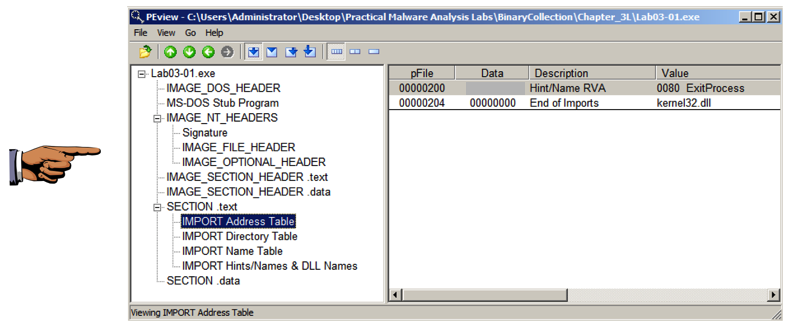

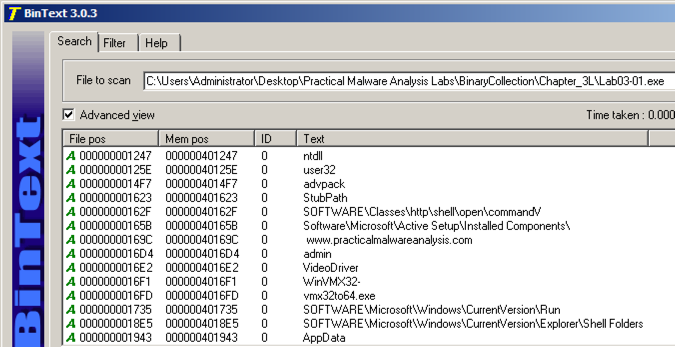
We will use these three programs to see what the malware does:我们将使用这三个程序来查看恶意软件的功能:
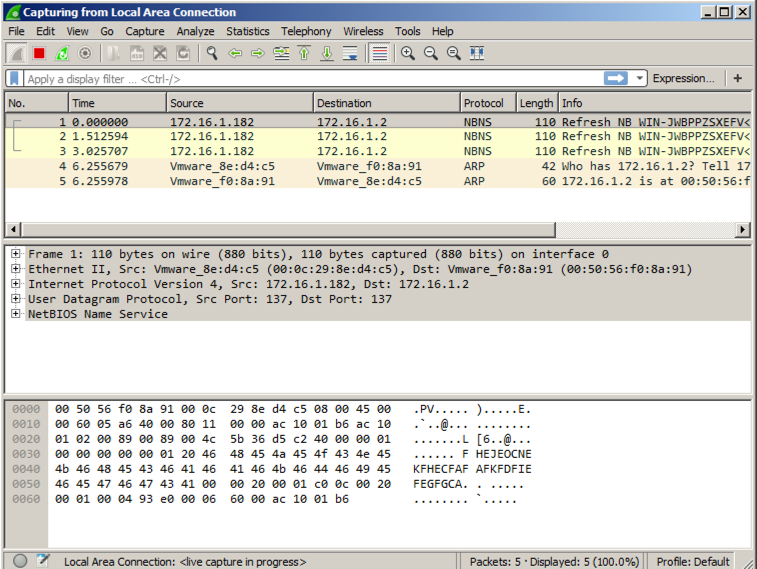
If your virtual machine is in "NAT" networking mode, there shouldn't be a lot of traffic.如果您的虚拟机处于“NAT”联网模式,则应该不会有很多流量。
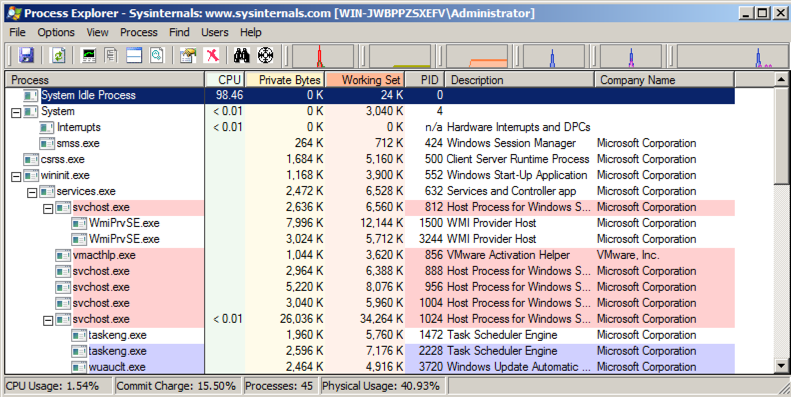
It's best to start Process Monitor last, so you can exclude all the harmless processes the other tools are using.最好先启动进程监视器,以便排除其他工具正在使用的所有无害进程。
Launch Process Monitor.启动进程监视器。 If a Security Warning box pops up, allow the software to run.如果弹出安全警告框,请运行软件。
Agree to the license.同意许可证。
You should see Process Monitor, with a lot of processes visible, as shown below:您应该看到Process Monitor,其中有很多进程可见,如下所示:
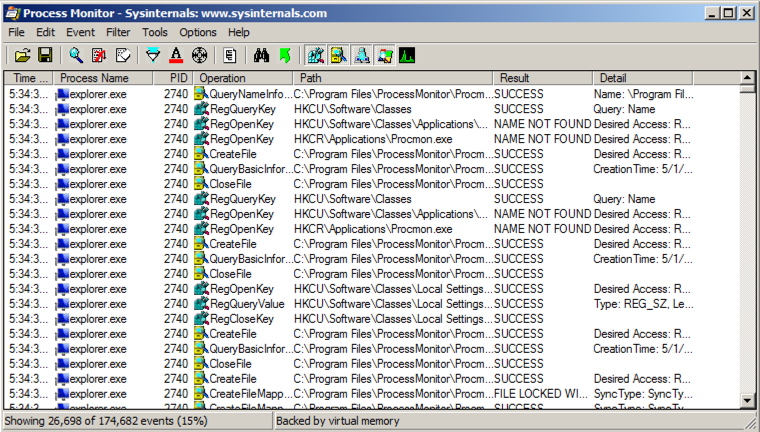
In Process Monitor, right-click the name of one of the visible processes, such as explorer.exe , and click " exclude 'lsass.exe' ", as shown below:在Process Monitor中,右键单击其中一个可见进程的名称,例如explorer.exe ,然后单击“ exclude'lsass.exe' ”,如下所示:
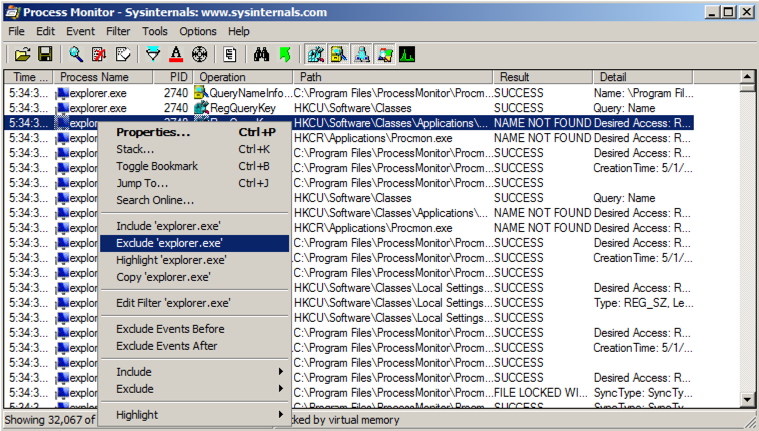
Right-click a remaining process, such as "lsass" and exclude it too.右键单击剩余的进程,例如“lsass”并将其排除。
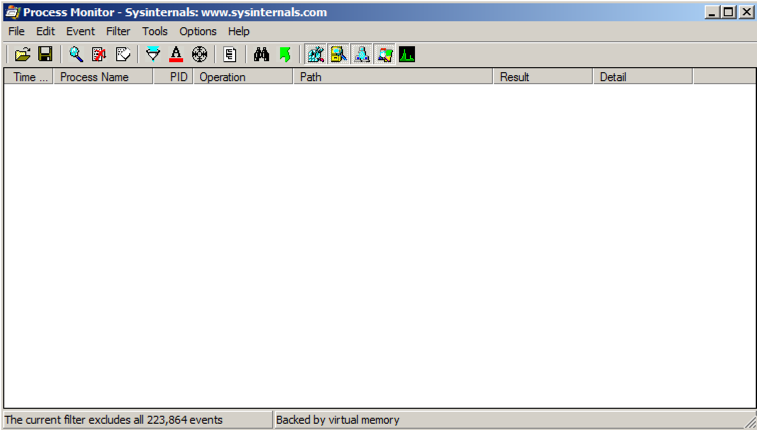
