Skip this Project
This project uses LiveKD and the old version of WinDbg which are out of date.
Windows on ARM
If you are using Windows on ARM64, on a Mac M1 or later, watch for these red boxes for special instructions.
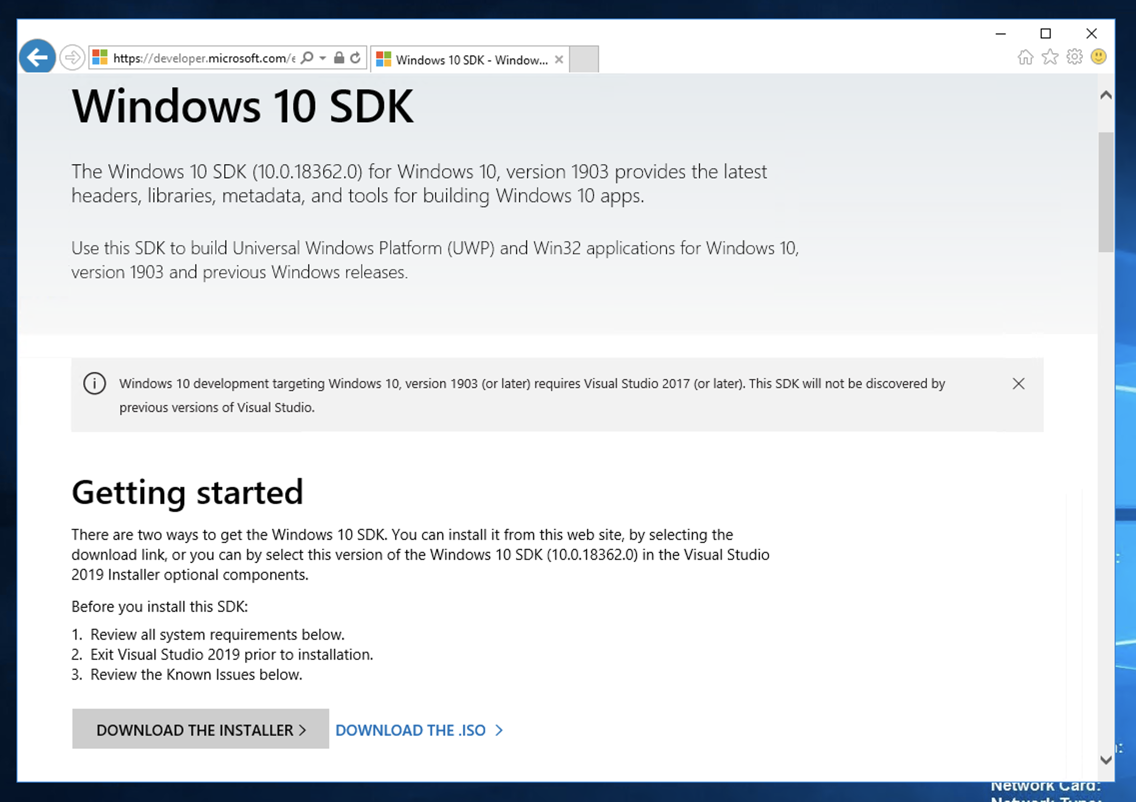
Use Internet Explorer or Edge, and go to :
https://developer.microsoft.com/en-us/windows/downloads/windows-10-sdk
In the "Getting started" section, click "DOWNLOAD THE INSTALLER", as shown below:

Run the installer.
