Place both machines in NAT networking mode.
Ping your Kali mache from the Windows machine and make sure you get replies.
Use ifconfig to find the IP address of your Kali machine and make a note of it.
(There's a BeEF icon on the desktop, but it doesn't work.)
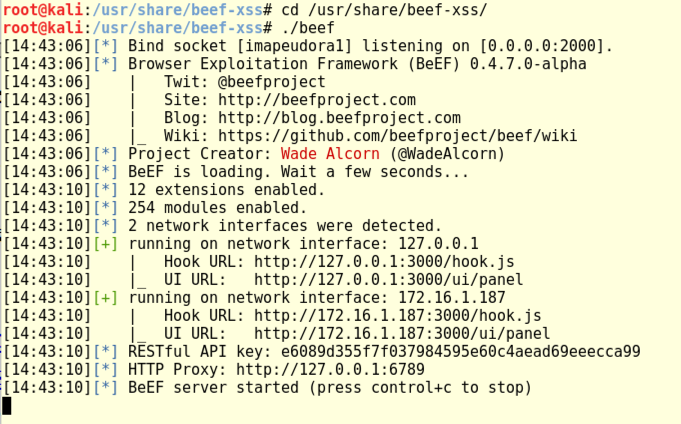
cd /usr/share/beef-xss/
./beef

In Kali, at the top left, click Applications, Favorites, "Firefox ESR". In Firefox, go to:
http://127.0.0.1:3000/ui/panel
The BeEF login page appears. Log in with a username of beef and a password of beef, as shown below.
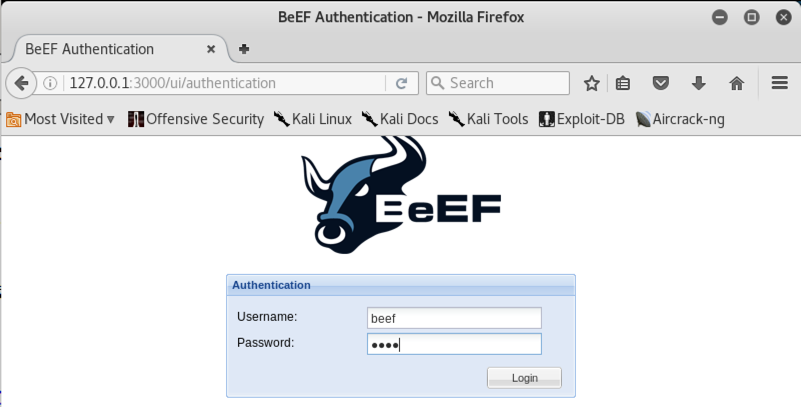
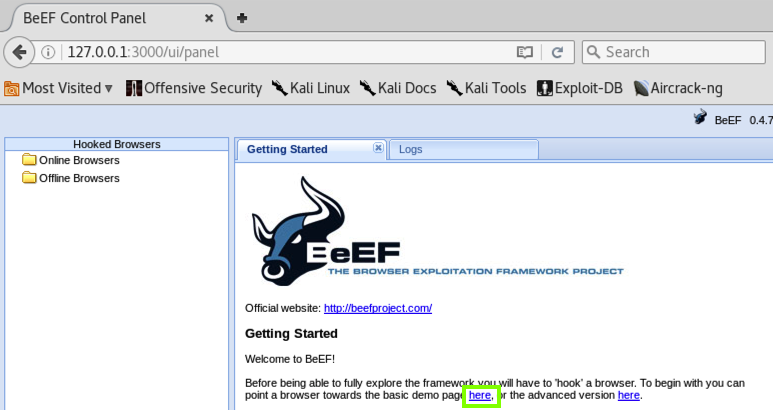
BeEF's control panel opens, as shown below.
Currently there are no "Online Browsers" that you control.
Click the new tab to see it, as shown below. This page contains Javascript loaded from BeEF, which enables BeEF to execute commands within the browser.
