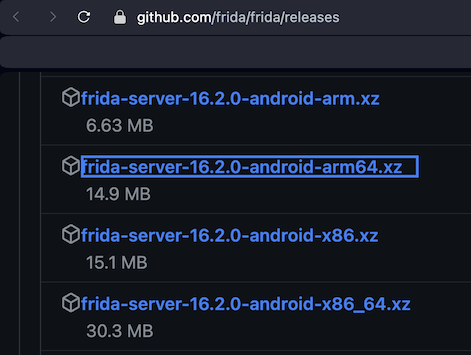
Download the appropriate version of frida-server for your emulator's processor, with the same version number you found above, or as close as possible.I used frida-server-16.2.0-android-arm64.xz, outlined in the image below.
adb push frida-server-16.2.0-android-arm64 /data/local/tmp/
adb shell
su
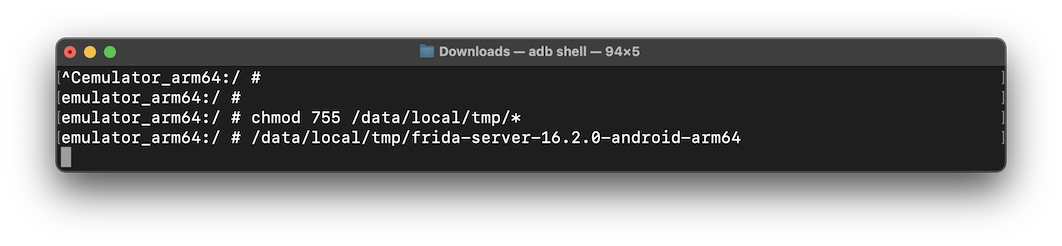
chmod 755 /data/local/tmp/*
/data/local/tmp/frida-server-16.2.0-android-arm64
Leave this Terminal window open.
If your frida-tools were installed in a virtual environment, execute this command:
source venv/bin/activate
frida-ps -U
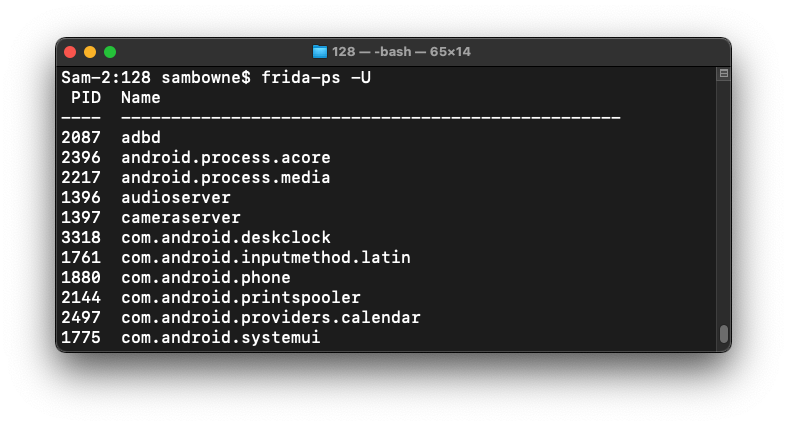
On your host system, in a Web browser, go to
https://github.com/OWASP/owasp-mastg/blob/master/Crackmes/Android/Level_01/UnCrackable-Level1.apk
Download UnCrackable-Level1.apk.If that page is not available, use this alternate link.
Drag the UnCrackable-Level1.apk file and drop it on your running Android emulator.
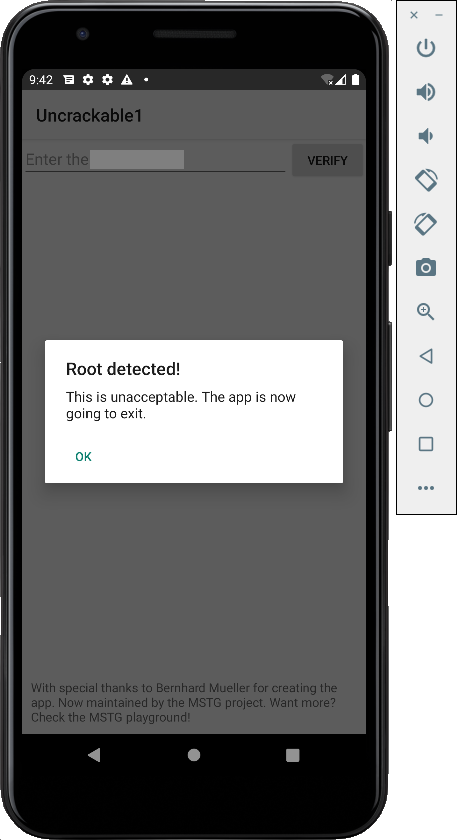
On your emulator, launch the Uncrackable app.
