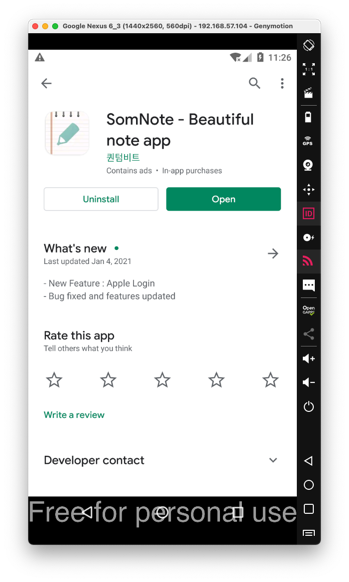
If you can't get the app from Google Play, download my archived copy.

Click "LOGIN WITH EMAIL", and enter any email and password, and click the Login button.
If it asks for permissions, grant them.
In the login screen, as shown below, at the top right, click X.

A "VIP Privileges" box appears. At the top right, click X to close it.
Click "Get started with SomNote", as shown below.
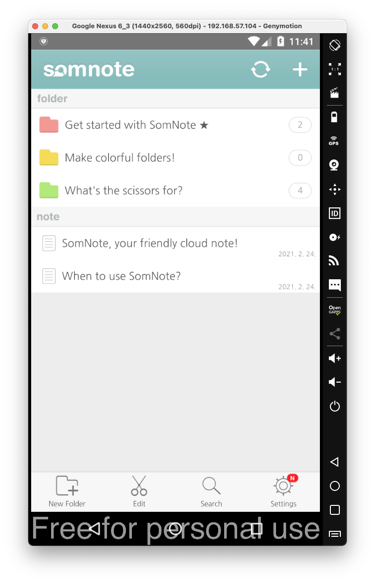
On the next screen, at the top right, click the + sign.
Type in a secret message, as shown below.
At the top right, click Save.
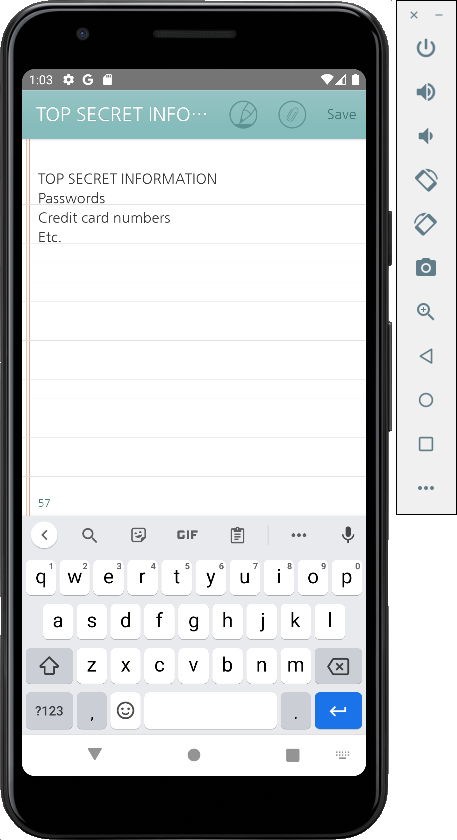
At the lower right of your Android device, click the square button.
Close SomNote.
You will need to use the answer from the first command as the argument for the second, and the answer from the second command as the argument for the third.
You may need to enter a path before the adb command, which you can get from Android Studio's SDK manager.
mkdir somnote
cd somnote
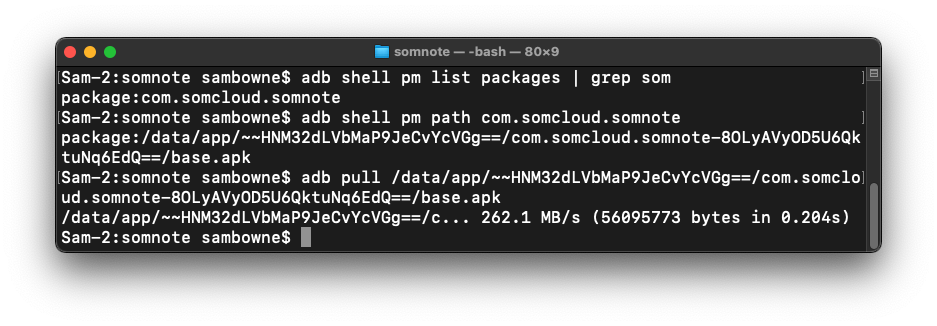
adb shell pm list packages | grep som
adb shell pm path com.somcloud.somnote
adb pull /data/app/~~HNM32dLVbMaP9JeCvYcVGg==/com.somcloud.somnote-8OLyAVyOD5U6QktuNq6EdQ==/base.apk
In the center pane, scroll down to the AndroidManifest.xml file, as shown below.