Repeat the process until all current processes are hidden, as shown below.重复该过程,直到隐藏所有当前进程,如下所示。 There are a lot of processes to ignore, perhaps 20 or 30.有许多过程可以忽略,大概20或30。
Troubleshooting故障排除
If the Lab03-01.exe process does not appear in Process Explorer, that probably means that the malware has already been run on this VM.如果Lab03-01.exe进程没有出现在Process Explorer中,那可能意味着恶意软件已经在该VM上运行。To make the malware run properly again, open Process Explorer and kill the vmx32to64.exe process.要使恶意软件再次正常运行,请打开Process Explorer并终止vmx32to64.exe进程。 Then delete this file:然后删除这个文件:
C:\Windows\System32\vmx32to64.exe C:\ WINDOWS \ SYSTEM32 \ vmx32to64.exe
In Process Explorer, click View , " Lower Pane View ", Handles .在Process Explorer中,单击查看 ,“ 下窗格视图 ”, 句柄 。
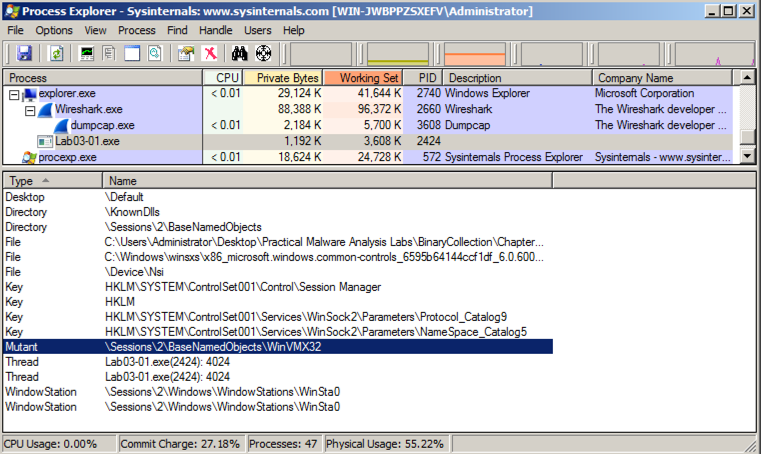
You see the WinVMX32 mutant, as highlighted below.您将看到WinVMX32突变体,如下所示。 A mutant, also called a mutex, is used for interprocess connunication.一个突变体,也称为互斥体,用于进程间通信。 A wonderful explantion of mutexes in terms of rubber chickens is here .关于橡胶鸡的互斥体的精彩解说在这里 。
In Process Explorer, click View , " Lower Pane View ", DLLs .在Process Explorer中,单击查看 ,“ 下窗格视图 ”, DLL 。
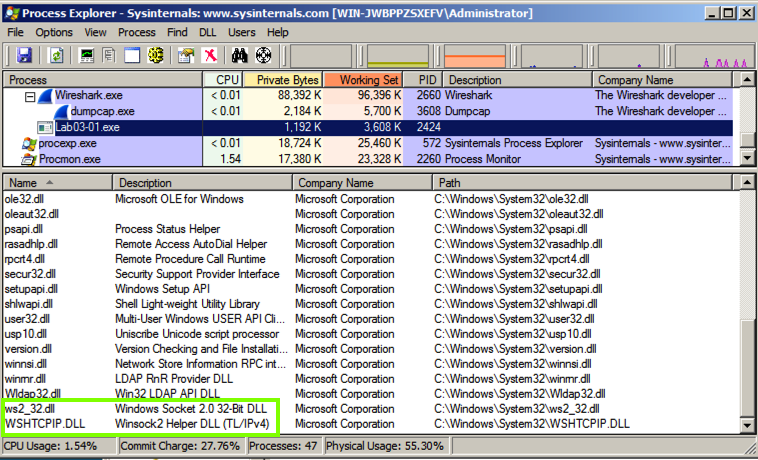
