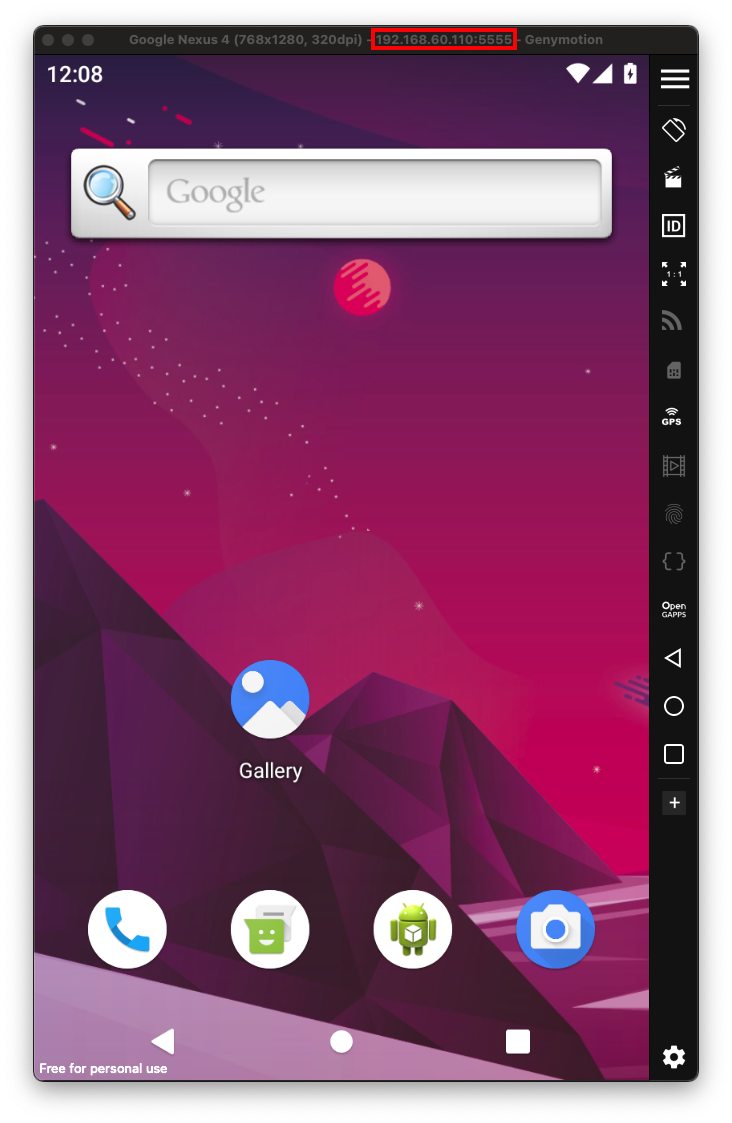
https://www.genymotion.com/download/Launch Genymotion. At the top right, click the pink plus-sign and create an emulator using these options:
Notice the device identifier, outlined in red at the top of the image below.

Get DockerA "docker desktop" window appears, as shown below.
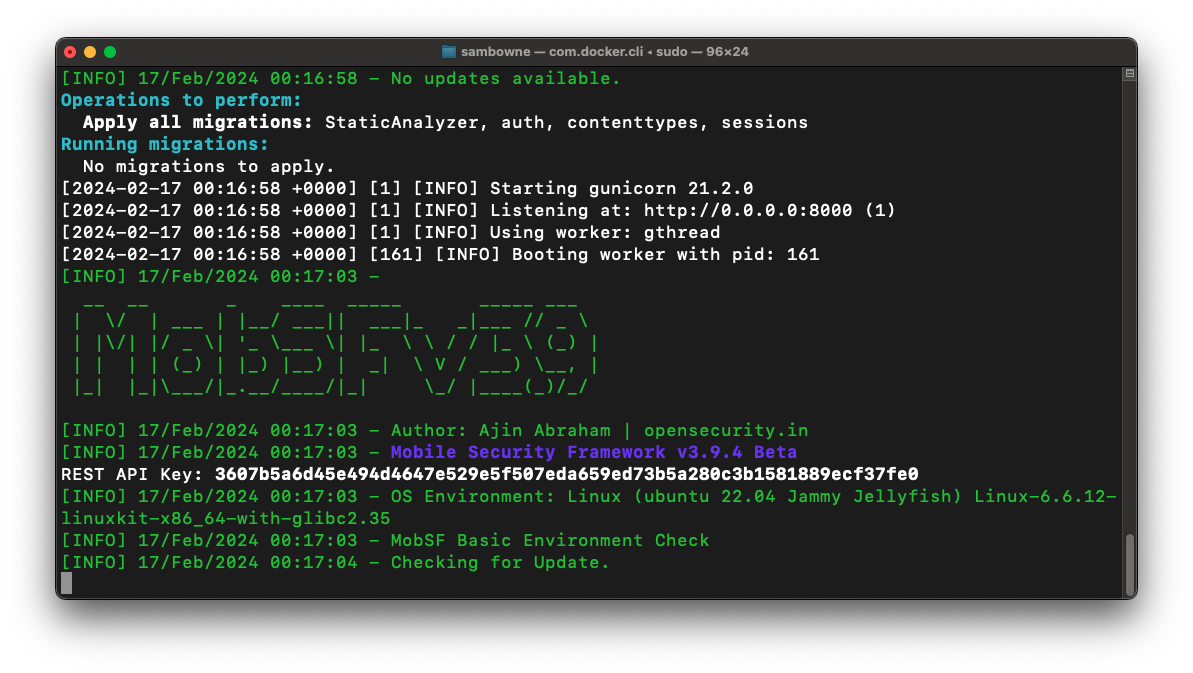
sudo docker run -it --rm -p 8000:8000 -p 1337:1337 \
-e MOBSF_ANALYZER_IDENTIFIER=192.168.60.110:5555 \
