In a Web browser, go to https://portswigger.net/burp
In the "Community Edition" column, click Download", as shown below.

Install the software with the default options.
Click Start, "Burp Suite Community Edition".
An agreement appears. Click "I Accept".
In the next page, click the Start Burp button.
The main Burp window opens, as shown below.
Click the Proxy tab. Click the Intercept sub-tab.
The third button says "Intercept is on", as shown below.
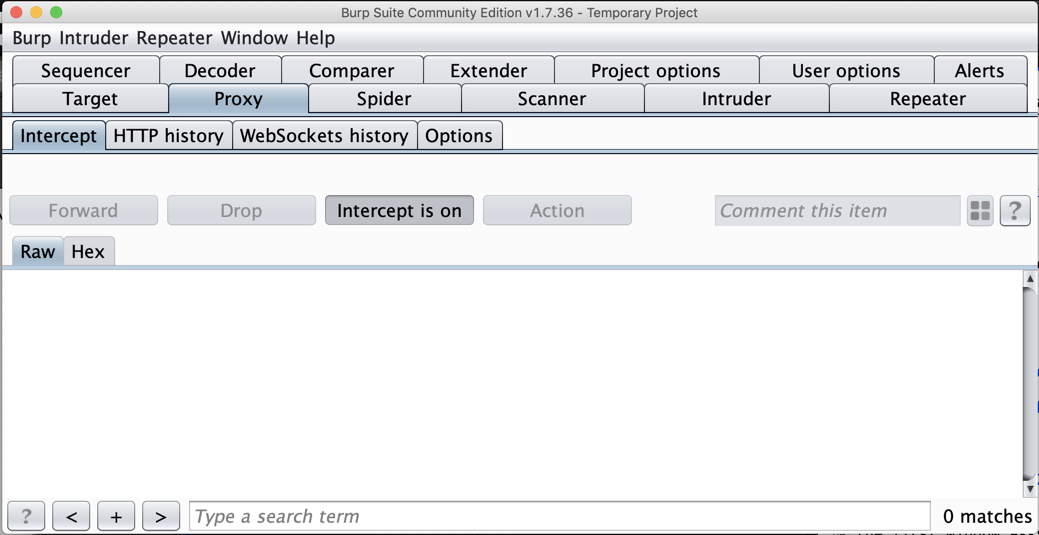
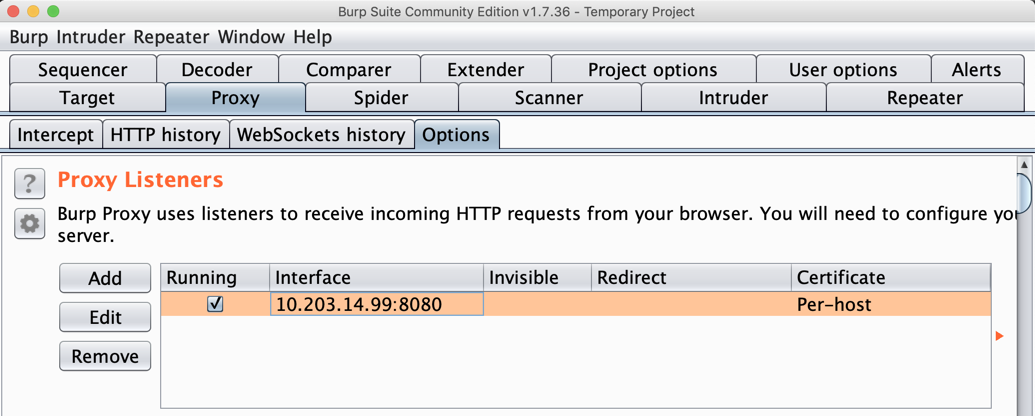
On the Proxy tab, click the Options sub-tab.
In the central box, click the Interface address to highlight it, as shown below.
