M 105: Plaintext Login (15 pts)
What You Need for This Project
- An Android Emulator with Google Play
Purpose
To observe network transmissions from
an insecure app, and prove that they
are not encrypted properly.
Background
This problem is gaining recognition, so few
apps still have this flaw.
The app below used plaintext network transmission
on Mar 26, 2021, but eventually it may
be fixed or removed.
<
Installing a Vulnerable App
This App is no longer available in Google Play,
as of August, 2022, so we'll use an archived
APK file.
Download this APK file:
traveler.apk
Drag and drop that file onto your Android Emulator
to install the app.
Starting Wireshark
On your host system, launch Wireshark.
If you don't have it, get it at:
https://www.wireshark.org/
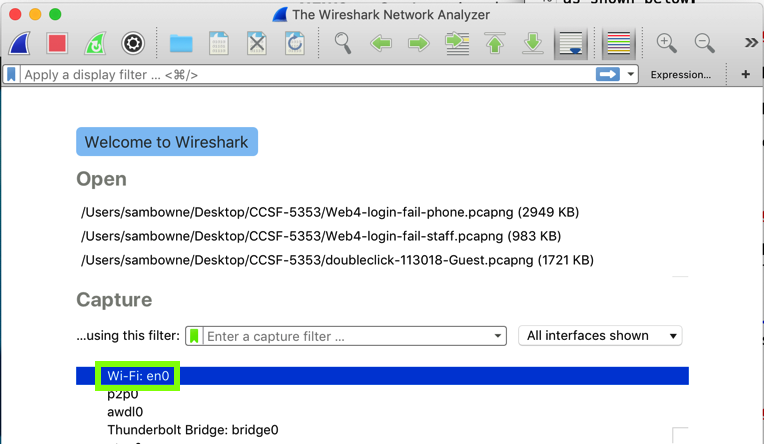
In the main Wireshark window, double-click the
network interface that is being used to reach
the Internet. On my system, it is "Wi-Fi: en0",
outlined in green in the image below.
Wirehark starts displaying packets.
At the top, in the Filter bar, enter this
display filter:
http
Press Enter to filter the traffic.
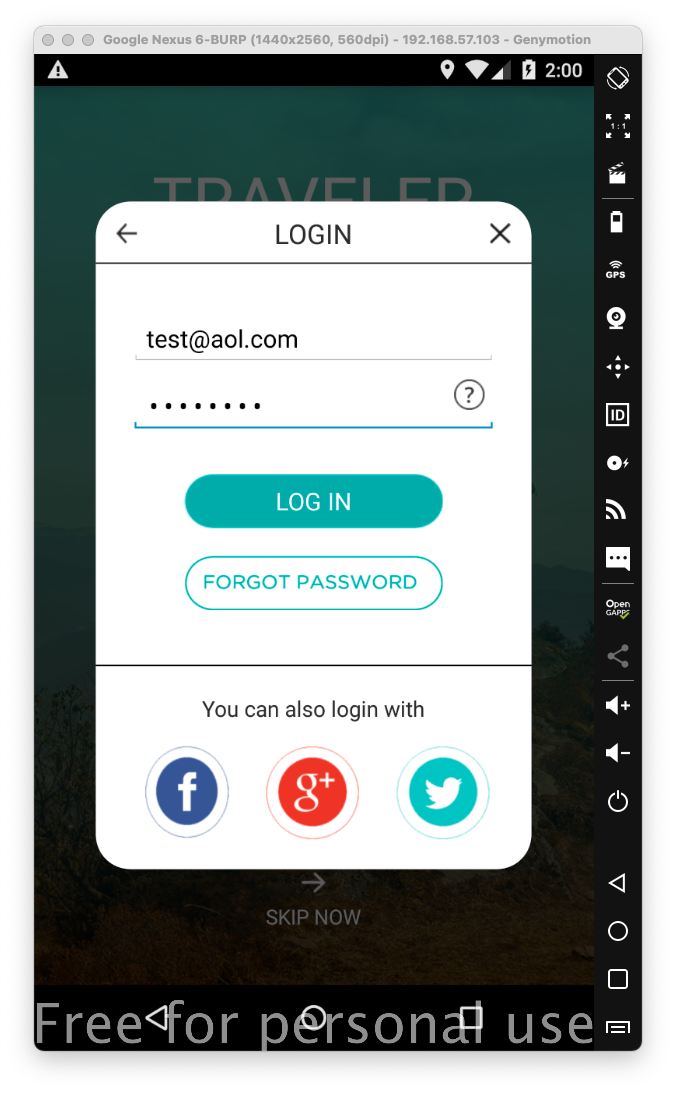
On your Android device,
in the vulnerable app,
enter any email and password into the login
page,
as shown below.