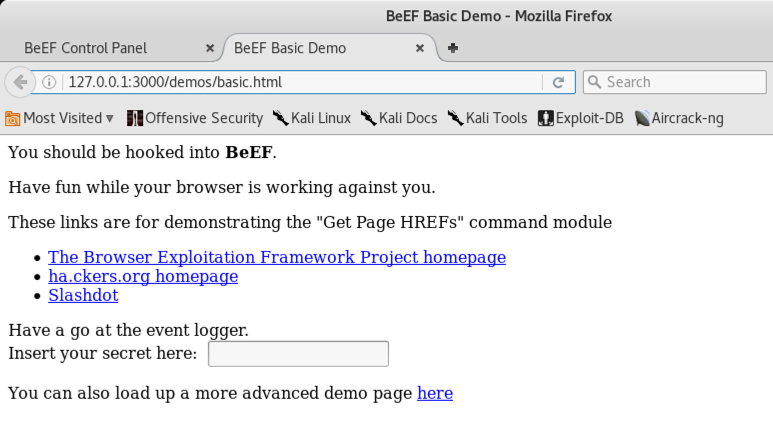
Return to the "BeEF Control Panel" tab.
You should see 127.0.0.1 in the "Online Browsers" section, as shown below.

http://172.16.1.187:3000/demos/basic.html
After a few seconds, BeEF shows the IP address of your target system, as shown below.

Before executing the attack, we need to put several images and a fake malware file on Kali.
On Kali, open a new Terminal window and execute these commands, replacing "YOURNAME" with your own name (without spaces):
cd /usr/share/beef-xss/extensions/demos/html
wget https://samsclass.info/124/proj14/clippy.tar.gz
tar xvf clippy.tar.gz
touch pwned-by-YOURNAME.exe
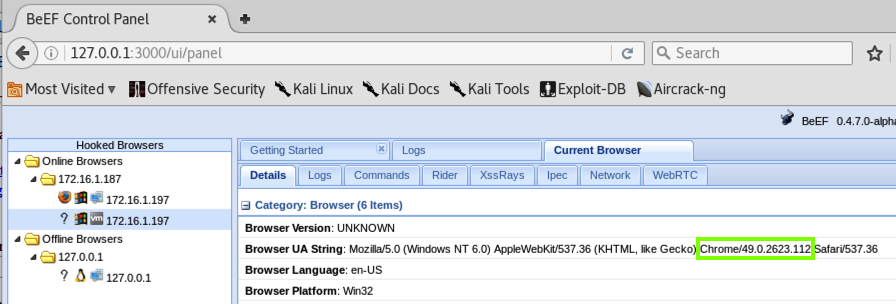
On the right side, the "Browser US String" shows that this is Chrome, as shown below.