opensecurity/mobile-security-framework-mobsf:latest
http://127.0.0.1:8000
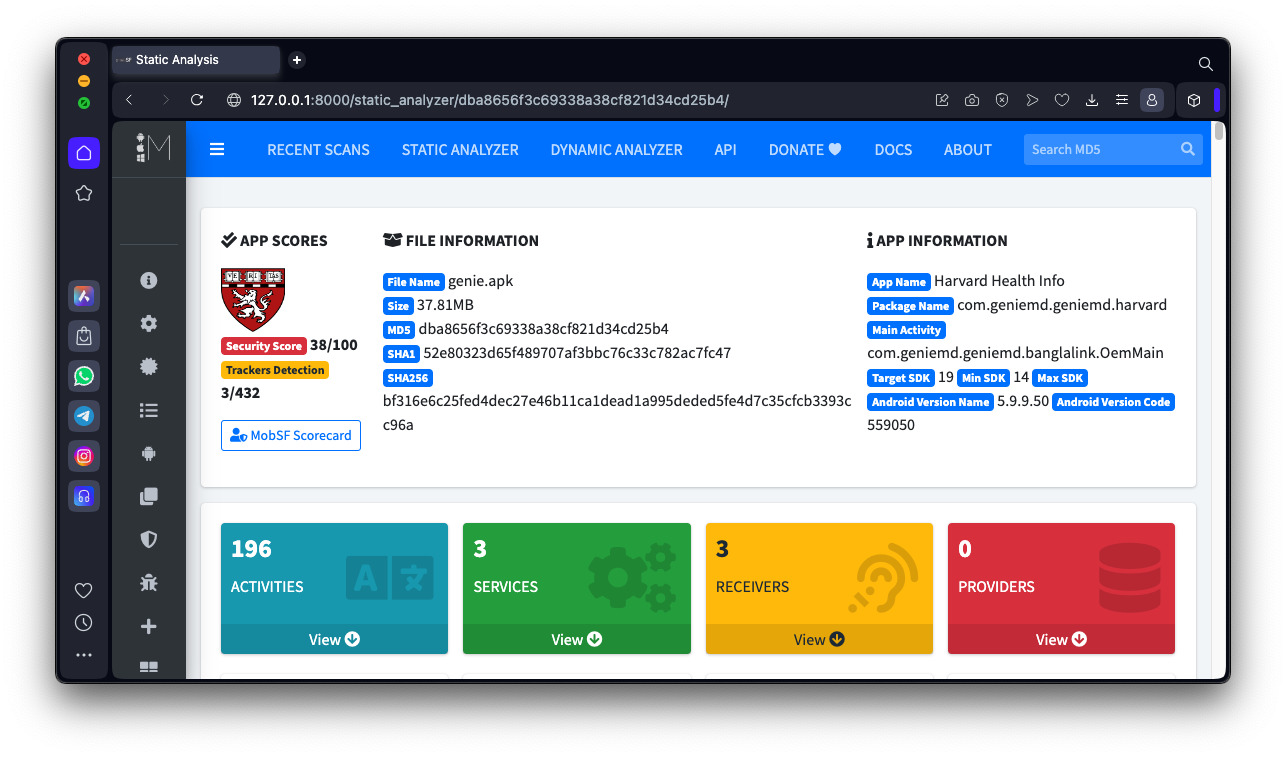
genie.apkDrag and drop the genie.apk file onto the MobSF Web page.
Wait while the MobSF analyzes the app.
When it finishes, you see a pretty display of the results, as shown below.
The MobSF Dynamic Analyzer page opens, as shown below.
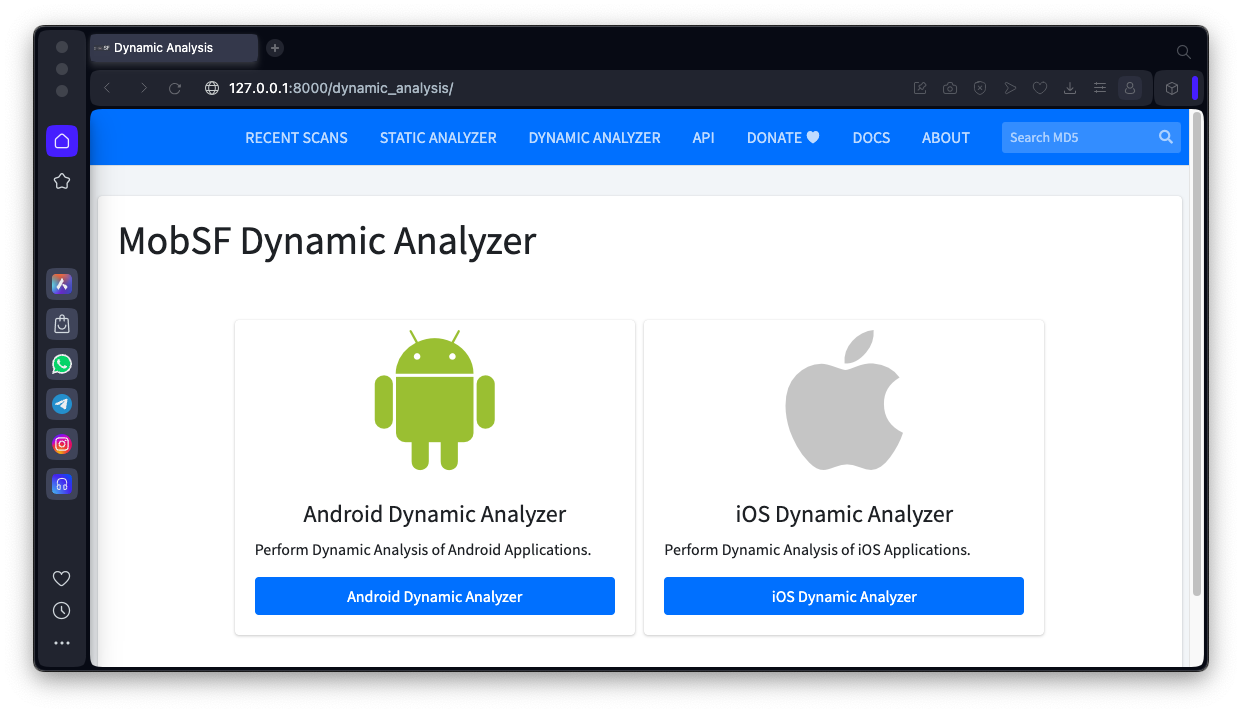
Click the "Android Dynamic Analyzer" button.