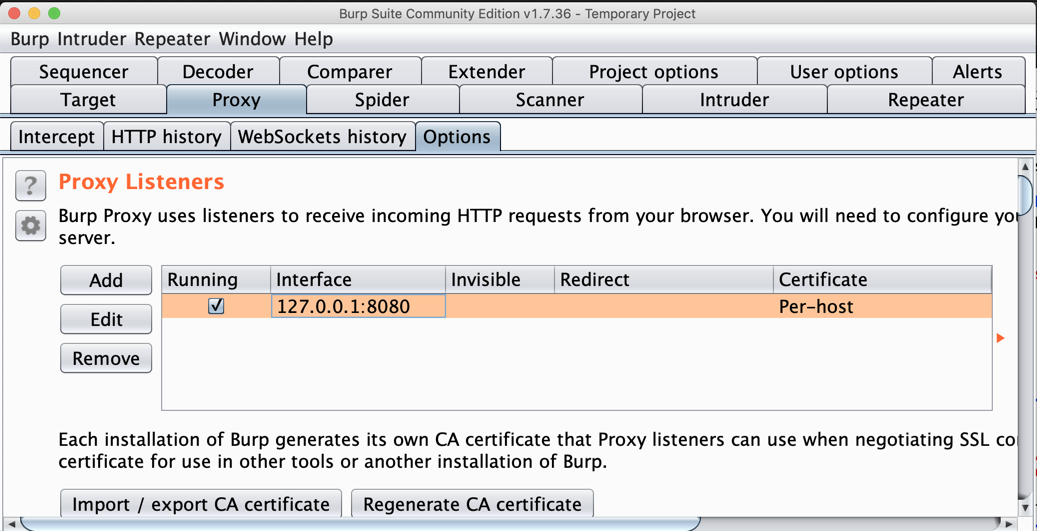
On the left side, click the Edit button.
In the "Edit proxy listener" box, click the "Specific address" button, and select your computer's IP address that is used to connect to the Internet, as shown below.
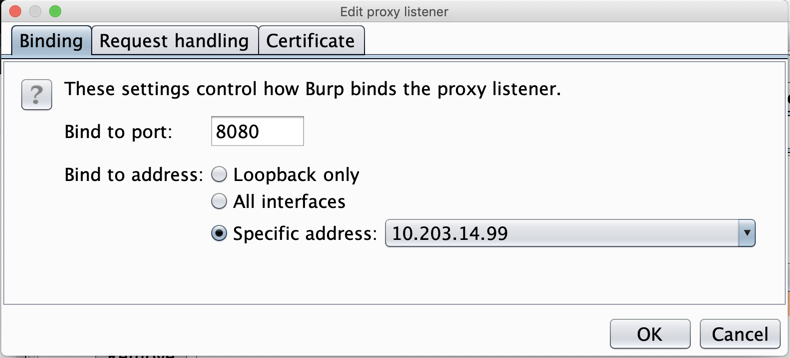
Click OK.
Burp shows a proxy listener on your IP address and port 8080, as shown below.
Make a note of this address--you will need it below.
Download and install the Nox emulator. When it launches, click "Skip Tutorial".
Click OK.
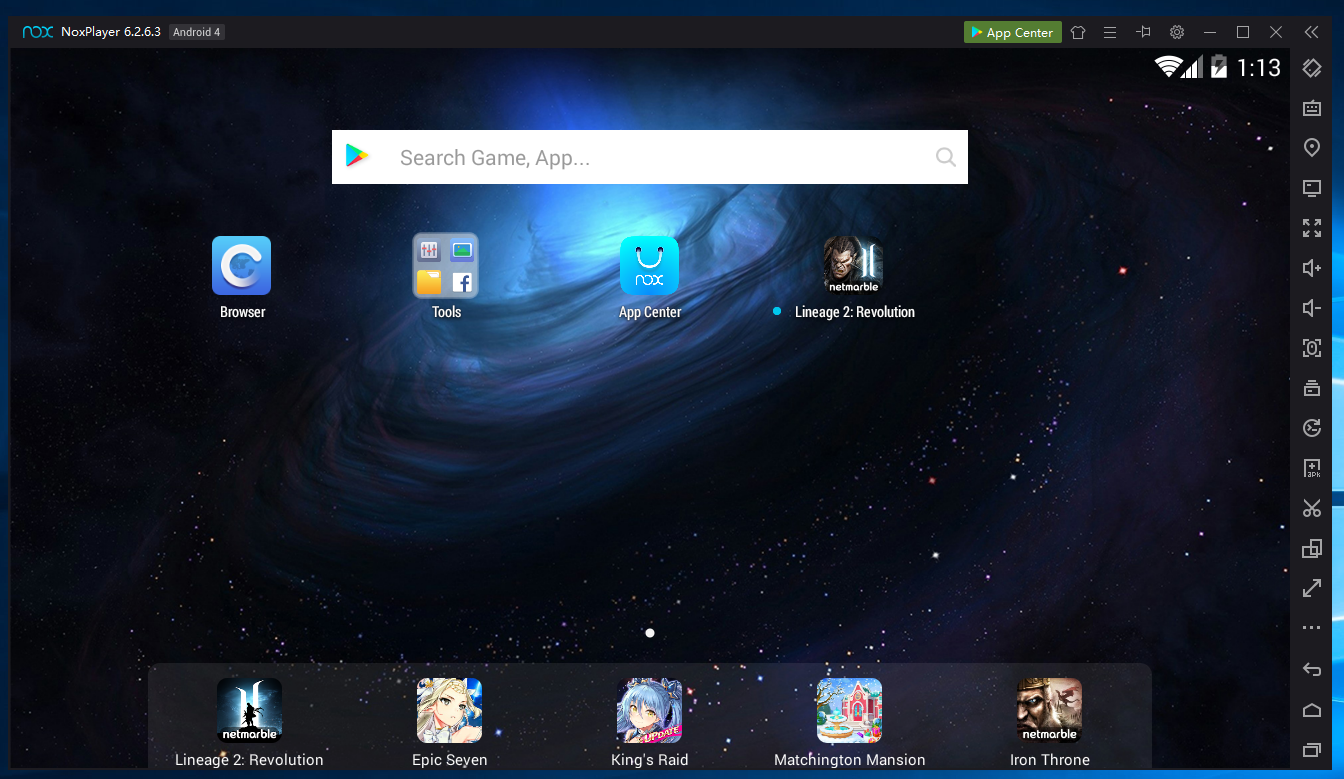
Nox launches, as shown below.

On the lower right, in the black bar of icons, click the second icon from the bottom, which is shaped like an envelope.
