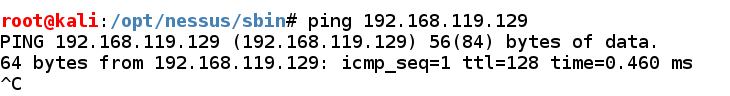
Find your Windows machine's IP address and ping it from the Kali machine. Make sure you can see replies, as shown below.

If you don't see replies, make sure the firewall is off on the Windows machine.
ls /usr/share/nmap/scripts | more
On Kali, in a Terminal window, execute this command:
nmap --script-help default
Scroll back many pages to see the smtp-commands script description, as shown below.

nmap -sC 192.168.119.129
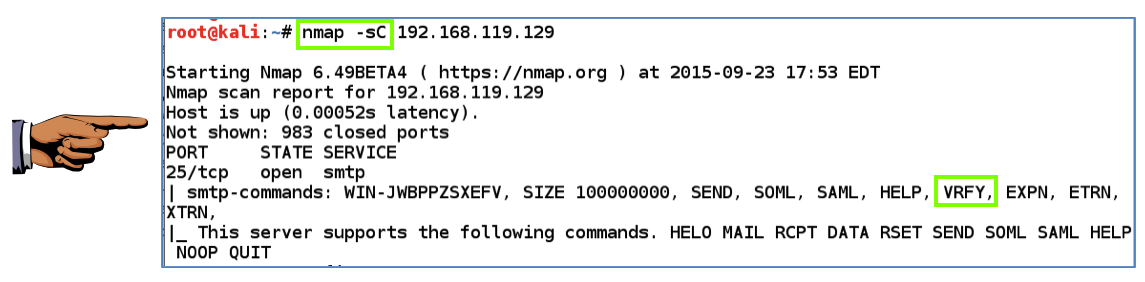
YOU MUST SEND IN A WHOLE-DESKTOP IMAGE FOR FULL CREDIT
On Kali, in a Terminal window, execute these commands to see the scanner modules available:
msfconsole
search auxiliary ^scanner
Execute these commands to enumerate the user accounts on the system via SMB (Microsoft's File and Printer Sharing).
use auxiliary/scanner/smtp/smtp_enum
show options
set RHOSTS 192.168.119.129
exploit
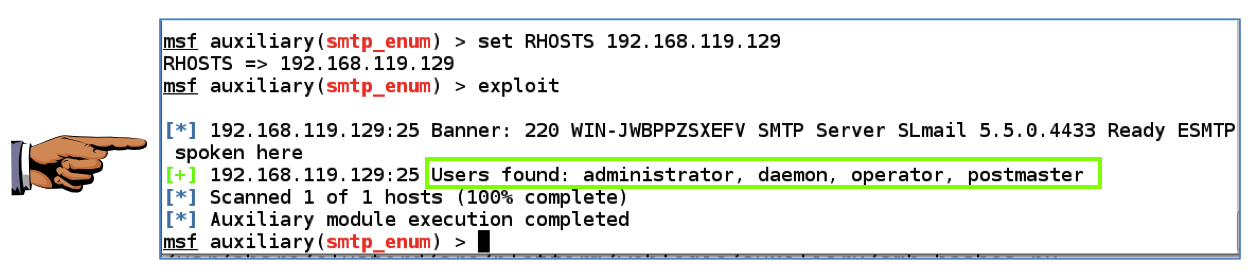
Capture a whole-desktop image and save it as "Proj 9b".
YOU MUST SEND IN A WHOLE-DESKTOP IMAGE FOR FULL CREDIT
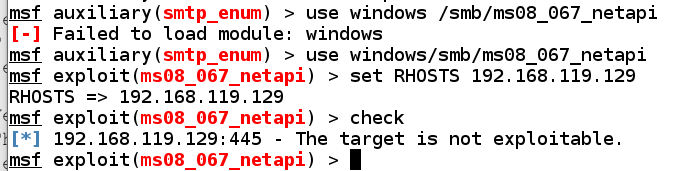
use windows/smb/ms08_067_netapi
set RHOSTS 192.168.119.129
check
exit
You see a page titled "XAMPP 1.7.2", as shown below.

Nikto is a web application vulnerability scanner. Execute this command, replacing the IP address with the IP address of your Windows 2008 machine.
nikto -h 192.168.119.129
These are serious vulnerabilities--that module should be hidden from unauthorized users of the website.
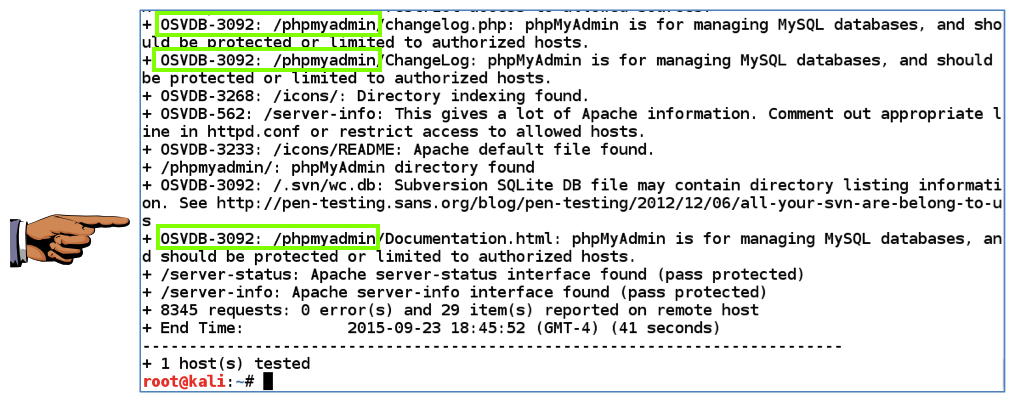
Capture a whole-desktop image and save it as "Proj 9c".
YOU MUST SEND IN A WHOLE-DESKTOP IMAGE FOR FULL CREDIT
Send a Cc to yourself.
Last Modified: 9-28-17