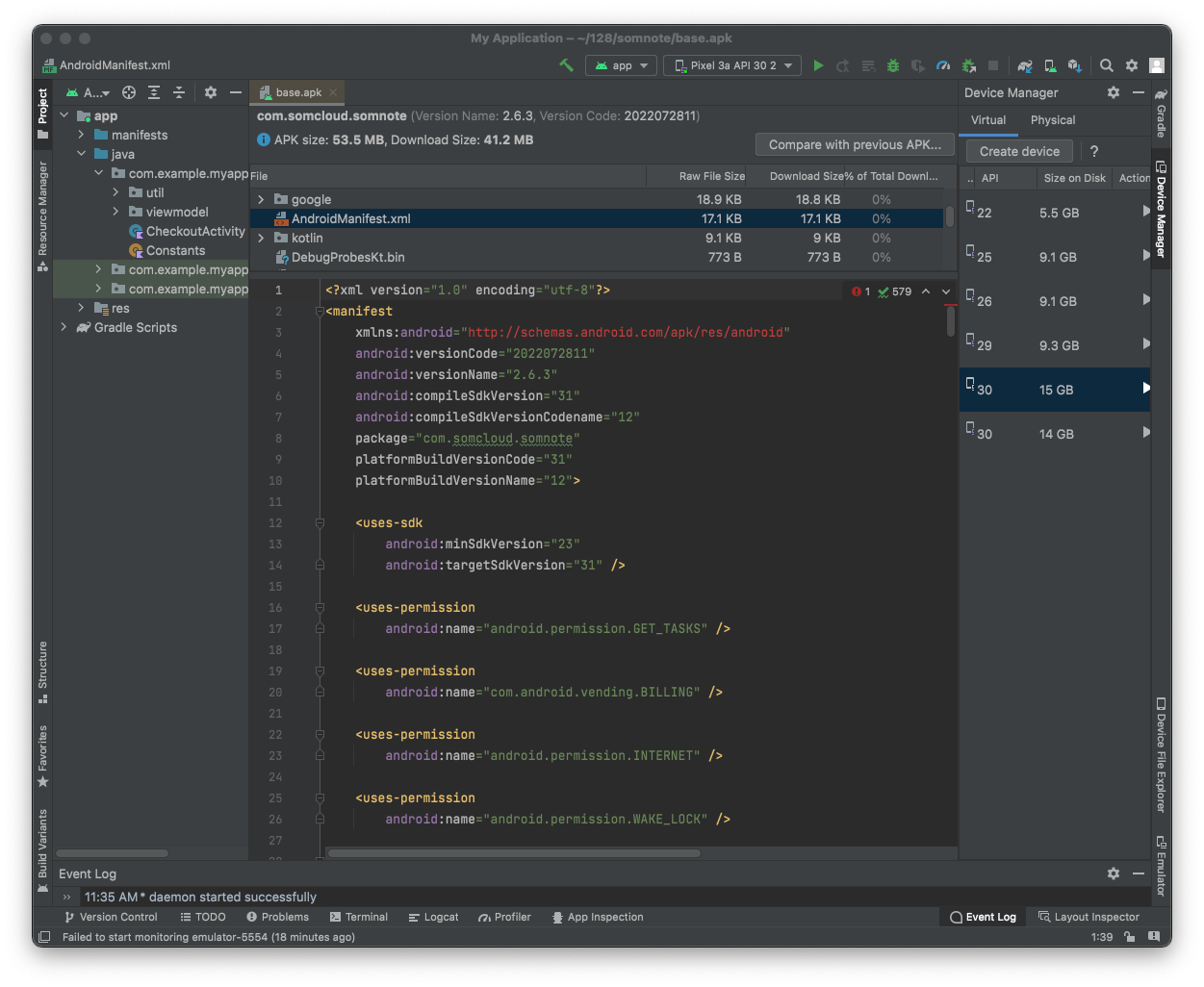
Find the provider named "com.somcloud.somnote.database.SomNoteProvider", as shown below.