On the next page, at the bottom, find the "genie.apk" line. On the right side, click the "Start Dynamic Analysis" button, as shown below.
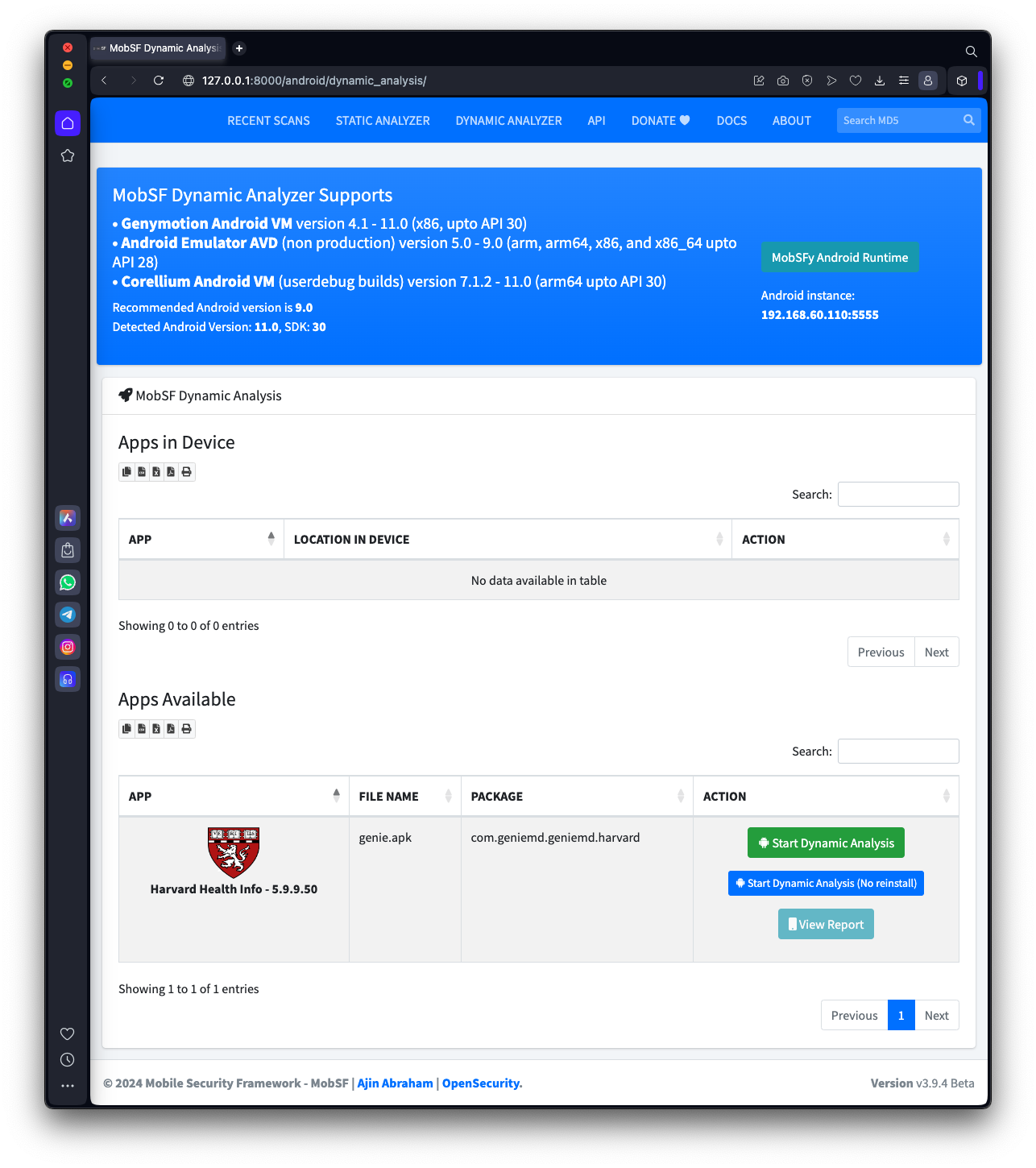
The Dynamic Analyzer page opens, as shown below.
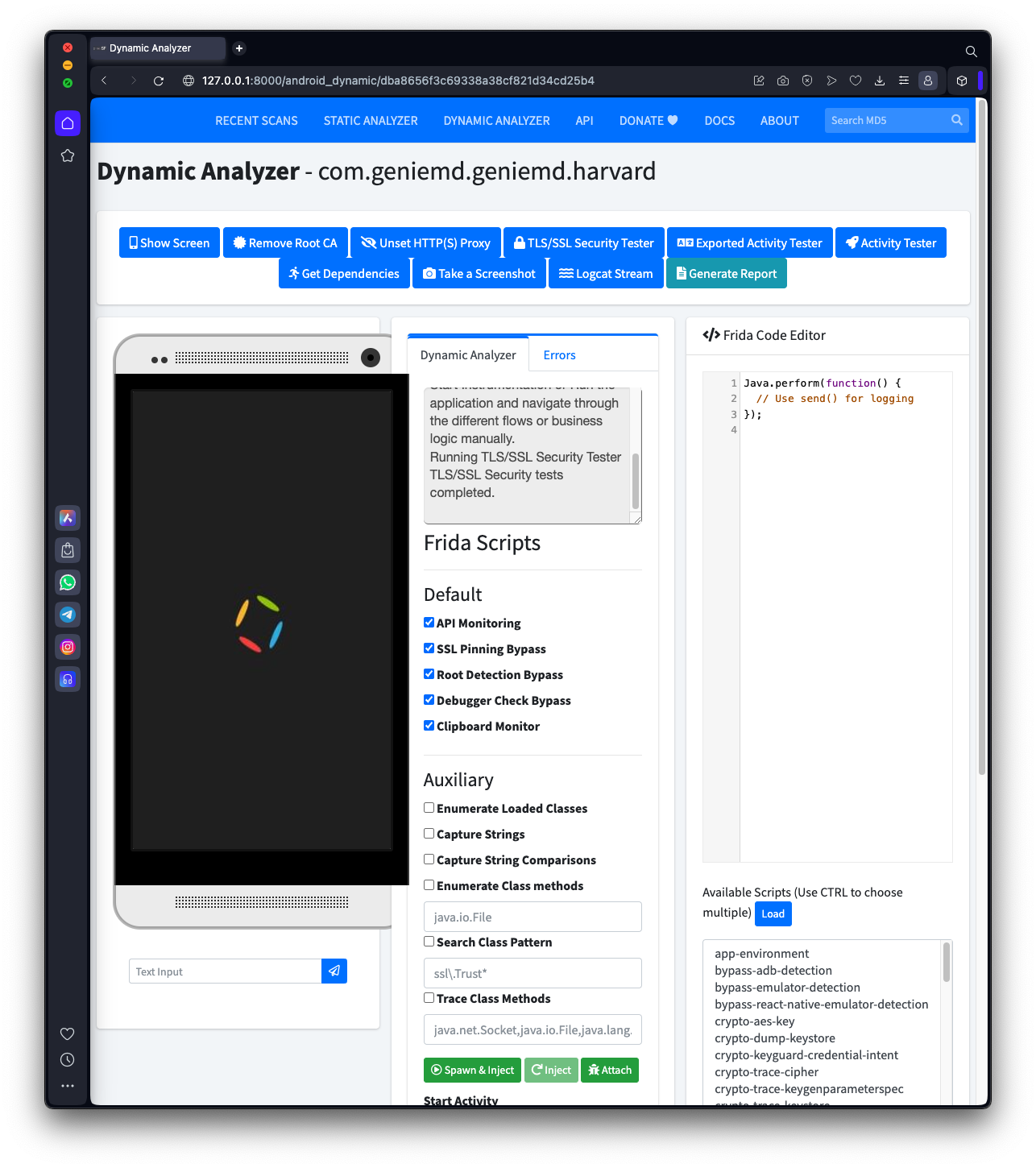