Wireshark shows a GET request to
/Webservice/user_login.ashx.
Click that line and expand the
"Hypertext Transfer Protocol item
in the lower pane,
as shown below.
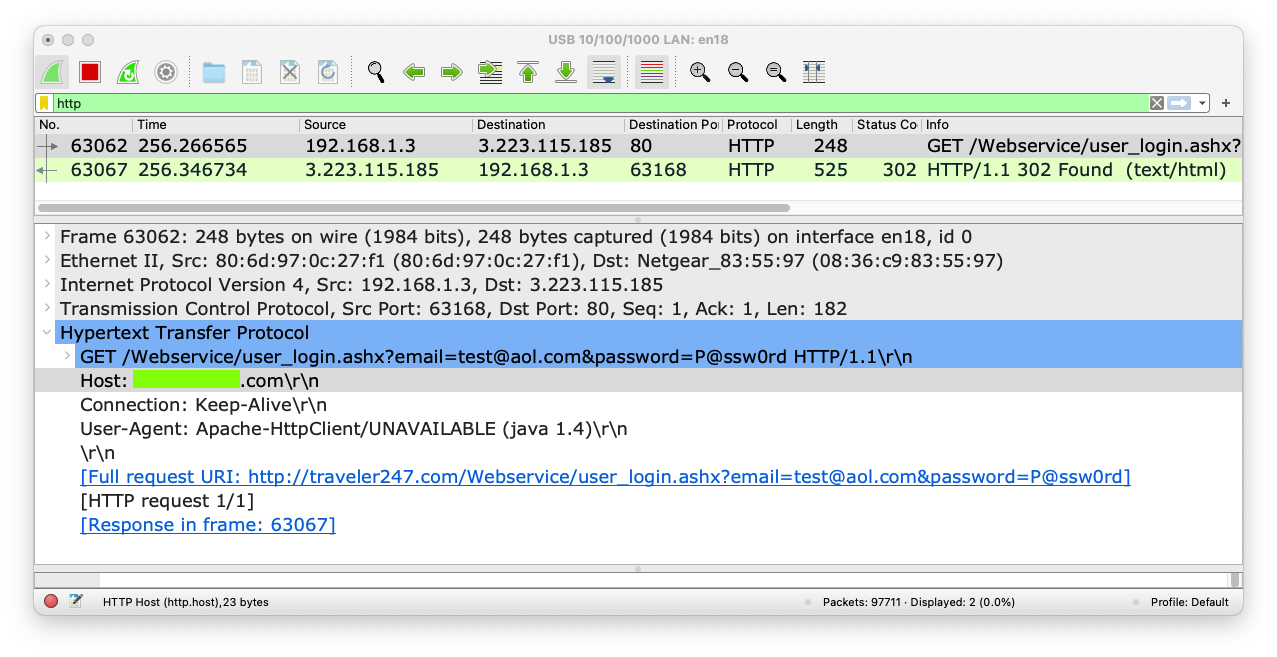
M 105.1: Host (15 pts)
Find the text covered by a green box
in the image above. That's the flag.
|
Responsible Disclosure
I notified the developer
in 2017.
Converted to a CTF 2-28-19
Wireshark image fixed 1-29-2020
Updated 1-20-21
Updated to use Traveler app 3-26-2021
Google Play instructions removed 8-29-22
APK download link fixed 8-30-22