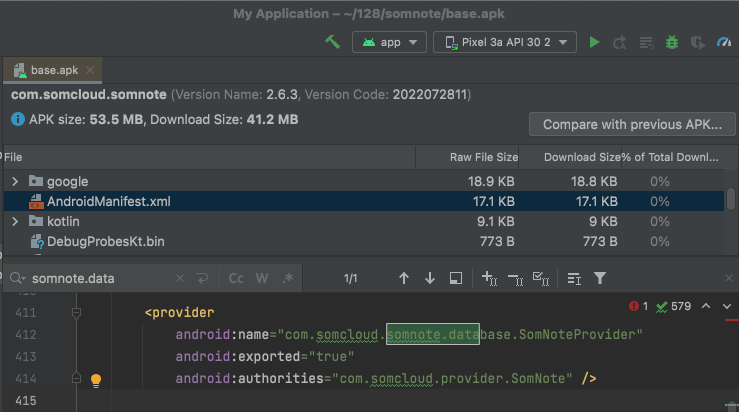
Notice that no permissions are required to access this provider.
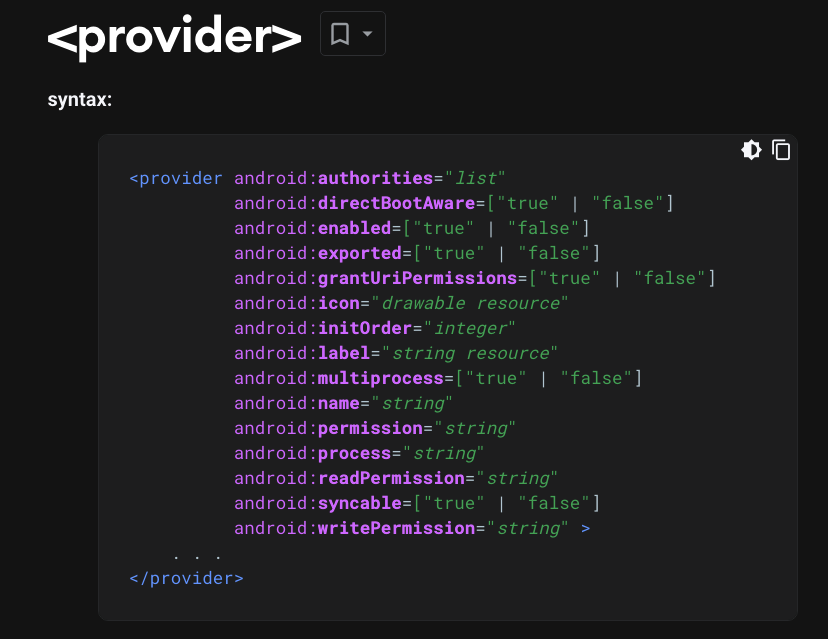
The Android documentation shown below shows that permissions should be defined within the "provider" container:
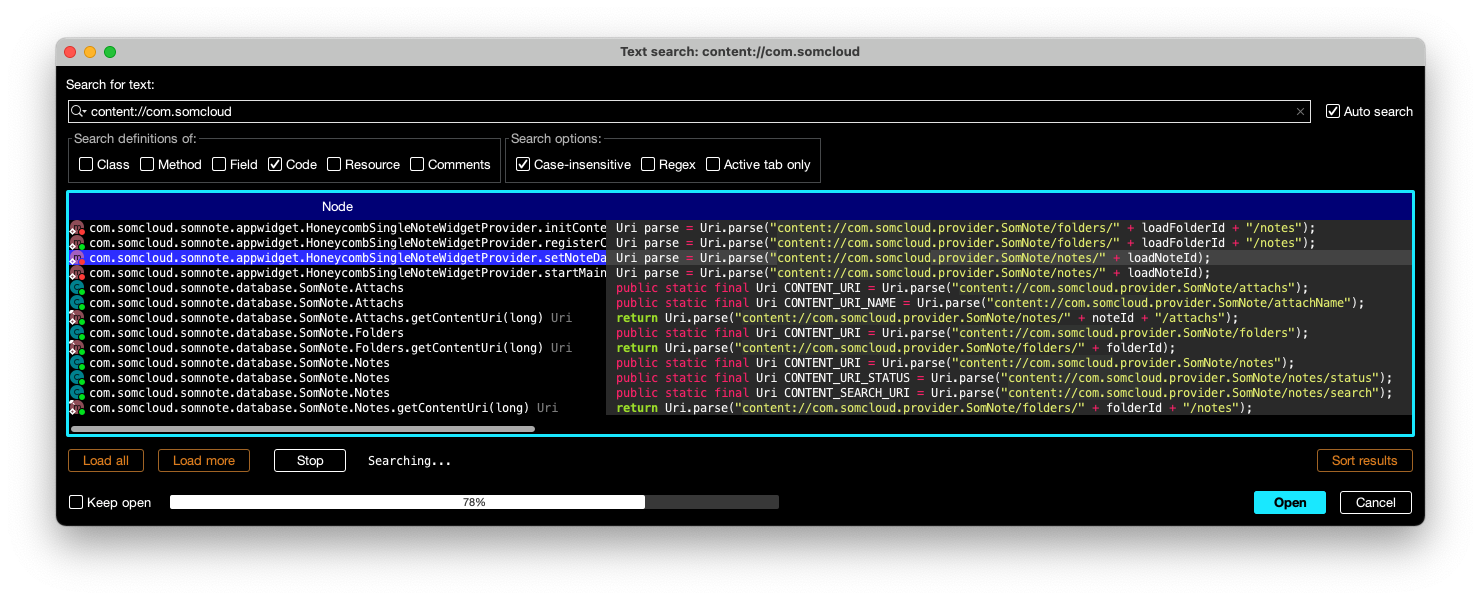
Click Navigation, "Text search".
Search for:
content://com.somcloud
content://com.somcloud.provider.SomNote/notes/
On your MacOS or Linux system, execute this command:
M 503.1: Reading from the Content Provider (15 pts)
