sudo apt update
sudo apt install curl build-essential gdb -y
sudo apt install rustc -y
mkdir HelloWorld-App
cd HelloWorld-App
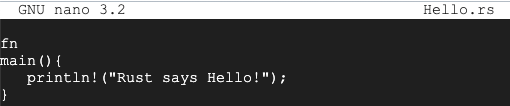
nano Hello.rs
fn
main(){
println!("Rust says Hello!");
}

Save the file with Ctrl+X, Y, Enter.
Execute these commands to compile and run the program:
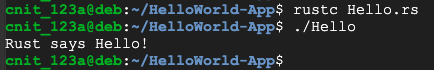
rustc Hello.rs
./Hello
cd
mkdir Int-App
cd Int-App
nano Int.rs
fn main() {
let i = 1;
let j:u32 = -5;
println!("i is {}", i);
println!("j is {}", j);
}
rustc Int.rs
R 10.1: Int (5 pts)
Change one character in the "Int.rs" program to fix it and produce this desired output:
The flag is the complete fixed line.
cd
mkdir Add-App
cd Add-App
nano Add.rs
fn main() {
let a = 1;
a = a + 1;
println!("a is {}", a);
}
Execute this command to compile it:
rustc Add.rs
R 10.2: Add (5 pts)
Add one three-letter keyword to a single line in the "Add.rs" program to fix it and produce this desired output:
The flag is the complete fixed line.
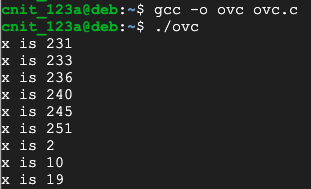
nano ovc.c
#include <stdio.h>
int main()
{
unsigned char x = 230;
int i;
for (i = 1; i < 10; i++)
{
x = x + i;
printf("x is %d\n",x);
}
}
Execute these commands to compile the program and run it:
gcc -o ovc ovc.c
./ovc
cd
mkdir Ov-App
cd Ov-App
nano Ov.rs
fn main() {
let mut x:u8 = 230;
for y in 1..10{
x = x + y;
println!("x is {}",x);
}
}
Execute these commands to compile and run it:
rustc Ov.rs
./Ov
R 10.3: Overflow (5 pts)
Compile the file and run it.As shown below, Rust does not allow the integer to assume an incorrect value. Instead, it stops and alerts the developer with an error message.
The flag is covered by a green rectangle in the image below.
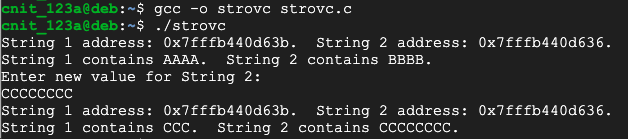
nano strovc.c
#include <stdio.h>
int main()
{
char s1[5] = "AAAA";
char s2[5] = "BBBB";
printf("String 1 address: %p. String 2 address: %p.\n", s1, s2);
printf("String 1 contains %s. String 2 contains %s.\n", s1, s2);
printf("Enter new value for String 2:\n");
scanf("%s", s2);
printf("String 1 address: %p. String 2 address: %p.\n", s1, s2);
printf("String 1 contains %s. String 2 contains %s.\n", s1, s2);
}
Execute these commands to compile the program and run it:
gcc -o strovc strovc.c
./strovc
The program asks for a new value. Enter eight "C" characters, as shown below.
The eight-letter value in String 2 overflows into String 1. As before, C just lets this awful thing happen without stopping or warning the developer.
This is the notorious "buffer overflow" vulnerability responsible for many viruses and other security problems.
cd
mkdir Str-App
cd Str-App
nano Str.rs
fn main() {
let mut s1 = String::from("AAAA");
let mut s2 = String::from("BBBB");
println!("String 1 address: {:p}. String 2 address: {:p}.", &s1, &s2);
println!("String 1 contains {}. String 2 contains {}. ", s1, s2);
println!("Enter new value for String 1: ");
let num = std::io::stdin().read_line(&mut s1).unwrap();
println!("{} bytes read", num);
println!("String 1 address: {:p}. String 2 address: {:p}.", &s1, &s2);
println!("String 1 contains {}. String 2 contains {}. ", s1, s2);
}
Execute these commands to compile and run it. Don't omit the "-g" switch--we'll need it later for debugging.