A page of instructions appears, as shown below.
Notice the NOTE line in the center: when the app is running, you need to enter fake credentials into the login screen and log in, to create network traffic.
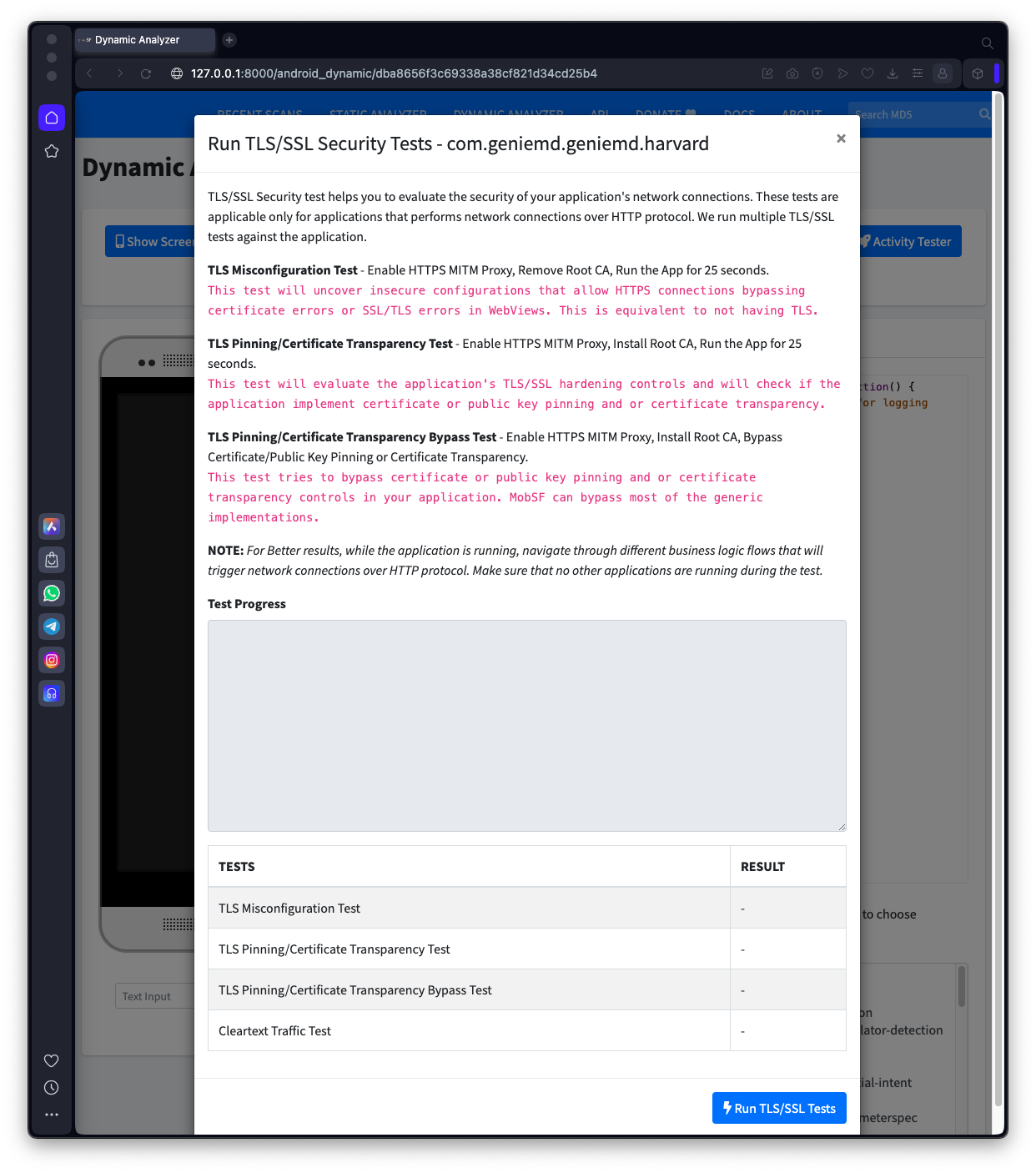
At the bottom, click the "Run TLS/SSL Tests" button.
