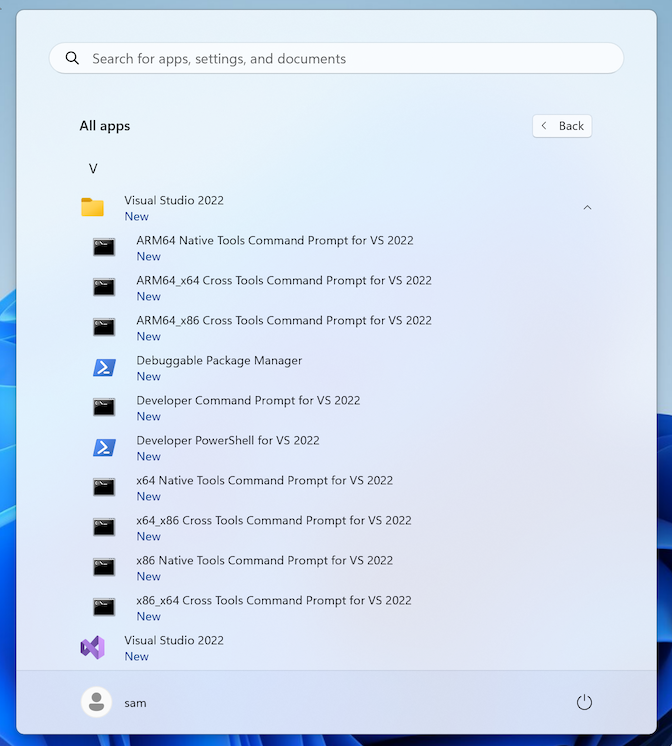
Scroll to the V section. Open the "Visual Studio 2022" folder and click "ARM64 Native Tools Command Prompt for VS 2022", as shown below.

A Developer Command Prompt window opens, as shown below.
mkdir c:\127
cd c:\127
notepad secret.cpp
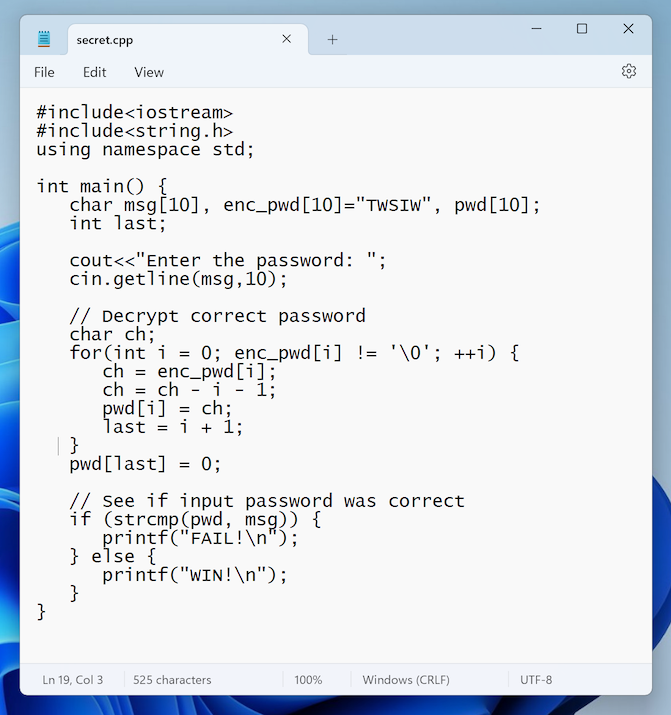
Enter this code, as shown below:
#include<iostream>
#include<string.h>
using namespace std;
int main() {
char msg[10], enc_pwd[10]="TWSIW", pwd[10];
int last;
cout<<"Enter the password: ";
cin.getline(msg,10);
// Decrypt correct password
char ch;
for(int i = 0; enc_pwd[i] != '\0'; ++i) {
ch = enc_pwd[i];
ch = ch - i - 1;
pwd[i] = ch;
last = i + 1;
}
pwd[last] = 0;
// See if input password was correct
if (strcmp(pwd, msg)) {
printf("FAIL!\n");
} else {
printf("WIN!\n");
}
}
In Notepad, click File, Save.
