Otherwise, download these files into the C:\IDA folder.否则,请将这些文件下载到C:\ IDA文件夹中。
When you see the IDA window shown below, click the OK button.当您看到下面显示的IDA窗口时,单击确定按钮。

Click " I Agree ".点击“ 我同意 ”。
In the "Welcome to IDA!"在“欢迎使用IDA!” box, as shown below, click the New button.框,如下所示,单击新建按钮。
In the "About" box, click the OK button.在“关于”框中,单击确定按钮。
In the "New disassembly database" box, click " PE Executable ", and then click OK , as shown below:在“新的反汇编数据库”框中,单击“ PE可执行文件 ”,然后单击确定 ,如下所示:
In the "Select PE Executable to disassemble" box, navigate to C:\IDA\crackme-121-1.exe and double-click it.在“选择要反汇编的PE可执行文件”框中,导航至C:\ IDA \ crackme-121-1.exe并双击它。
In the "Welcome to the PE Executable file loading Wizard" box, click the Next button, as shown below:在“欢迎使用PE可执行文件加载向导”框中,单击下一步按钮,如下所示:
In the "Segment Creation" box, click Next .在“段创建”框中,单击下一步 。
In the "File loading" box, click Finish .在“文件加载”框中,单击完成 。
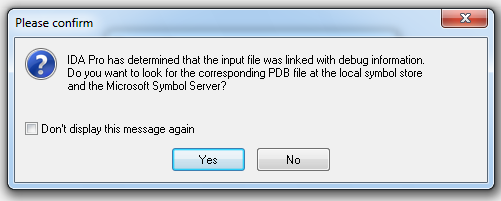
A box pops up saying "...the input file was linked with debug information...", as shown below.一个盒子弹出“...输入文件与调试信息链接...”,如下所示。 Click the Yes button.点击是按钮。
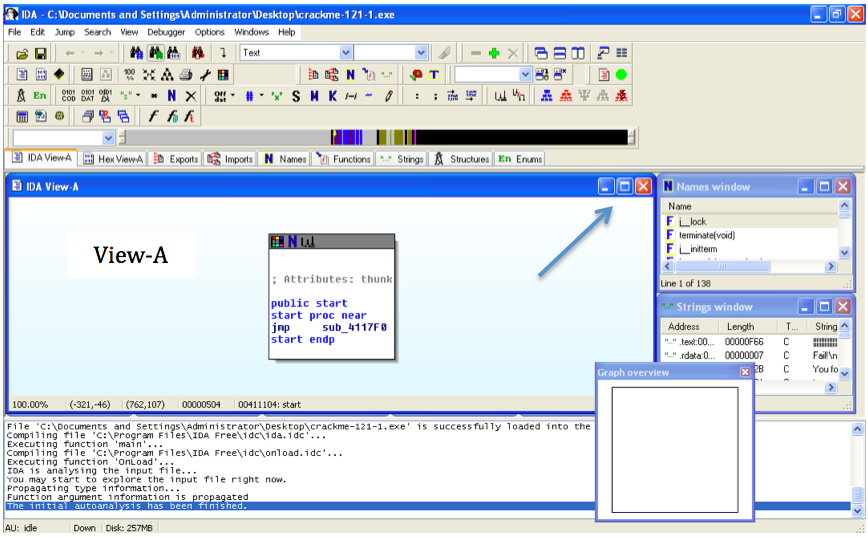
Close the "Graph Overview" box in the lower right corner.关闭右下角的“图表概览”框。
