This project follows Lab 1-2 in the textbook. There are more detailed solutions in the back of the book.
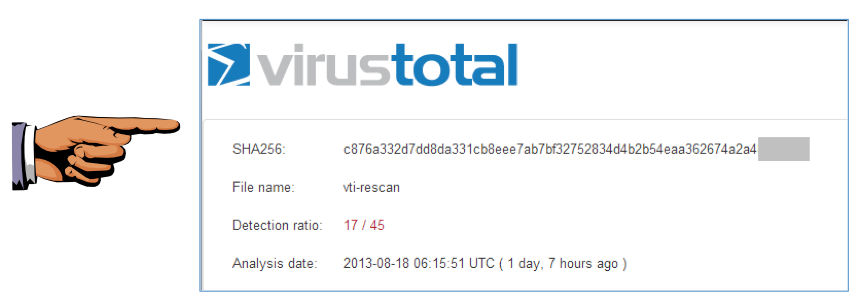
We will grade it by checking the last digits of the SHA256 value.

Press the PrntScrn key to capture an imag of the whole desktop.
Open Paint and paste the image in with Ctrl+V.
Save this image with the filename "Proj 2a from YOUR NAME".
YOU MUST SUBMIT WHOLE-DESKTOP IMAGES TO GET FULL CREDIT!
Download the UPX Zip file from here:
Download the upx391w.zip file, as shown below.
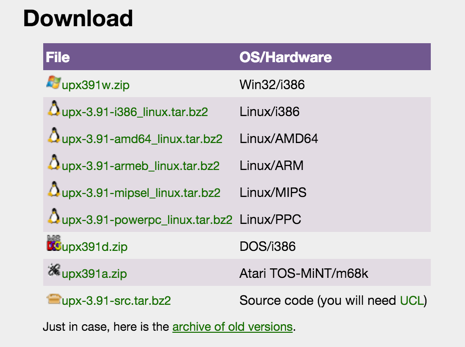
Unzip it and put upx.exe in your C:\Windows\System32 folder.
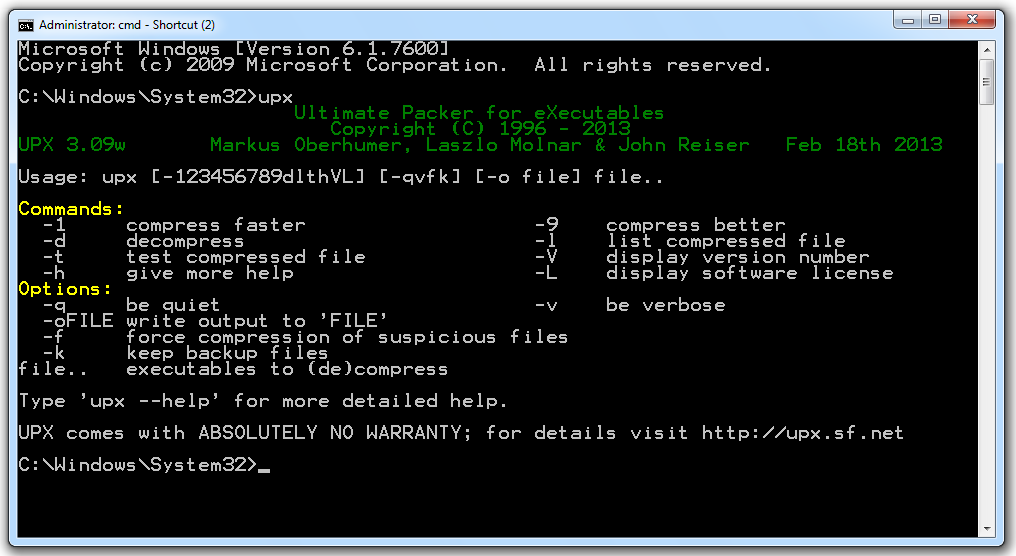
Open a Command Prompt window and execute this command:
UPX
Use the CD command to move to the directory containing your malware samples.