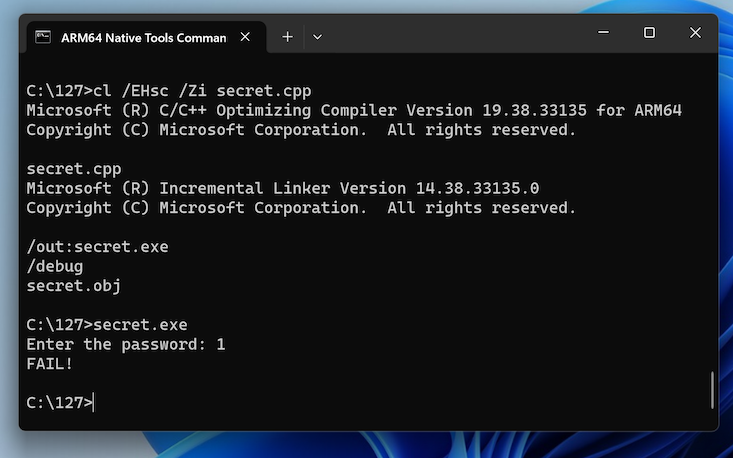
In the Developer Command Prompt window, execute these commands:
cl /EHsc /Zi secret.cpp
secret.exe
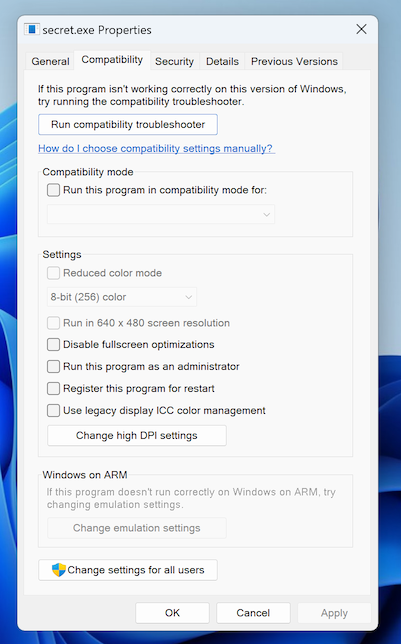
On the Compatibility tab, at the bottom, in the Windows on ARM section, the items are grayed out, as shown below.
That indicates that this is a native ARM program.
https://learn.microsoft.com/en-us/windows-hardware/drivers/debugger/
Click the "Download WinDbg" button.
Run the installer.
WinDbg launches, as shown below.
Navigate to C:\127. Double-click secret.exe
The program launches, opening an empty Command Prompt window.
Click the WinDbg window to bring it to the front.
The modules in the program are shown, starting with pwd.exe and then loading three libraries, as shown below.
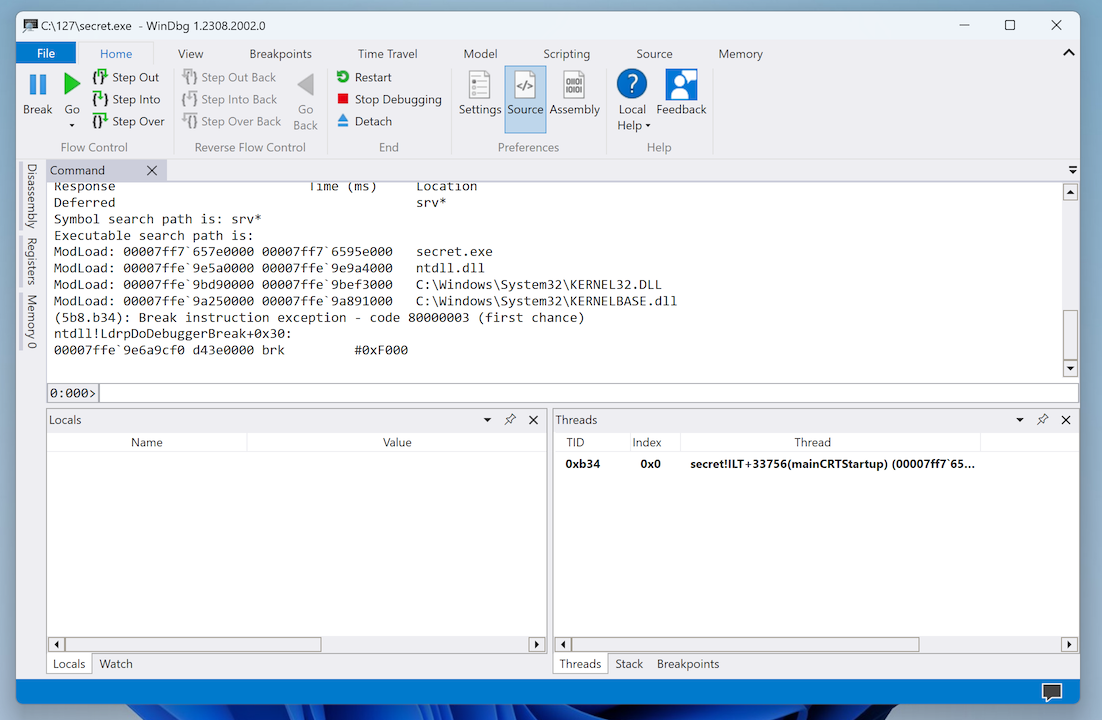
In the command line, in the center of the WinDbg window, outlined in red in the image above, execute these commands, one at a time:
x secret!main
bp secret!main
g
The second command sets a breakpoint at secret!main.
