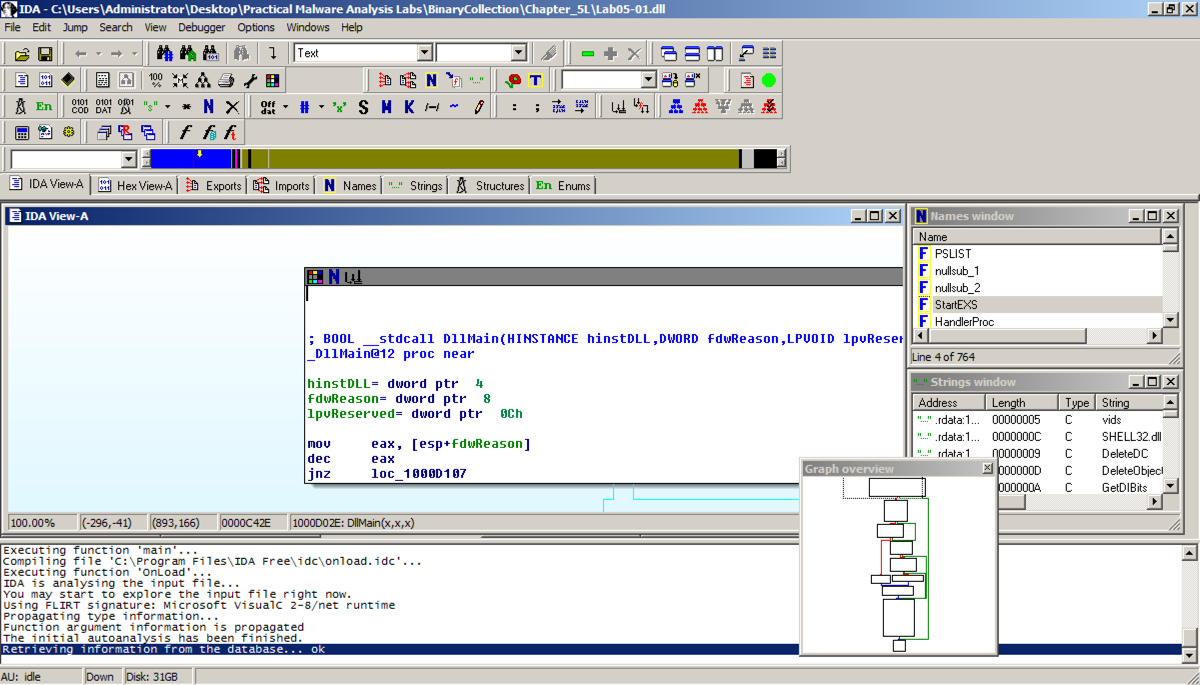
In the "Welcome to the PE Dynamic Library file loading Wizard" box, click Next, Next, Finish. IDA opens the file, as shown below:

The code doesn't show line numbers or hexadecimal instructions. To fix that, click Options, General.
In the IDA Options box, in the top right, in the '"Display disassembly line parts" pane, make these changes, as shown below:
The "graph mode" display is more informative now, as shown below.
IDA shows the assembly code in a text-only view, as shown below.
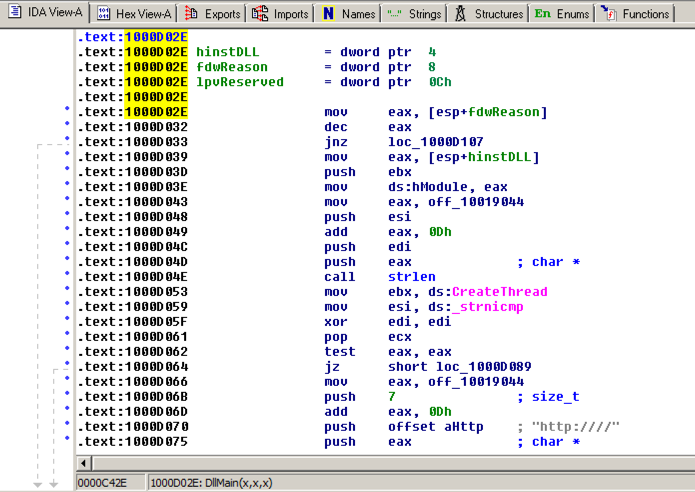
Press the SPACEBAR again to return to Graph Mode.
In IDA Pro, click View, "Open subview", Imports. Click the Name header to sort by name. Find "gethostbyname", as shown below. (Note that capital letters and lowercase letters sort into separate groups.)
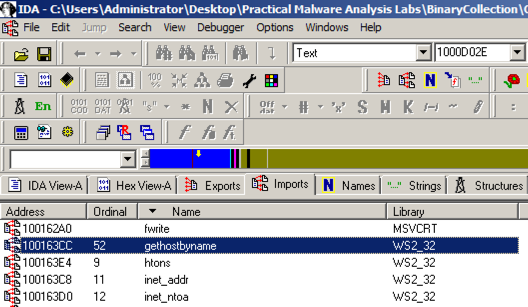
Double-click gethostbyname.