The app launches in the Gennymotion emulator.
Approve the installation of the app and click through the introduction screen.
When you see a "Sign In" button, click it and attempt to log in with fake credentials.
The app will launch three times. Perform login attempts each time.
M 305.1: Test Results (10 pts)
In the the "Test Progress" box, find the text covered by a green box in the image below. That's the flag.
Look at the Android emulator. You will see several screens pop up.
When the test is done, you'll see the message "Exported Activity testing completed.", highlighted in the image below.
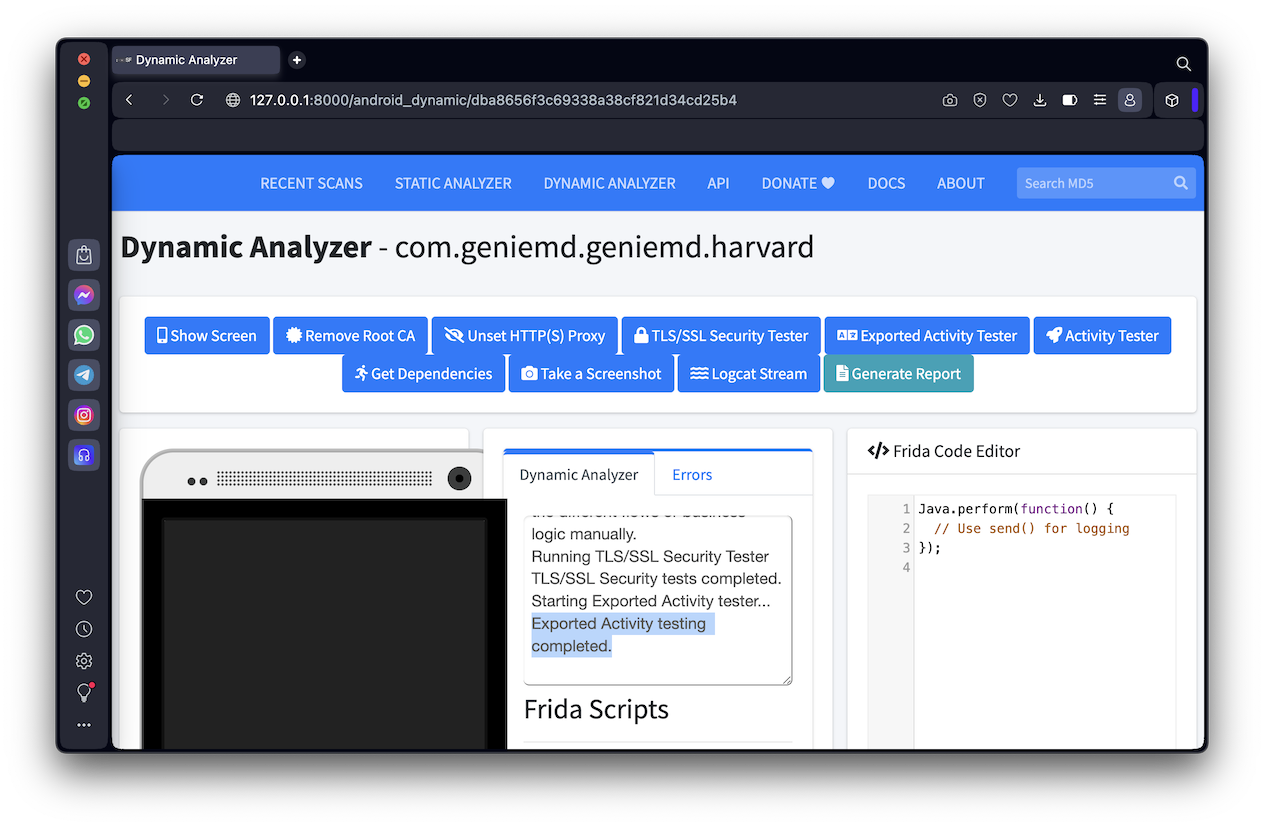
On the Dynamic Analyzer page, at the top, click the "Generate Report" button.
M 305.2: Exported Activity (5 pts)
Scroll down to find activity shown below.Find the text covered by a green box in the image below. That's the flag.
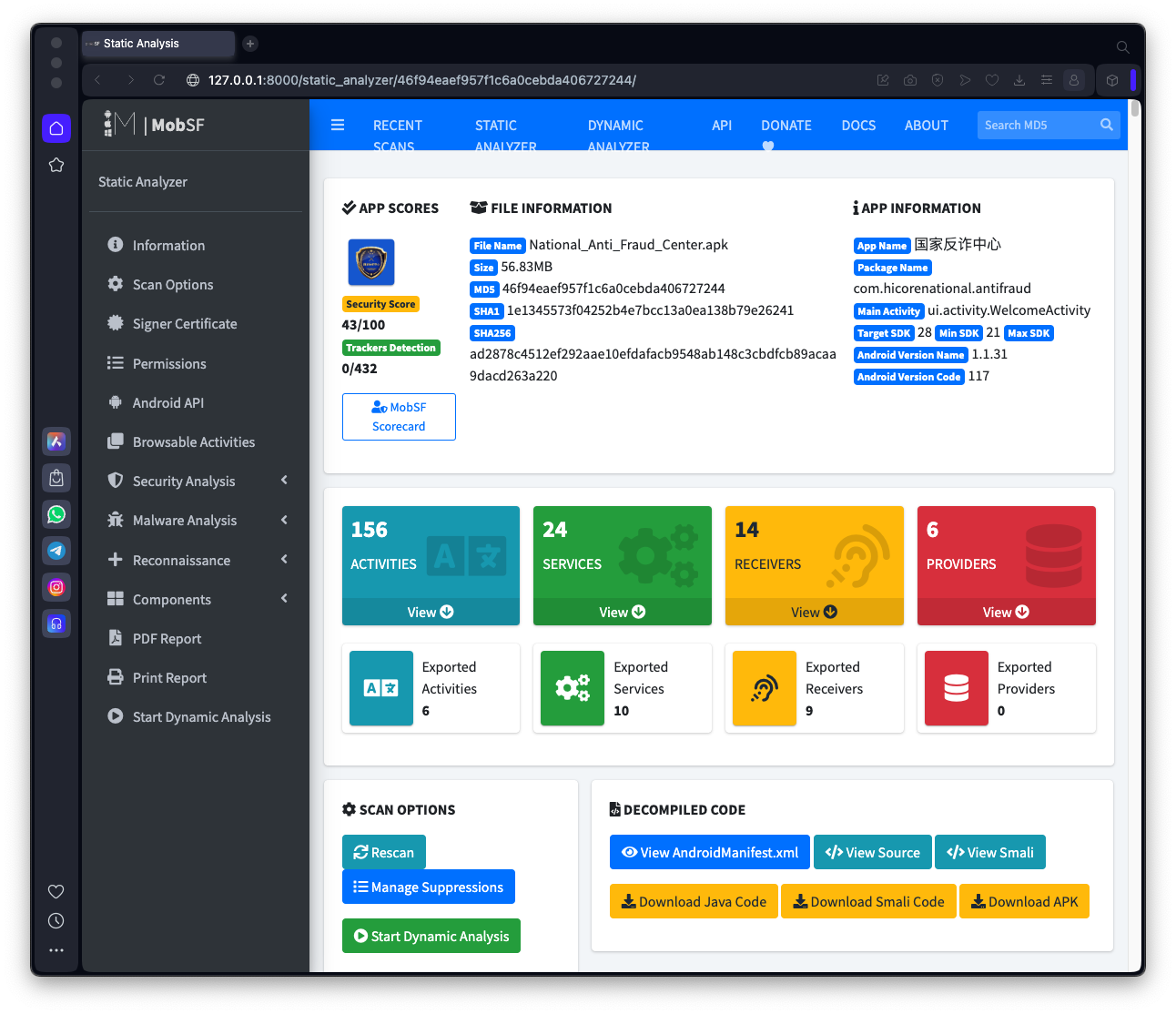
National_Anti_Fraud_Center.apkThe app is larger than the "genie" app, so the analysis will take longer. 3:36
In the DECOMPILED CODE section, click the "Download Java Code" button, as shown below.
M 305.3: HelloWorld (5 pts)
Unzip the file that you downloaded.Expand the folders. There are very few files in it, as shown below. One of them is a demonstration "heloworld" function, which is unprofessional to leave in a finished app.
Find the text covered by a green box in the image below. That's the flag.
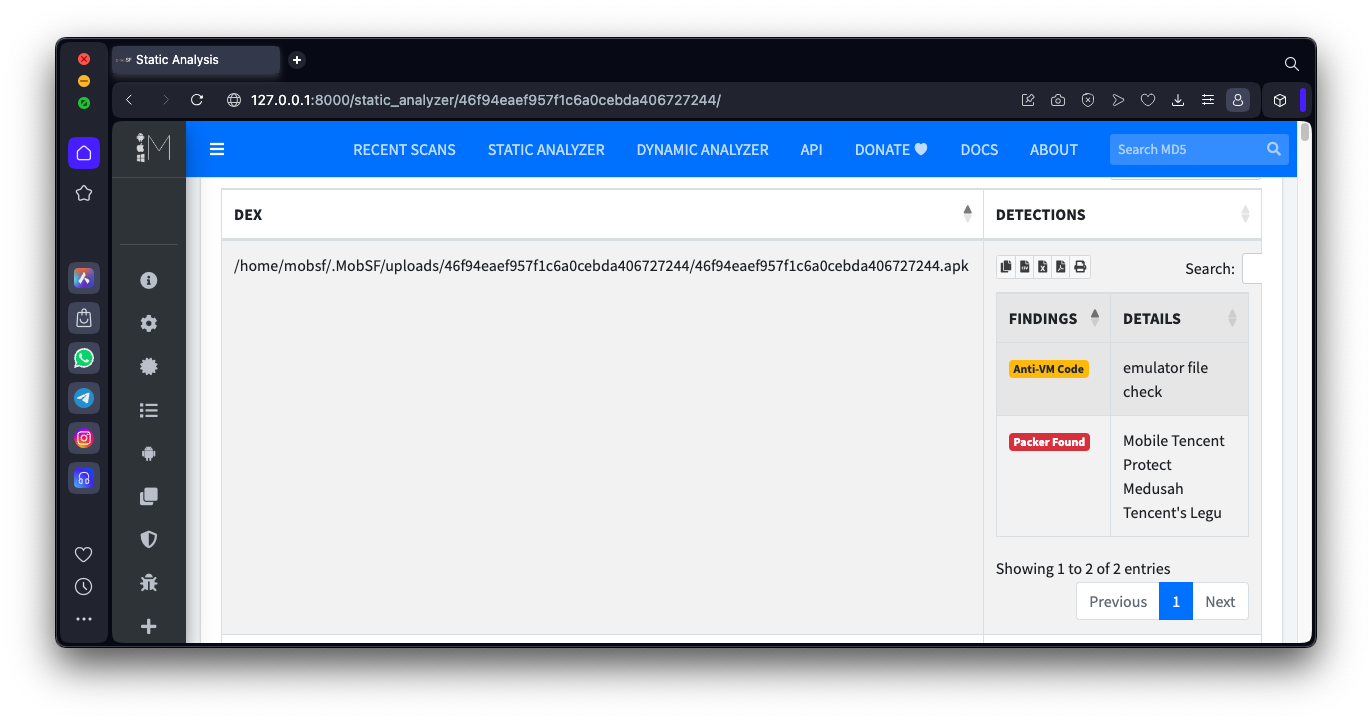
As shown below, MobSF identifies the
packer as:
Mobile Tencent Protect
To learn more about this app, we need to perform dynamic analysis.
Download the Genymotion-ARM-Translation_for_9.0.zip file from this page:
https://github.com/m9rco/Genymotion_ARM_Translation
Drag the the Genymotion-ARM-Translation_for_9.0.zip file onto your Genymotion Android device and drop it there.
A warning message pops up, as shown below. Click OK.