The third command runs to the breakpoint.
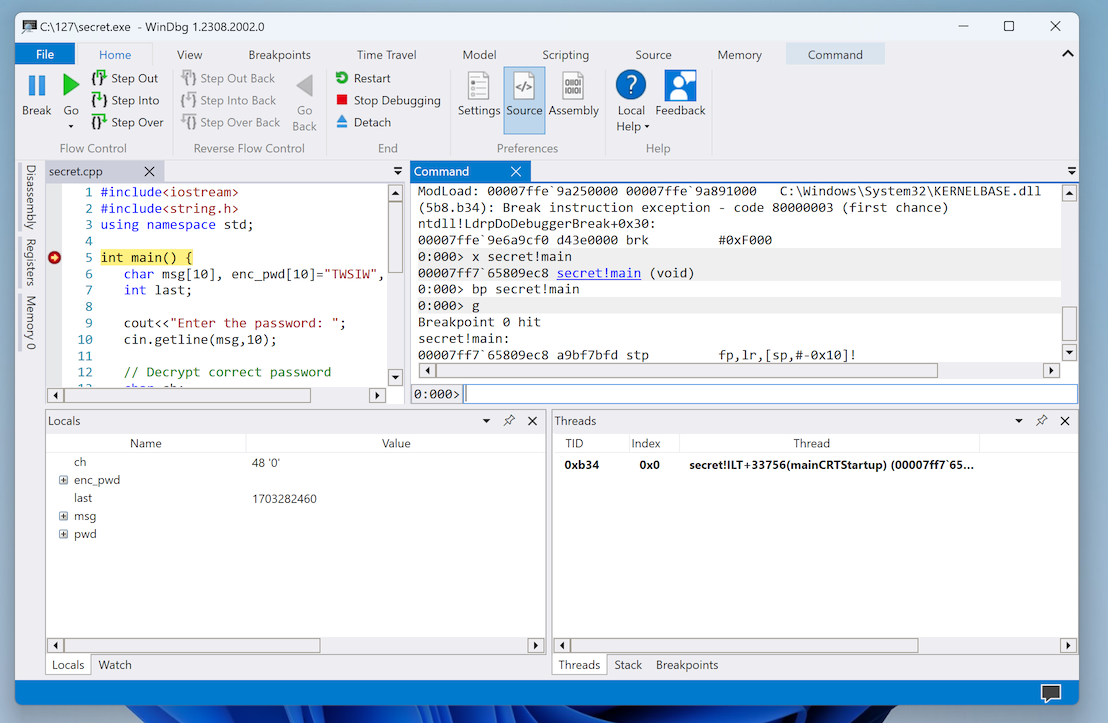
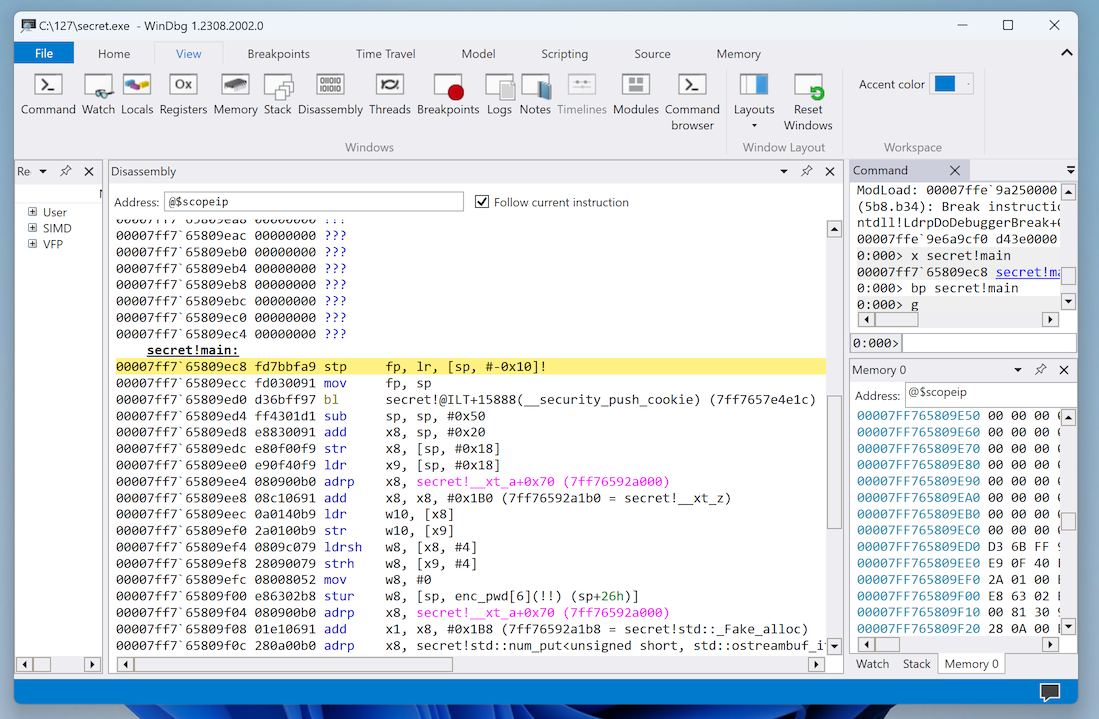
WinDbg shows the source code of the main() function in the left pane, as shown below.