The Nox home page opens, as shown below.
On the Nox home page, click Tools.
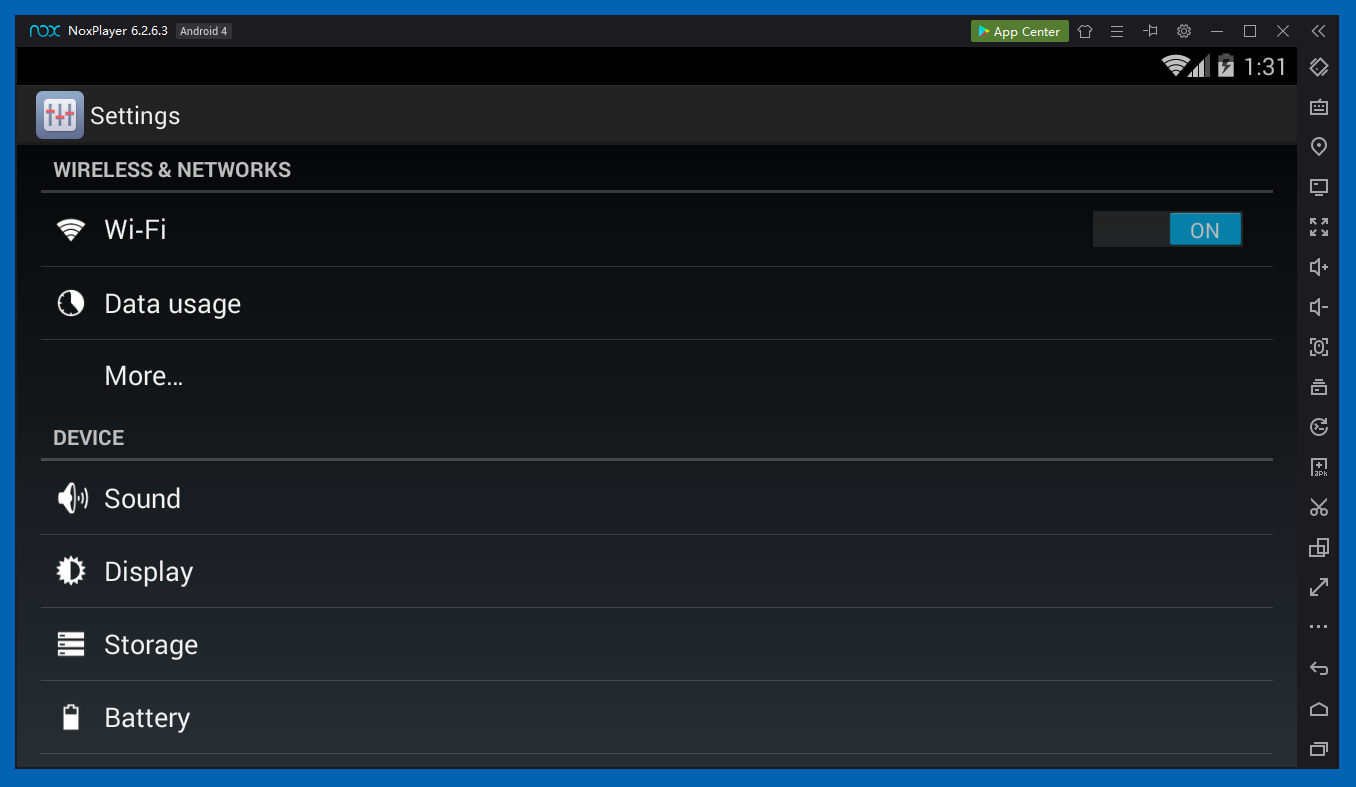
Click Settings.
In Settings, click Wi-Fi, as shown below.
On the next screen, point to WiredSSD. Press and hold down the left mouse button.
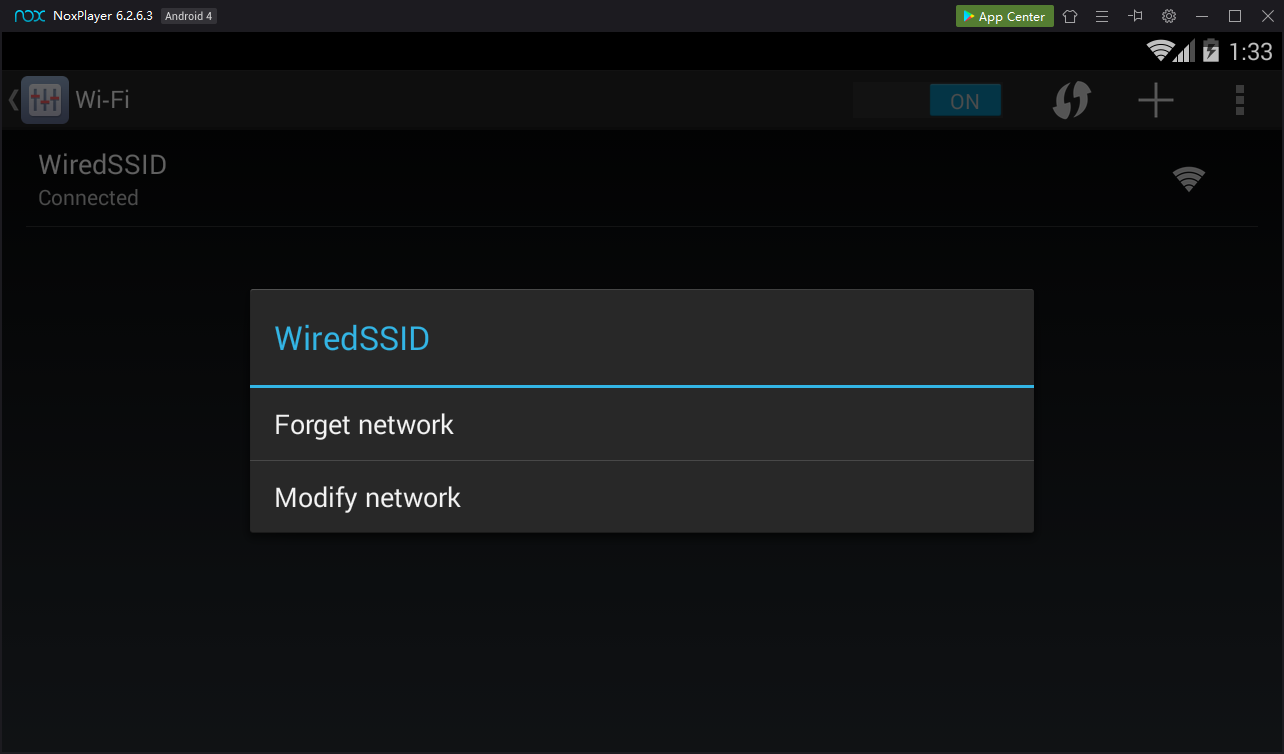
A "WiredSSD" box pops up, as shown below.