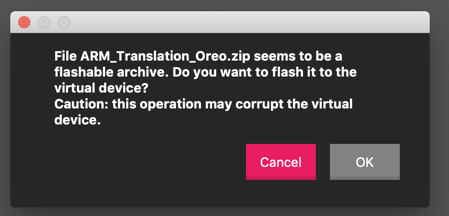
A message says the file was flashed successfully. Click "Restart Now".
Click the "Android Dynamic Analyzer" button.
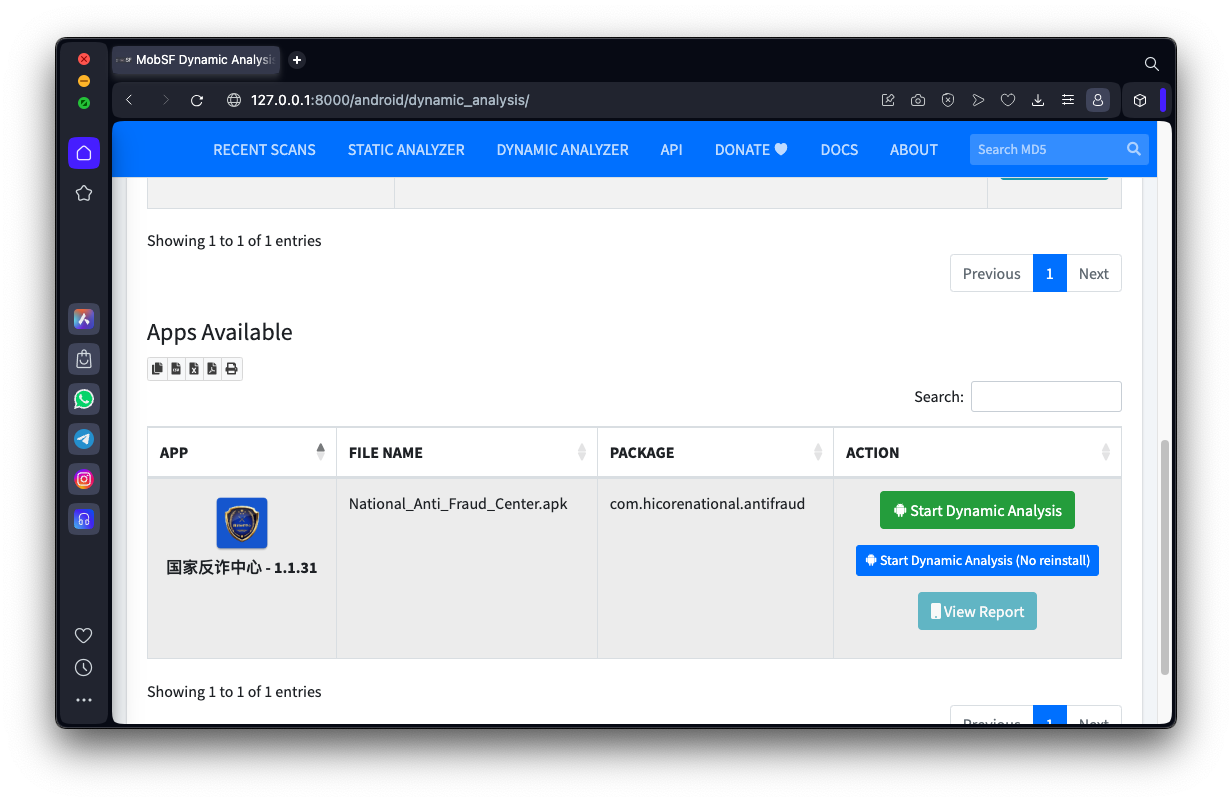
On the next page, at the bottom, find the "National_Anti_Fraud_Center.apk" line. On the right side, click the "Start Dynamic Analysis" button, as shown below.
The Dynamic Analyzer page appears, as shown below.
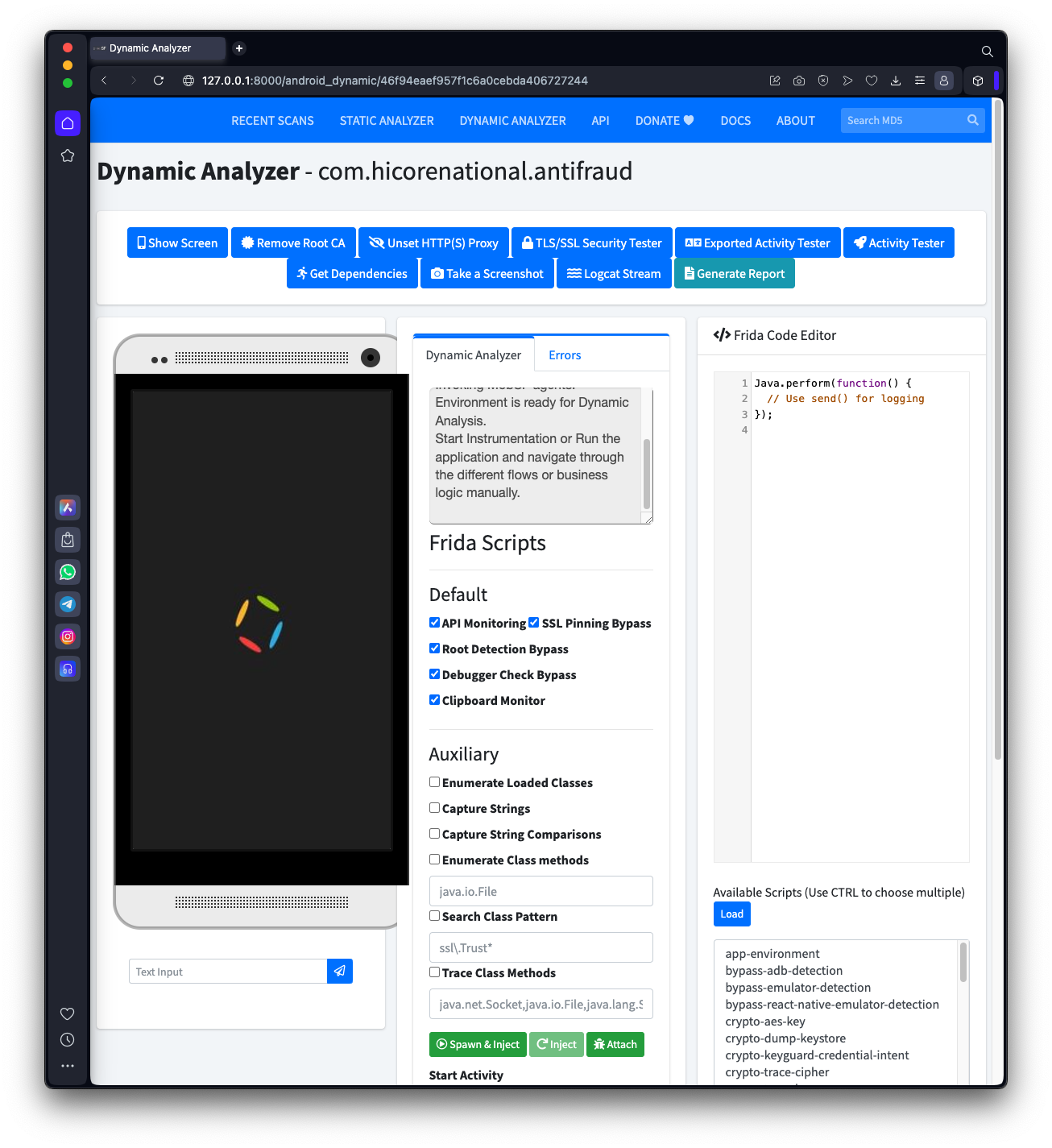
The app installs, and screens open and close on the emulator.