In the "BeEF Control Panel", in the right pane, click the Commands tab.
In the "Module Tree" section, at the bottom. Expand the "Social Engineering" folder.
Click Clippy as shown below.
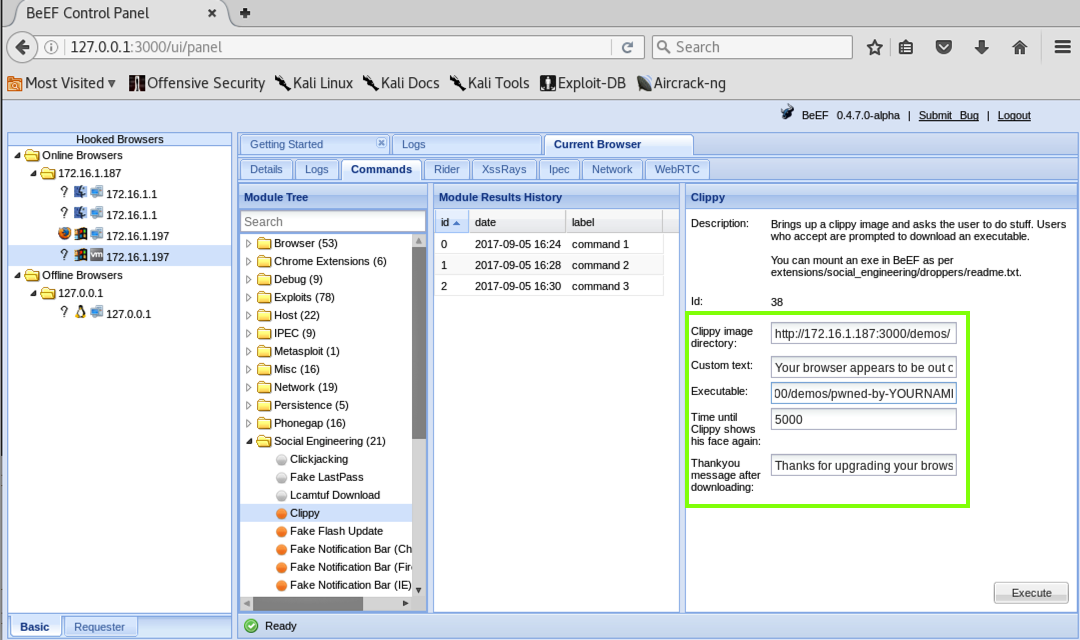
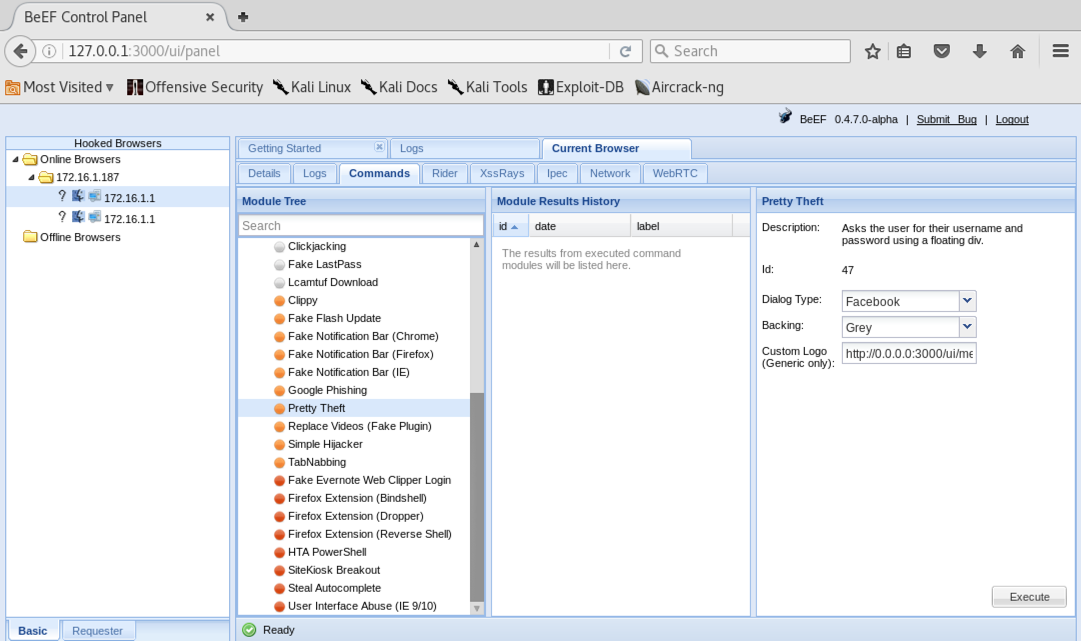
In the "BeEF Control Panel", on the right side, there are several fields to fill in, as indicated by the green outline in the image below.
Enter these values into those fields, replacing the IP address with the IP address of your Kali machine, as shown below.
Clippy image directory: http://172.16.1.187:3000/demos/Executable: http://172.16.1.187:3000/demos/pwned-by-YOURNAME.exe
At the lower right, click the Execute button.
On your target machine, in Chrome, Clippy appears, prompting you to download a file, as shown below.