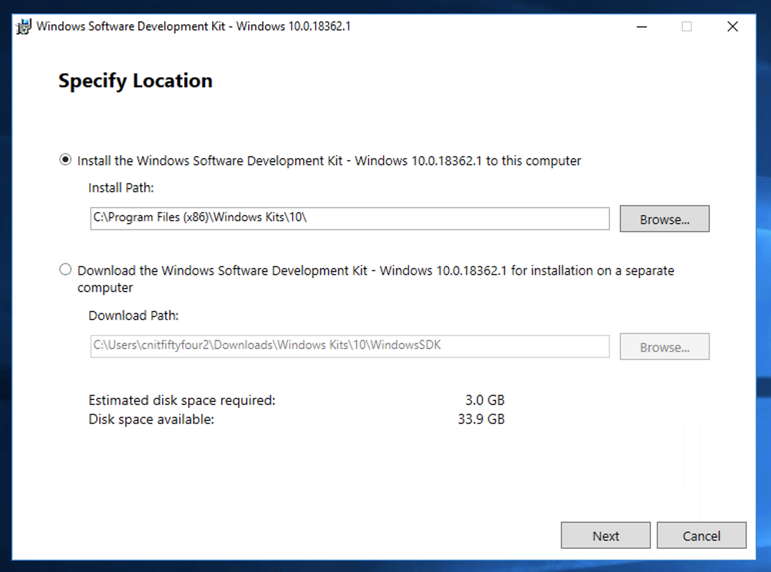
At the "Specify Location" screen, accept the default options and click Next, as shown below:
At the "Windows Kits Privacy" screen, accept the default options and click Next.
At the "License Agreement" screen, click Accept.
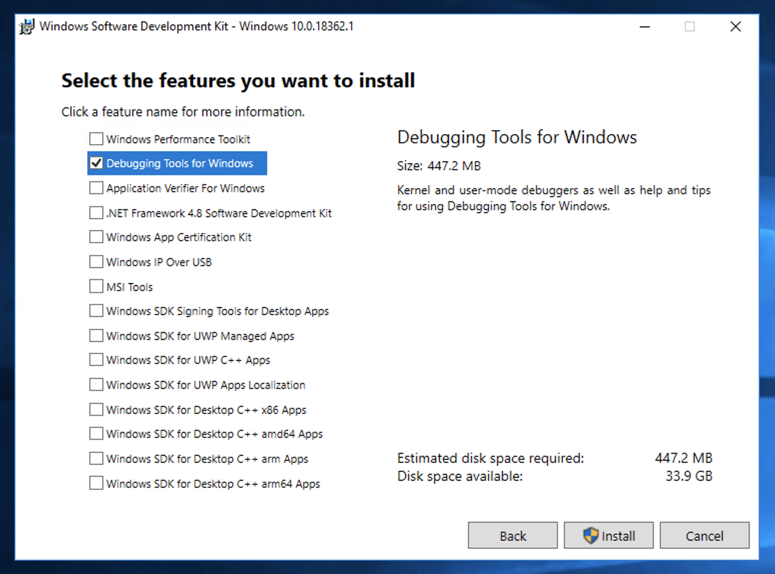
At the "Select the features you want to install" screen, check the "Debugging Tools for Windows" box and clear all the other boxes, as shown below.
Click Install.
In the User Account Control box, click Yes.
When you see the "Welcome to the Windows Software Development Kit" message, click Close.
Click "Command Prompt (Admin)", "Windows PowerShell Prompt (Admin)", or "Terminal Prompt (Admin)".
In the User Account Control box, click Yes.
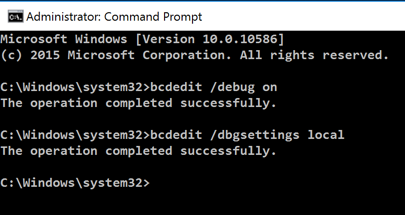
In the Administrator Command Prompt window, execute these commands:
bcdedit /debug on
bcdedit /dbgsettings local
Click "Edit the system environment variables".
In the System Properties box, on the Advanced tab, at the bottom, click the "Environment Variables..." button.
In the Environment Variables box, in the "System variables" section, scroll down and double-click Path.
In the 'Edit environment variable" box, click the New button.
