apt-get update apt-get install cppcheck -y
Enter this code:nano pwd.c
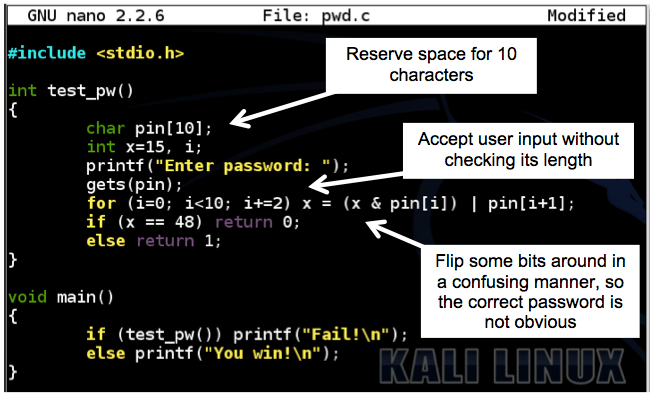
Your screen should look like this, without the explanatory boxes and arrows.#include <stdio.h> int test_pw() { char pin[10]; int x=15, i; printf("Enter password: "); gets(pin); for (i=0; i<10; i+=2) x = (x & pin[i]) | pin[i+1]; if (x == 48) return 0; else return 1; } void main() { if (test_pw()) printf("Fail!\n"); else printf("You win!\n"); }
This program has a simple buffer overflow because it uses gets().

Save the file with Ctrl+X, Y, Enter.
Cppcheck finds nothing wrong, as shown below.cppcheck pwd.c
An unimpressive performance.
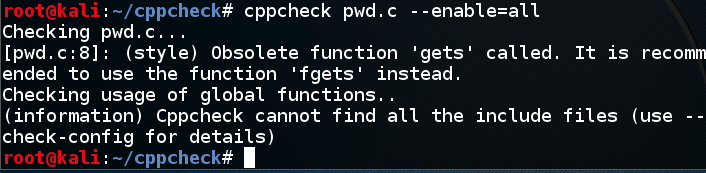
It can do better, if we enable all tests.
In your Kali machine, in a Terminal window, execute this command:
Now cppcheck gives us a generic warning about using gets(), as shown below.cppcheck pwd.c --enable=all
The gcc compiler gave us this same warning when we compiled that program.
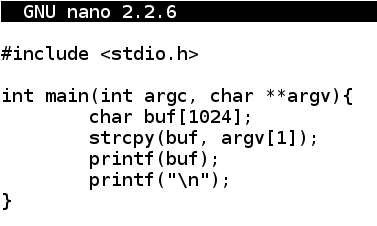
Enter the program shown below.nano fs.c
#include <stdio.h> int main(int argc, char **argv){ char buf[1024]; strcpy(buf, argv[1]); printf(buf); printf("\n"); }
Save the file with Ctrl+X, Y, Enter.
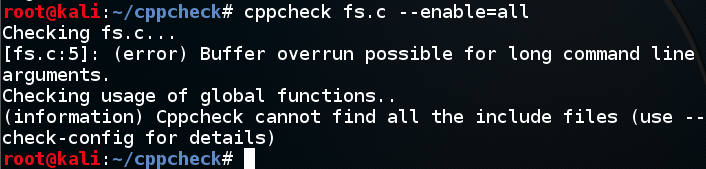
Cppcheck finds the buffer overflow in line 5, but doesn't detect the format string vulnerability at all, as shown below.cppcheck fs.c --enable=all
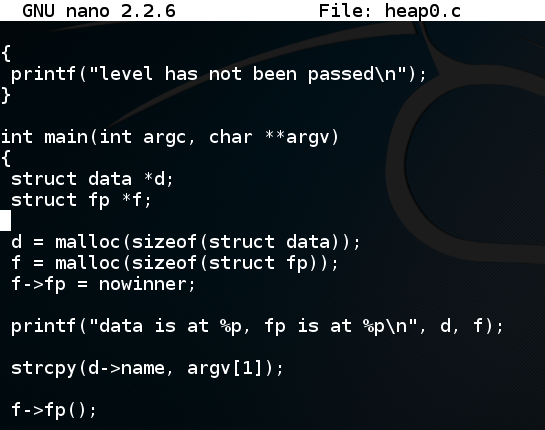
Scroll down to see the vulnerable code, as shown below.curl https://samsclass.info/127/proj/heap0.c > heap0.c nano heap0.c
strcpy is used to copy the command-line argument into the "d" structure without checking its size.
Close the file with Ctrl+X.
Cppcheck finds several problems: memory is allocated for "d" and "f" but never freed, which causes a "memory leak" (RAM is wasted).cppcheck heap0.c --enable=all
Also, the "d" pointer might allow a read of uninitialized memory.
Bizarreley, in an earlier version, it failed to find the same buffer overflow vulnerability it caught in the earlier program, but the version I used in April, 2018 found it, as shown below.

Save a whole-desktop screen capture with a filename of "Proj 19x from YOUR NAME".
Email the image to cnit.127sam@gmail.com with a subject of "Project 19x from YOUR NAME".