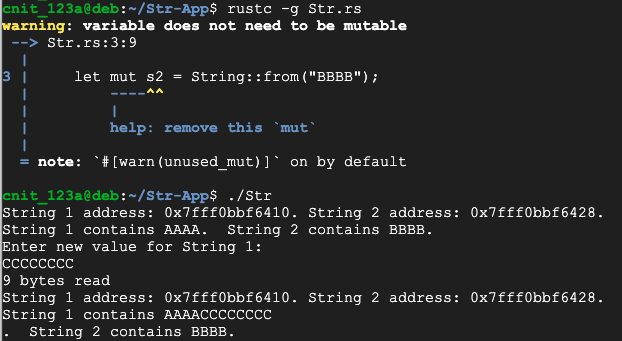
rustc -g Str.rs
./Str
When the program asks for a new value, enter eight "C" characters.
Notice these things:
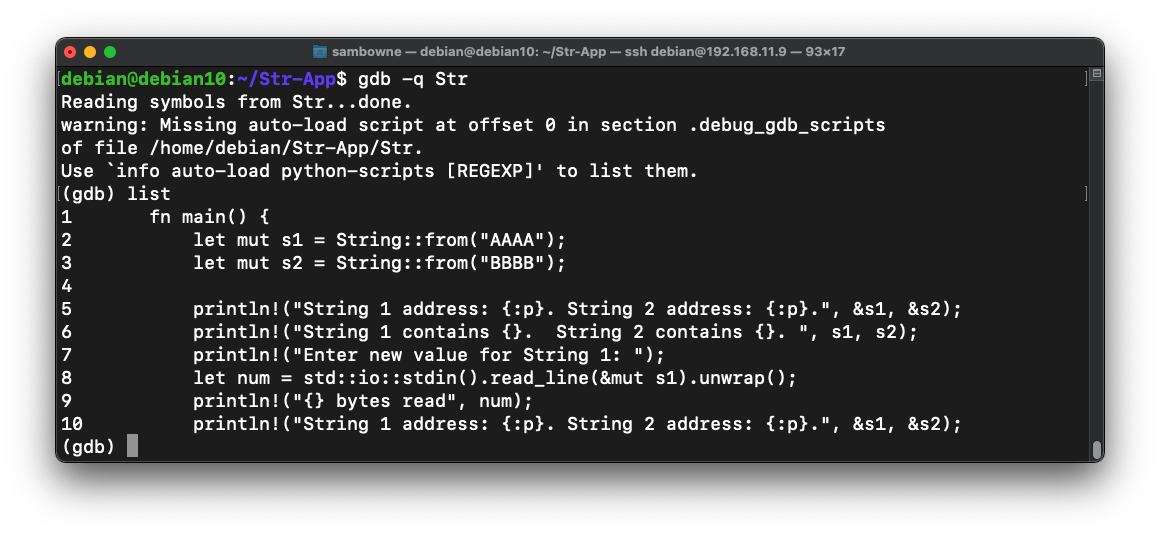
gdb -q Str
list
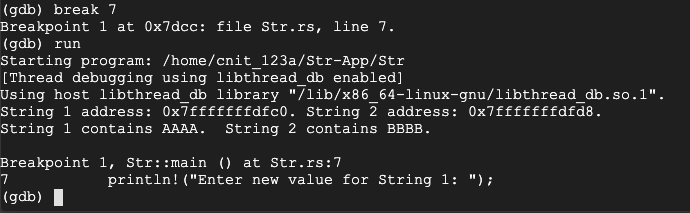
Execute these commands to set a breakpoint and start running the program:
break 7
run
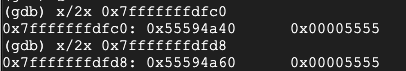
Execute these commands to examine memory where the strings are stored. You may have to adjust the addresses to match the addresses shown on your system:
x/2x 0x7fffffffdfc0
x/2x 0x7fffffffdfd8
Instead, pointers are stored here, as shown below.