It refuses to run, complaining about the phone being rooted, as shown below.
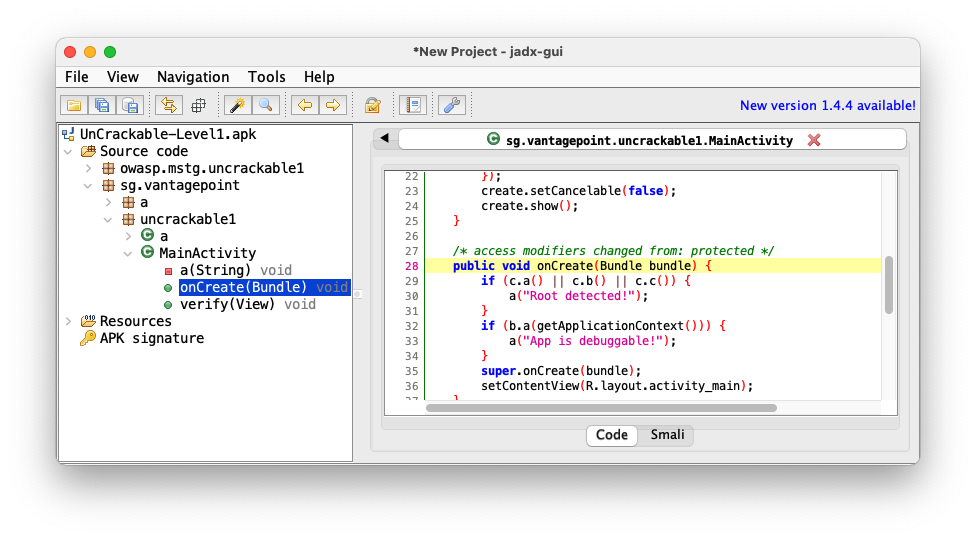
Navigate to the Main Activity and click OnCreate(Bundle), as shown below.
The root detection uses three functions: c.a(), c.b(), and c.c().
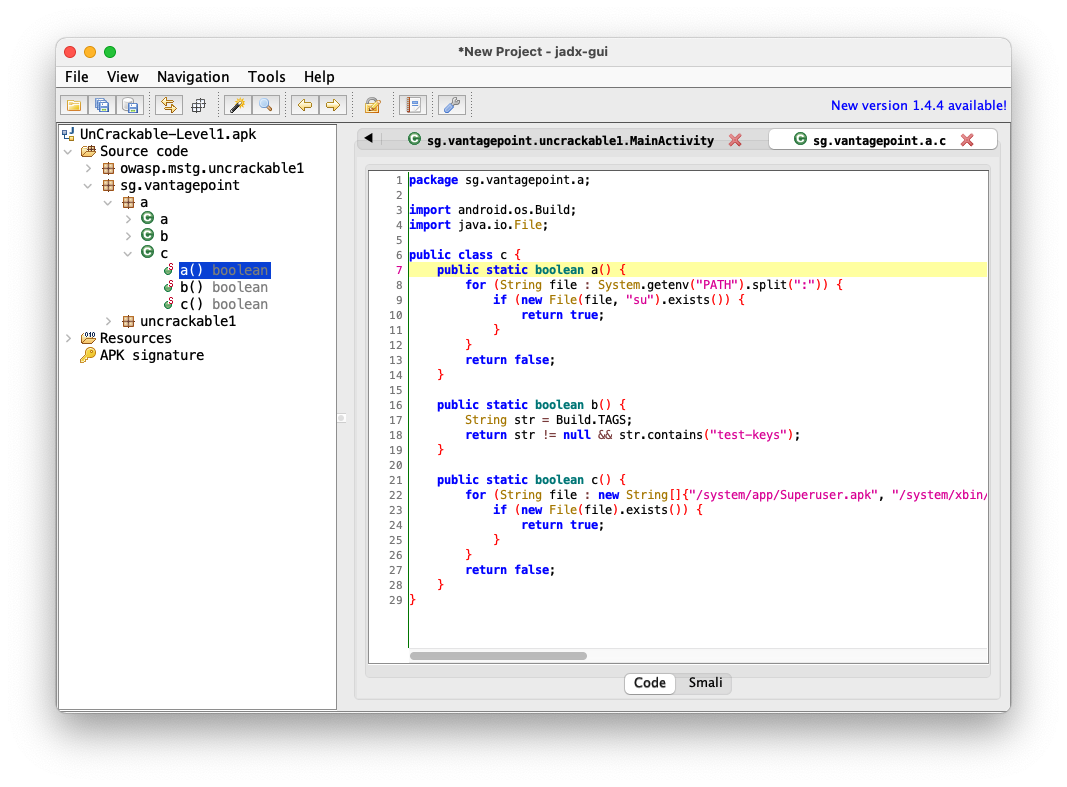
Navigate to sg.vantagepoint.a.c, as shown below.
The three functions: c.a(), c.b(), and c.c() are performing various tests to see if the phone is rooted.
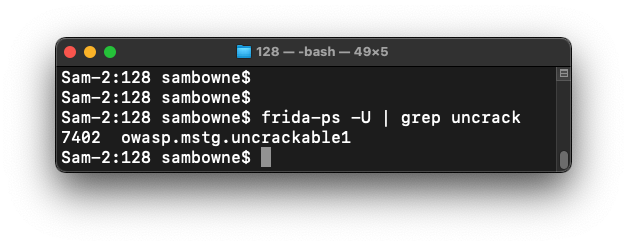
frida-ps -U | grep uncrack
The name is owasp.mstg.uncrackable1
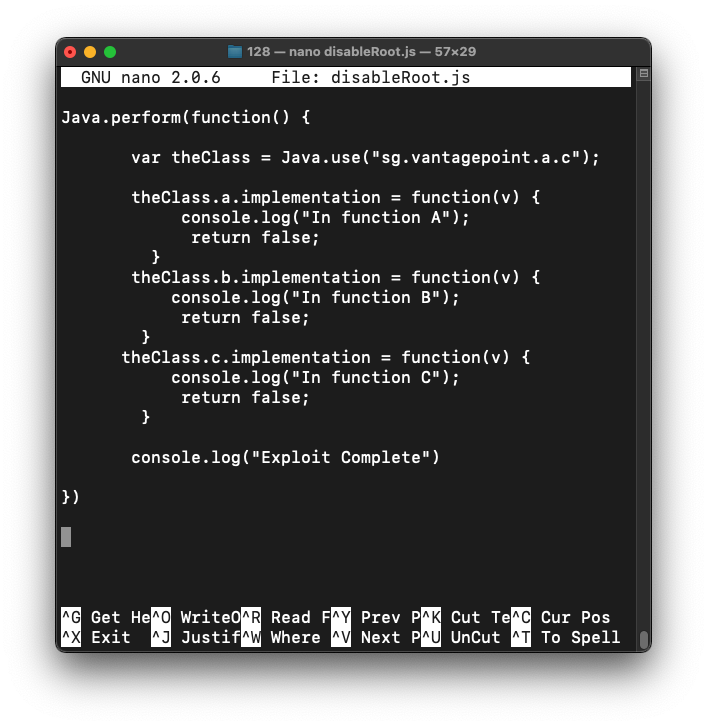
nano disableRoot.js
This code will override the a, b, and c functions and always return false.
Java.perform(function() {
var theClass = Java.use("sg.vantagepoint.a.c");
theClass.a.implementation = function(v) {
console.log("In function A");
return false;
}
theClass.b.implementation = function(v) {
console.log("In function B");
return false;
}
theClass.c.implementation = function(v) {
console.log("In function C");
return false;
}
console.log("Exploit Complete")
})
Type Ctrl+x, y, Enter to save the file.
In a Terminal, execute this command:
If you are using Frida version 16, omit the --no-pause switch
frida -U --no-pause -l disableRoot.js -f owasp.mstg.uncrackable1
M 513.1: Message
The app opens.The flag is covered by a green rectangle in the image below.