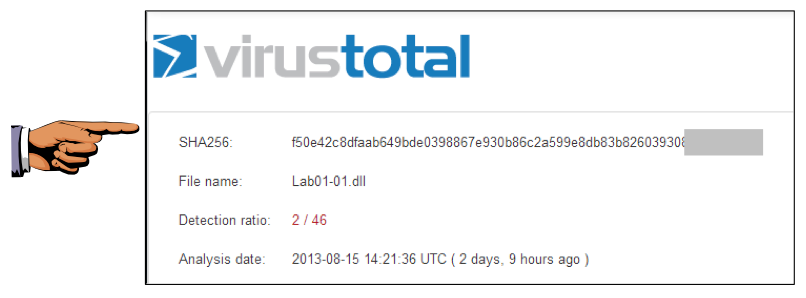
As shown below, some of the engines detect Lab01-01.dll .如下所示,一些引擎检测Lab01-01.dll 。

The files were both compiled on the same date within a minute of each other, indicating that they are part of the same package.这些文件都是在相同的日期在一分钟内彼此编译的,表明它们是同一个软件包的一部分。
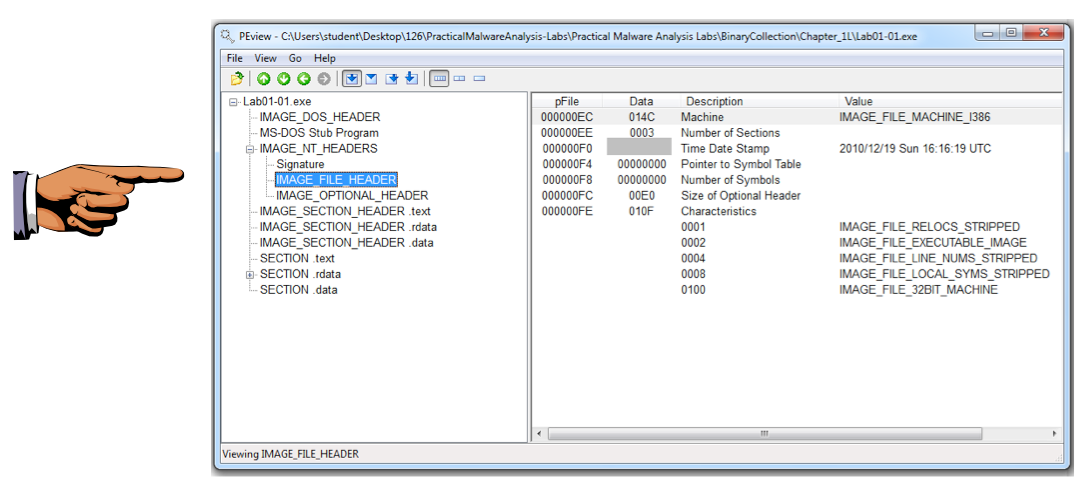
These files are identified as "Microsoft Visual C++" files, which shows that they are unpacked.这些文件被标识为“Microsoft Visual C ++”文件,这表明它们是解压缩的。
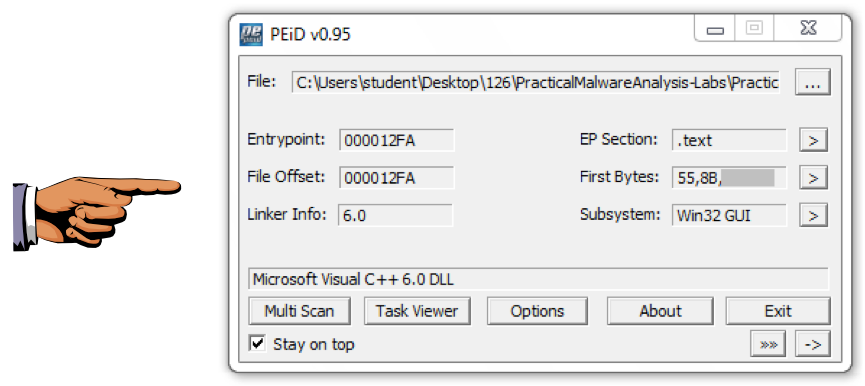
Look at the strings for Lab01-01.dll .查看Lab01-01.dll的字符串。
Notice these items, as shown below:注意这些项目,如下所示:
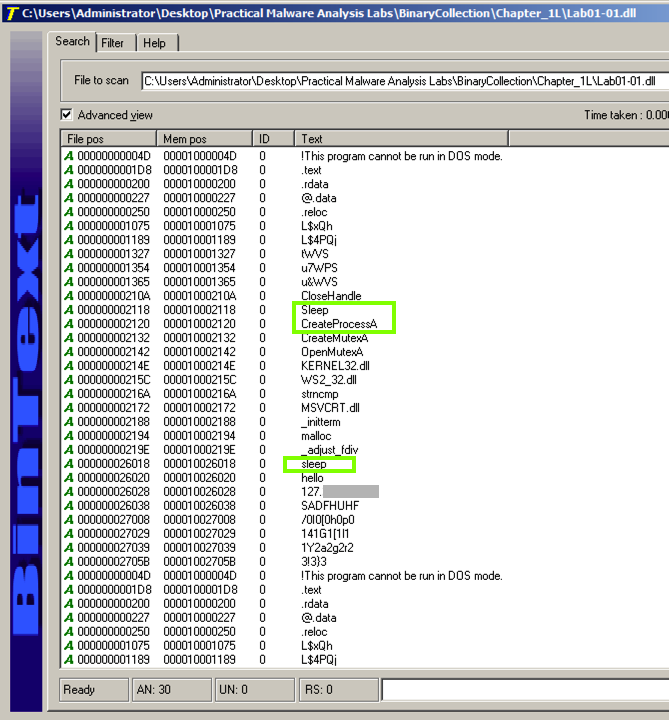
The command to launch a program is missing.启动程序的命令丢失。 To see it, click the Filter tab and adjust the "Min. text length" to 4 as shown below.要查看它,请单击“ 过滤器”选项卡,然后将“最小文本长度”调整为4 ,如下所示。
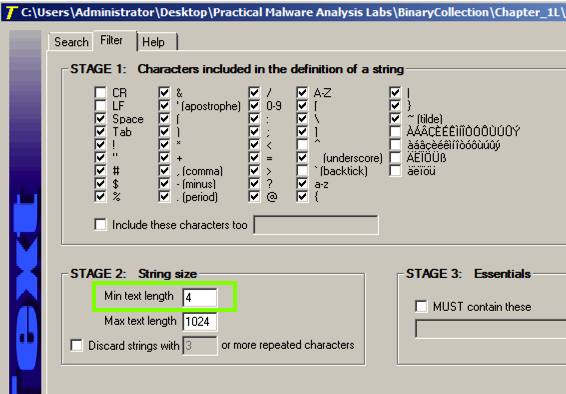