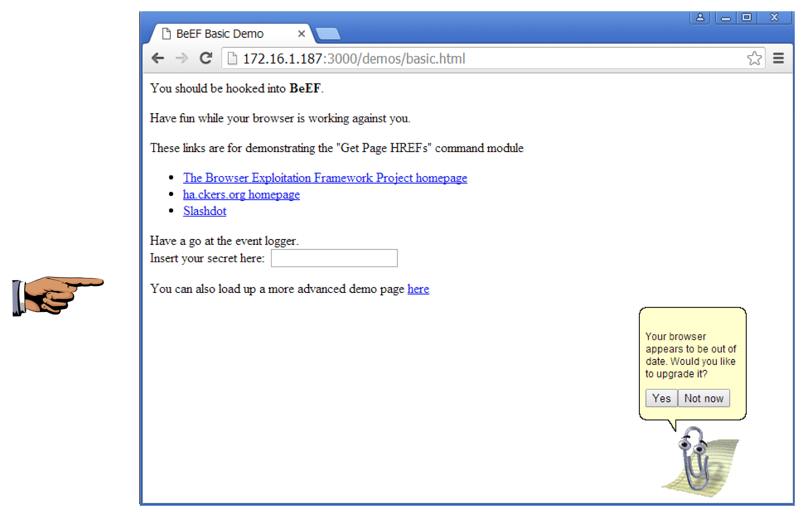
Save a whole-desktop screen capture with a filename of "Proj 16a from YOUR NAME".
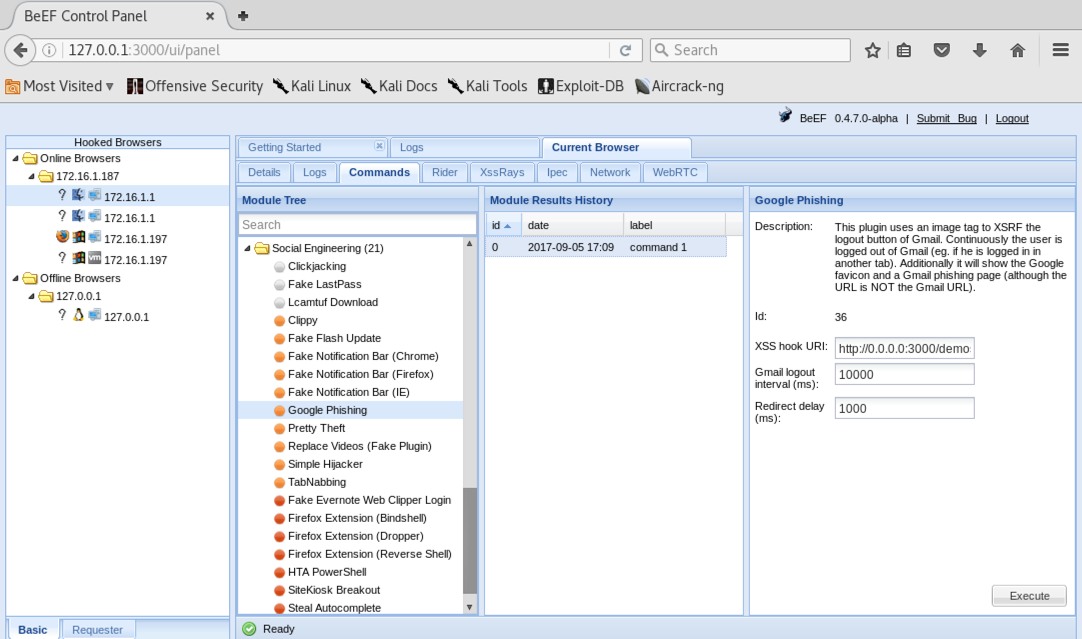
On the right side, in the "XSS Hook URI" field, replace "0.0.0.0" with your Kali machine's IP address, as shown below.
