I recommend skipping this project.
https://samsclass.info/128/proj/genie.apk
Save the genie.apk file in your Downloads folder.https://www.vegabird.com/yaazhini/
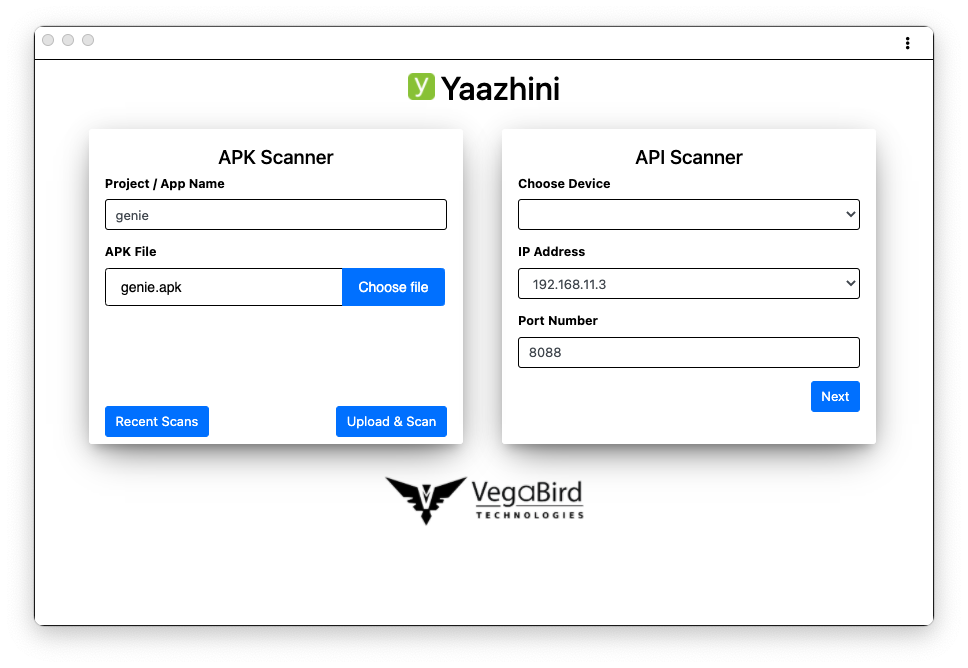
Download and install Yaazhini. On Debian, in a Terminal, execute these commands:To get around that, open Finder and go to Applications. Right-click Yaazhini and click Open.
Click the "Choose file" button. Navigate to the genie.apk file you downloaded and double-click it.
Click the "Upload & Scan" button.

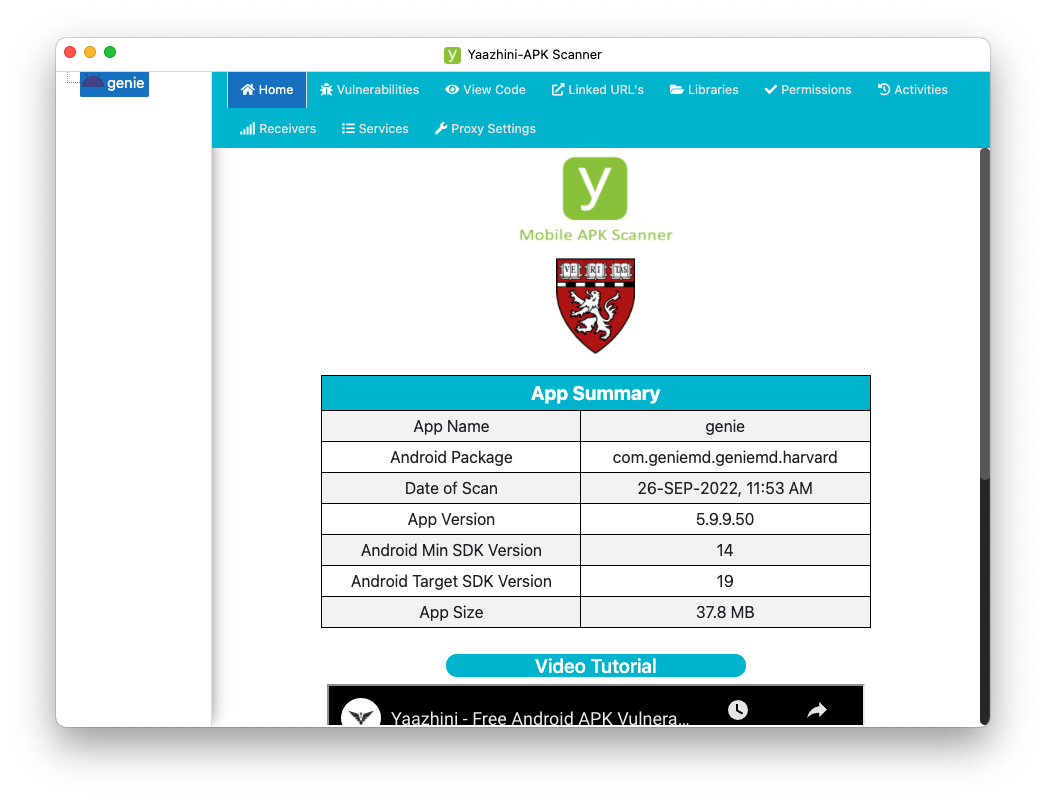
When the scan finishes, a page opens with a summary, as shown below.
M 303.1: Man in the Middle Attack (10 pts)
At the top, click the Vulnerabilities tab.Expand the High object and the "Man in the middle attack" object.
Double-click CryptoHttpClient.java(1).
The vulnerability description appears in the lower pane.
Find the text covered by a green box in the image below. That's the flag.
M 303.2: ECB Mode (5 pts)
In the Medium section, find the vulnerability shown below.Find the text covered by a green box in the image below. That's the flag.
Posted 9-26-22
Warning added 10-22-22