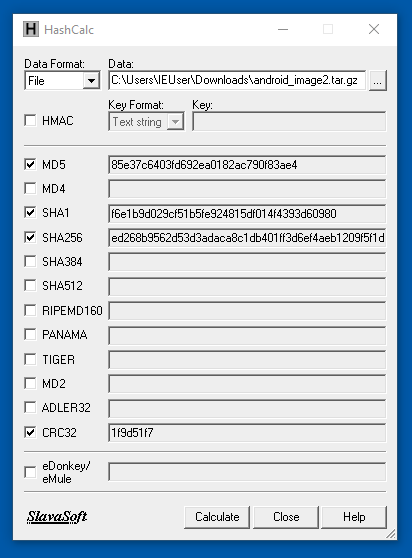
Hashcalc is no longer available, but you can calculate hashes with Powershell like this:
Get-FileHash -Algorithm SHA1 android_image2.tar.gz

Put the android_image2.tar.gz file on your Windows desktop.
Right-click the android_image2.tar.gz file and click 7-Zip, "Extract Here".
A data folder appears on your desktop.
If 7-Zip shows some messages saying "Can not create symbolic link", just ignore them and click Close.
Enter a Case Name of Android2.
Click the Next button.
Click the Finish button.
At step 2. Select Data Source Type, click "Logical Files".
Click the Next button.
At step 3. Select Data Source, click the Add button. Navigate to your desktop. Click the data folder and click Select.
Click the Next button.
At step 4. Configure Ingest, clear all the boxes except "Android Analyzer (aLEAPP)", as shown below.
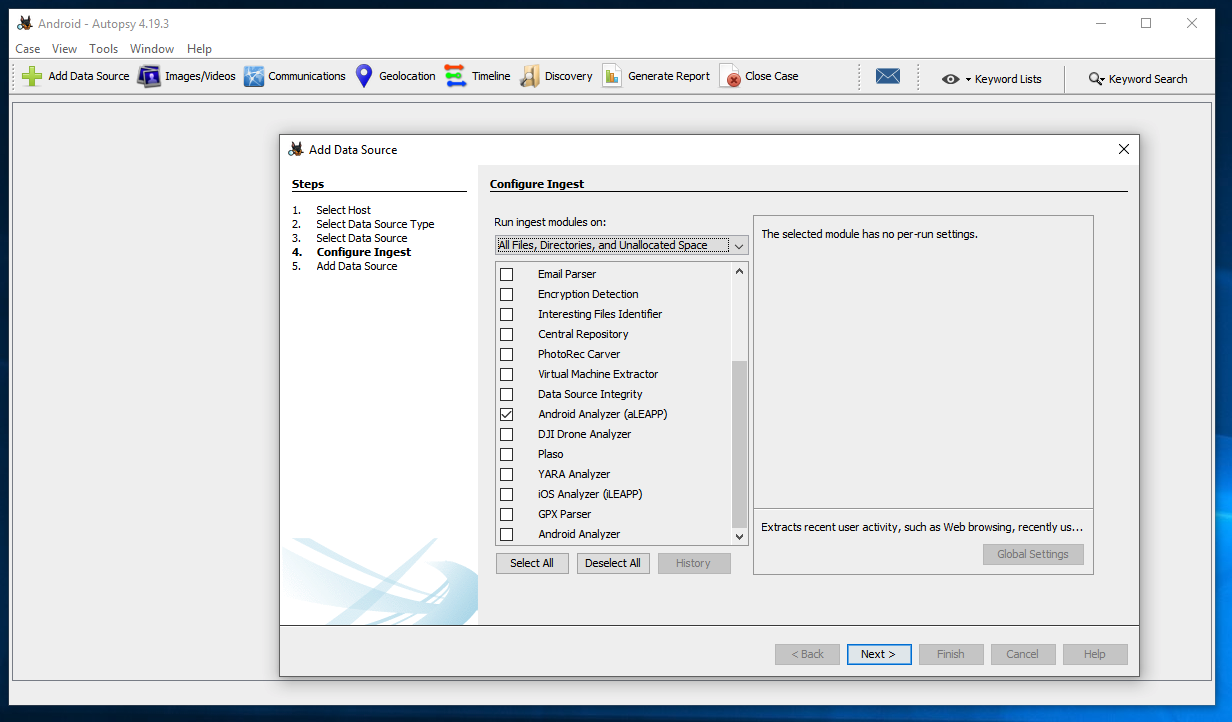
Click the Next button.
At step 5. Add Data Source, click the Finish button.
M 144.1: Newest App (5 pts)
What is the most recently installed app? That program name is the flag.
M 144.2: Website (5 pts)
What website was viewed at 14:52:39 PDT on Oct 8, 2022? That URL is the flag.
http://sleuthkit.org/autopsy/docs/user-docs/4.18.0/aleapp_page.html
Posted 10-7-22
Hash value and unzipping instructions updated 10-16-22
Video added 4-3-23
Fixed download size, hashcalc link 7-15-23
Unzipping to get hash value explained more 10-6-25