Click the Search tab.点击搜索标签。 At the top right, click Go .点击右上角的开始。
Now you can see that the command to launch a program is exec , as shown below.现在您可以看到启动程序的命令是exec ,如下所示。
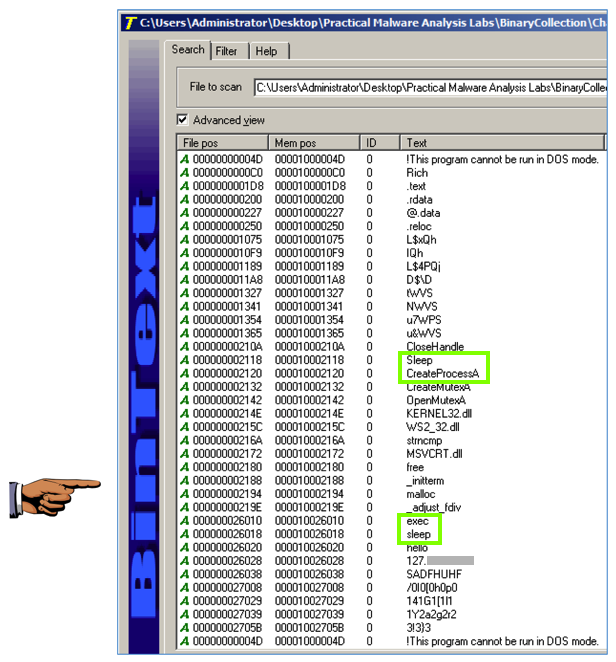
*** ANSWER: 127.26.152.13 *** Then collect the strings from the Lab01-01.exe file. ***答案:127.26.152.13 ***然后从Lab01-01.exe文件中收集字符串。
Notice these items, as shown below:注意这些项目,如下所示:
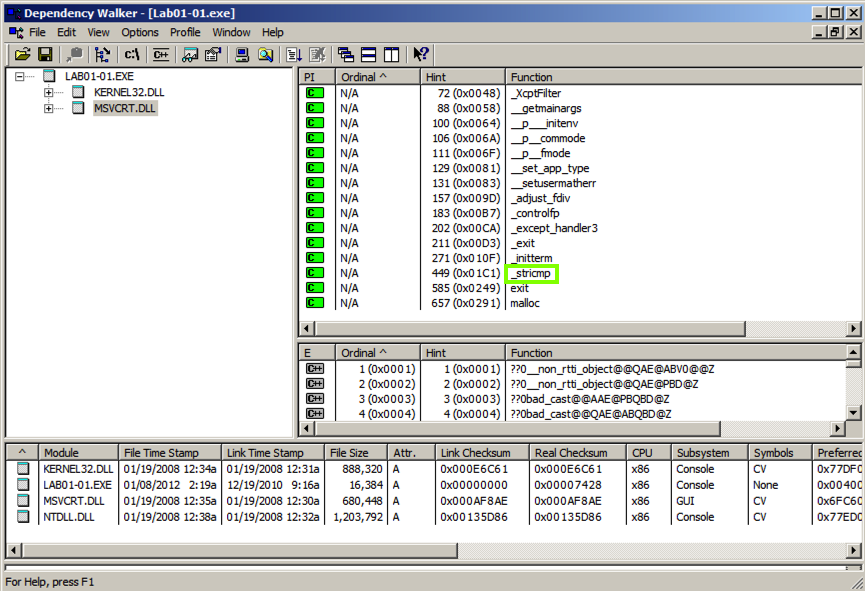
The top left pane is the In the top left pane is called " Module Dependency Tree View ".左上窗格是在左上窗格中称为“ 模块依赖树视图 ”。 It shows the EXE file and the two Windows libraries it uses: MSVCRT.DLL and KERNEL32.DLL.它显示了EXE文件和它使用的两个Windows库:MSVCRT.DLL和KERNEL32.DLL。
In the top left pane, click MSVCRT.DLL .在左上角的窗格中,单击MSVCRT.DLL 。 The top right pane shows " Parent Imports ".右上窗格显示“ 父项导入 ”。 These are the functions the EXE file uses from the library file.这些是EXE文件在库文件中使用的函数。
