Securing NETLAB with CloudFlare
What is NETLAB?
NETLAB is a product used to remotely control
Cisco routers and other devices, used at
colleges for distance education.
Unfortunately, NETLAB lacks HTTPS protection
in its current production version (2014.R1). That feature
is still in beta (2014.R2), as detailed here:
http://www.netdevgroup.com/support/release_notes.html
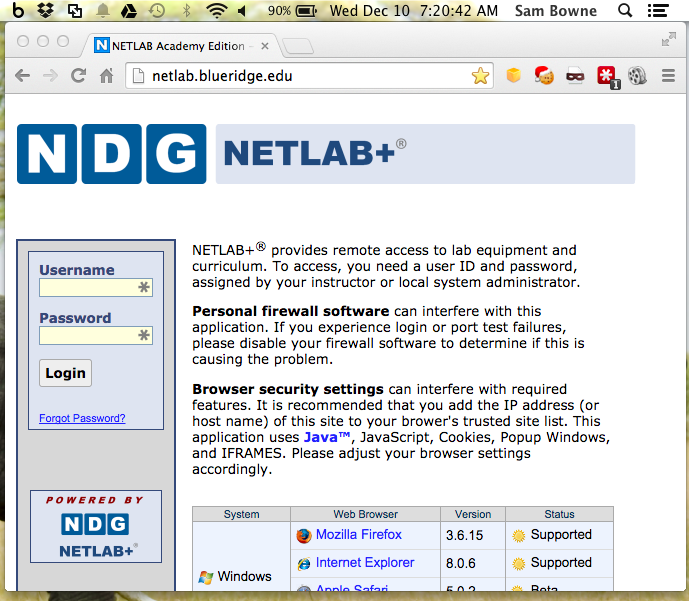
Here's a typical NETLAB server, open
to the Internet:
NETLAB Insecurity
NETLAB logins are not encrypted with HTTPS.
They are not plaintext, but they are weakly
obfuscated with Javascript, and very easy to
reverse.
For a fun hacking project, write a tool
yourself to recover the passwords
from packet captures. I did it
myself in a couple hours, but as a courtesy
to NETLAB I haven't released it yet.
Access via IP Address
This particular NETLAB installation is
useful for my demonstration, because
it can be opened from the IP address alone--the
Host parameter is ignored:

This makes the demonstration below possible--I
can secure the Blue Ridge NETLAB server
without any access to it.
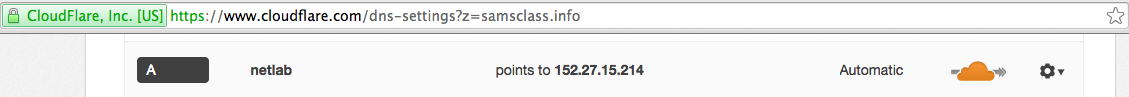
Adding HTTPS with CloudFlare
All I need to do is add that IP address
to my DNS records at CloudFlare:
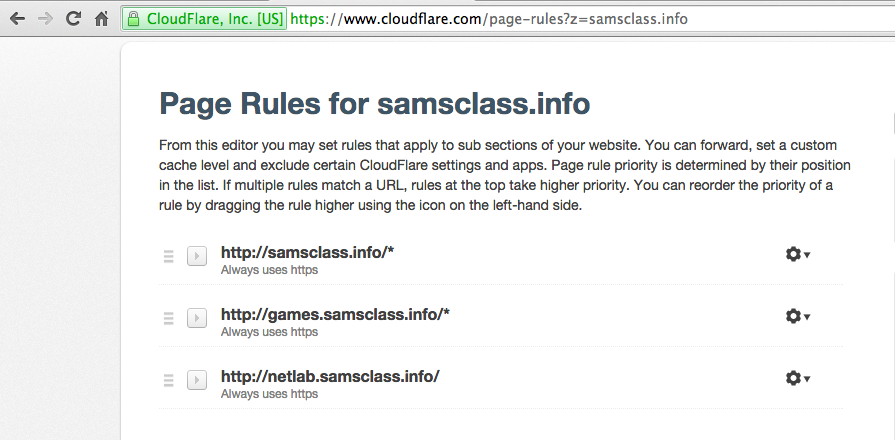
And add a Page Rule:
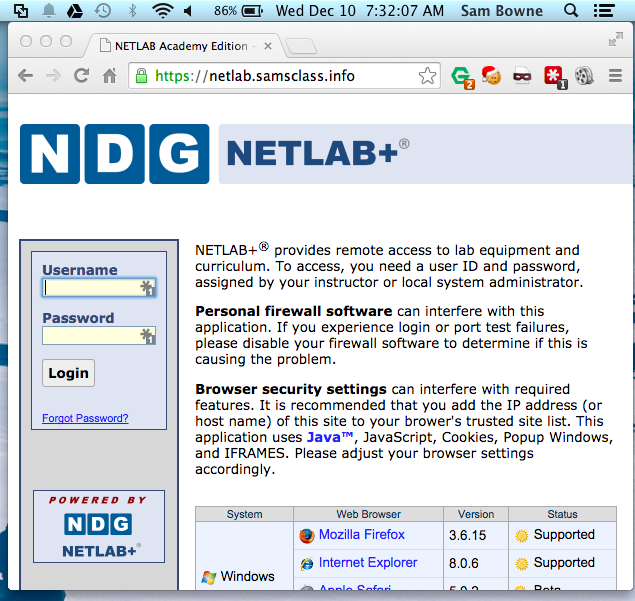
Secure NETLAB Server
Now students can log in with more security
by using this URL:
https://netlab.samsclass.info
Limitations
This is CloudFlare's "Flexible SSL"--it
doesn't provide complete end-to-end
encryption. Since I cannot reconfigure
the Blue Ridge server itself, the last
portion of the login traffic is still
plaintext. But the traffic from the
end user to Cloudflare is encrypted,
protecting the region of highest risk.
It would be more secure to actually
update the NETLAB device to the Beta
version and add a real SSL certificate.
But this is a lot better than no
HTTPS at all, and it's easy and free!
Posted 12-10-14 by Sam Bowne