Drag the lower border of the "View-A" pane down, to make as large a viewable area as possible.向下拖动“View-A”窗格的下边框,以尽可能增大可视区域的面积。
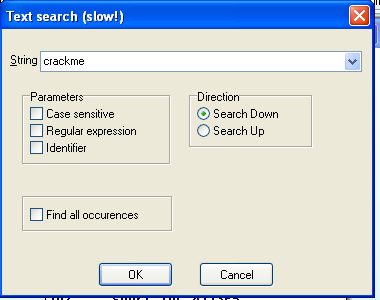
From the IDA menu bar, click Search , Text .从IDA菜单栏中,单击搜索 , 文本 。
Search for crackme as shown below.如下所示搜索crackme 。
Click OK .点击确定 。
Right-click in the "View-A" box and click " Fit window ", as shown below:右键单击“View-A”框并单击“ Fit窗口 ”,如下所示:
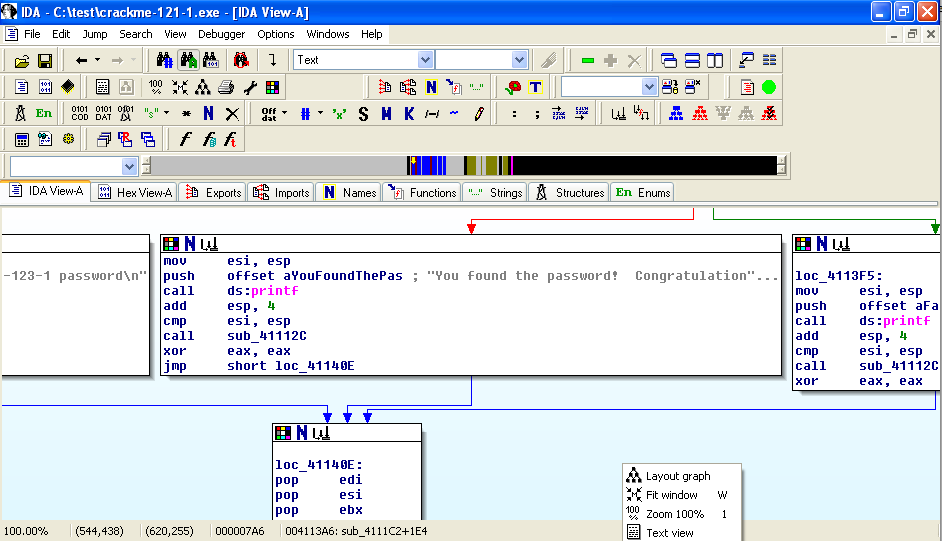
You should now see the entire program shown as six boxes connected by lines, as shown below.您现在应该看到整个程序显示为六个通过线连接的框,如下所示。 (Ignore the two extra boxes at the upper left): (忽略左上方的两个额外的框):
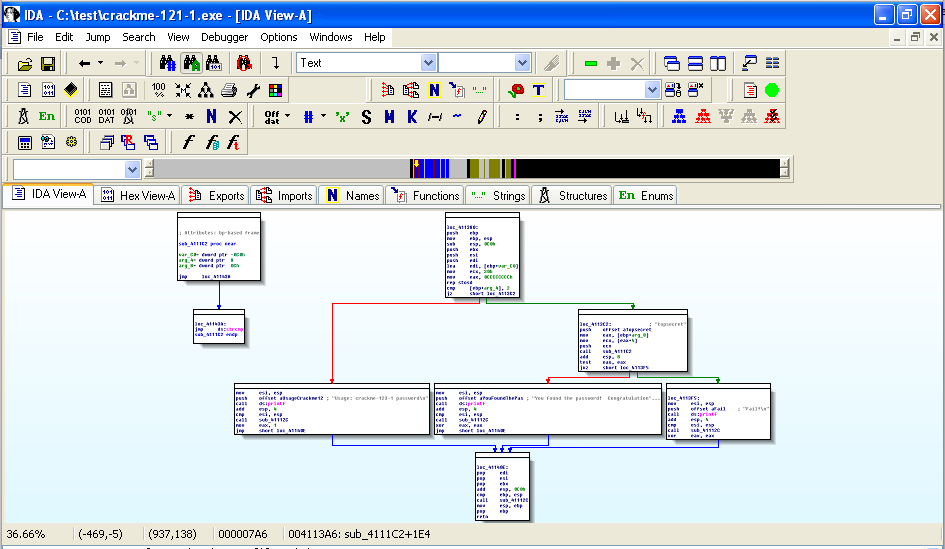
For this project, I have labelled the modules with letters as shown below:对于这个项目,我已经用字母标记了模块,如下所示:

Right-click in the "View-A" box and click " Zoom 100% ", as shown below:右键单击“视图A”框并单击“ 缩放100% ”,如下所示:
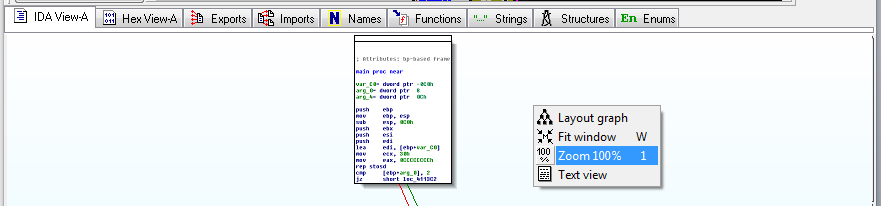
Click and drag the "View-A" display as needed to make module A visible, as shown below:按需要点击并拖动“View-A”显示,使模块A可见,如下所示:
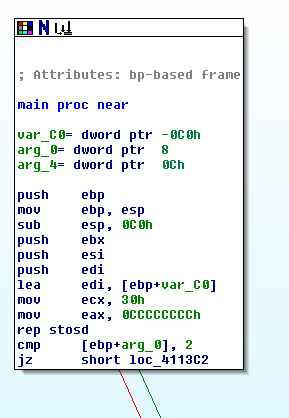
The assembly code is hard to read, but you don't need to understand it all.汇编代码很难阅读,但你不需要全部理解。 Focus on the last two instructions:关注最后两条指令:
cmp [ebp+arg_0], 2
