
For Ubuntu Linux users, in a Terminal, execute these commands:
cd
cd Android/Sdk/platform-tools
./adb devices -l
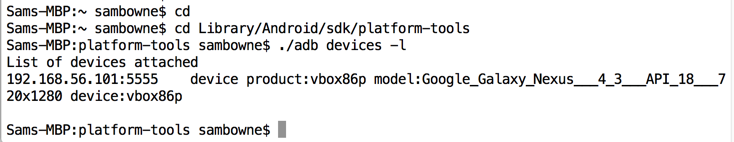
cd
cd Library/Android/sdk/platform-tools
./adb devices -l
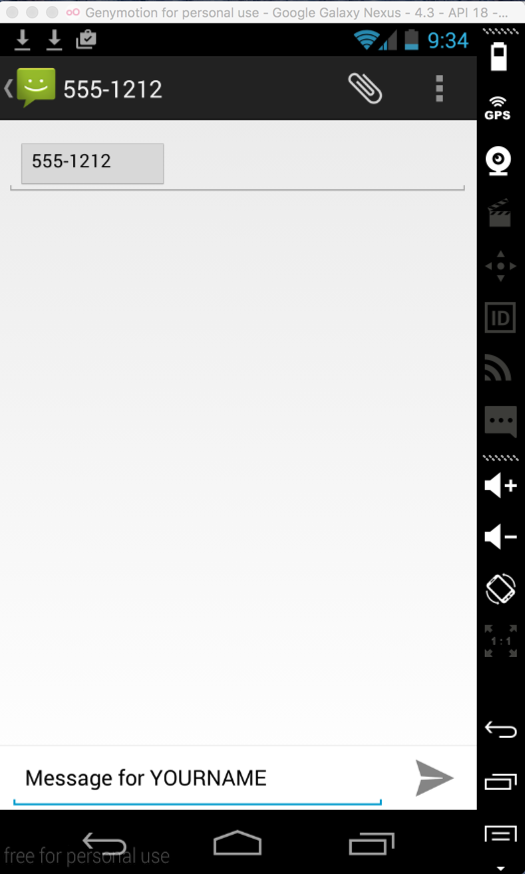
At the lower right, click the arrow icon to send your message.
In the bottom center, click the icon shaped like an open business envelope. This takes you back to the home screen.
At the bottom of the screen, click the blue Earth to open a Web browser. Go to samsclass.info and kittenwar.com
./adb shell
mount
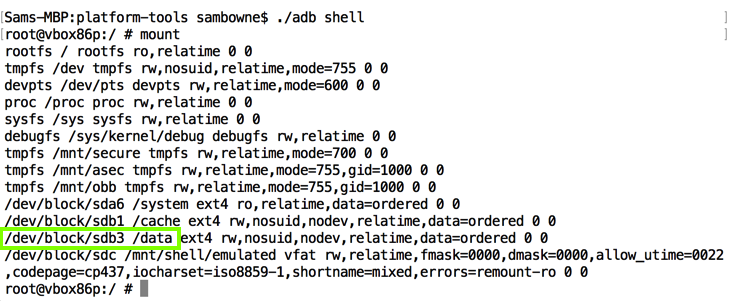
The /data partition is at /dev/block/sdb3, as highlighted in the image above.
Execute this command:
df
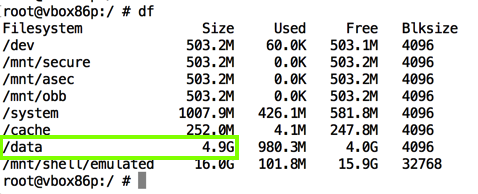
The /data partition is where apps store their data; the main place to find forensic artifacts.
For Ubuntu Linux users, in a Terminal, execute these commands:
cd
cd Android/Sdk/platform-tools
./adb forward tcp:7000 tcp:7000
cd
cd Library/Android/sdk/platform-tools
./adb forward tcp:7000 tcp:7000
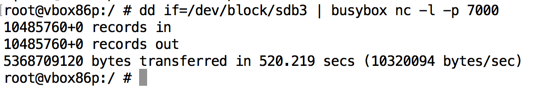
dd if=/dev/block/sdb3 | busybox nc -l -p 7000

Open a new Terminal window and execute this command:
nc 127.0.0.1 7000 > /tmp/p14-YOURNAME.dd
ls -lh /tmp/p*
When the process completes, you'll see the number of bytes transferred, as shown below.
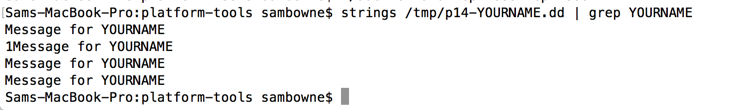
strings /tmp/p14-YOURNAME.dd | grep YOURNAME
Execute this command to see evidence about kittenwar:
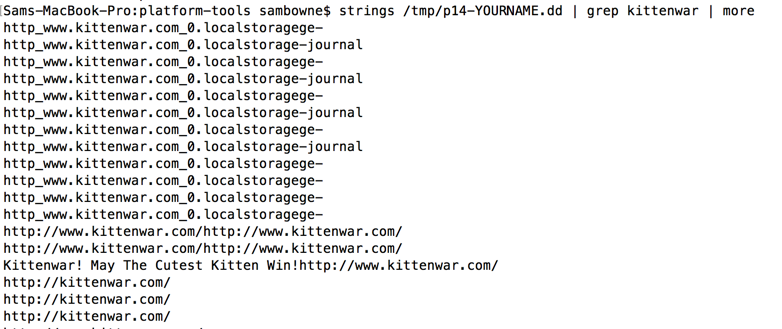
strings /tmp/p14-YOURNAME.dd | grep kittenwar | more
Execute this command to see evidence about samsclass:
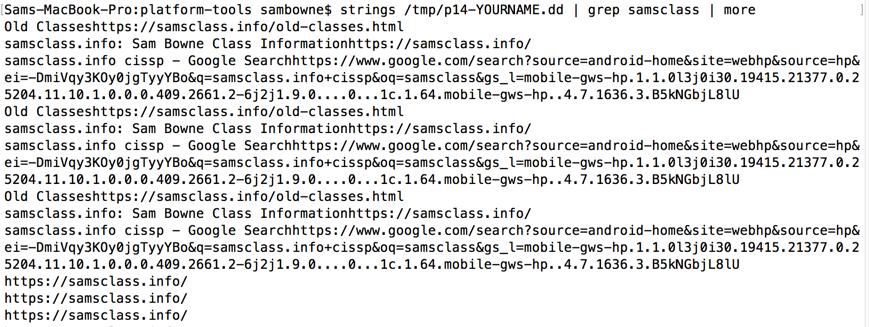
strings /tmp/p14-YOURNAME.dd | grep samsclass | more
Review of Android Partition Layout
DD over Netcat for a Cheap Ghost Alternative
Android Forensics, Part 1: How we recovered (supposedly) erased data
Live imaging an Android device | Free Android Forensics (from 2014)
http://virtualboxes.org/images/android-x86/