Scroll to the bottom to find ws2_32.dll and WSHTCPIP.DLL , as shown below.滚动到底部以查找ws2_32.dll和WSHTCPIP.DLL ,如下所示。 This shows that the malware has networking functionality.这表明该恶意软件具有网络功能。
In Process Monitor, click Filter , Filter .在进程监视器中,单击筛选器 , 筛选器 。 Enter a Filter for " Process Name " is Lab03-01.exe , Include , as shown below.为“ 进程名称 ”输入过滤器Lab03-01.exe , 包括 ,如下所示。
Click Add to add the filter.点击添加以添加过滤器。
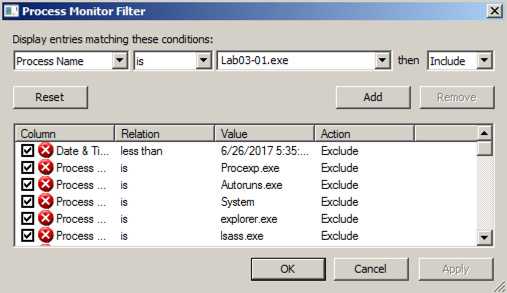
Add two more filters:再添加两个过滤器:
You end up with the two events shown below.您最终会看到下面显示的两个事件。
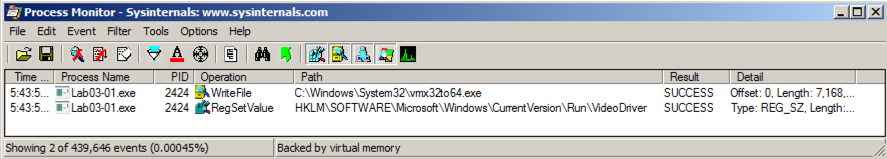
Double-click the event with a Path ending in vmx32to64.exe .双击带有以vmx32to64.exe结尾的路径的事件。 The Properties sheet shows that this event creates a file named vmx32to64.exe, as shown below.属性表显示此事件会创建一个名为vmx32to64.exe的文件,如下所示。
The malware wrote 7,168 bytes--the same size as Lab03-01.exe itself.该恶意软件写入7,168字节 - 与Lab03-01.exe本身大小相同。 The malware copied itself to a file named vmx32to64.exe, so that filename is a useful Indicator of Compromise.恶意软件将其自身复制到一个名为vmx32to64.exe的文件中,以便文件名是一个有用的妥协指标。
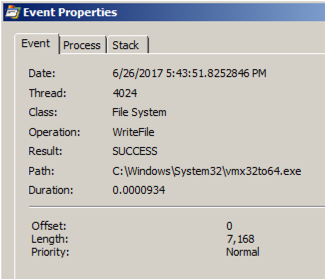
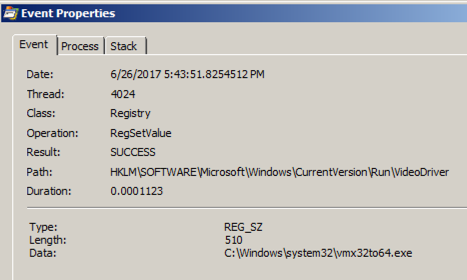
Double-click the event with a Path ending in VideoDriver .双击VideoDriver中以Path结尾的事件。