As shown below, this executable uses only a small number of library functions, and none of them indicate much about its purpose.如下所示,这个可执行文件只使用少量的库函数,而且它们都没有多说明它的用途。 One of them is named _stricmp , which indicates that this progam performs a string copmarison, but that's a very common operation.其中一个名为_stricmp ,表示该程序执行字符串copmarison,但这是一个非常常见的操作。
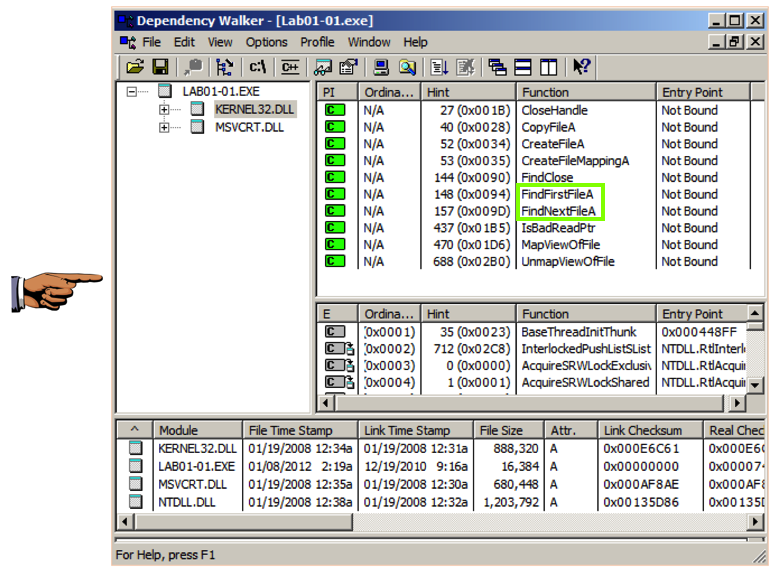
In the top left pane, click KERNEL32.DLL .在左上角的窗格中,单击KERNEL32.DLL 。
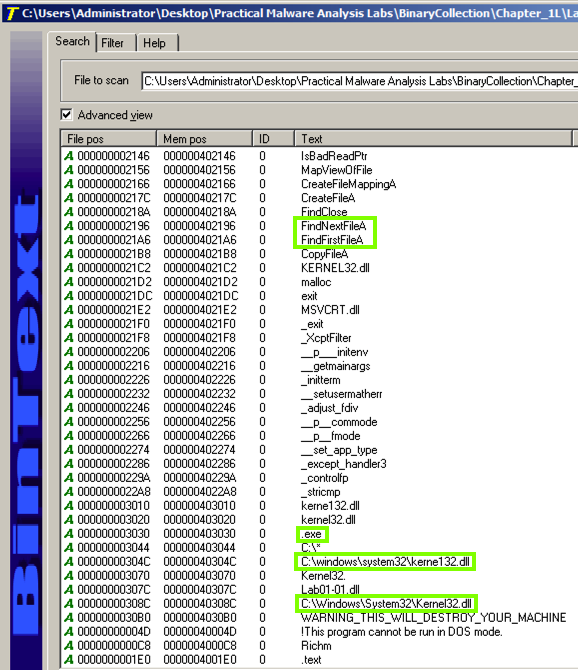
The top right pane shows that this file uses several functions that manipulate files, including FindNextFileA and FindFirstFileA , as shown below.右上窗格显示该文件使用几个操作文件的函数,包括FindNextFileA和FindFirstFileA ,如下所示。
This suggests that the malware searches through the file system and can open and modify files.这表明恶意软件通过文件系统进行搜索并可以打开和修改文件。
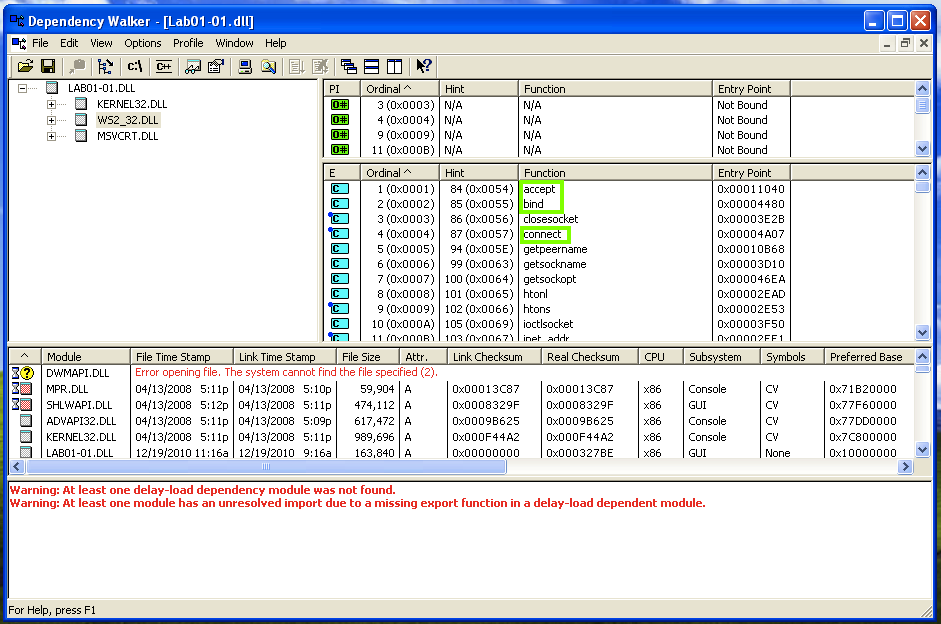
