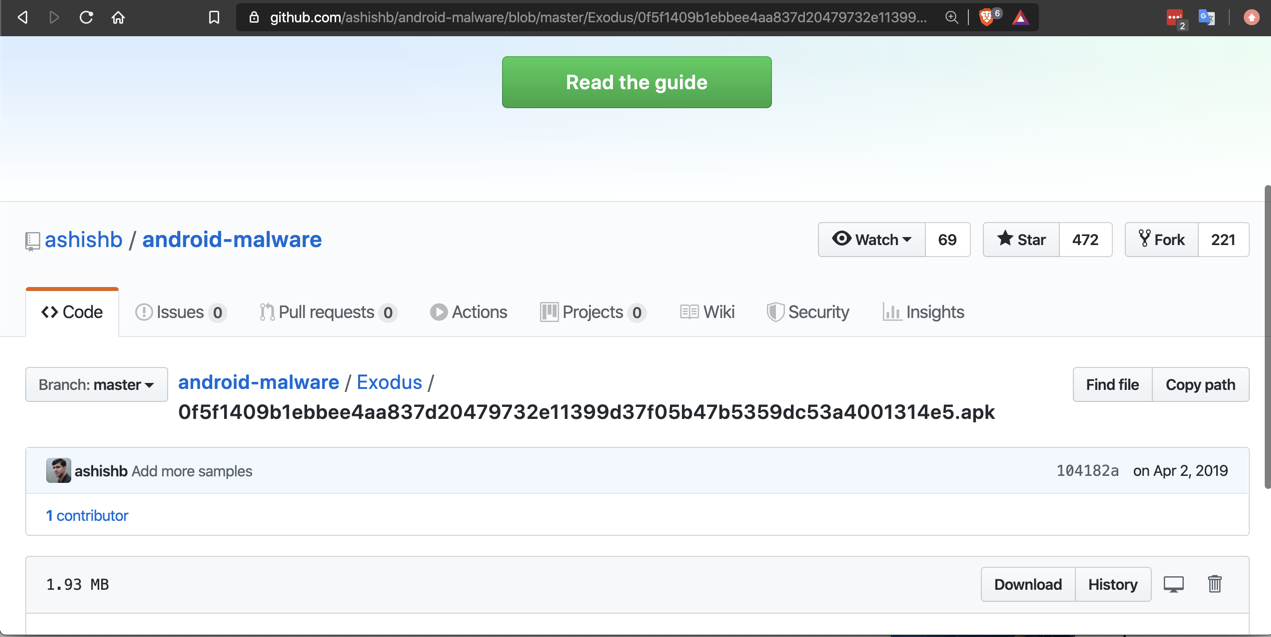
https://github.com/ashishb/android-malware
Click Exodus. Click the first sample, with a long name beginning with 0f5.
Click the Download button, as shown below.
Save the malware file on your computer.

Drag the malware sample and drop it onto the VirusTotal page.
VirusTotal analyzes the file.
First it shows you the results of many antivirus engines, detecting this file as malware, as shown below.
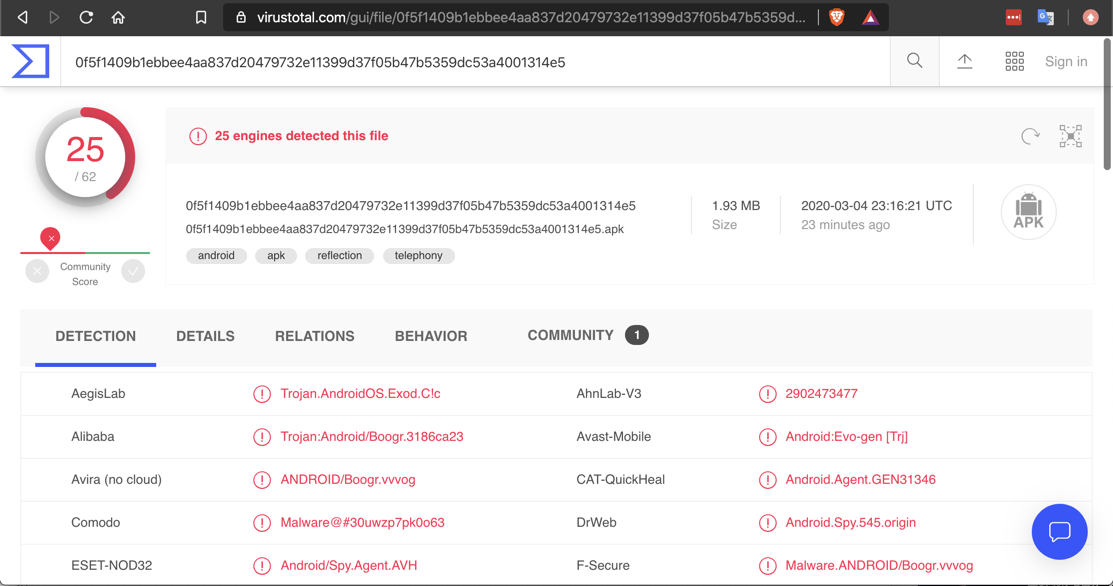
Click the other tabs, especially DETAILS, RELATIONS, and BEHAVIOR.
Flag M 310.1: Country Code (5 pts)
Find the digital certificate used to sign this file.The flag is the Country Code.
Flag M 310.2: System command (5 pts)
Use the same sample.
This sample only executes one system command.
That command is the flag.Hint: On the BEHAVIOR tab, view the full reports and look for a path starting with /system
Flag M 310.3: dsencrypt (5 pts)
Download and analyze the dsencrypt sample.
This sample contacts a domain that starts with "p".That domain name is the flag.
Flag M 310.4: Brazilian Android RAT (5 pts)
Download and analyze the brazilian_android_RAT sample.
Find the digital certificate used to sign this file.The flag is the Organization that signed this file.