jz short loc_4113C2 This compares some number to 2 with the cmp (Compare) operation, and jumps to a different module if it is 2, using the jz (Jump if Zero) operation.这将一些数字与cmp (比较)操作进行比较,如果它是2,则使用jz (如果为零)操作跳转到另一个模块。
Drag the "View-A" display to make Module C visible, as show below:拖动“View-A”显示屏可以看到Module C,如下所示:
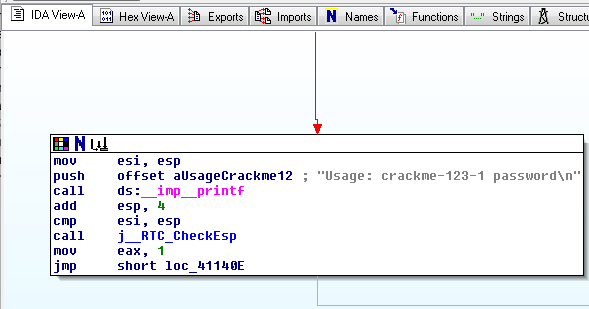
Notice the gray readable text on the right side, saying "Usage: crackme-121-1 password".注意右边灰色的可读文字,说“用法:crackme-121-1密码”。
This module pushes those characters onto the stack with a push command, and then calls the printf function with the call ds:_imp_printf command.该模块使用push命令将这些字符压入堆栈,然后使用调用ds:_imp_printf命令调用printf函数。
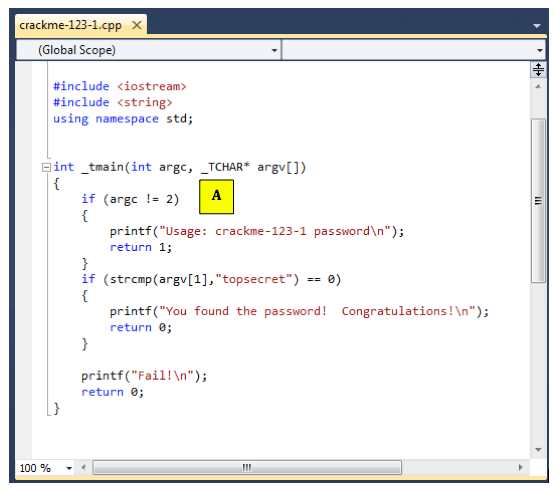
The figure below shows the C statements that comple to the "C" module:下图显示了对“C”模块进行补充的C语句:
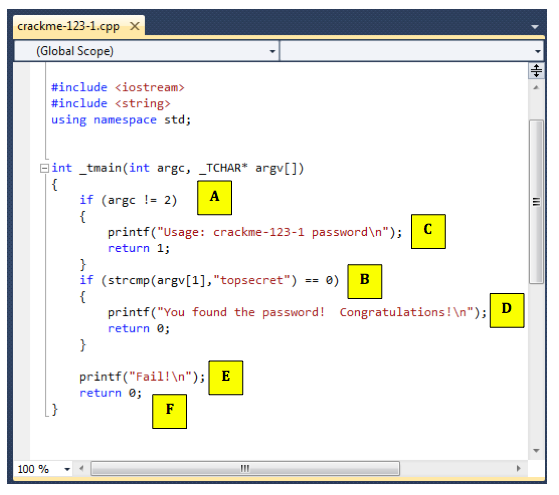
Follow along in IDA Pro and make sure you see what each of the six modules do, and how they correspond to the C source code.请继续关注IDA Pro,并确保您看到六个模块中的每一个都做了什么,以及它们与C源代码的对应关系。
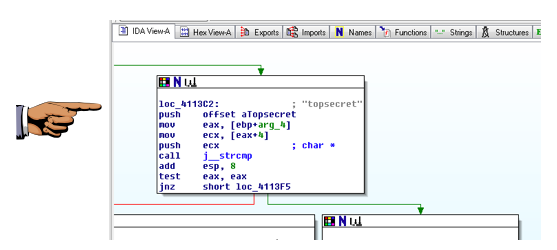
The password "topsecret" is visible.密码“topsecret”是可见的。
In the Command Prompt window, execute these commands:在命令提示符窗口中,执行以下命令:
You should see the message "Usage: crackme-121-1 password", as shown below:您应该看到消息“Usage:crackme-121-1 password”,如下所示:cd \IDAcrackme-121-1的crackme-121-1
