NOTE: Windows 7 will not work for this project! 注意:Windows 7将不适用于此项目!
This project follows Lab 3-3 in the textbook.该项目遵循教科书中的实验3-3 。
Open Process Explorer and move it so you can see it at the same time as the Explorer window.打开Process Explorer并移动它,以便您可以在Explorer窗口的同时看到它。 Scroll to the bottom to show explorer.exe (your desktop) and its children, which are processes launched by the currently logged-in user, as shown below.滚动到底部以显示explorer.exe (您的桌面)及其子项,这是当前登录的用户启动的进程,如下所示。

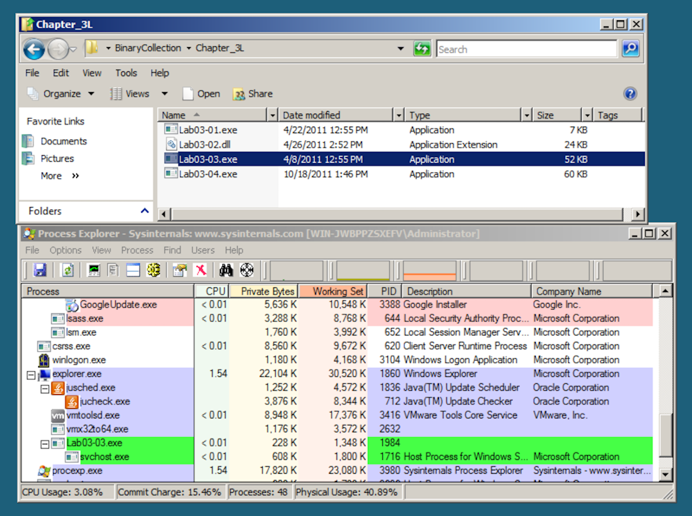
After a second or two, the Lab03-03.exe process terminates, leaving the svchost.exe running as an orphan process, as shown below.一两秒钟后,Lab03-03.exe进程终止,将svchost.exe作为孤立进程运行,如下所示。
This is highly unusual and suspicious behavior.这是非常不寻常和可疑的行为。
To see that, in Process Explorer, right-click svchost.exe and click Properties .要查看该文件,请在Process Explorer中右键单击svchost.exe ,然后单击“ 属性” 。
Click the Strings tab.单击字符串选项卡。 At the bottom, make sure Image is selected, as shown below.在底部,确保选择了图像 ,如下所示。
These are the strings on the disk, in the real svchost.exe file.这些是真正的svchost.exe文件中的磁盘上的字符串。
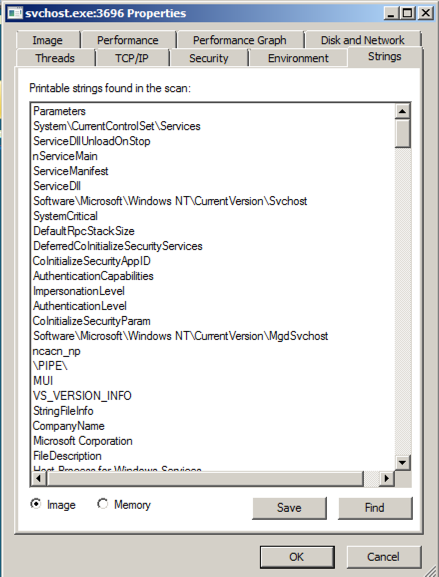
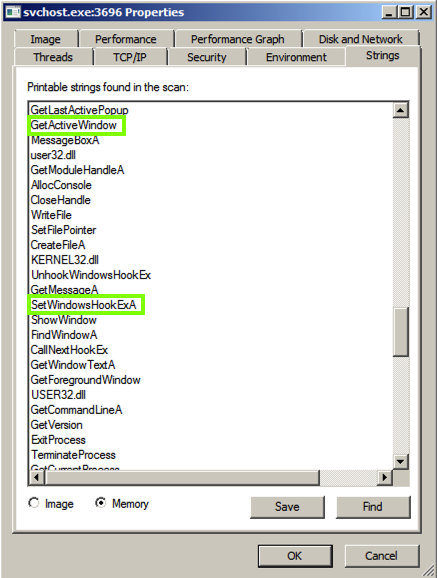