The code for the function opens in Text mode, as shown below.
Click gethostbyname. Yellow highlights appear on both occurrences of that name, as shown below. Press Ctrl+x to open the "xrefs to gethostbyname" box shown below.
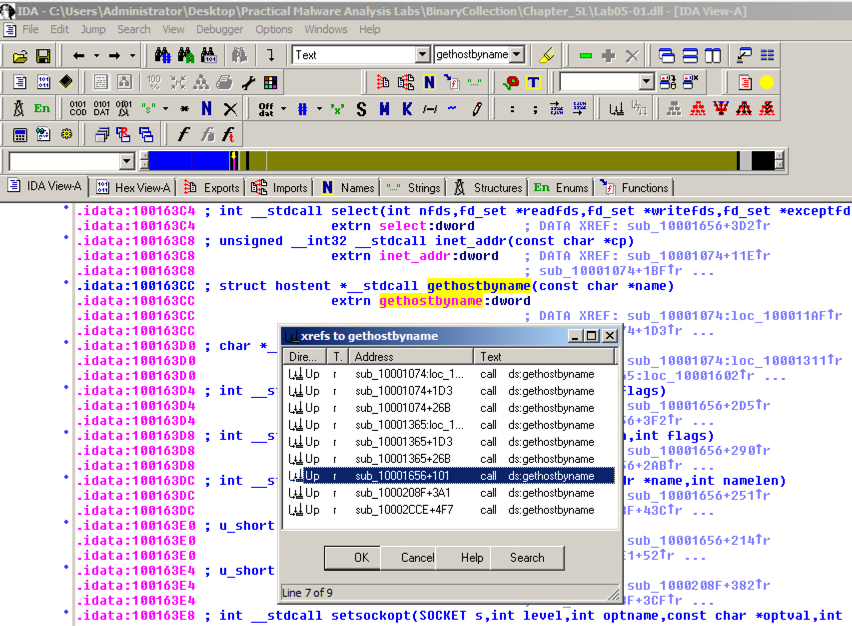
There are nine calls to gethostbyname in five different functions. Double-click the third one from the bottom, at an address of 1001656+101, as highlighted in the image above.
The function appears, as shown below. It loads an address named off_10019040 into register eax, adds 13 to it (0d in hexadecimal), pushes that address onto the stack, and calls gethostbyname.
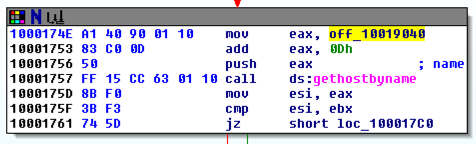
Double-click off_10019040.
The Text view shows that this location contains a pointer to a string containing "praticalmalwareanalys", as shown below.
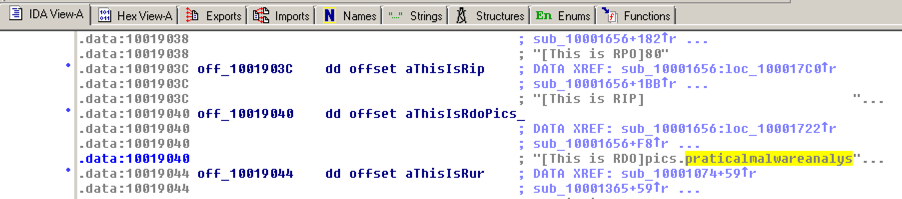
For a clearer view, click the "Hex View-A" tab.
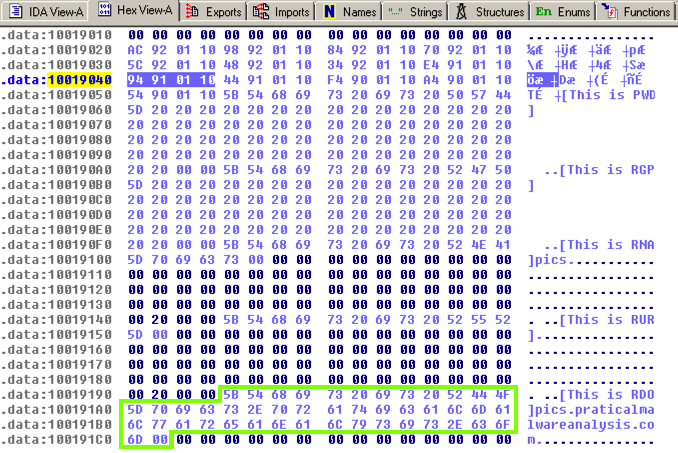
The four bytes starting at 10019040 contain a 32-bit address in little-endian order, as highlighted in blue in the figure below. That address is 10019194. There's a series of ASCII values at that address, outlined in green in the figure below. Skipping the first 13 bytes leaves the string
pics.praticalpalwareanalysis.com
as shown below. This is the domain that will be resolved by calling gethostbyname.