Execute these commands to examine the details of how the strings are stored:
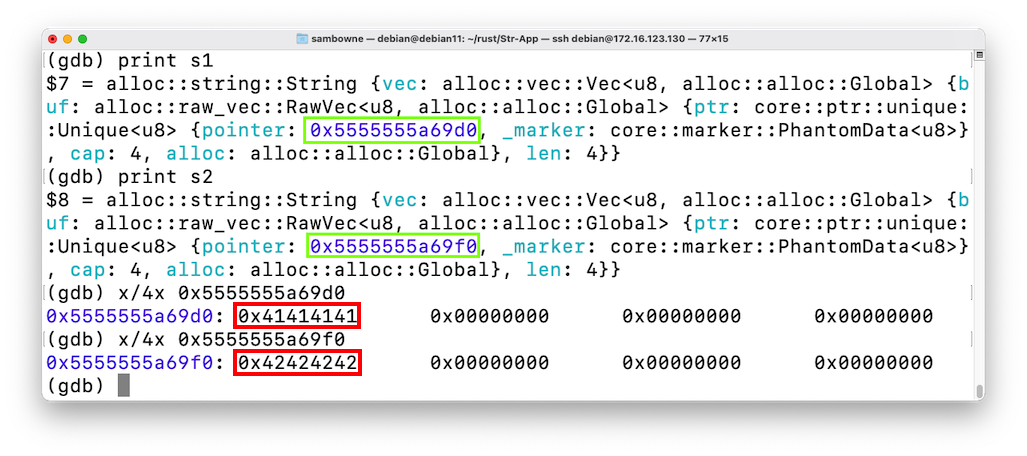
print s1
print s2
Execute these commands to see the stored strings, replacing the addresses with the correct addresses on your system:
x/4x 0x5555555a69d0
x/4x 0x5555555a69f0
break 10
continue
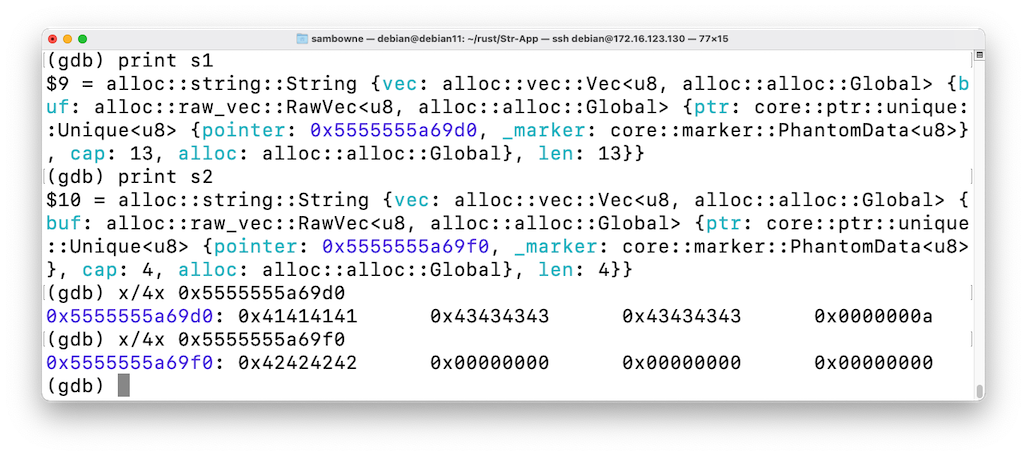
Execute these commands to examine the details of how the strings are stored, correcting the addresses as you did before:
print s1
print s2
x/4x 0x5555555a69d0
x/4x 0x5555555a69f0
run
y
continue
Execute these commands to examine the details of how the strings are stored, adjusting the addresses to match the new values of the pointers:
print s1
print s2
x/4x 0x5555555a8a20
x/4x 0x5555555a69f0
This is much safer. The developer doesn't need to remember how long the string is--it just resizes automatically as needed, and never corrupts memory used by some other variable.
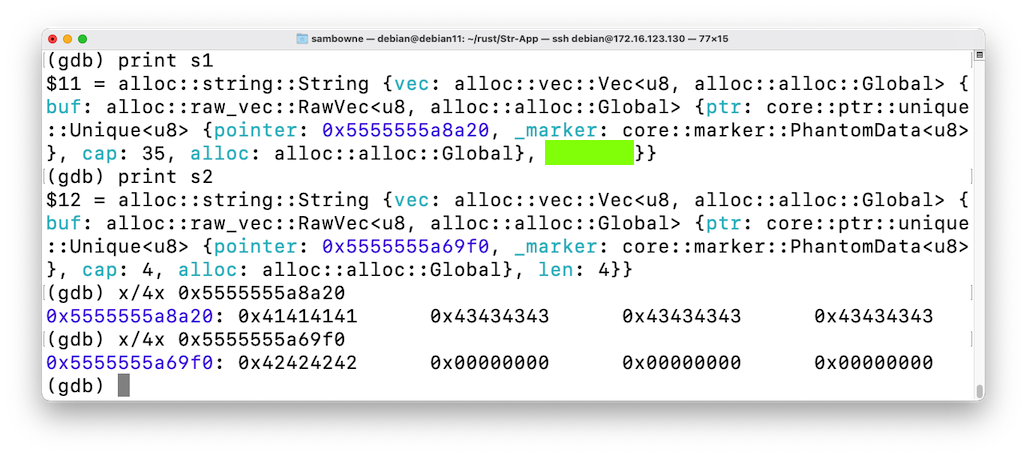
R 10.4: String Storage (10 pts)
The flag is covered by a green rectangle in the image above.