When you see messages asking for permissions, allow them.
If boxes pop up saying the app keeps stopping, click "Close app".
If boxes pop up saying the app has stopped, click "Open app again".
When the testing is completed, at the top, click the "Generate Report" button.
Scroll down to the ACTIVITY TESTER section to see screenshots of each activity, as shown below.
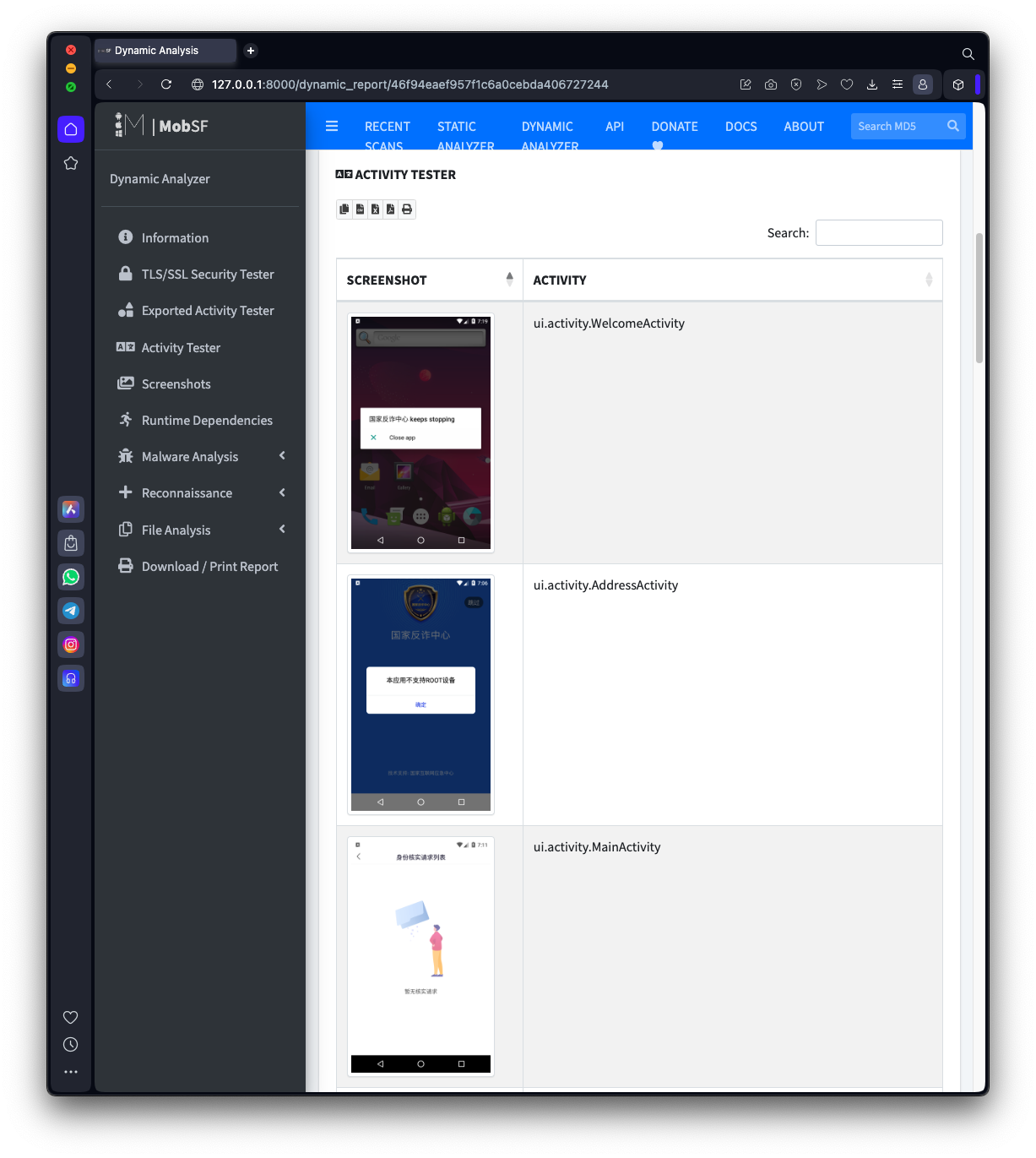
M 305.4: Activity Name (10 pts)
Find the activity shown below.Find the text covered by a green box in the image below. That's the flag.
M 305.5: Files (5 pts)
In the OTHER FILES section, find the file shown below.Find the text covered by a green box in the image below. That's the flag.
Posted 2-18-24