Click "Modify network".
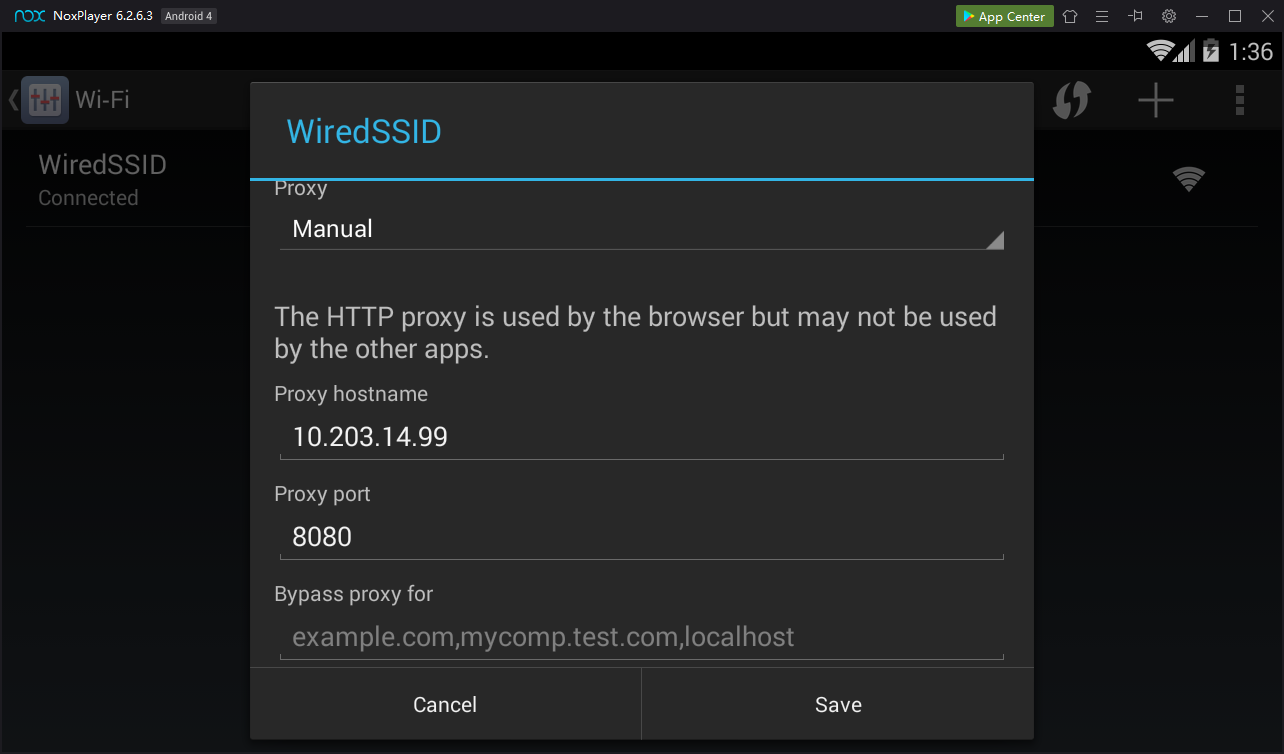
In the "WiredSSD" box, click the "Show advanced options" box.
