The same techniques work for Linux and Mac hashes, but thousands of times slower, because Windows uses especially weak hashes.
password
8846f7eaee8fb117ad06bdd830b7586c
This is the "modern" NTLM hash, not the even weaker LM hashes which Windows stopped using after Windows XP.
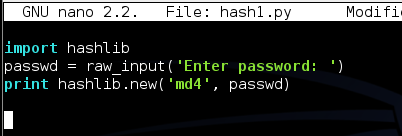
nano hash1.py

Save the file with Ctrl+X, Y, Enter.
python hash1.py
You should see a result like that shown below (the memory location may be different):
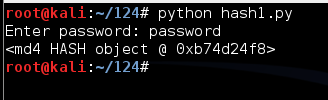
This is a hash, but it's a binary object and all you see is its memory location. To see the normal result in hexadecimal, add the hexdigest() method like this:
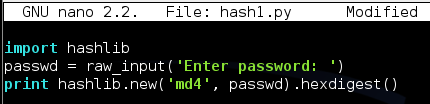
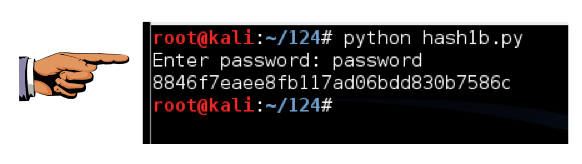
Run the program again. This time you should get the exact hash shown below:
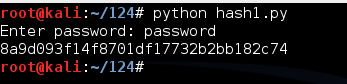
This looks more like a hexadecimal hash, but it's incorrect for Windows passwords. As shown above, the correct NT hash starts with 8846.
That's because the Windows algorithm uses Unicode, not ASCII, to encode the characters.
Modify your program to use Unicode, as shown below. (NOTE: the code for Unicode is "UTF-16LE" with the letters in lowercase, NOT "utf-161e".)
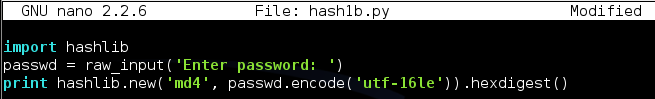
Run the program again. This time you should get the exact hash shown below:
The last several hashes should look like the figure below.
Revised for NETLAB 6-13-16