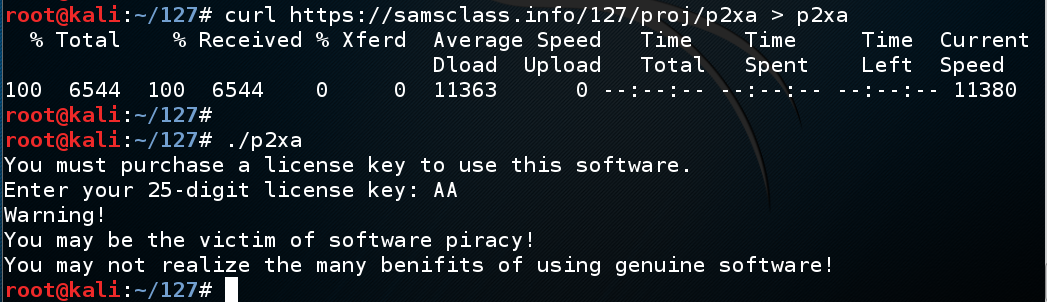
Enter AA as the product key. The key is rejected, as shown below.curl https://samsclass.info/127/proj/p2xa.c > p2xa.c curl https://samsclass.info/127/proj/p2xa > p2xa chmod a+x p2xa ./p2xa

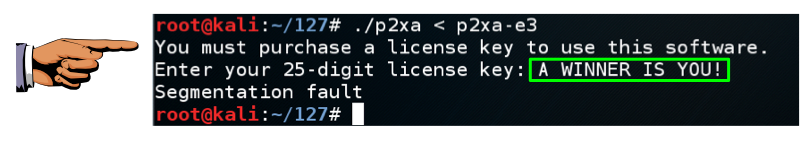
Hack past the product activation, to reveal the message "A WINNER IS YOU!" message, as shown below.
Hint: this executable was compiled with symbols, so you can use the "list" command in gdb to see the source code.
Press the PrintScrn key to copy the whole desktop to the clipboard.
YOU MUST SUBMIT A FULL-SCREEN IMAGE FOR FULL CREDIT!
Paste the image into Paint.
Save the document with the filename "YOUR NAME Proj 2xa", replacing "YOUR NAME" with your real name.
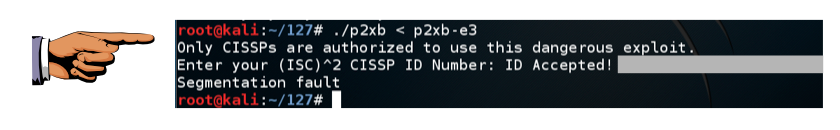
Enter AA as a CISSP ID. The ID is rejected.curl https://samsclass.info/127/proj/p2xb > p2xb chmod a+x p2xb ./p2xb
Hack in to reveal the secret message, redacted in the image below.
Hints: this executable was compiled without symbols, so you cannot see the source code. Use the "disassemble main" command to see the assembly code in the main() routine.
Examine that code to find the name of the function called, and use "disassemble functionname" to see its code.
Then set a breakpoint at a memory address with a command like this: "break *0x08048470".
Press the PrintScrn key to copy the whole desktop to the clipboard.
YOU MUST SUBMIT A FULL-SCREEN IMAGE FOR FULL CREDIT!
Paste the image into Paint.
Save the document with the filename "YOUR NAME Proj 2xb", replacing "YOUR NAME" with your real name.