Add this item, as shown below:
C:\Program Files (x86)\Windows Kits\10\Debuggers\x64
Windows on ARM
If you are using Windows on ARM64, add this path instead:C:\Program Files (x86)\Windows Kits\10\Debuggers\arm64
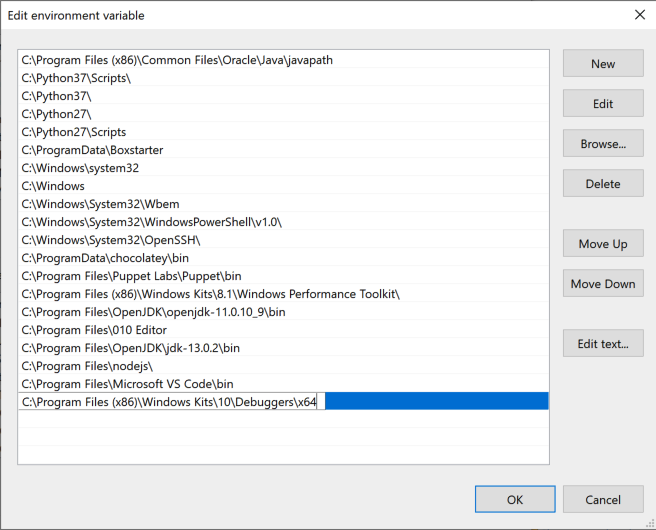
Click OK.
Click OK.
Click OK.
Restart your Windows machine.
Windows on ARM
You can't use LiveKD on Windows on ARM64.Instead, in an Administrator Terminal window, execute this command:
windbgA "SYSINTERNALS SOFTWARE LICENSE TERMS" box pops up. Click the Agree button.When LiveKD starts, it asks you whether to set the _NT_SYMBOL_PATH automatically.
Type y and press Enter.
It asks "Enter the folder to which symbols download", press Enter to accept the default option.
In WinDbg, click File, "Kernel Debug...".
In the Kernel Debugging box, click the Local tab.
Click OK.
Then skip ahead to "Using WinDbg".
Getting LiveKD
If you are using the "Windows 10 with Tools" machine, LiveKD is already installed.If you are using some other machine, follow these steps to get it:
In Internet Explorer, go to
https://technet.microsoft.com/en-us/sysinternals/bb897415.aspx
Click the "Download LiveKD" link. Click Save.
Click "Open Folder".
Right-click LiveKD.zip and click "Extract All...", Extract.
A LiveKD window opens, showing three files, as shown below.
Right-click the Start button.
Click "Command Prompt (Admin)", "Windows PowerShell Prompt (Admin)", or "Terminal Prompt (Admin)".
In the User Account Control box, click Yes.
In the Administrator Command Prompt window, execute this command, replacing "yourname" with your user name:
Close the Administrator Command Prompt window.
Click "Command Prompt (Admin)",
In the User Account Control box, click Yes.
In the Administrator Command Prompt window, execute one of these commands, depending on which machine you are using:
livekd64.exe -w
livekd.exe -w
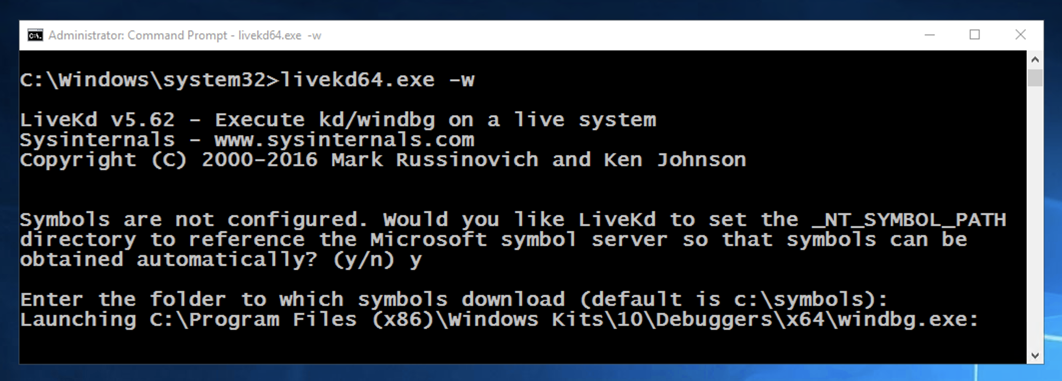
When LiveKD starts, it asks you whether to set the _NT_SYMBOL_PATH automatically, as shown below.
Type y and press Enter.
If LiveKD asks "Enter the folder to which symbols download", press Enter to accept the default option, as shown below.
To adjust the font size, click View, Font....
Maximize the Command window.
This is a strange combination of a GUI and command-line, like the other debuggers we've used. Commands are typed into the box at the bottom and the results appear in the large top pane.
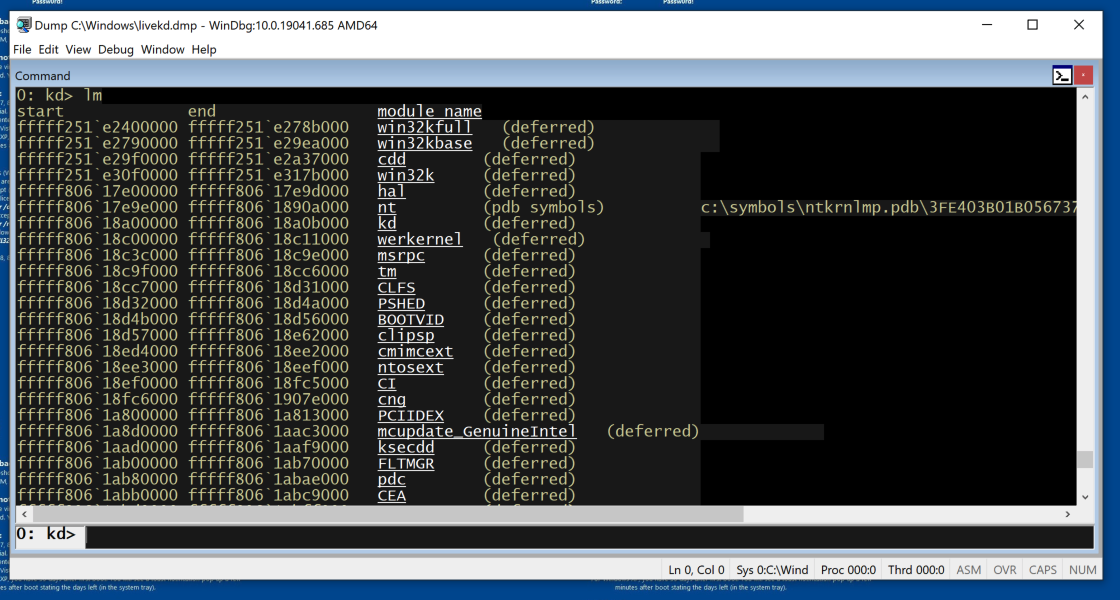
lm
Scroll back to find the module named nt, as shown below. It's easy to spot because it'e one of the few modules that shows a Symbols path.
This is Ntoskrnl, the main kernel module.
