This project follows Lab 3-3 in the textbook.
Open Process Explorer and move it so you can see it at the same time as the Explorer window. Scroll to the bottom to show explorer.exe (your desktop) and its children, which are processes launched by the currently logged-in user, as shown below.

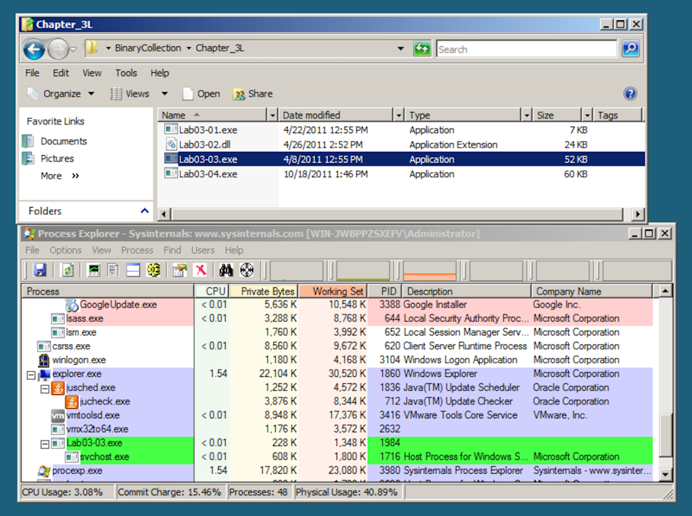
After a second or two, the Lab03-03.exe process terminates, leaving the svchost.exe running as an orphan process, as shown below.
This is highly unusual and suspicious behavior.
To see that, in Process Explorer, right-click svchost.exe and click Properties.
Click the Strings tab. At the bottom, make sure Image is selected, as shown below.
These are the strings on the disk, in the real svchost.exe file.
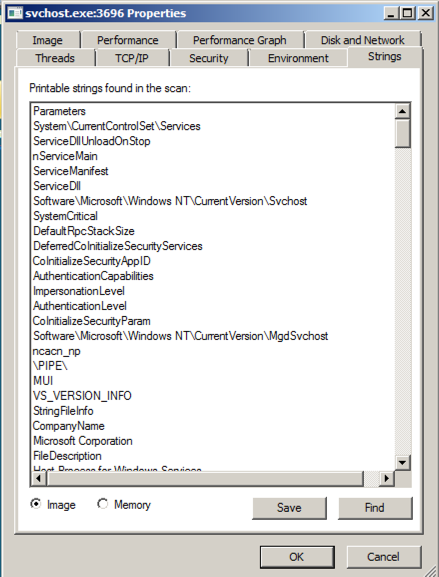
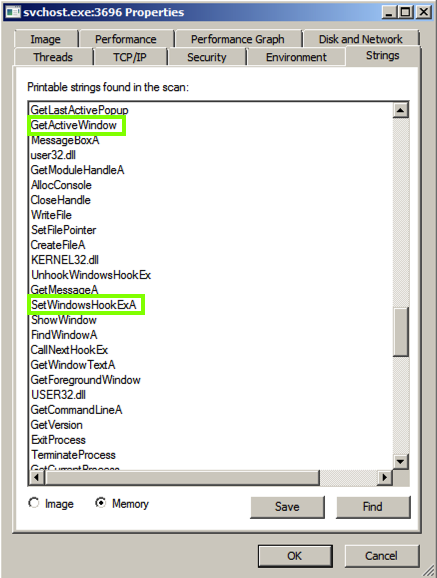
At the bottom of the box, click the Memory button. Now the strings are completely different, and contain these suspicious items: GetActiveWindow and SetWindowsHookExA.
Those functions can be used by a keylogger, to hook the keypresses and run added code to record them.
Scroll down and find the string practicalmalwareanalysis.log, as shown below. This may be the filename used to store the keypresses.
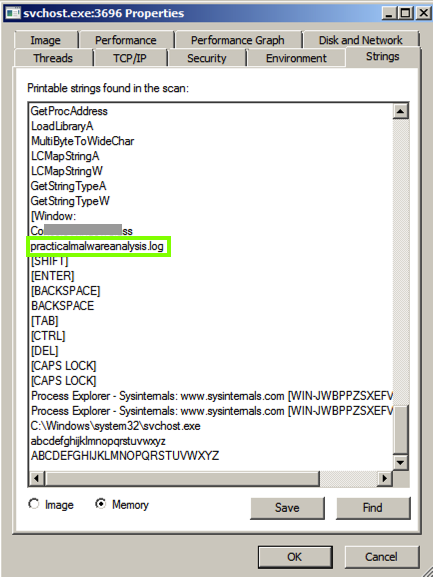
Just above "practicalmalwareanalysis.log" there is another string, beginning with "Co", partially covered by a gray box in the image above.
Enter that string into the form below.
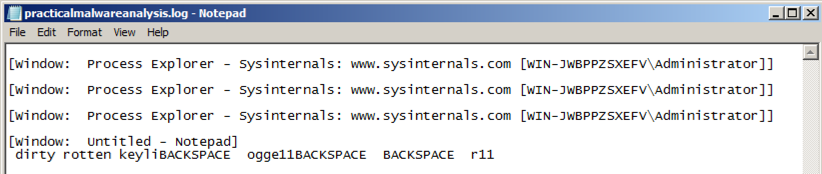
Double-click the practicalmalwareanalysis.log file. The stolen keystrokes appear, as shown below.
If you aren't using the VM your instructor provided, download the file here.
This file is a keylogger. Find the file containing the captured keystrokes.