This event creates a new a Run key in the registry named "VideoDriver" with a value of "C:\WINDOWS\system32\vmx32to64.exe" -- this is a persistence mechanism, to re-launch the malware when the machine restarts.此事件在名为“VideoDriver”的注册表中创建一个新的Run key,值为“C:\ WINDOWS \ system32 \ vmx32to64.exe” - 这是一种持久性机制,可在计算机重新启动时重新启动恶意软件。
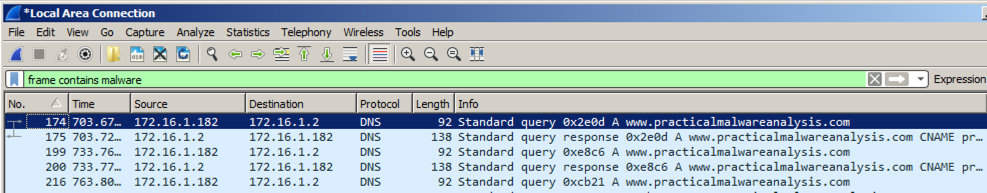
At the top left of the Wireshark window, in the Filter bar, type a filter of在Wireshark窗口的左上角,在过滤器栏中,输入过滤器
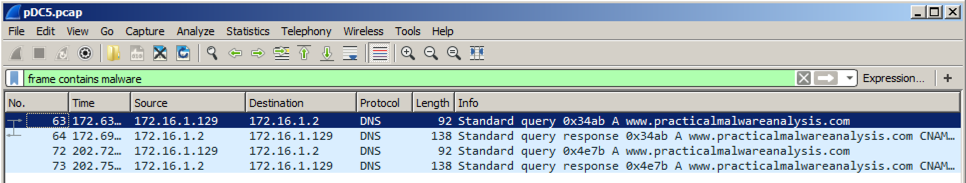
frame contains malware Press Enter to see the filtered packets, as shown below.按Enter查看过滤的数据包,如下所示。 Every 30 seconds, the malware performs a DNS lookup for the domain "www.practicalmalwaresnalysis.com".每隔30秒,恶意软件会为域名“www.practicalmalwaresnalysis.com”执行DNS查找。
Click the line showing the first DNS request for www.practicalmalwareanalysis.com -- in the example above, it is packet 174.点击显示www.practicalmalwareanalysis.com的第一个DNS请求的行 - 在上面的例子中,它是包174。
In the top right of Wireshark, in the green filter bar, click the X button to clear the filter.在Wireshark的右上角,在绿色的过滤器栏中,单击X按钮清除过滤器。
The packets following the DNS request appear, as shown below.出现DNS请求后的数据包,如下所示。 Notice these items:注意这些项目:
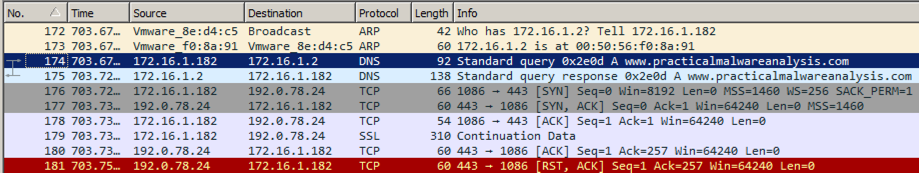
This is intended to fool a firewall into thinking it's HTTPS traffic, but there is no actual encryption or key exchange.这是为了让防火墙认为它是HTTPS流量,但没有真正的加密或密钥交换。 A real HTTPS connection contains many more packets, such as "Client Hello", "Server Hello", and "Change Cipher Spec".一个真正的HTTPS连接包含更多的数据包,例如“Client Hello”,“Server Hello”和“Change Cipher Spec”。
Find the SYN packet sent to the https port, which may be marked "443".查找发送到https端口的SYN数据包,该数据包可能标记为“443”。 In the example above, it is packet 176. Right-click it and click " Follow TCP Stream ".在上面的示例中,它是数据包176.右键单击它并单击“ Follow TCP Stream ”。
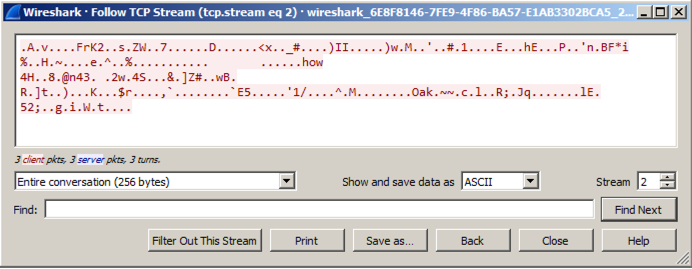
You see 256 bytes of random data, as shown below.您会看到256个字节的随机数据,如下所示。 These are beacons and are used by malware to notify the Command and Control server that the machine is infected and ready to use.这些是信标 ,被恶意软件用来通知命令和控制服务器该机器已被感染并准备使用。
The file contains two malware beacons, as shown below.该文件包含两个恶意软件信标,如下所示。
Follow the TCP stream in the second beacon.跟随第二个信标中的TCP流。 You should see random bytes, as shown below.你应该看到随机字节,如下所示。
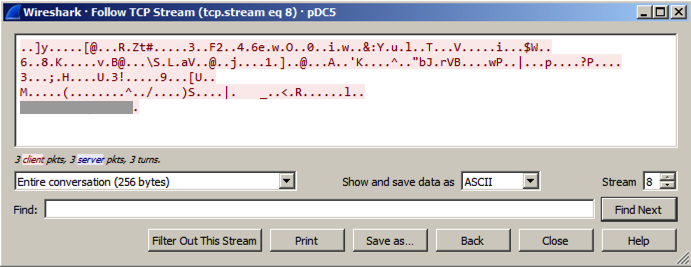
The last line of the beacon contains six readable characters, which are redacted in the image above.信标的最后一行包含六个可读的字符,它们在上面的图像中被编辑。
Use the form below to put your name on the WINNERS PAGE .使用下面的表格将您的姓名放在赢家页面上 。