dd Display dwords (32-bit values)
da Display ASCII text
db Display Bytes and ASCII text
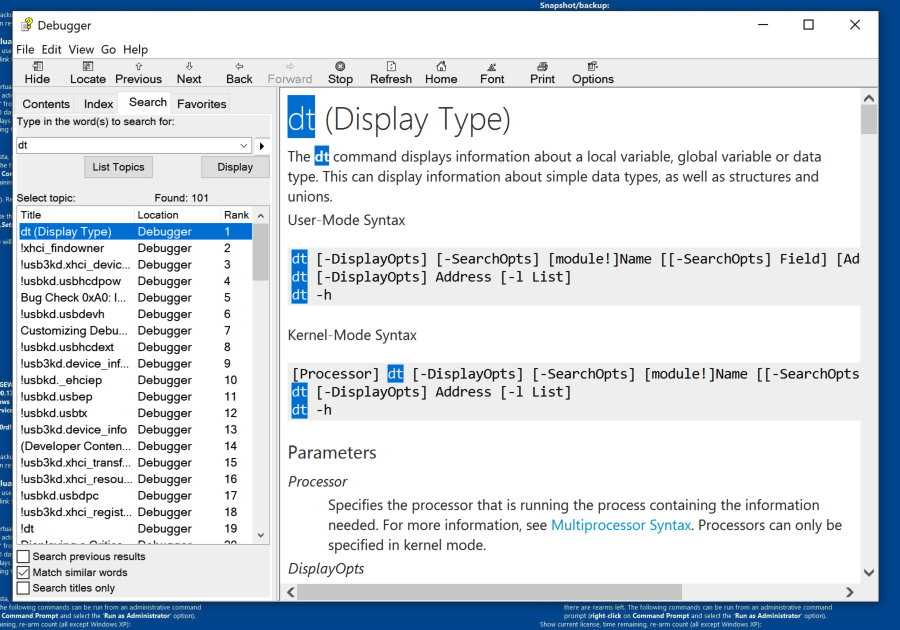
dt Display Type: Information about a variable, data type, or structure
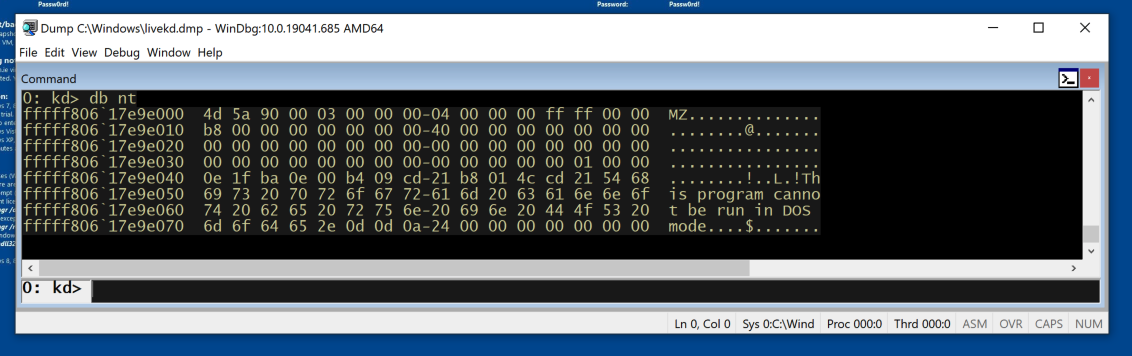
db nt
This displays the bytes on the left, and the ASCII on the right. Now you can see the message "This program cannot be run in DOS mode", which appears at the start of many EXE files.
x nt!*
This finds all the functions in Ntoskrnl.
There are a lot of them. It may take a minute or so for them all to scroll by.
In WinDbg, execute this command:
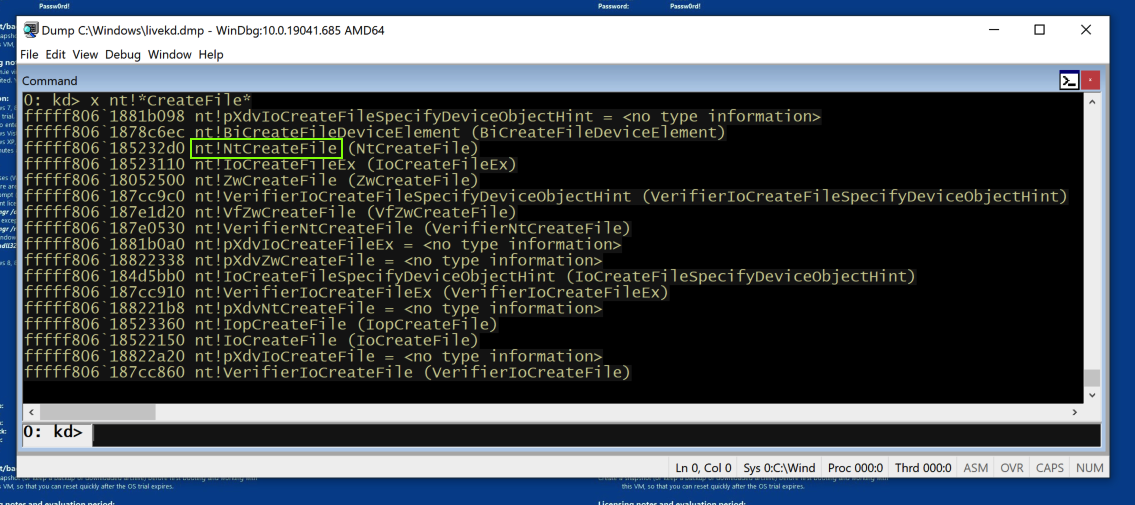
x nt!*CreateFile*
This finds all the symbols in Ntoskrnl that contain the word "CreateFile".
