How to Set Up WebGoatHow do I get configure WebGoat to run on an IP other than localhost?
root with password toor
startx
/etc/init.d/networking start
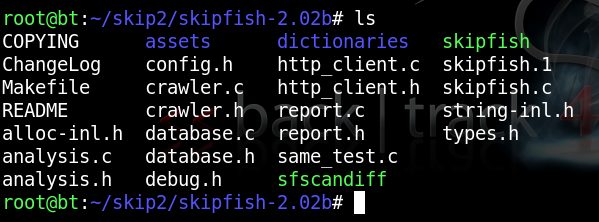
You should see several files in the directory, as shown below:mkdir skipfish
wget http://skipfish.googlecode.com/files/skipfish-2.02b.tgz
tar xzf skipfish-2.02b.tgz
cd skipfish-2.02b
make
ls

In the Terminal window, execute this command:
cp dictionaries/minimal.wl skipfish.wl
./skipfish -o /tmp/skip1 -A guest:guest -m 5 -LVY -X -u "http://192.168.5.93/webgoat/attack"
Replace the IP address with the real address of your WebGoat target machine.
Note: each time you run Skipfish, you must specify a new directory for output (-o). If you run it again, use /tmp/skip2, etc.
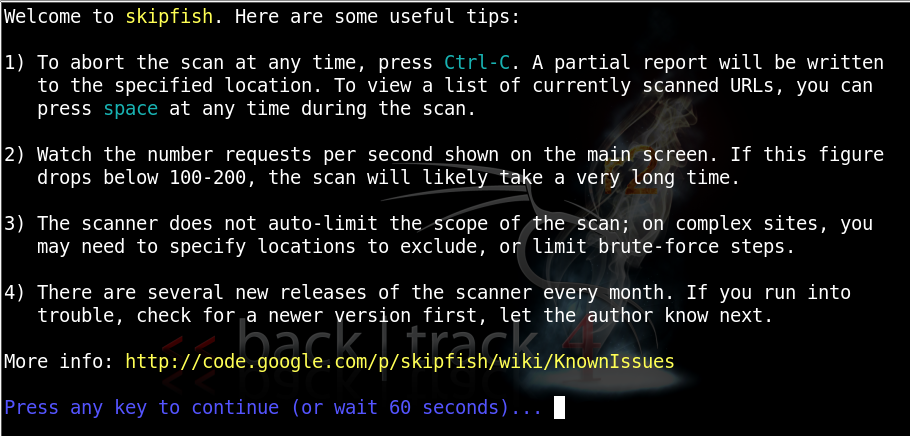
When Skipfish starts, you will see this screen:
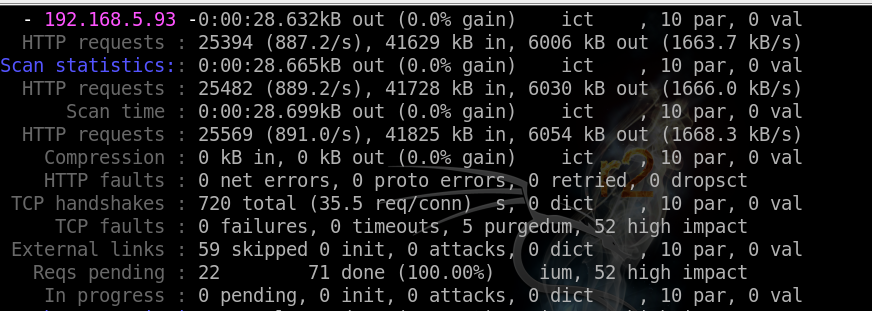
While it is running, you will see messages like this:
When it finishes, you will see this:
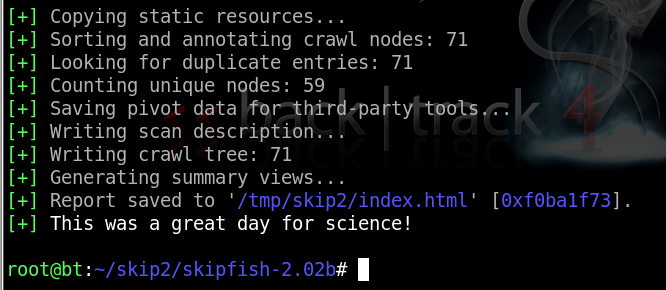
/tmp/skip3/index.html
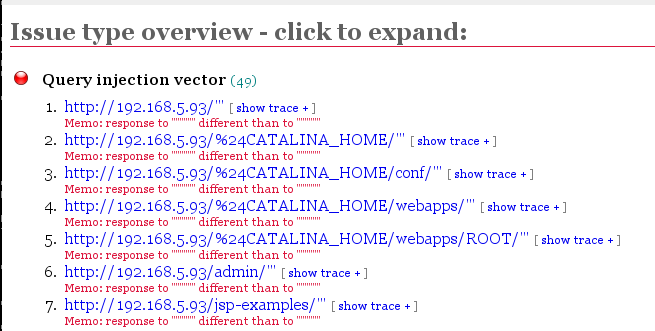
At the top, a summary appears, showing counts of vulnerabilities with colored dots. The red dot indicates the most dangerouos problems:
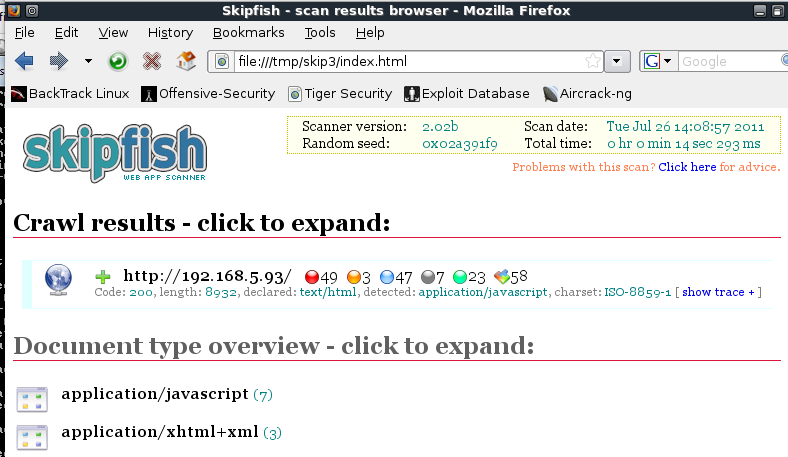
Scroll down to see a more detailed list:
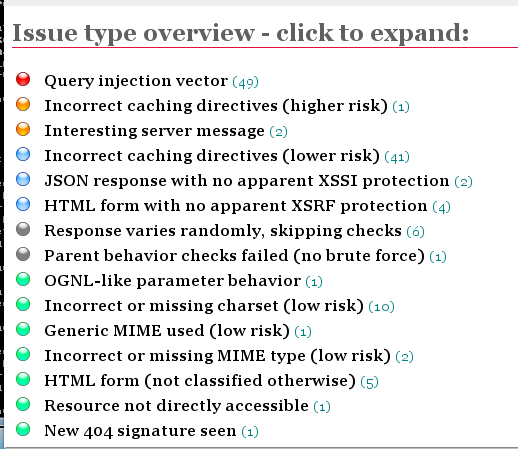
Click the red item to expand it, showing each URL tested, and the exact test that was performed: