Proj 19x: Pen Test a Host (Up to 50 pts. extra credit)
What You Need for this Project
A Kali VM, and VMware.
Purpose
To practice
the main steps of a penetration test
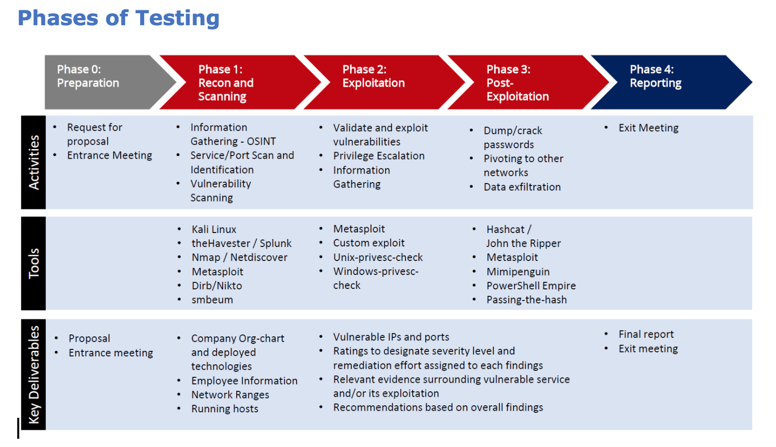
against a single host, as shown below.
For this project, we begin at "Phase 1",
after
Information Gathering (and host discovery)
are complete.
Getting a Target
You can use the VM linked in the box below, or
visit
Hack the Box,
sign up for a free membership, and hack one of those.
Target VM
Download this file, unzip it, and run it in VMware:
PT2.7z
Size: 297,171,095 bytes
SHA-1: 51cab175279a9299ea5c25881f4df21c181f768d
It's got a manual address of 192.168.1.10/24.
To connect to it:
- Set your Kali VM to Bridged networking
- Execute this command:
ifconfig eth0 192.168.1.100/24
- Execute this command:
ping 192.168.1.10
- You should get replies!
|
Phase 1: Recon and Scanning
First do port scans with nmap and/or sparta.
Then scan with vuln scanners like
nikto, nessus, or ZAP. If the target is
a Web server, use dirb to enumerate files.
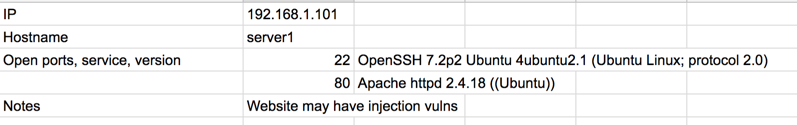
Fill in a chart with your findings, like this:
Research Vulnerabilities
Use Google, searchsploit, exploit-db, etc. to learn
about the vulnerabilities you found.
Rate the vulnerabilities by how much actual
risk they represent to the business. Sort them
into High, Medium, and Low risk.
Phase 2: Exploitation
Exploit the vulnerabilities as possible.
Record the results. Test as many
remote code execution and privilege
escalation vulnerabilities as possible.
Phase 3: Post-Exploitation
Once you have a shell on a box,
focus on the primary business of the server.
Try to find ways to impact the most important
business purposes.
Save screen images to demonstrate your results.
Phase 4: Reporting
Write a report documenting the risks
you identified, and proof of their
exploitability. Rate your results
by their real business impact.
Make your report no longer than 5 pages.
Explain recommendations to remediate the
risks.
Prepare a thorough written report, starting
with a brief executive summary, followed by
appendices with detailed results.
Prepare a brief presentation of your result,
and present it in 5-10 minutes.
Here is
an example report
Credits
This project is based on the work done by CCSF's CPTC 2017 team:
- Elizabeth Biddlecome
- Tomas Horvath
- Tim Ip
- Andrew Mei
- Stuart Morris
- Joseph Nguyen
Also, the VM used is not original; I based it on one others made,
but I can't specify the source without making the project too easy.
Updated 2-21-19