You see the ARM64 assembly code, beginning with pushing a security cookie onto the stack, as shown below.
In the ribbon, click the Home tab.
Click Restart.
Move the Command Prompt out of the way.
Click Go.
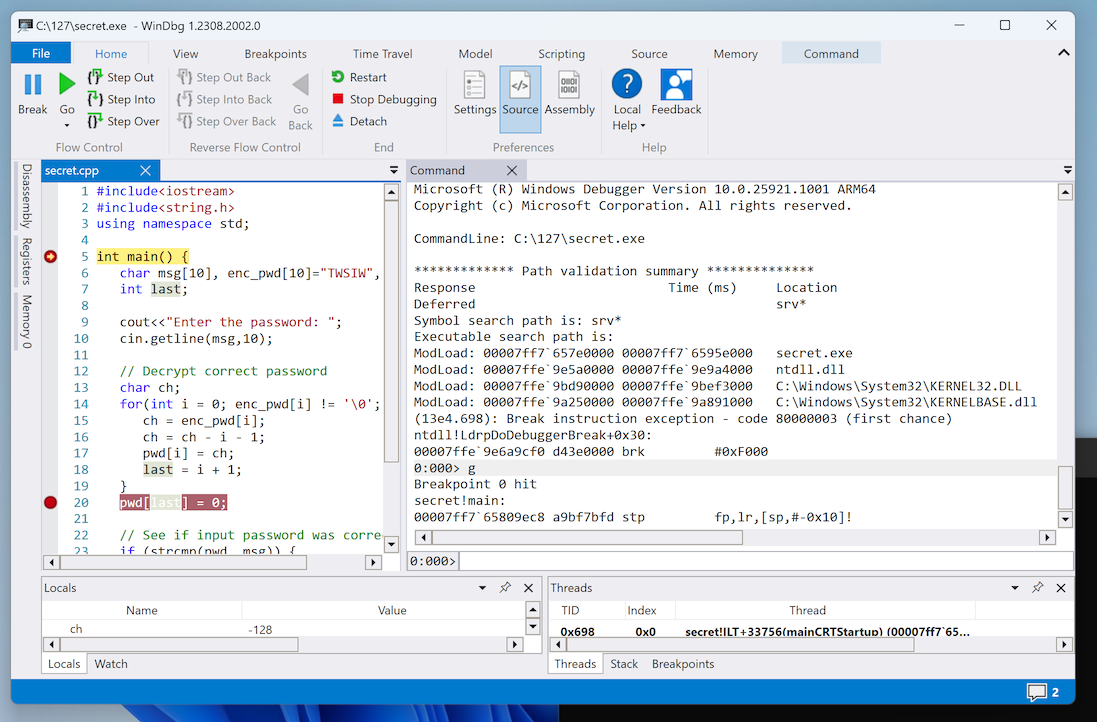
You see the source code, as shown below.
In line 20, click in the left border to set a breakpoint there. At this point, the correct password is in the "pwd" variable.
PMA 340.1: Finding the Secret Password (15 pts)
In WinDbg, click Go.In the Command Prompt window, enter a password of 1 and press Enter.
In the lower left "Locals" pane, expand pwd. The password is visible, covered by a green box in the image below. That's the flag.
Note: if the GUI fails, which happened to me in July 25, execute the dv command to display local variables.
Posted 2-5-24
Last image updated 1-30-25
dv command and Visual Studio install instructions updated 6-11-25