cd
nano cmdi.c
#include <stdio.h>
#include <string.h>
#include <stdlib.h>
int main()
{
char ip[30];
char cmd[40];
printf("IP:");
scanf("%s", ip);
strcpy(cmd, "ping -c 1 ");
strcat(cmd, ip);
system(cmd);
}
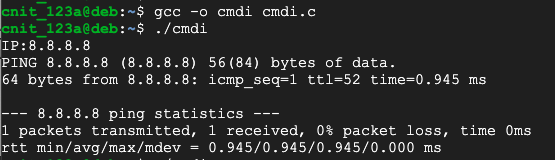
Execute these commands to compile the program and run it:
gcc -o cmdi cmdi.c
./cmdi
8.8.8.8
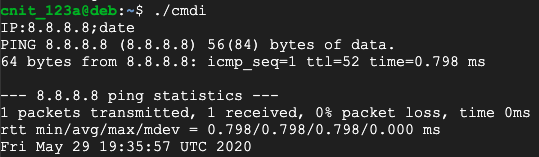
Run the program again, entering this address:
8.8.8.8;date
Execute these commands to create a new Rust package named cmdi and edit its "Manifest":
cd
cargo new cmdinj
cd cmdinj
nano Cargo.toml
cmd_lib = "0.6.5"
Save the file with Ctrl+X, Y, Enter.
Execute this command to edit the package's source code:
nano src/main.rs
use cmd_lib::{run_cmd};
fn main() {
let mut ip = String::new();
println!("Enter IP: ");
let _num = std::io::stdin().read_line(&mut ip).unwrap();
run_cmd!("ping -c 1 {}", ip);
}
Save the file with Ctrl+X, Y, Enter.
Execute this command to compile and run it:
cargo run
8.8.8.8
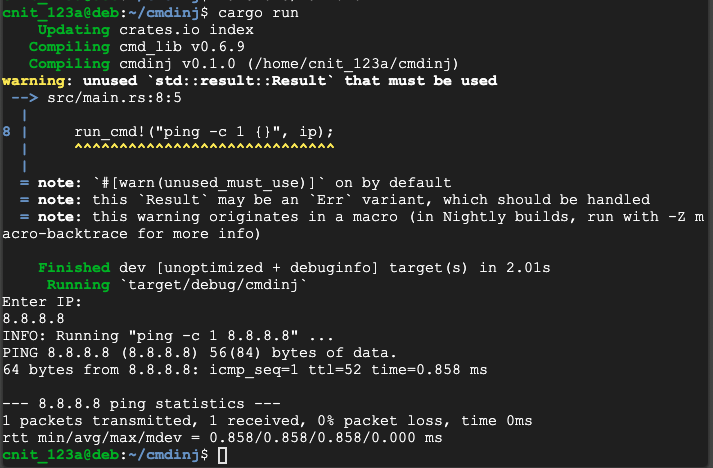
cargo run
8.8.8.8;date
Rust does not prevent command injection vulnerabilities.
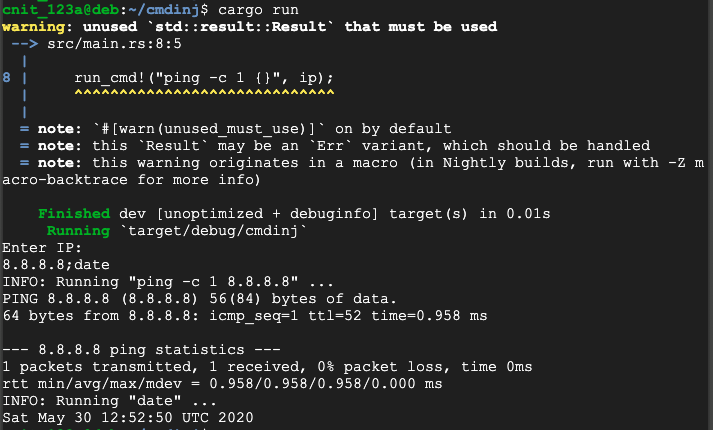
R 10.5: Lock File (10 pts)
Execute this command:The flag is covered by a green rectangle in the image below.
Posted 5-30-2020
R 10.3 instructions fixed 11-15-20
R 10.2 instructions fixed 4-26-2021
Rust install instructions updated 8-3-2021
Updated with different gdb commands 6-22-22
Minor updates 11-22-22
Video and note about string pointer order added 4-20-23