At the bottom of the box, click the Memory button.在框的底部,单击Memory按钮。 Now the strings are completely different, and contain these suspicious items: GetActiveWindow and SetWindowsHookExA .现在这些字符串是完全不同的,并且包含这些可疑项目: GetActiveWindow和SetWindowsHookExA 。
Those functions can be used by a keylogger, to hook the keypresses and run added code to record them.键盘记录器可以使用这些函数来钩住按键并运行添加的代码来记录它们。
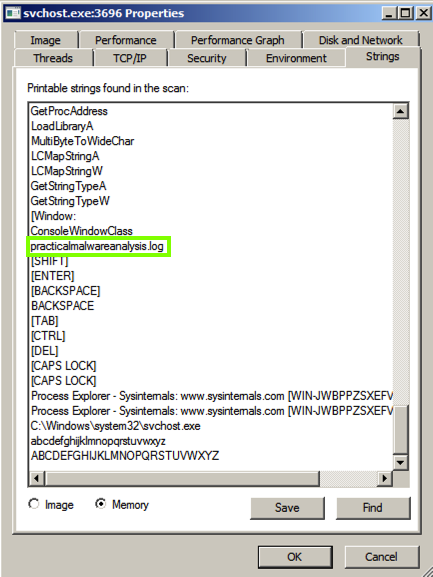
Scroll down and find the string practicalmalwareanalysis.log , as shown below.向下滚动并找到字符串practicalmalwareanalysis.log ,如下所示。 This may be the filename used to store the keypresses.这可能是用于存储按键的文件名。
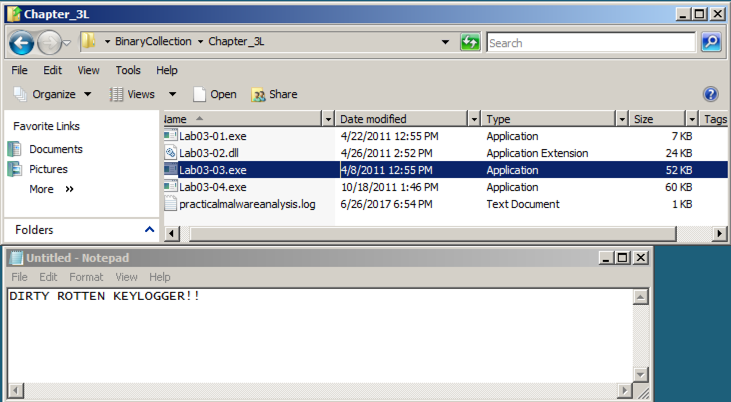
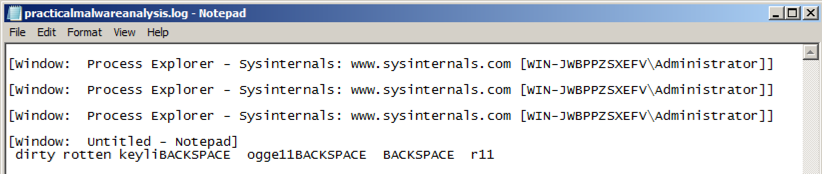
Double-click the practicalmalwareanalysis.log file.双击实用的malwareanalysis.log文件。 The stolen keystrokes appear, as shown below.出现被盗的按键,如下所示。
Find the Logfile (15 pts)找到日志文件(15分)
In your Documents folder, find the file chal6.exe在您的文档文件夹中,找到文件chal6.exeIf you aren't using the VM your instructor provided, download the file here .如果您没有使用教师提供的虚拟机,请在此处下载该文件。
This file is a keylogger.这个文件是一个键盘记录器。 Find the file containing the captured keystrokes.找到包含捕获的击键的文件。 Use the form below to get your points.使用下面的表格来获得你的观点。