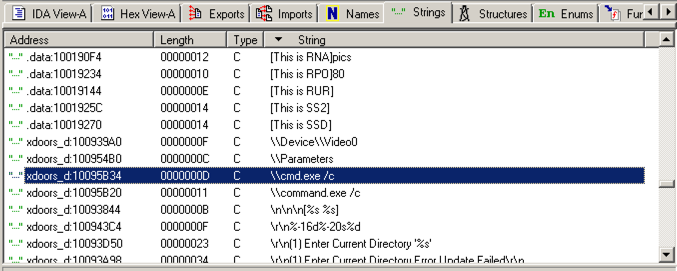
Scroll down about 3/4 of the way, and find the String "\\cmd.exe /c", as highlighted in the image below.
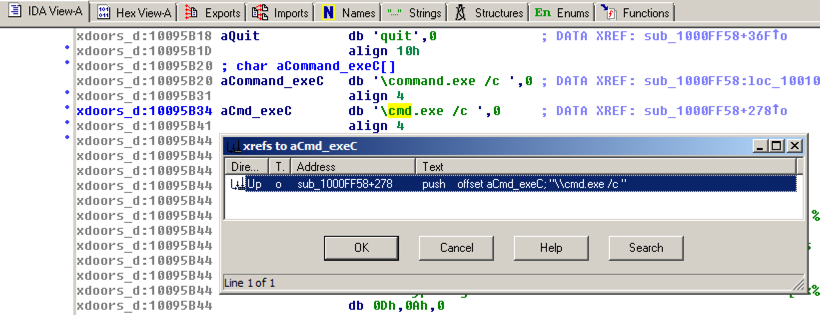
Double-click "\\cmd.exe /c". Click the "IDA View-A" tab.
The string appears in text mode, as shown below. Click in the word cmd so it's highlighted and press Ctrl+x. A "xrefs to aCmd_exeC" box appears, as shown below.
In the "xrefs to aCmd_exeC" box, double-click sub_1000FF58+278.
You see the code that uses this string. There are two boxes of code, one that starts a string with "cmd.exe -c" and the other that starts it with "command.exe /c". This looks like a remote shell, executing commands from the botmaster for either a 32-bit or 16-bit system.
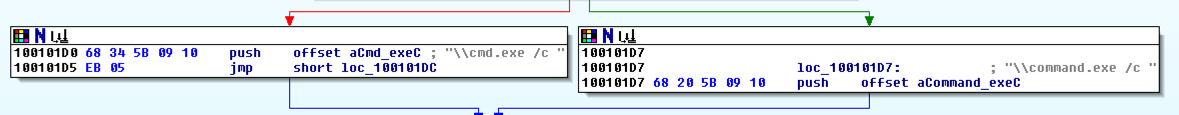
Drag the code boxes down to see the module containing "Hi, Master", as shown below.
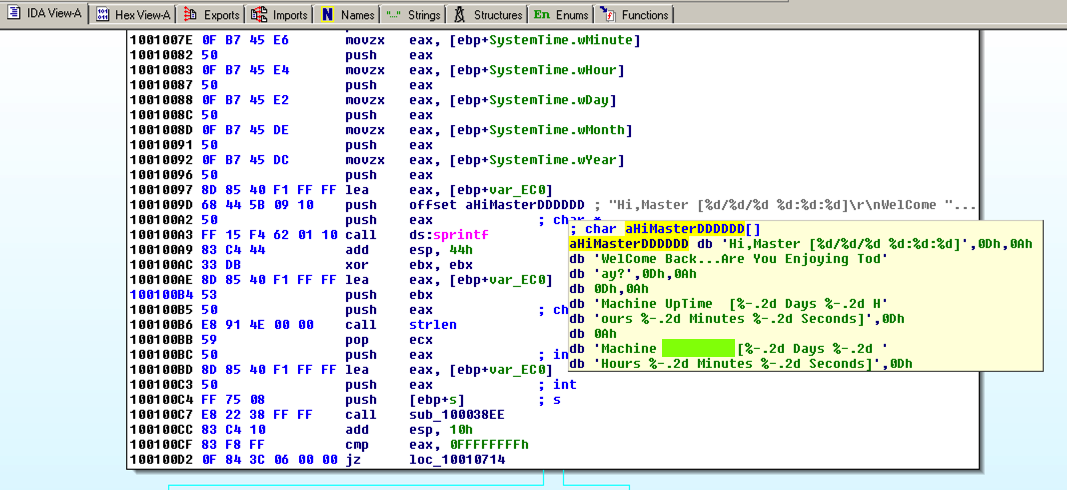
Hover the mouse over aHiMasterDDDDDD to see more of the referenced strings, as shown below.
This looks like a message the bot sends to the botmaster, further confirming that this is a RAT (Remote Administration Tool).
Use the form below to record your score in Canvas.