Scroll down and set the Proxy type to Manual.
Enter the IP address you set in Burp above, and a port of 8080, as shown below.
Click Save.
On the Nox home page, at the top left, click Browser.
A "Security warning" box pops up, as shown below.
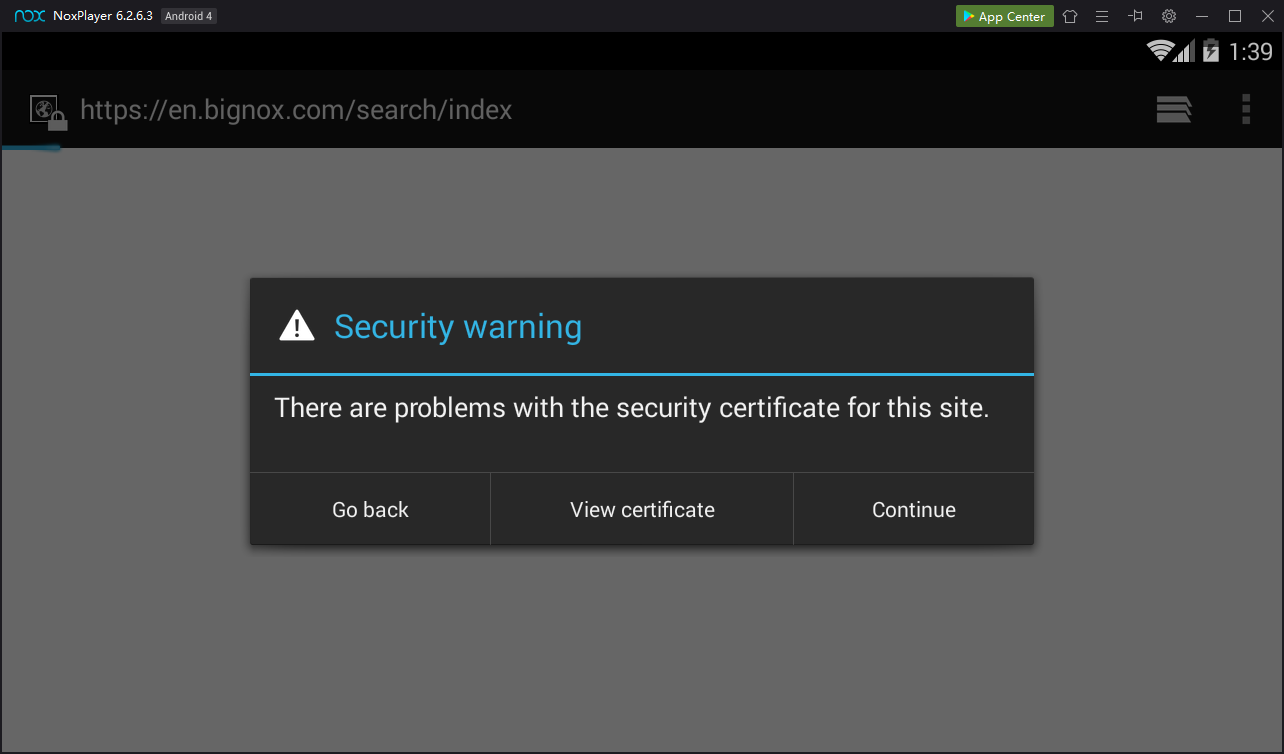
This is good! Burp is performing a man-in-the-middle attack and the Android browser is detecting it.
In the "Security warning" box, click Continue as many times as necessary, to get the boxes out of the way.