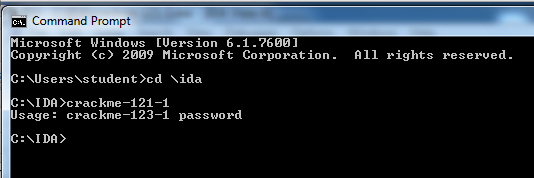
This message is telling you that you need to add a password after the "crackme-121-1".此消息告诉你,你需要在“crackme-121-1”之后添加一个密码。
In the Command Prompt window, execute this command:在“命令提示符”窗口中,执行以下命令:
crackme-121-1 wrongpassword You should see the message "Fail!".您应该看到消息“失败!”。 In the Command Prompt window, execute this command:在“命令提示符”窗口中,执行以下命令:
crackme-121-1 topsecret You should see the message "You found the password!", as shown below:您应该看到消息“您找到了密码!”,如下所示: 
It is very similar to crackme-121-1.这与crackme-121-1非常相似。 Use IDA Pro to find the password, and run the program with the correct password, so you see a "Congratulations" message.使用IDA Pro找到密码,并使用正确的密码运行程序,以便看到“恭喜”消息。
Use the form below to put your name on the WINNERS PAGE .使用下面的表格将您的姓名放在赢家页面上 。
It is very similar to crackme-121-1.这与crackme-121-1非常相似。 Use IDA Pro to find the password, and run the program with the correct password, so you see a "Congratulations" message.使用IDA Pro找到密码,并使用正确的密码运行程序,以便看到“恭喜”消息。
Use the form below to put your name on the WINNERS PAGE .使用下面的表格将您的姓名放在赢家页面上 。
Use the form below to put your name on the WINNERS PAGE .使用下面的表格将您的姓名放在赢家页面上 。