There are only a few of those, including nt!NtCreateFile, as shown below:
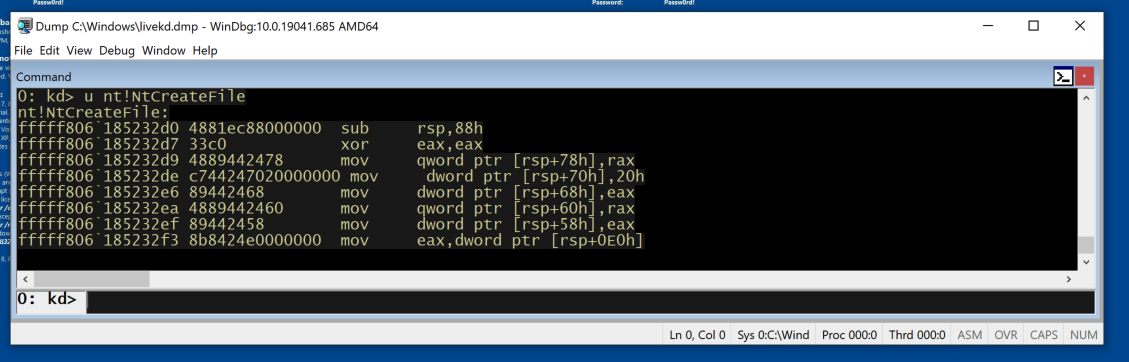
u nt!NtCreateFile
This shows the first few bytes of the function, disassembled, as shown below:
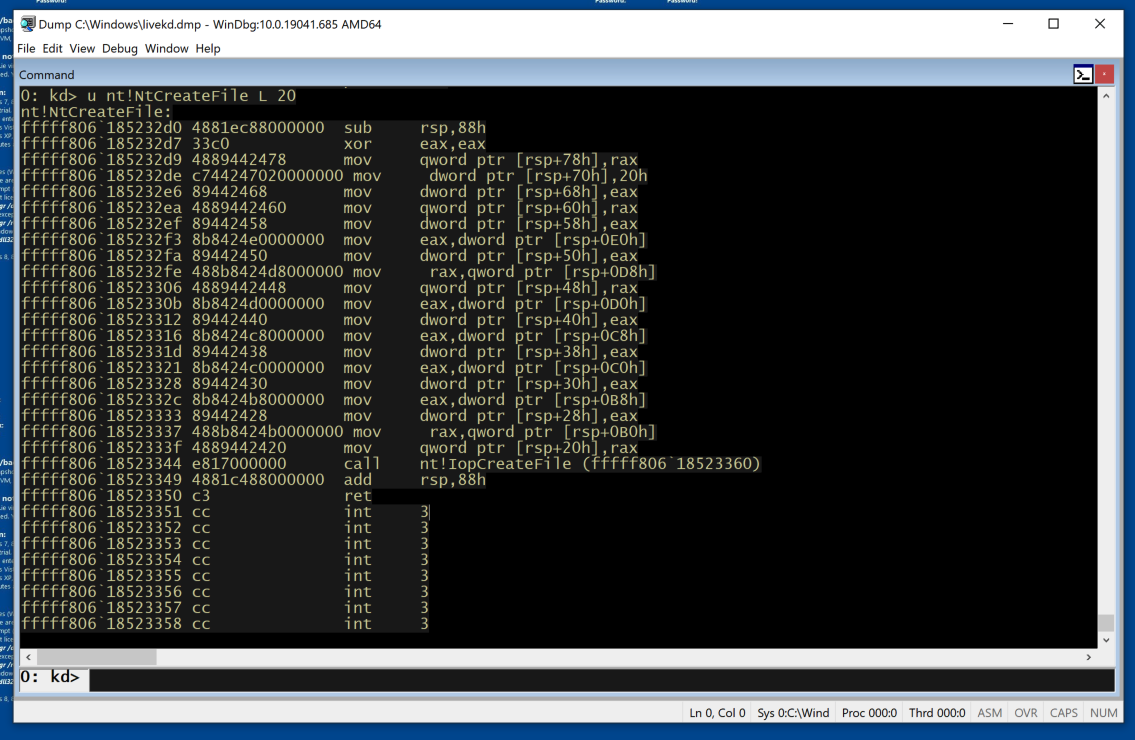
To see more of this function, execute this command:
u nt!NtCreateFile L 20
This shows the entire function, as shown below:
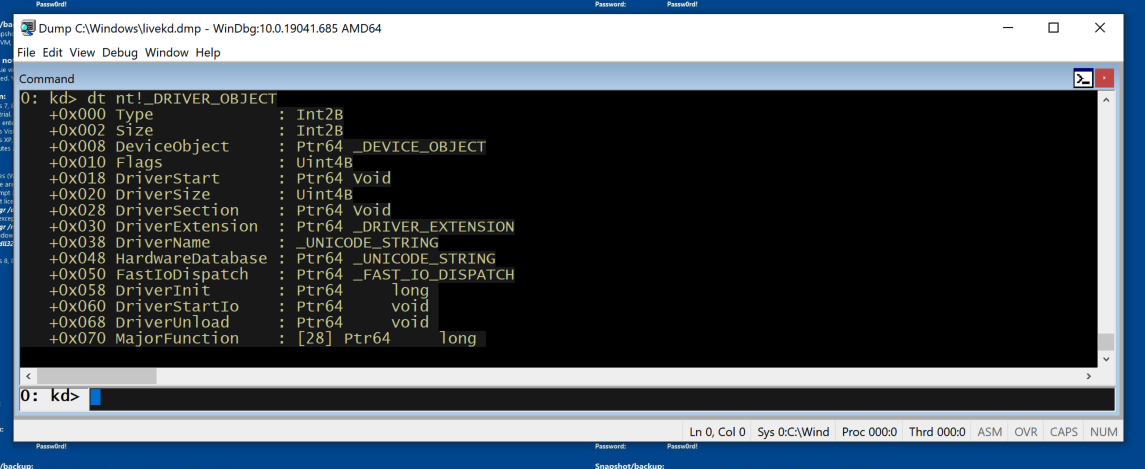
dt nt!_DRIVER_OBJECT
This shows the first few lines of a driver object structure, which stores information about a kernel driver, as shown below. Notice the DriverStart pointer--this contains the location of the driver in memory.
.hh
Flag PMA 410c.1: Function Name (5 pts)
If you are using Windows on ARM, skip this flag and do flag PMA 410c.3 below.Find the Windows kernel function that has a name fitting this pattern: two characters, RegistryKey, then six more letters, like this:
That's the flag.--RegistryKey------
Flag PMA 410c.2: nt!NtShutdownSystem (10 pts)
If you are using Windows on ARM, skip this flag and do flag PMA 410c.4 below.Disassemble the nt!NtShutdownSystem module.
Find the text covered by the green box in the image below. That's the flag.
Flag PMA 410c.3: Function Name (5 pts) FOR ARM
If you are using Windows on ARM, find the Windows kernel function that has a name fitting this pattern: Nt, four characters, and then RegistryKey, like this:That's the flag.Nt----RegistryKey
Flag PMA 410c.4: nt!NtShutdownSystem (10 pts) FOR ARM
Disassemble the nt!NtShutdownSystem module.Find the text covered by the green box in the image below. That's the flag.