Open Lab01-01.dll in Dependency Walker.在Dependency Walker中打开Lab01-01.dll 。 In the top left pane, partially collapse the tree to match the image below and click WS2_32.DLL .在左上方的窗格中,部分折叠树以匹配下面的图像并单击WS2_32.DLL 。
The top right pane doesn't show function names this time, it only shows "Ordinal" numbers.右上角的窗格不显示功能名称,它只显示“序号”数字。 This is called Linking by Ordinal , and it's an annoyance to us because we can't easily see what functions are in use.这就是所谓的按序连接 ,这对我们来说是一个烦恼,因为我们无法轻松看到正在使用的功能。
However, the center-right pane shows the Exports of WS2_32.DLL, which include accept , bind , and connect .但是,中间右侧窗格显示WS2_32.DLL的导出 ,其中包括接受 , 绑定和连接 。 These are the standard Berkeley Sockets functions used for networking.这些是用于联网的标准Berkeley套接字函数。 This suggest that the malware performs some networking functions, such as connecting to a server and opening a listening port.这表明恶意软件执行一些网络功能,例如连接到服务器并打开侦听端口。
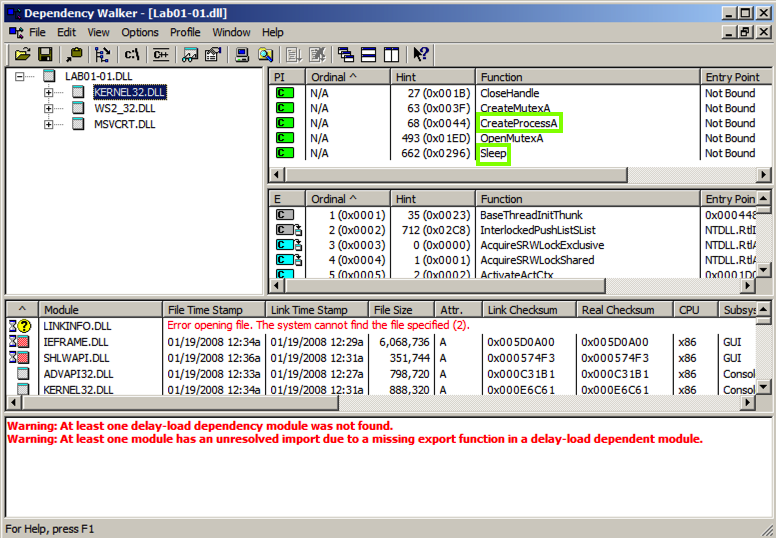
In the top let pane, click KERNEL32.DLL .在顶部放置窗格中,单击KERNEL32.DLL 。 The top right pane shows the "Parent Imports", which include CreateProcessA and Sleep , as shown below.右上方的窗格显示“Parent Imports”,其中包括CreateProcessA和Sleep ,如下所示。
For more information about using Dependency Walker, see ths tutorial:有关使用Dependency Walker的更多信息,请参阅教程:
Analyzing dependencies with Dependency Walker 使用Dependency Walker分析依赖关系
Find the Downloaded File (5 pts)找到下载的文件(5分)
Analyze the sample Lab01-04.exe分析样本Lab01-04.exeIt downloads a file from this domain: practicalmalwareanalysis.com它从该域下载文件: practicalmalwareanalysis.com
Find that file's name and use the form below to get your points.找到该文件的名称并使用下面的表格来获得您的观点。
Find the Downloaded File (5 pts)找到下载的文件(5分)
Analyze the sample Lab01-04.exe分析样本Lab01-04.exeIt imports a function from WINTRUST.DLL它从WINTRUST.DLL导入函数
Find that function's name and use the form below to get your points.找到该函数的名称并使用下面的表格来获得你的观点。