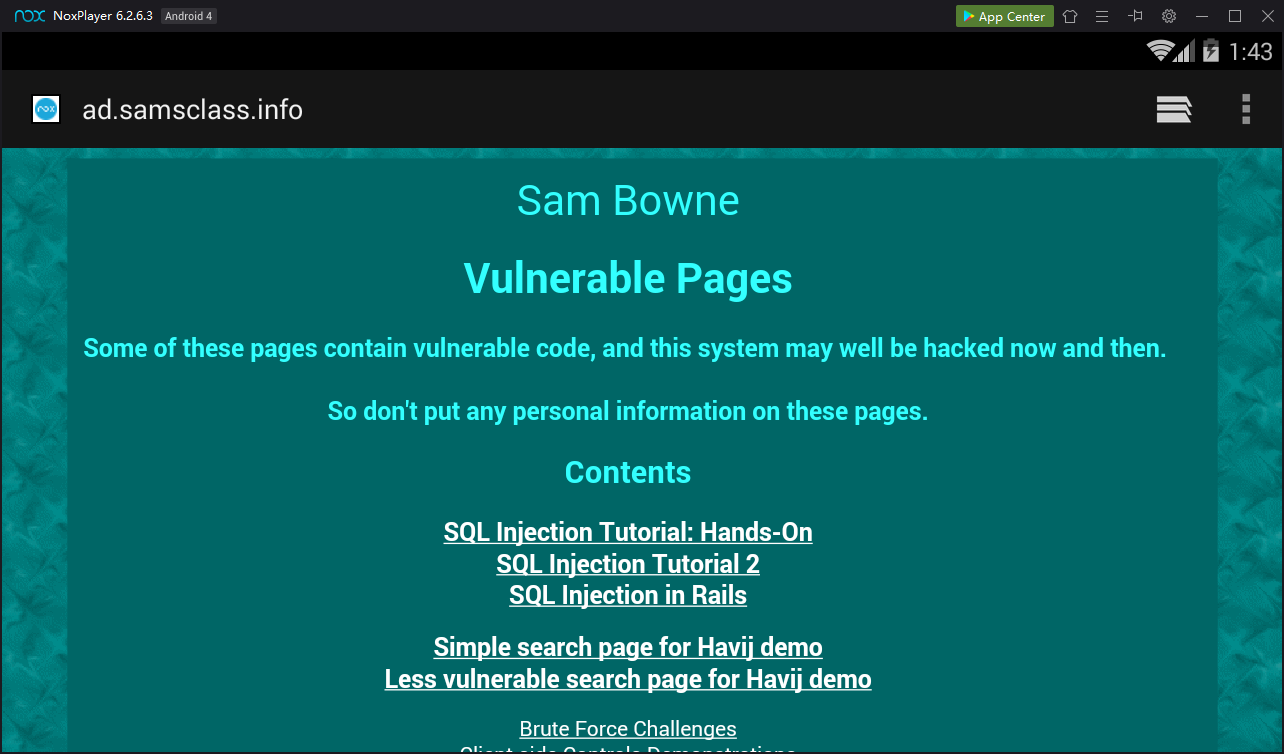
When you can get to the address bar, enter this address:
A web page opens, as shown below.
Scroll down and find traffic to ad.samsclass.info as shown below.
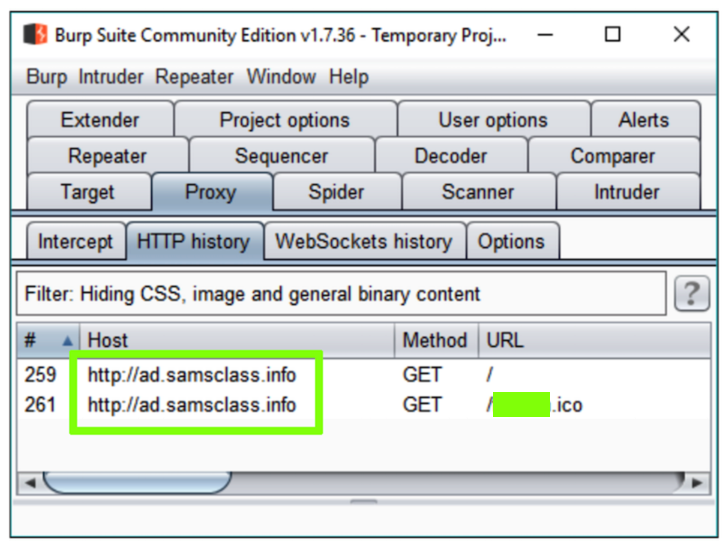
Find the text covered by a green box in the image above. Enter it into the form below to record your success.