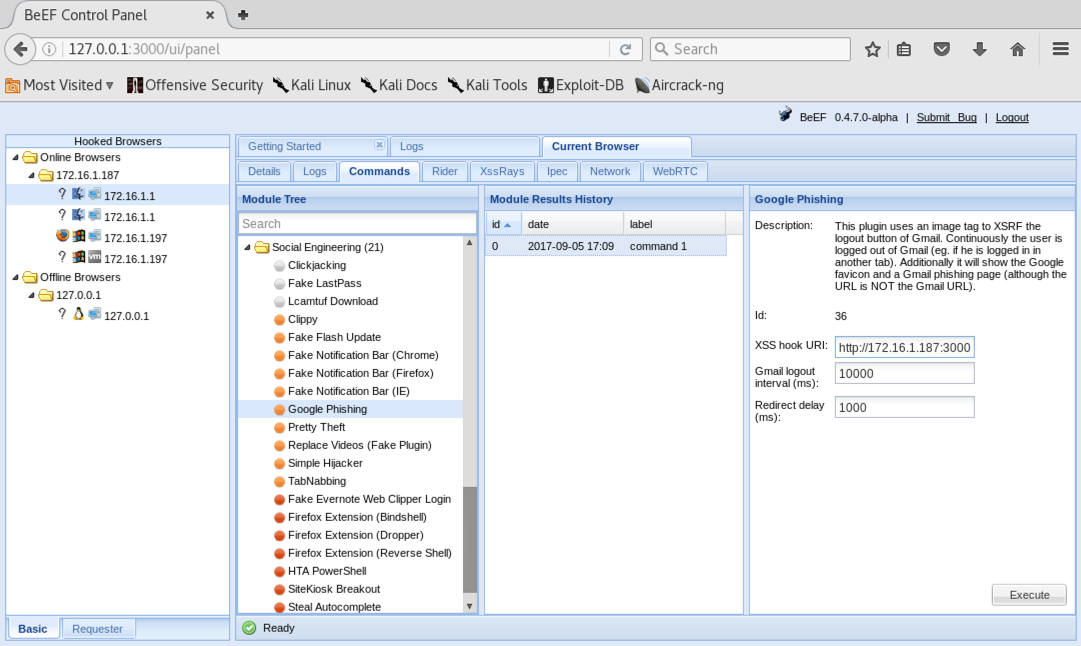
At the lower right, click the Execute button.
On your target machine, in Chrome, a fake Gmail login page appears, as shown below.
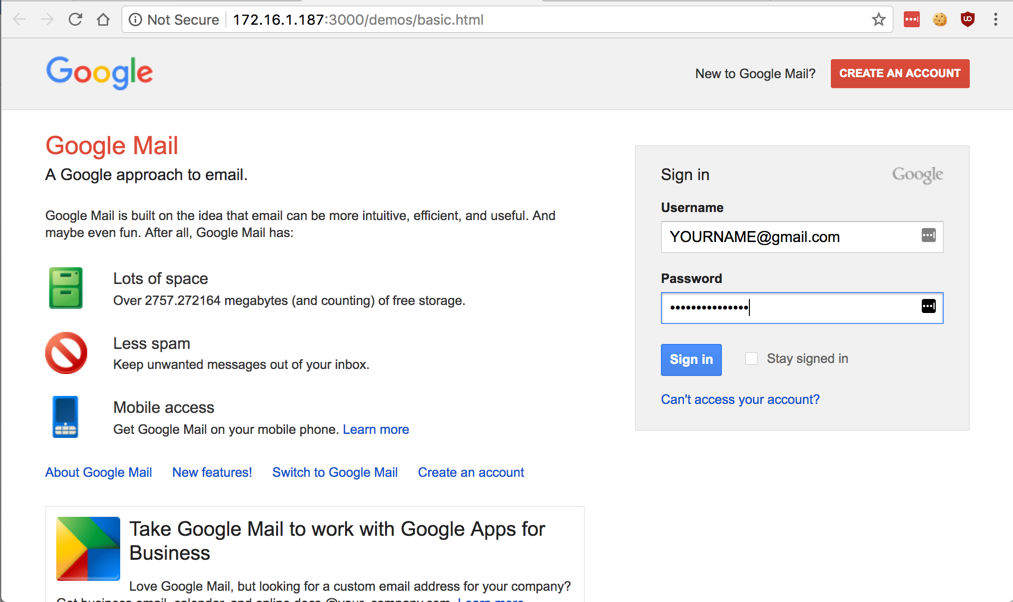
Log in with these fake credentials:
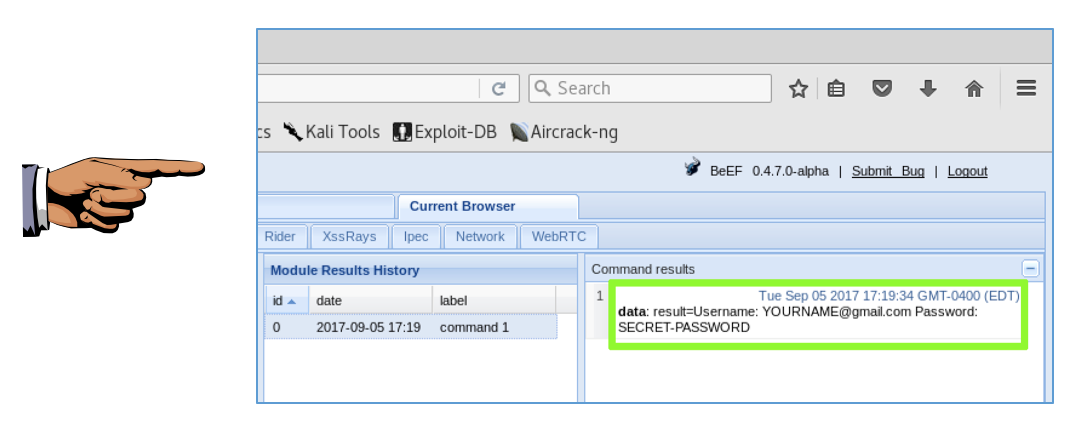
Save a whole-desktop screen capture with a filename of "Proj 16b from YOUR NAME".