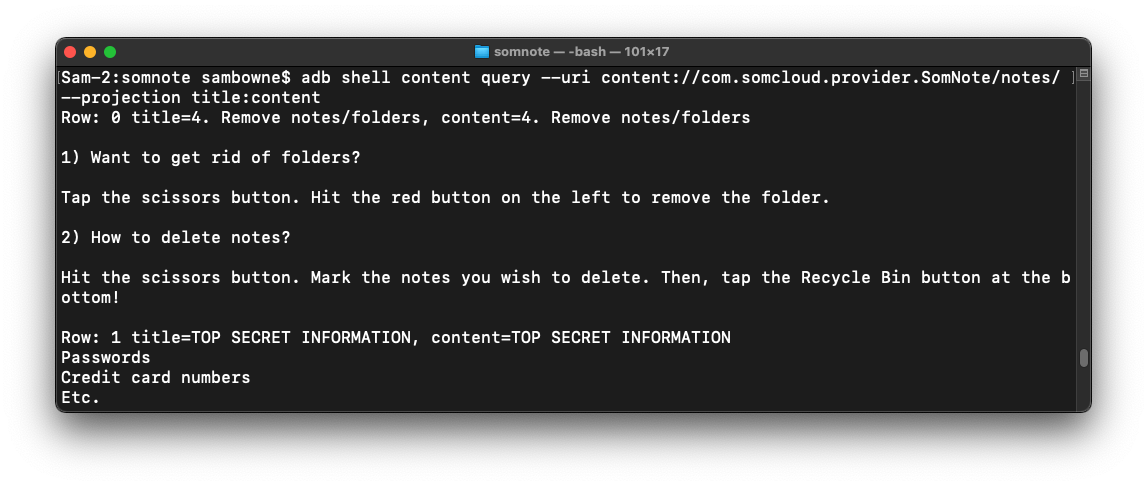
On your MacOS or Linux system, execute this command:The reply includes a list of fields, including the "title" and "content" fielda, highlighted in the image below.
Find the text covered by a green box in the image above. That's the flag.
adb shell content query --uri content://com.somcloud.provider.SomNote/notes/ --projection title:content
Updated to remove Drozer 10-31-22
Extraneous apktool command removed 11-1-22
More references to drozer removed 11-22-22