In a Terminal window, execute this command:
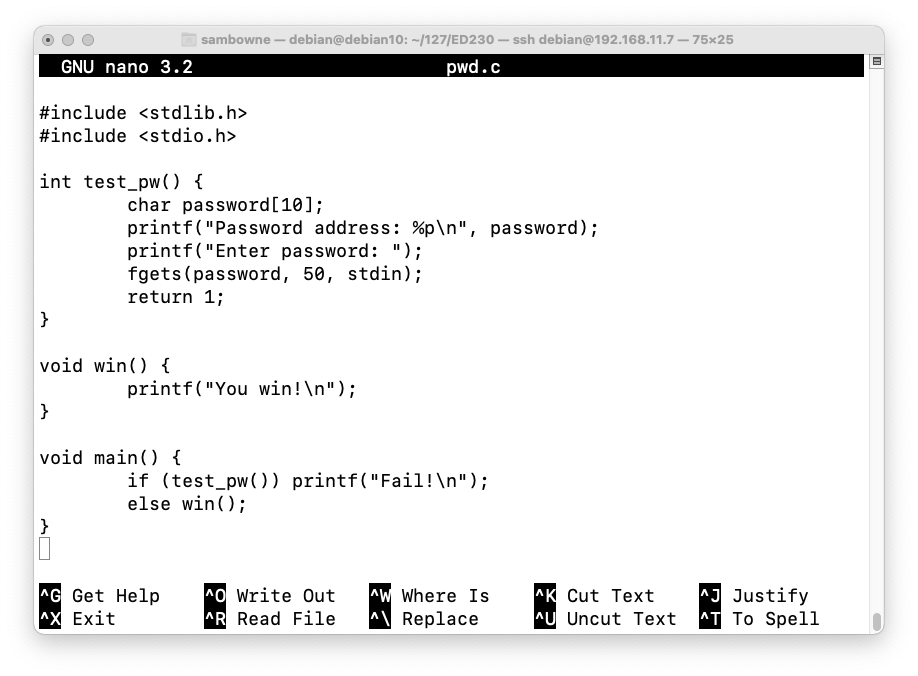
Enter this code, as shown below.nano pwd.c
The test_pw function reserves room for 10 characters in pin[], but reads up to 50 characters from stdin, allowing a buffer overflow.#include <stdlib.h> #include <stdio.h> int test_pw() { char password[10]; printf("Password address: %p\n", password); printf("Enter password: "); fgets(password, 50, stdin); return 1; } void win() { printf("You win!\n"); } void main() { if (test_pw()) printf("Fail!\n"); else win(); }
It also always returns 1, so the win() function is never executed.

Save the file with Ctrl+X, Y, Enter.
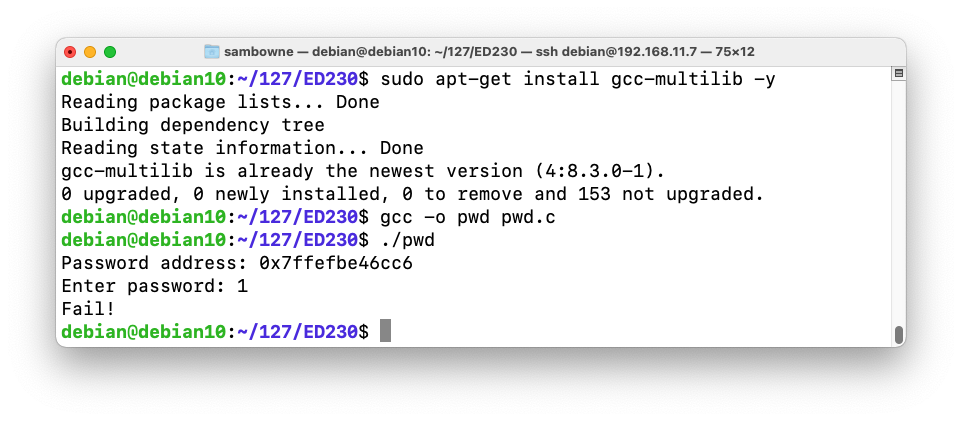
The program runs normally, wth the "Fail!" message, as shown below.sudo apt-get update sudo apt-get install gcc-multilib -y gcc -o pwd pwd.c ./pwd 1
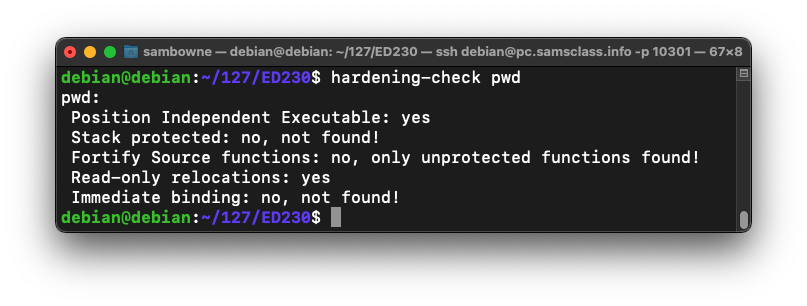
You see a list of defenses, and whether they are implemented, as shown below.sudo apt-get install devscripts -y hardening-check pwd
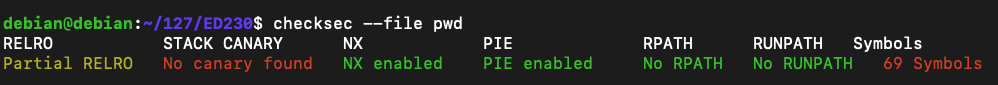
You see a list of defenses, and whether they are implemented, as shown below (I trimmed some fields on the right).sudo apt-get install checksec -y checksec --file pwd
Flag ED 230.1: PIE (3 pts)
Find the gcc flag needed to disable Position Independent Executable support, outlined in red in the image below.The flag is covered by a green rectangle in the image below.
Flag ED 230.2: Canary (3 pts)
Find the gcc flag needed to add a stack canary to the file, outlined in red in the image below.The flag is covered by a green rectangle in the image below.
Flag ED 230.3: Symbols (3 pts)
Find the gcc flag needed to remove symbols, outlined in red in the image below.The flag is covered by a green rectangle in the image below.
Flag ED 230.4: Fortify (3 pts)
Find the gcc flag needed to "Fortify Source functions", outlined in red in the image below.The flag is covered by a green rectangle in the image below.
Flag ED 230.5: Binding (3 pts)
Find the gcc flag needed to implement "Immediate binding", outlined in red in the image below.The flag is covered by a green rectangle in the image below.
Posted 4-11-2021
Images updated 3-8-23
Video added 3-23-35