On my machine, I used this command:
cd "\Users\Administrator\Desktop\126\Practical Malware Analysis Labs\BinaryCollection\Chapter_1L"
UPX -d -o Lab01-02-unpacked.exe Lab01-02.exe
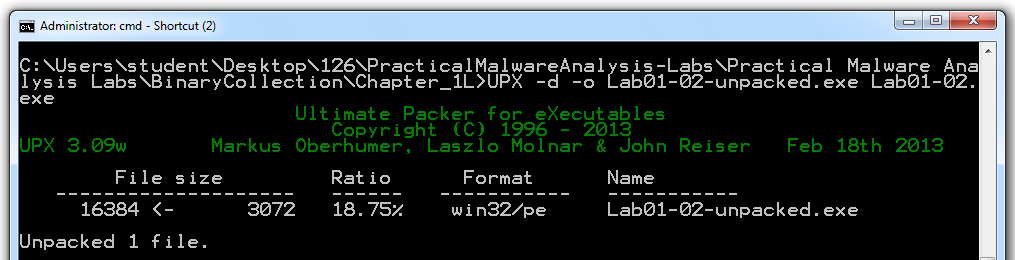
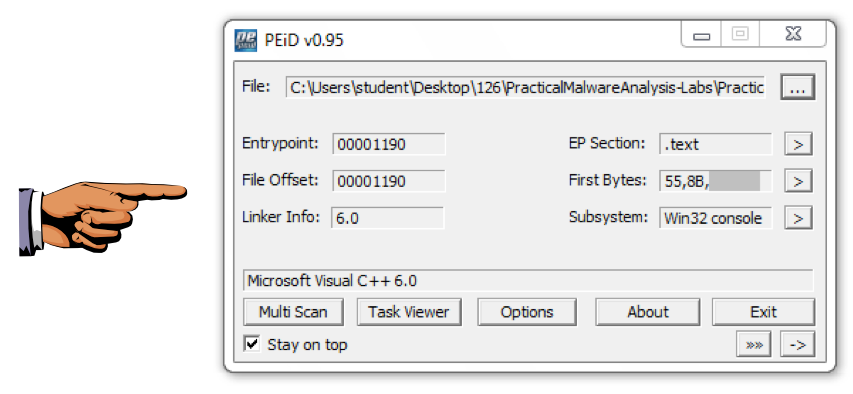
Analyze the unpacked file with PEiD. It now is regognized as a "Microsoft Visual C++ 6.0" file, as shown below.
Turn in the image showing your analysis of Lab01-02-unpacked.exe as shown below.
We will grade it based on the "First Bytes".
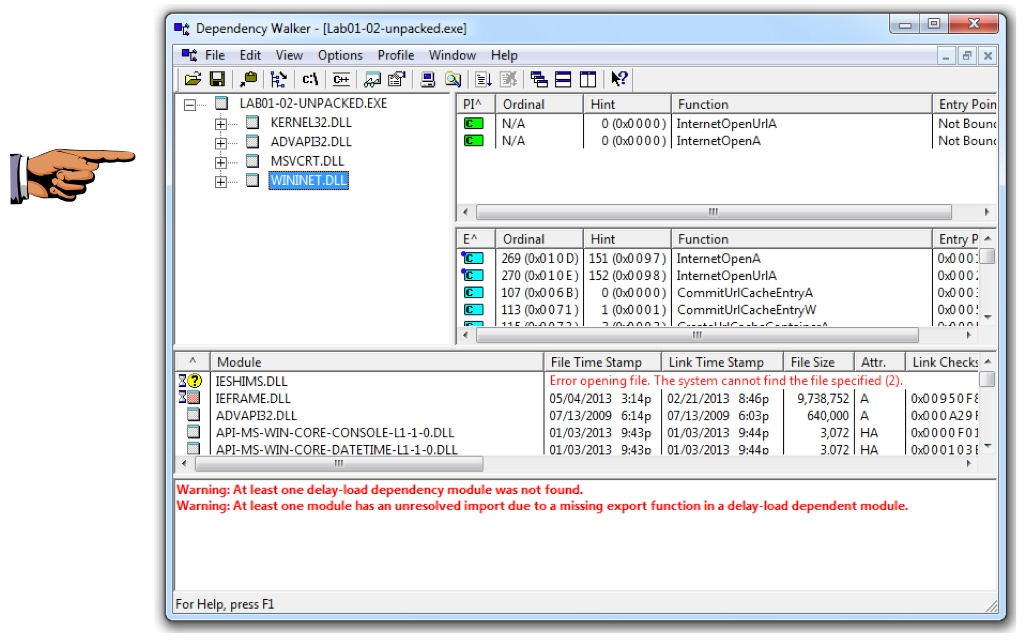
Save this image with the filename "Proj 2b from YOUR NAME".
Turn in the image showing the two functions InternetOpenUrlA and InternetOpenA as shown in the upper right pane of the image below.
Save this image with the filename "Proj 2c from YOUR NAME".
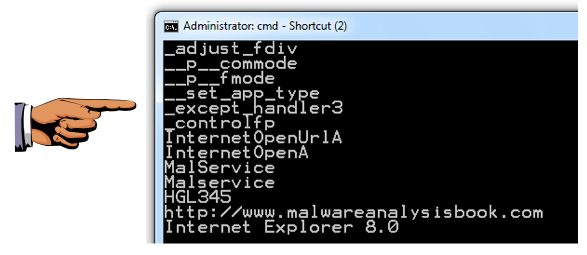
You should see MalService and http://www.malwareanalysisbook.com as shown below.
These suggest that infected machines will connect to http://www.malwareanalysisbook.com and will show a running service named MalService.
Save this image with the filename "Proj 2d from YOUR NAME".