At the lower right, click the Execute button.
On your target machine, in Chrome, a fake Facebook login dialog appears, as shown below.
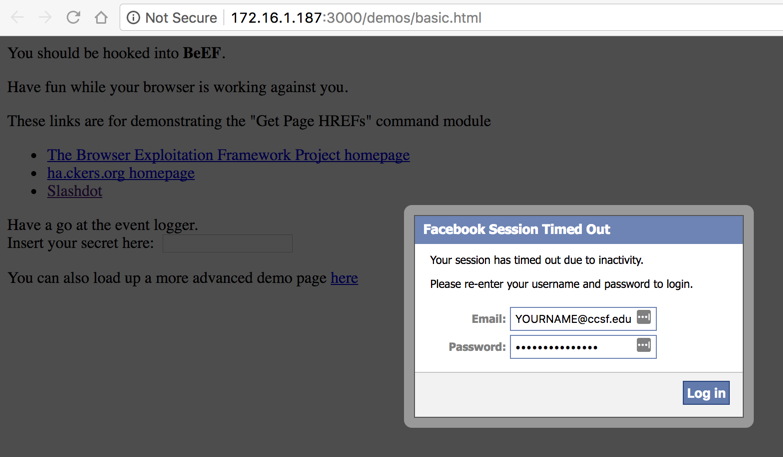
Log in with these fake credentials:
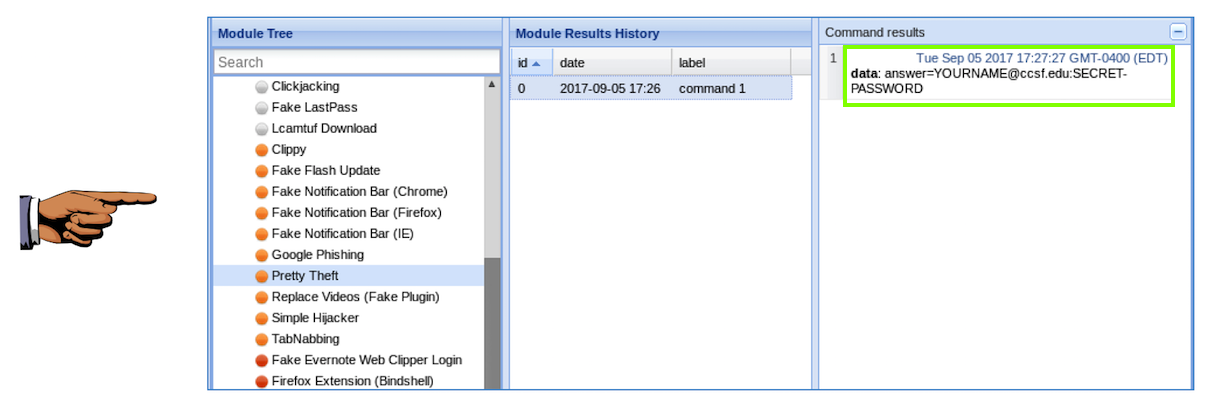
Save a whole-desktop screen capture with a filename of "Proj 16c from YOUR NAME".
Email the image to cnit.124@gmail.com with a subject of "Project 16 from YOUR NAME".